Dictionary SSI
(risk) control
digital.govt.nz
(noun) measure that maintains and / or modifies risk[Source: ISO 31073:2022 modified to add note 3]Additional notes:Note 1: Risk controls include, but are not limited to, any process, policy, device, practice, or other conditions and / or actions which maintain and / or modify risk.Note 2: Risk controls do not always exert the intended or assumed modifying effect.Note 3: When using the Assessing identification risk guidance to calculate levels of identification process, these processes are not included as risk controls.
AAL
ToIP
ABAC
ToIP
ACDC
ToIP
WebOfTrust
ADC
Nist
Term found but the definition does not exist yet.WebOfTrust
ADR
WebOfTrust
AID
Nist
A globally unique identifier of a card application as defined in ISO/IEC 7816-4.ToIP
See autonomic identifier.
WebOfTrust
AID controlled identifiers
ToIP (DID:Webs)
Any identifier, including did:webs DIDs, that have the same AID are by definition referencing the same identity. As defined in the KERI specification
APC
WebOfTrust
API
Nist
A system access point or library function that has a well-defined syntax and is accessible from application programs or user code to provide well-defined functionality.WebOfTrust
AVR
WebOfTrust
Action
Actor
Essif-Lab
entity that can act (do things/execute action), e.g. people, machines, but not organization.
Advertisement
Essif-Lab
an offer by a specific party to provide a (type of) credential, where the offer includes (a reference to) the syntax and semantics specifications of that credential, and also lists various other characteristics that enable other parties to decide whether or not a credential that the advertising party has issued under this offer, is valid to be processed in one or more of its information processes.
Agent
Assertion
Essif-Lab
a declaration/statement, made by a specific party, that something is the case.
Assessment Framework
Attribute
TSWG (ACDC)
a top-level field map within an ACDC that provides a property of an entity that is inherent or assigned to the entity.
Authentic Chained Data Container
ToIP
A digital data structure designed for both cryptographic verification and chaining of data containers. ACDC may be used for digital credentials.
For more information, see: ToIP ACDC Task Force.
TSWG (Keri)
a directed acyclic graph with properties to provide a verifiable chain of proof-of-authorship. See the full specification
Authority (Centralized or Decentralized)
Autonomic Identifier
TSWG (ACDC)
a self-managing cryptonymous identifier that must be self-certifying (self-authenticating) and must be encoded in CESR as a qualified Cryptographic Primitive.
Autonomic Identifier (AID)
TSWG (CESR)
a self-managing cryptonymous identifier that must be self-certifying (self-authenticating) and must be encoded in CESR as a qualified Cryptographic Primitive.
Autonomic identifier
TSWG (Keri)
a self-managing cryptonymous identifier that must be self-certifying (self-authenticating) and must be encoded in CESR as a qualified Cryptographic primitive.
Autonomic identity system
TSWG (Keri)
an identity system that includes a primary root-of-trust in self-certifying identifiers that are strongly bound at issuance to a cryptographic signing (public, private) key pair. An AIS enables any entity to establish control over an AN in an independent, interoperable, and portable way.
Autonomic namespace
TSWG (Keri)
a namespace that is self-certifying and hence self-administrating. An AN has a self-certifying prefix that provides cryptographic verification of root control authority over its namespace. All derived AIDs in the same AN share the same root-of-trust, source-of-truth, and locus-of-control (RSL). The governance of the namespace is therefore unified into one entity, that is, the controller who is/holds the root authority over the namespace.
BADA
WebOfTrust
BADA-RUN
ToIP (DID:Webs)
Best available data acceptance - Read/Update/Nullify provides a medium level of security because events are ordered in a consistent way, using a combination of date-time and a key state. The latest event is the one with the latest date-time for the latest key state. See The KERI spec for more detail.
BFT
Nist
Term found but the definition does not exist yet.WebOfTrust
BOLA
WebOfTrust
Backer
TSWG (Keri)
an alternative to a traditional KERI based Witness commonly using Distributed Ledger Technology (DLT) to store the KEL for an identifier.
C2PA
CA
ToIP
See: certificate authority.
CAI
ToIP
CBOR
Nist
Term found but the definition does not exist yet.WebOfTrust
CESR
WebOfTrust
CLC
WebOfTrust
CRUD
Nist
Term found but the definition does not exist yet.WebOfTrust
CRUD
Definition
Is acronym for the traditional client-server database update policy is CRUD (Create, Read, Update, Delete).
CRUD as opposed to RUN which is the acronym for the new peer-to-peer end-verifiable monotonic update policy.
OOBI related
We RUN off the CRUD, which means that because the source of truth for each data item is a decentralized controller Peer, a given database hosted by any Peer does not create records in the traditional sense of a server creating records for a client.
CSPRNG
WebOfTrust
CSPRNG
Definition
means "Cryptographically Secure Pseudorandom Number Generator" which means that a sequence of numbers (bits, bytes...) that is produced from an algorithm which is deterministic (the sequence is generated from some unknown internal state), hence pseudorandom, is also cryptographically secure, or not.
It is cryptographically secure if nobody can reliably distinguish the output from true randomness, even if the PRNG algorithm is perfectly known (but not its internal state). A non-cryptographically secure PRNG would fool basic statistical tests but can be distinguished from true randomness by an intelligent attacker.
(Source: https://crypto.stackexchange.com/questions/12436/what-is-the-difference-between-csprng-and-prng)See also
CT
Nist
A framework for publicly logging the existence of Transport Layer Security (TLS) certificates as they are issued or observed in a manner that allows anyone to audit CA activity and notice the issuance of suspect certificates as well as to audit the certificate logs themselves. (Experimental RFC 6962)WebOfTrust
Capability (of a Party)
Essif-Lab
the (named) combination of (a) the means of a specific party to get something done, (b) the party governance process that ensures that its (business) policies for getting that something done are being created and maintained, and (c) the party management process that creates and maintains the (operational) policies, such that every employee that has a task in getting this something done can find and interpret a policy and use it as it executes action in such tasks.
Capability (of an Actor)
Chain-link Confidential Disclosure
TSWG (ACDC)
contractual restrictions and liability imposed on a recipient of a disclosed ACDC that contractually link the obligations to protect the disclosure of the information contained within the ACDC to all subsequent recipients as the information moves downstream. The Chain-link Confidential Disclosure provides a mechanism for protecting against unpermissioned exploitation of the data disclosed via an ACDC.
Coalition for Content Provenance and Authenticity
ToIP
C2PA is a Joint Development Foundation project of the Linux Foundation that addresses the prevalence of misleading information online through the development of technical standards for certifying the source and history (or provenance) of media content.
Also known as: C2PA.
See also: Content Authenticity Initiative.
Colleague
Commitment Decision
Essif-Lab
the decision of that party whether or not to commit to that business transaction, i.e. (promise) to fulfill the obligation that the associated transaction agreement proposal would impose on that party once it were signed.
Communication Channel
Essif-Lab
a (digital or non-digital) means by which two actor can exchange messages with one another.
Communication Session
Essif-Lab
a time interval during which two actor have an established communication channel that does not exist outside of that time interval.
Community
Compact Disclosure
TSWG (ACDC)
a disclosure of an ACDC that discloses only the SAID(s) of some or all of its field maps. Both Partial and Selective Disclosure rely on Compact Disclosure.
Compliance
Essif-Lab
the state of realization of a set of conformance criteria or normative framework of a party.
Compliance Objective
Compliance level
Essif-Lab
a measure for stating how well an entity conforms with a stated (set of) requirement(s).
Compliance management
Essif-Lab
the process that is run by (or on behalf of) a specific party for the purpose of managing its compliance objectives.
Composability
TSWG (CESR)
short for text-binary concatenation composability. An encoding has Composability when any set of Self-Framing concatenated Primitives expressed in either the Text domain or Binary domain may be converted as a group to the other Domain and back again without loss.
Concept
Concise Binary Object Representation
TSWG (Keri)
a binary serialization format, similar in concept to JSON but aiming for greater conciseness. Defined in [RFC7049].
Configuration traits
TSWG (Keri)
a list of specially defined strings representing a configuration of a KEL. See (Configuration traits field)[#configuration-traits-field].
Content Authenticity Initiative
ToIP
The Content Authenticity Initiative (CAI) is an association founded in November 2019 by Adobe, the New York Times and Twitter. The CAI promotes an industry standard for provenance metadata defined by the C2PA. The CAI cites curbing disinformation as one motivation for its activities.
Source: Wikipedia.
Also known as: CAI.
Contractually Protected Disclosure
TSWG (ACDC)
a discloser of an ACDC that leverages a Graduated Disclosure so that contractual protections can be put into place to minimize the leakage of information that can be correlated. A Contractually Protected Disclosure partially or selectively reveals the information contained within the ACDC in the initial interaction with the recipient and disclose further information only after the recipient agrees to the terms established by the discloser. More information may be progressively revealed as the recipient agrees to additional terms.
Control
Essif-Lab
the combination of resources (e.g. people, tools, budgets, time) and processes that are tasked to realize a specific control objective of a particular party.
Control Objective
Control Process
Control level
Essif-Lab
a measure for the efficiency and effectiveness in which a control produces the results specified by its control objective
Controller
TSWG (ACDC)
an entity that can cryptographically prove the control authority over an AID and make changes on the associated KEL. A controller of a multi-sig AID may consist of multiple controlling entities. See controller.TSWG (Keri)
an entity that can cryptographically prove the control authority over an AID and make changes on the associated KEL. A controller of a multi-sig AID may consist of multiple controlling entities.
Controllership
Essif-Lab
the capability of an actor to execute action on a specific entity for the purpose of ensuring that this entity will act/behave, or be used, in a particular way.
Corpus of Terminology
Credential
Credential Catalogue
Essif-Lab
a functional component that has the capability to register and advertise the information about credential types that their respective governing parties have decided to disclose so as to enable other parties to decide whether or not it is beneficial for them to use credential of such types.
Credential Type
Essif-Lab
the specification of the contents, properties, constraints etc. that credential of this type must have/comply with.
Cryptographic Primitive
TSWG (CESR)
the serialization of a value associated with a cryptographic operation including but not limited to a digest (hash), a salt, a seed, a private key, a public key, or a signature.TSWG (Keri)
the serialization of a value associated with a cryptographic operation including but not limited to a digest (hash), a salt, a seed, a private key, a public key, or a signature.
Cryptonym
TSWG (Keri)
a cryptographic pseudonymous identifier represented by a string of characters derived from a random or pseudo-random secret seed or salt via a one-way cryptographic function with a sufficiently high degree of cryptographic strength (e.g., 128 bits, see appendix on cryptographic strength) [13] [14] [12] [11]. A Cryptonym is a type of Primitive. Due to the entropy in its derivation, a Cyptonym is a universally unique identifier and only the Controller of the secret salt or seed from which the Cryptonym is derived may prove control over the Cryptonym. Therefore the derivation function must be associated with the Cryptonym and may be encoded as part of the Cryptonym itself.
Current threshold
TSWG (Keri)
represents the number or fractional weights of signatures from the given set of current keys required to be attached to a Message for the Message to be considered fully signed.
DAG
Nist
Term found but the definition does not exist yet.WebOfTrust
DAR
Nist
Term found but the definition does not exist yet.WebOfTrust
DEL
WebOfTrust
DHT
WebOfTrust
DID
Nist
Term found but the definition does not exist yet.ToIP
See: decentralized identifier.
WebOfTrust
DID URL
ToIP
A DID plus any additional syntactic component that conforms to the definition in section 3.2 of the W3C Decentralized Identifiers (DIDs) 1.0 specification. This includes an optional DID path (with its leading / character), optional DID query (with its leading ? character), and optional DID fragment (with its leading # character).
Source: W3C DID.
W3C (DID)
A DID plus any additional syntactic component that conforms to thedefinition in 3.2 DID URL Syntax. This includes an optional DIDpath (with its leading / character), optional DID query(with its leading ? character), and optional DID fragment(with its leading # character).
DID URL dereferencer
W3C (DID)
A software and/or hardware system that performs the DID URL dereferencingfunction for a given DID URL or DID document.
DID URL dereferencing
W3C (DID)
The process that takes as its input a DID URL and a set of inputmetadata, and returns a resource. This resource might be a DIDdocument plus additional metadata, a secondary resourcecontained within the DID document, or a resource entirelyexternal to the DID document. The process uses DID resolution tofetch a DID document indicated by the DID contained within theDID URL. The dereferencing process can then perform additional processingon the DID document to return the dereferenced resource indicated by theDID URL. The inputs and outputs of this process are defined in7.2 DID URL Dereferencing.
DID controller
ToIP
An entity that has the capability to make changes to a DID document. A DID might have more than one DID controller. The DID controller(s) can be denoted by the optional controller property at the top level of the DID document. Note that a DID controller might be the DID subject.
Source: W3C DID.
See also: controller.
W3C (DID)
An entity that has the capability to make changes to a DID document. ADID might have more than one DID controller. The DID controller(s)can be denoted by the optional controller property at the top level of theDID document. Note that a DID controller might be the DIDsubject.
DID delegate
W3C (DID)
An entity to whom a DID controller has granted permission to use averification method associated with a DID via a DIDdocument. For example, a parent who controls a child's DID documentmight permit the child to use their personal device in order toauthenticate. In this case, the child is the DID delegate. Thechild's personal device would contain the private cryptographic materialenabling the child to authenticate using the DID. However, the childmight not be permitted to add other personal devices without the parent'spermission.
DID document
ToIP
A set of data describing the DID subject, including mechanisms, such as cryptographic public keys, that the DID subject or a DID delegate can use to authenticate itself and prove its association with the DID. A DID document might have one or more different representations as defined in section 6 of the W3C Decentralized Identifiers (DIDs) 1.0 specification.
Source: W3C DID.
ToIP (DID:Webs)
A set of data describing the subject of a DID, as defined by DID Core. See also section DID Documents.W3C (DID)
A set of data describing the DID subject, including mechanisms, such ascryptographic public keys, that the DID subject or a DID delegatecan use to authenticate itself and prove its association with theDID. A DID document might have one or more differentrepresentations as defined in 6. Representations or in theW3C DID Specification Registries [DID-SPEC-REGISTRIES].
DID document metadata
ToIP (DID:Webs)
DID document metadata is metadata about the DID and the DID document that is the result of the DID Resolution process. See also DID Document Metadata in the DID Core specification.
DID fragment
W3C (DID)
The portion of a DID URL that follows the first hash sign character(#). DID fragment syntax is identical to URI fragment syntax.
DID method
ToIP
A definition of how a specific DID method scheme is implemented. A DID method is defined by a DID method specification, which specifies the precise operations by which DIDs and DID documents are created, resolved, updated, and deactivated.
Source: W3C DID.
For more information: https://www.w3.org/TR/did-core/#methods
W3C (DID)
A definition of how a specific DID method scheme is implemented. A DID method isdefined by a DID method specification, which specifies the precise operations bywhich DIDs and DID documents are created, resolved, updated,and deactivated. See 8. Methods.
DID path
W3C (DID)
The portion of a DID URL that begins with and includes the first forwardslash (/) character and ends with either a question mark(?) character, a fragment hash sign (#) character,or the end of the DID URL. DID path syntax is identical to URI path syntax.See Path.
DID query
W3C (DID)
The portion of a DID URL that follows and includes the first questionmark character (?). DID query syntax is identical to URI querysyntax. See Query.
DID resolution
W3C (DID)
The process that takes as its input a DID and a set of resolutionoptions and returns a DID document in a conforming representationplus additional metadata. This process relies on the "Read" operation of theapplicable DID method. The inputs and outputs of this process aredefined in 7.1 DID Resolution.
DID resolution metadata
ToIP (DID:Webs)
DID resolution metadata is metadata about the DID Resolution process that was performed in order to obtain the DID document for a given DID. See also DID Resolution Metadata in the DID Core specification.
DID resolver
W3C (DID)
A DID resolver is a software and/or hardware component that performs theDID resolution function by taking a DID as input and producing aconforming DID document as output.
DID scheme
W3C (DID)
The formal syntax of a decentralized identifier. The generic DID schemebegins with the prefix did: as defined in 3.1 DID Syntax. Each DID method specification defines a specificDID method scheme that works with that specific DID method. In a specific DIDmethod scheme, the DID method name follows the first colon and terminates withthe second colon, e.g., did:example:
DID subject
ToIP
The entity identified by a DID and described by a DID document. Anything can be a DID subject: person, group, organization, physical thing, digital thing, logical thing, etc.
Source: W3C DID.
See also: subject.
W3C (DID)
The entity identified by a DID and described by a DID document.Anything can be a DID subject: person, group, organization, physical thing,digital thing, logical thing, etc.
DKMI
WebOfTrust
DPKI
WebOfTrust
DRM
ToIP
DWN
ToIP
See: Decentralized Web Node.
Data
Essif-Lab
something (tangible) that can be used to communicate a meaning (which is intangible/information).
Dead-Attack
TSWG (Keri)
an attack on an establishment event that occurs after the Key-state for that event has become stale because a later establishment event has rotated the sets of signing and pre-rotated keys to new sets. See (Security Properties of Prerotation)[#dead-attacks].
Decentralized GRC Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain one's thinking about topics related to Governance, Risk management and Compliance (GRC) in a decentralized context, i.e., a context in which parties all autonomously do their own GRC.
Decentralized Identity Foundation
ToIP
A non-profit project of the Linux Foundation chartered to develop the foundational components of an open, standards-based, decentralized identity ecosystem for people, organizations, apps, and devices.
See also: OpenWallet Foundation, ToIP Foundation.
For more information, see: http://identity.foundation/
Decentralized Risk Management Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain how individual parties can efficiently and effectively perform their own risk management processes, while taking into account that there are other parties that have expectations towards them.
Decentralized Web Node
ToIP
A decentralized personal and application data storage and message relay node, as defined in the DIF Decentralized Web Node specification. Users may have multiple nodes that replicate their data between them.
Source: DIF DWN Specification.
Also known as: DWN.
For more information, see: https://identity.foundation/decentralized-web-node/spec/
Decentralized key management infrastructure
TSWG (Keri)
a key management infrastructure that does not rely on a single entity for the integrity and security of the system as a whole. Trust in a DKMI is decentralized through the use of technologies that make it possible for geographically and politically disparate entities to reach an agreement on the key state of an identifier DPKI.
Decision
Decision Making Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain how parties would, could, or should reason in order to reach good conclusions and make good decisions. This can be used as a basis for understanding the information needs of parties as they need to decide e.g. whether or not to commit to a Transaction proposal, or whether or not data is valid for some purpose. This pattern is based on Toulmin's use of arguments (of which a pragmatical text can be found here)
Define
Essif-Lab
to provide a criterion and a term, where the criterion can be used by people to determine whether or not something is an instance/example of a concept (or other semantic unit), and the term is used to refer to that concept, or an arbitrary instance thereof.
Definition
Definition Pattern
Essif-Lab
a mental model that describes the relations between a concept (or any other semantic unit), the term(s) that are used to refer to it, and the criteria to use for determining whether or not something is an instance (example) of that semantic unit.
Delegate
Essif-Lab
the transferral of ownership of one or more obligation of a party (the delegator), including the associated accountability, to another party (the delegatee)), which implies that the delegatee can realize such obligation as it sees fit.
Dependent
Essif-Lab
an entity for the caring for and/or protecting/guarding/defending of which a guardianship arrangement has been established.
Dictionary
Essif-Lab
an alphabetically sorted list of term with various meanings they may have in different contexts.
Disclosee
TSWG (ACDC)
a role of an entity that is a recipient to which an ACDC is disclosed. A Disclosee may or may not be the Issuee of the disclosed ACDC.
Discloser
TSWG (ACDC)
a role of an entity that discloses an ACDC. A Discloser may or may not be the Issuer of the disclosed ACDC.
Documentation Interoperability
Essif-Lab
the property that a documentation system of making its content comprehensible for a variety of people that come from different backgrounds.
Domain
TSWG (CESR)
a representation of a Primitive either Text (T), Binary (B) or Raw binary (R).
Duplicity
TSWG (ACDC)
the existence of more than one Version of a Verifiable KEL for a given AID. See duplicity.TSWG (Keri)
the existence of more than one Version of a Verifiable KEL for a given AID.
Duties and Rights Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain what a generic duties and rights consists of (based on Hofeld's theories), and relates it to jurisdictions, parties and legal entities.
E2E
WebOfTrust
ECR
WebOfTrust
ESSR
WebOfTrust
Ecosystem
Essif-Lab
a set of at least two (autonomous) parties (its 'members') whose individual work complements that of other members, and is of benefit to the set as a whole.
Edge
TSWG (ACDC)
a top-level field map within an ACDC that provides edges that connect to other ACDCs, forming a labeled property graph (LPG).
Employee
Employer
Employment Contract
End-to-End Principle
ToIP
The end-to-end principle is a design framework in computer networking. In networks designed according to this principle, guaranteeing certain application-specific features, such as reliability and security, requires that they reside in the communicating end nodes of the network. Intermediary nodes, such as gateways and routers, that exist to establish the network, may implement these to improve efficiency but cannot guarantee end-to-end correctness.
Source: Wikipedia.
For more information, see: https://trustoverip.org/permalink/Design-Principles-for-the-ToIP-Stack-V1.0-2022-11-17.pdf
End-verifiability
TSWG (Keri)
a data item or statement may be cryptographically securely attributable to its source (party at the source end) by any recipient verifier (party at the destination end) without reliance on any infrastructure not under the verifiers ultimate control.
Entity
Essif-Lab
someone or something that is known to exist.
Establishment event
TSWG (Keri)
a Key event that establishes or changes the Key state which includes the current set of authoritative keypairs (Key state) for an AID.
Expectation
FAL
ToIP
FFI
WebOfTrust
First-Seen
TSWG (Keri)
refers to the first instance of a Message received by any Witness or Watcher. The first-seen event is always seen, and can never be unseen. It forms the basis for Duplicity detection in KERI based systems.
Framework (Conceptual)
Essif-Lab
a set of assumptions, concepts, values, and practices that constitutes a way of viewing reality.
Framing Code
TSWG (ACDC)
a code that delineate a number of characters or bytes, as appropriate, that can be extracted atomically from a Stream.
Framing Codes
TSWG (CESR)
codes that delineate a number of characters or bytes, as appropriate, that can be extracted atomically from a Stream.
Full Disclosure
TSWG (ACDC)
a disclosure of an ACDC that discloses the full details of some or all of its field maps. In the context of Selective Disclosure, Full Disclosure means detailed disclosure of the selectively disclosed attributes, not the detailed disclosure of all selectively disclosable attributes. In the context of Partial Disclosure, Full Disclosure means detailed disclosure of the field map that was so far only partially disclosed.
GAR
WebOfTrust
GDPR
ToIP
GLEIF
WebOfTrust
GLEIS
WebOfTrust
GLEIS
Definition
Global Legal Entity Identifier System
GPG
WebOfTrust
GRC
General Data Protection Regulation
ToIP
The General Data Protection Regulation (Regulation (EU) 2016/679, abbreviated GDPR) is a European Union regulation on information privacy in the European Union (EU) and the European Economic Area (EEA). The GDPR is an important component of EU privacy law and human rights law, in particular Article 8(1) of the Charter of Fundamental Rights of the European Union. It also governs the transfer of personal data outside the EU and EEA. The GDPR's goals are to enhance individuals' control and rights over their personal information and to simplify the regulations for international business.
Source: Wikipedia.
Also known as: GDPR.
Glossary
Essif-Lab
an alphabetically sorted list of term with the (single) meaning it has in (at least) one context.
Governance
Governance and Management Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain how parties organize that their objectives are realized, either by doing the associated work themselves, or by arranging for other parties to do that.
Governance, Risk Management, and Compliance
ToIP
Governance, risk management, and compliance (GRC) are three related facets that aim to assure an organization reliably achieves objectives, addresses uncertainty and acts with integrity. Governance is the combination of processes established and executed by the directors (or the board of directors) that are reflected in the organization's structure and how it is managed and led toward achieving goals. Risk management is predicting and managing risks that could hinder the organization from reliably achieving its objectives under uncertainty. Compliance refers to adhering with the mandated boundaries (laws and regulations) and voluntary boundaries (company's policies, procedures, etc.)
Source: Wikipedia.
Also known as: GRC.
Governor
Graduated Disclosure
TSWG (ACDC)
a disclosure of an ACDC that does not to reveal its entire content in the initial interaction with the recipient and, instead, partially or selectively reveal only the information contained within the ACDC that is necessary to further a transaction with the recipient. A Graduated disclosure may invole multiple steps where more information is prgressively revealed as the recipient satisfy the conditions set by the discloser. Compact disclosure, Partial disclosure, Selective disclosure and Full disclosure are all Graduated disclosure mechanisms.
Group/Count Codes
TSWG (CESR)
special Framing Codes that can be specified to support groups of Primitives which make them pipelinable. Self-framing grouping using Count Codes is one of the primary advantages of composable encoding.
Guardian
Essif-Lab
a party that has been assigned rights and duties in a Guardianship Arrangement for the purpose of caring for and/or protecting/guarding/defending the entity that is the dependent in that Guardianship Arrangement.
Guardianship (in a Jurisdiction)
Essif-Lab
the specification of a set of rights and duties between legal entities of the jurisdiction that enforces these rights and duties, for the purpose of caring for and/or protecting/guarding/defending one or more of these entities. (Synonym of Guardianship Arrangement)
Guardianship Arrangement
Essif-Lab
guardianship Arrangement (in a Jurisdiction): the specification of a set of rights and duties between legal entities of the jurisdiction that enforces these rights and duties, for the purpose of caring for and/or protecting/guarding/defending one or more of these entities.
Guardianship Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain what a generic guardianship consists of, and how it relates to guardians, dependents, jurisdictions, etc.
Guardianship-type
Essif-Lab
a class of guardianship arrangements within the jurisdiction that governs and manages them.
HSM
Nist
Term found but the definition does not exist yet.ToIP
See: hardware security module.
WebOfTrust
Holder
Essif-Lab
a component that implements the capability to handle presentation requests from a peer agent, produce the requested data (a presentation) according to its principal's holder-policy, and send that in response to the request.
Holder Policy
Essif-Lab
a digital policy that enables an operational holder component to function in accordance with the objective of its principal.
Home
WebOfTrust
Home
Welcome to the WebofTrust terms wiki!
The wiki also serves the glossary terms for the underlying and related techniques to ACDC, like KERI, CESR and OOBI.
There are a few practical rules from the originator ToIP to get these wiki terms through their equivalent github actions script, please:
- beware all new wiki items you create, lead to new .md files. We'd like to know
- introduce lowercase names with spaces (they will convert into lower case names with dashes between the words)
- start with ## Definition header; example
- start with uppercase abbreviations with only the "## See" header; example
- don't delete items (i.e. .md files) but make clear they are depreciated and / or link to the new concept / term
- don't change or update the name of an item single handed, for it might change the concept / meaning for other people and create dead links for those who read - or link to the term. Please open an issue or a PR to discuss first.
- any other immediate updates and amendments welcome, the revisions are available for us to be able to (partially) revert if something unwanted or unexpected happens.
KERISSE reads this wiki
The weboftrust wiki glossary is currently our input tool for our KERI Suite glossary. However, we regularly scrape the wiki into KERISSE, we add features and metadata, we connect relevant matching terms from related glossaries and finally we index it for the KERI Suite Search Engine (KERISSE).
Have fun CRU-ing!
'* CRU=Create Read Update
Human Being
Essif-Lab
a person of flesh and blood (homo sapiens), that we classify both as a party,an actor, and a jurisdiction.
I O
WebOfTrust
IAL
ToIP
See: identity assurance level.
IANA
Nist
Term found but the definition does not exist yet.WebOfTrust
IDP
ToIP
See: identity provider.
IP
ToIP
See: Internet Protocol.
IP address
ToIP
An Internet Protocol address (IP address) is a numerical label such as 192.0.2.1 that is connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: network interface identification, and location addressing.
Source: Wikipedia.
IPEX
WebOfTrust
Identification Pattern
Identifier
Identifier Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain how identifiers are defined and used for identification purposes.
Identify
Identity
Identity Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain how digital identities work, how this relates to (attributes in) credentials, and how all this can be made to work in SSI contexts.
Inception
TSWG (Keri)
the operation of creating an AID by binding it to the initial set of authoritative keypairs and any other associated information. This operation is made verifiable and Duplicity evident upon acceptance as the Inception event that begins the AIDs KEL.
Inception event
TSWG (ACDC)
an Establishment event that provides the incepting information needed to derive an AID and establish its initial Key state. See inception event.TSWG (Keri)
an Establishment event that provides the incepting information needed to derive an AID and establish its initial Key state.
Information Process
Information theoretic security
TSWG (ACDC)
the highest level of cryptographic security with respect to a cryptographic secret (seed, salt, or private key).
Interaction event
TSWG (ACDC)
a Non-establishment event that anchors external data to the Key state as established by the most recent prior Establishment event. See interaction event.TSWG (Keri)
a Non-establishment event that anchors external data to the Key state as established by the most recent prior Establishment event.
Internet Protocol
ToIP
The Internet Protocol (IP) is the network layer communications protocol in the Internet protocol suite (also known as the TCP/IP suite) for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet.
IP has the task of delivering packets from the source host to the destination host solely based on the IP addresses in the packet headers. For this purpose, IP defines packet structures that encapsulate the data to be delivered. It also defines addressing methods that are used to label the datagram with source and destination information.
Source: Wikipedia.
Also known as: IP.
See also: Transmission Control Protocol, User Datagram Protocol.
Internet protocol suite
ToIP
The Internet protocol suite, commonly known as TCP/IP, is a framework for organizing the set of communication protocols used in the Internet and similar computer networks according to functional criteria. The foundational protocols in the suite are the Transmission Control Protocol (TCP), the User Datagram Protocol (UDP), and the Internet Protocol (IP).
Source: Wikipedia
Also known as: TCP/IP.
See also: protocol stack.
Issuee
TSWG (ACDC)
a role of an entity to which the claims of an ACDC are asserted.
Issuer
Essif-Lab
a component that implements the capability to construct credential from data objects, according to the content of its principal's issuer-Policy (specifically regarding the way in which the credential is to be digitally signed), and pass it to the wallet-component of its principal allowing it to be issued.TSWG (ACDC)
a role of an entity that asserts claims and creates an ACDC from these claims.
Isuer Policy
Essif-Lab
a digital policy that enables an operational issuer component to function in accordance with the objective of its principal.
JOSE
Nist
Term found but the definition does not exist yet.WebOfTrust
JSON
Nist
Term found but the definition does not exist yet.WebOfTrust
JSON
Definition
JavaScript Object Notation. JSON is a language-independent data format. It was derived from JavaScript. It's an open standard file format and data interchange format that uses human-readable text to store and transmit data objects consisting of attribute–value pairs and arrays (or other serializable values).
More on source Wikipedia
Jurisdiction
Essif-Lab
the composition of a legal system (legislation, enforcement thereof, and conflict resolution), a party that governs that legal system, a scope within which that legal system is operational, and one or more objective for the purpose of which the legal system is operated. See also the Jurisdictions pattern.
Jurisdiction Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain what a generic jurisdiction consists of, and relates it to parties and legal entities.
KA2CE
WebOfTrust
KAACE
WebOfTrust
KAPI
WebOfTrust
KAPI
Definition
Application programmer interfaces (APIs) for the various components in the KERI ecosystem such as Controllers, Agents, Witnesses, Watchers, Registrars etc need by which they can share information. The unique properties of the KERI protocol require APIs that preserve those properties. We call the set of APIs the KERI API.
Source Kapi Repo
KATE
ToIP
See: keys-at-the-edge.
KEL
WebOfTrust
KEL backed data
ToIP (DID:Webs)
KEL backed data in did:webs provides the highest level of data security assurance and such data can be found either in the KEL or anchored to an event in the KEL. This means that the signatures on the events in the KEL are strongly bound to the key state at the time the events are entered in the KEL, that is the data. This provides strong guarantees of non-duplicity to any verifiers receiving a presentation as the KELs are protected and can be watched by agents (watcher) of the verifiers. The information is end-verifiable and any evidence of duplicity in the events is evidence that the data or presentation should not be trusted. See WebOfTrust glossary for more detail.
KERI
ToIP
WebOfTrust
KERI Request Authentication Mechanism
ToIP (DID:Webs)
A non-interactive replay attack protection algorithm that uses a sliding window of date-time stamps and key state (similar to the tuple in BADA-RUN) but the date-time is the repliers not the queriers. KRAM is meant to protect a host. See the WebOfTrust glossary for more detail.
KERI event stream
ToIP (DID:Webs)
A stream of verifiable KERI data, consisting of the key event log (KEL) and other data such as a transaction event log (TEL). This data is a CESR event stream, with media type application/cesr, and may be serialized in a file using CESR encoding. We refer to these CESR stream resources as KERI event streams to simplify the vocabulary. See WebOfTrust glossary for more detail.
KERIMask
WebOfTrust
KERIMask
Definition
A wallet similar to MetaMask, the manifestation will be a browser extension and it will connect to KERIA servers in order for a person to control AIDs from their browser.
Status
As of October 2023 KERIMask is only planned.
Related
KERISSE
WebOfTrust
KERIs Algorithm for Witness Agreement
TSWG (Keri)
a type of Byzantine Fault Tolerant (BFT) algorithm
KERL
WebOfTrust
KID
WebOfTrust
KMS
ToIP
See: key management system.
KRAM
WebOfTrust
Key Event Receipt Infrastructure
ToIP
A decentralized permissionless key management architecture.
Also known as: KERI.
For more information, see: https://keri.one/, ToIP ACDC Task Force
Key Event Receipt Infrastructure (KERI)
TSWG (CESR)
or the KERI protocol, is an identity system-based secure overlay for the Internet.
Key event
TSWG (Keri)
concretely, the serialized data structure of an entry in the Key event log (KEL) for an AID. Abstractly, the data structure itself. Key events come in different types and are used primarily to establish or change the authoritative set of keypairs and/or anchor other data to the authoritative set of keypairs at the point in the KEL actualized by a particular entry.
Key event log
TSWG (Keri)
a Verifiable data structure that is a backward and forward chained, signed, append-only log of key events for an AID. The first entry in a KEL must be the one and only Inception event of that AID.
Key event message
TSWG (Keri)
message whose body is a Key event and whose attachments may include signatures on its body.
Key event receipt
TSWG (Keri)
message whose body references a Key event and whose attachments must include one or more signatures on that Key event.
Key event receipt log
TSWG (Keri)
a key event receipt log is a KEL that also includes all the consistent key event receipt Messages created by the associated set of witnesses. See annex Key event receipt log
Key-State
TSWG (Keri)
a set of authoritative keys for an AID along with other essential information necessary to establish, evolve, verify, and validate control-signing authority for that AID. This information includes the current public keys and their thresholds (for a multi-signature scheme); pre-rotated key digests and their thresholds; witnesses and their thresholds; and configurations. An AIDs key state is first established through its inception event and may evolve via subsequent rotation events. Thus, an AIDs key state is time-dependent.
Key-state
TSWG (ACDC)
a set of currently authoritative keypairs for an AID and any other information necessary to secure or establish control authority over an AID. This includes current keys, prior next key digests, current thresholds, prior next thresholds, witnesses, witness thresholds, and configurations. A key-state of an AID is first established through an inception event and may be altered by subsequent rotation events. See validator.
Knowledge
LEI
ToIP
See: Legal Entity Identifier.
WebOfTrust
LEI
Definition
Legal Entity Identifier
LID
WebOfTrust
LLM
WebOfTrust
LLM
See Large Language Model
Laws of Identity
ToIP
A set of seven “laws” written by Kim Cameron, former Chief Identity Architect of Microsoft (1941-2021), to describe the dynamics that cause digital identity systems to succeed or fail in various contexts. His goal was to define the requirements for a unifying identity metasystem that can offer the Internet the identity layer it needs.
For more information, see: https://www.identityblog.com/?p=352.
Layer 1
ToIP
See: ToIP Layer 1.
Layer 2
ToIP
See: ToIP Layer 2.
Layer 3
ToIP
See: ToIP Layer 3.
Layer 4
ToIP
See: ToIP Layer 4.
Legal Entity
Essif-Lab
an entity that is known by, recognized to exist, and registered in that jurisdiction.
Legal Entity Identifier
ToIP
The Legal Entity Identifier (LEI) is a unique global identifier for legal entities participating in financial transactions. Also known as an LEI code or LEI number, its purpose is to help identify legal entities on a globally accessible database. Legal entities are organisations such as companies or government entities that participate in financial transactions.
Source: Wikipedia.
Note: LEIs are administered by the Global Legal Entity Identifier Foundation (GLEIF).
Legal Jurisdiction
Essif-Lab
a jurisdiction that is governed/operated by a governmental body.
Legal System
Essif-Lab
a system in which rules are defined, and mechanisms for their enforcement and conflict resolution are (implicitly or explicitly) specified.
Live-Attack
TSWG (Keri)
an attack that compromises either the current signing keys used to sign non-establishment events or the current pre-rotated keys needed to sign a subsequent establishment event. See (Security Properties of Prerotation)[#live-attacks].
LoA
WebOfTrust
LoC
WebOfTrust
MFA
Nist
Authentication using two or more factors to achieve authentication. Factors include: (i) something you know (e.g., password/personal identification number [PIN]); (ii) something you have (e.g., cryptographic identification device, token); or (iii) something you are (e.g., biometric).WebOfTrust
MIME type
WebOfTrust
MPC
ToIP
See: multi-party computation.
Management
Mandate
Mandates, Delegation and Hiring Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain the ideas behind Mandating, Delegating, Hiring and their relations.
Mental Model
Essif-Lab
a description, both casual and formal, of a set of concept (ideas), relations between them, and constraints, that together form a coherent and consistent 'viewpoint', or 'way of thinking' about a certain topic.
Mental Model Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain how to create, maintain and use (decentralized) vocabularies (terminologies) that groups of people can use for the specific purposes they pursue.
Message
TSWG (CESR)
consists of a serialized data structure that comprises its body and a set of serialized data structures that are its attachments. Attachments may include but are not limited to signatures on the body.TSWG (Keri)
a serialized data structure that comprises its body and a set of serialized data structures that are its attachments. Attachments may include but are not limited to signatures on the body.
Mission
NFT
Nist
An owned, transferable, and indivisible data record that is a digital representation of a physical or virtual linked asset. The data record is created and managed by a smart contract on a blockchain.WebOfTrust
Next threshold
TSWG (Keri)
represents the number or fractional weights of signatures from the given set of next keys required to be attached to a Message for the Message to be considered fully signed.
Non-establishment event
TSWG (Keri)
a Key event that does not change the current Key state for an AID. Typically, the purpose of a Non-establishment event is to anchor external data to a given Key state as established by the most recent prior Establishment event for an AID.
Normative framework
Essif-Lab
a set of rules that are followed and/or criteria that remain fulfilled by (a specific kind of) entities whose behavior and/or properties are characterized as 'normal'.
OOBI
ToIP
See: out-of-band introduction.
WebOfTrust
OOR
WebOfTrust
Objective
Obligation
Onboarding
Essif-Lab
a process that is run for a specific (set of) actor on behalf of a specific party, that terminates successfully if and only if the party has (a) established the suitability of the actor for executing certain kinds of action on its behalf, (b) ensured that their mutual rights and duties are properly specified and will be appropriately enforced, and (c) provided the circumstances/contexts within which the actor is enabled to do so.
OpenWallet Foundation
ToIP
A non-profit project of the Linux Foundation chartered to build a world-class open source wallet engine.
See also: Decentralized Identity Foundation, ToIP Foundation.
For more information, see: https://openwallet.foundation/
Operator
TSWG (ACDC)
an optional field map in the Edge section that enables expression of the edge logic on edge subgraph as either a unary operator on the edge itself or an m-ary operator on the edge-group.
Organization
Outsourcing
Essif-Lab
the state of affairs in which a party has an objective (better: an expectation) for the realization of a (set of) result(s), where the actual production of these results is expected to be done by a party other than itself.
Owned
Essif-Lab
an entity over which another entity (its owner) has the power (duty, right) to enjoy it, dispose of it and control it; that power is limited to (the scope of) that jurisdiction, and by its rules.
Owner
Ownership
Essif-Lab
a relationship between two entities that exists within the scope of control of a jurisdiction, in which one of them (called the owner) has legal, rightful or natural rights and/or duties to enjoy, dispose of, and control the other (called the owned).
P2P
Nist
Term found but the definition does not exist yet.ToIP
See: peer-to-peer.
WebOfTrust
PGP
Nist
Term found but the definition does not exist yet.WebOfTrust
PID
WebOfTrust
PII
ToIP
PKI
Nist
The architecture, organization, techniques, practices, and procedures that collectively support the implementation and operation of a certificate-based public key cryptographic system. Framework established to issue, maintain, and revoke public key certificates.ToIP
WebOfTrust
PRNG
Nist
A deterministic computational process that has one or more inputs called "seeds", and it outputs a sequence of values that appears to be random according to specified statistical tests. A cryptographic PRNG has the additional property that the output is unpredictable, given that the seed is not known.WebOfTrust
PRNG
Definition
means "Pseudorandom Number Generator" which means that a sequence of numbers (bits, bytes...) is produced from an algorithm which looks random, but is in fact deterministic (the sequence is generated from some unknown internal state), hence pseudorandom.
Such pseudorandomness can be cryptographically secure, or not. It is cryptographically secure if nobody can reliably distinguish the output from true randomness, even if the PRNG algorithm is perfectly known (but not its internal state). A non-cryptographically secure PRNG would fool basic statistical tests but can be distinguished from true randomness by an intelligent attacker.
(Source: https://crypto.stackexchange.com/questions/12436/what-is-the-difference-between-csprng-and-prng)See also
PTEL
WebOfTrust
Partial Disclosure
TSWG (ACDC)
a disclosure of an ACDC that partially discloses its field maps using Compact Disclosure. The Compact Disclosure provides a cryptographically equivalent commitment to the yet-to-be-disclosed content, and later exchange of the uncompacted content is verifiable to an earlier Partial Disclosure. Unlike Selective dDsclosure, a partially disclosable field becomes correlatable to its encompassing block after its Full Disclosure.
Partial identity
Participant
Essif-Lab
a party is negotiating (or has negotiated) a transaction agreement.
Party
Party Representation Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain how parties can be represented in various circumstances.
Party, Actor and Actions Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain how things get done. It answers questions such as: 'Who/what does things?', 'How are their actions being guided/controlled?', 'Who controls whom/what?', 'Who/what may be held accountable?'.
Pattern
Essif-Lab
a description, both casual and formal, of a set of concept (ideas), relations between them, and constraints, that together form a coherent and consistent 'viewpoint', or 'way of thinking' about a certain topic.
Peer Actor
Essif-Lab
Peer Party
Essif-Lab
a party that also participates in that business transaction.
Peer-agent
Essif-Lab
Percolated discovery
TSWG (ACDC)
a discovery mechanism for information associated with an AID or a SAID, which is based on Invasion Percolation Theory. Once an entity has discovered such information, it may in turn share what it discovers with other entities. Since the information so discovered is end-verifiable, the percolation mechanism and percolating intermediaries do not need to be trusted.
Perfect security
TSWG (ACDC)
a special case of Information theoretic security ITPS
PoP
ToIP
See: proof of personhood.
Policy
Presentation
Essif-Lab
a (signed) digital message that a holder component may send to a verifier component that contains data derived from one or more verifiable credential (that (a colleague component of) the holder component has received from issuer components of one or more parties), as a response to a specific presentation request of a Verifier component.
Presentation Request
Essif-Lab
a (signed) digital message that a verifier component sends to a holder component asking for specific data from one or more verifiable credential that are issued by specific Parties.
Primitive
TSWG (ACDC)
a serialization of a unitary value. All Primitives in KERI must be expressed in CESR.TSWG (CESR)
a serialization of a unitary value. All Primitives in KERI must be expressed in CESR.
Primitive:
TSWG (Keri)
a serialization of a unitary value. All Primitives in KERI must be expressed in CESR [1].
Principal
Principles of SSI
ToIP
A set of principles for self-sovereign identity systems originally defined by the Sovrin Foundation and republished by the ToIP Foundation.
For more information, see: https://sovrin.org/principles-of-ssi/ and https://trustoverip.org/wp-content/uploads/2021/10/ToIP-Principles-of-SSI.pdf
Property (of a Concept)
QAR
WebOfTrust
QR code
ToIP
A QR code (short for "quick-response code") is a type of two-dimensional matrix barcode—a machine-readable optical image that contains information specific to the identified item. In practice, QR codes contain data for a locator, an identifier, and web tracking.
Source: Wikipedia.
See also: out-of-band introduction.
QVI
WebOfTrust
Quadlet
TSWG (CESR)
a group of 4 characters in the T domain and equivalently in triplets of 3 bytes each in the B domain used to define variable size.
Qualified Data
RBAC
ToIP
RID
Nist
Term found but the definition does not exist yet.WebOfTrust
RUN
WebOfTrust
RUN
Definition
The acronym for the new peer-to-peer end-verifiable monotonic update policy is RUN (Read, Update, Nullify).
RUN as opposed to CRUD which is the traditional client-server database update policy.
OOBI related
We RUN off the CRUD, which means that because the source of truth for each data item is a decentralized controller Peer, a given database hosted by any Peer does not create records in the traditional sense of a server creating records for a client.
RWI
ToIP
See: real world identity.
Relation (between Concepts)
Essif-Lab
a (significant) connection or association between two or more concepts.
Revocation Policy
Essif-Lab
a digital policy that enables an operational revocation component to function in accordance with the objective of its principal.
Revocation component
Essif-Lab
a component that implements the capability to revoke credential that are issued by its principal, according to its principal revocation policy.
Revoke/Revocation
Essif-Lab
the act, by or on behalf of the party that has issued the credential, of no longer vouching for the correctness or any other qualification of (arbitrary parts of) that credential.
Risk
Risk Objective
Risk Owner
Risk level
Risk management
Essif-Lab
a process that is run by (or on behalf of) a specific party for the purpose of managing the risk that it owns (thereby realizing specific risk objectives).
Role
Essif-Lab
a defined set of characteristics that an entity has in some context, such as responsibilities it may have, action (behaviors) it may execute, or pieces of knowledge that it is expected to have in that context, which are referenced to by a specific role name.
Role name
Essif-Lab
name (text) that refers to (and identifies) a role in a specific context.
Rotation
TSWG (Keri)
the operation of revoking and replacing the set of authoritative keypairs for an AID. This operation is made verifiable and Duplicity evident upon acceptance as a Rotation event that is appended to the AIDs KEL.
Rotation event
TSWG (ACDC)
an Establishment Event that provides the information needed to change the Key state which includes a change to the set of authoritative keypairs for an AID. See rotation event.TSWG (Keri)
an Establishment Event that provides the information needed to change the Key state which includes a change to the set of authoritative keypairs for an AID.
Rules
TSWG (ACDC)
a top-level field map within an ACDC that provides a legal language as a Ricardian Contract [43], which is both human and machine-readable and referenceable by a cryptographic digest.
SAD
Nist
Term found but the definition does not exist yet.WebOfTrust
SAID
WebOfTrust
SATP
WebOfTrust
SCID
ToIP
WebOfTrust
SEMVER
TSWG (ACDC)
Semantic Versioning Specification 2.0. See also (https://semver.org)[https://semver.org]
SKRAP
WebOfTrust
SKWA
WebOfTrust
SPAC
WebOfTrust
SSI
Nist
Term found but the definition does not exist yet.ToIP
See: self-sovereign identity.
Note: In some contexts, such as academic papers or industry conferences, this acronym has started to replace the term it represents.
WebOfTrust
SSI (Self-Sovereign Identity)
Essif-Lab
sSI (Self-Sovereign Identity) is a term that has many different interpretations, and that we use to refer to concepts/ideas, architectures, processes and technologies that aim to support (autonomous) parties as they negotiate and execute electronic transaction with one another.
SSI Agent
Essif-Lab
a digital agent that provides one or more of the ssi functionalities (issuer, holder, verifier, wallet) to its principal.
SSI Assurance Community (SSI-AC)
Essif-Lab
a community that supports its members as they seek to increase their confidence in the SSI infrastructure and/or (specific) qualifications of the data exchanged through that infrastructure.
SSI Infrastructure
Essif-Lab
the technological components that are (envisaged to be) all over the world for the purpose of providing, requesting and obtaining qualified data, for the purpose of negotiating and/or executing electronic transaction.
SSL
ToIP
See: Secure Sockets Layer.
Salt
TSWG (Keri)
random data fed as an additional input to a one-way function that hashes data.
Schema
TSWG (ACDC)
the SAID of a JSON schema that is used to issue and verify an ACDC.
Scope
Essif-Lab
the extent of the area or subject matter (which we use, e.g., to define pattern, concept, term and glossaries in, but it serves other purposes as well).
Scope of Control
Scope: essifLabTerminology
Essif-Lab
specification of the eSSIF-Lab scope.
Seal
TSWG (Keri)
a seal is a cryptographic commitment in the form of a cryptographic digest or hash tree root (Merkle root) that anchors arbitrary data or a tree of hashes of arbitrary data to a particular event in the key event sequence. See annex (Seal)[#seal].
Secure Enclave
ToIP
A coprocessor on Apple iOS devices that serves as a trusted execution environment.
Secure Sockets Layer
ToIP
The original transport layer security protocol developed by Netscape and partners. Now deprecated in favor of Transport Layer Security (TLS).
Also known as: SSL.
Selective Disclosure
TSWG (ACDC)
a disclosure of an ACDC that selectively discloses its attributes using Compact Disclosure. The set of selectively disclosable attributes is provided as an array of blinded blocks where each attribute in the set has its own dedicated blinded block. Unlike Partial Disclosure, the selectively disclosed fields are not correlatable to the so far undisclosed but selectively disclosable fields in the same encompassing block.
Self-Addressing Identifier (SAID)
TSWG (ACDC)
any identifier which is deterministically generated out of the content, digest of the content.
Self-Framing
TSWG (CESR)
a textual or binary encoding that begins with type, size, and value so that a parser knows how many characters (when textual) or bytes (when binary) to extract from the stream for a given element without parsing the rest of the characters or bytes in the element is Self-Framing. A self-framing Primitive may be extracted without needing any additional delimiting characters. Thus, a stream of concatenated Primitives may be extracted without the need to encapsulate each Primitive inside a set of delimiters or an envelope.
Self-Sovereign Identity (SSI)
Essif-Lab
self-Sovereign Identity (SSI) is a term that has many different interpretations, and that we use to refer to concepts/ideas, architectures, processes and technologies that aim to support (autonomous) parties as they negotiate and execute electronic transaction with one another.
Self-Sovereignty
Self-addressed data
TSWG (Keri)
a representation of data content from which a SAID is derived. The SAID is both cryptographically bound to (content-addressable) and encapsulated by (self-referential) its SAD SAID.
Self-addressing identifiers
TSWG (Keri)
an identifier that is content-addressable and self-referential. A SAID is uniquely and cryptographically bound to a serialization of data that includes the SAID as a component in that serialization SAID.
Self-certifying identifier
TSWG (Keri)
a type of Cryptonym that is uniquely cryptographically derived from the public key of an asymmetric signing keypair, (public, private).
Semantic Unit
Semantics
Semantics Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain the relations between the (intangible) concepts (and other semantic units) that are part of a party's knowledge, and how they are (tangibly) represented by terms, attributes, etc.
Sovrin Foundation
ToIP
A 501 (c)(4) nonprofit organization established to administer the governance framework governing the Sovrin Network, a public service utility enabling self-sovereign identity on the internet. The Sovrin Foundation is an independent organization that is responsible for ensuring the Sovrin identity system is public and globally accessible.
For more information, see: https://sovrin.org/
Stable
TSWG (CESR)
todo
Stream
TSWG (ACDC)
a CESR Stream is any set of concatenated Primitives, concatenated groups of Primitives or hierarchically composed groups of Primitives.TSWG (CESR)
any set of concatenated Primitives, concatenated groups of Primitives or hierarchically composed groups of Primitives.
Subject
Essif-Lab
the (single) entity to which a given set of coherent data relates/pertains. Examples of such sets include attributes, Claims/Assertions, files/dossiers, (verifiable) credentials, (partial) identities, employment contracts, etc.
Sybil attack
ToIP
A Sybil attack is a type of attack on a computer network service in which an attacker subverts the service's reputation system by creating a large number of pseudonymous identities and uses them to gain a disproportionately large influence. It is named after the subject of the book Sybil, a case study of a woman diagnosed with dissociative identity disorder.
Source: Wikipedia.
TCP
Nist
TCP is one of the main protocols in TCP/IP networks. Whereas the IP protocol deals only with packets, TCP enables two hosts to establish a connection and exchange streams of data. TCP guarantees the delivery of data and also guarantees that packets will be delivered in the same order in which they were sent.ToIP
WebOfTrust
TCP/IP
ToIP
See: Internet Protocol Suite.
TCP/IP stack
ToIP
The protocol stack implementing the TCP/IP suite.
TEE
Nist
An area or enclave protected by a system processor.ToIP
WebOfTrust
TEL
WebOfTrust
TLS
ToIP
See: Transport Layer Security.
TOAD
WebOfTrust
TPM
Nist
Term found but the definition does not exist yet.WebOfTrust
TSP
Nist
Term found but the definition does not exist yet.ToIP
WebOfTrust
TTA
ToIP
TTP
ToIP
See: trusted third party.
Tag
Essif-Lab
an alphanumeric string that is used to identify scope (so called 'scopetags'), group term (so called 'grouptags'), or identify a specific version of a terminology (so called 'versiontags') from within a specific scope.
Targeted ACDC
TSWG (ACDC)
an ACDC with the presence of the Issuee field in the attribute or attribute aggregate sections.
Term
Term (Scoped)
Essif-Lab
a term, the meaning of which is determined by the definition to which it refers in a specific scope/context.
Terminology
Essif-Lab
the set of term that are used within a single scope to refer to a single definition, enabling parties to reason and communicate ideas they have about one or more specific topics.
Terminology Pattern
Essif-Lab
a set of concepts and other semantic units that one can use to explain one's thinking about a certain topic, as well as to devise/design a way of thinking that members of a community can use to align their thinking as they pursue that community's objectives.
Terminology Process
Essif-Lab
a method for recognizing misunderstandings as such, and creating or maintaining definition that resolve them.
Terms Community
Essif-Lab
a community that maintains a terminology for the purpose of avoiding misunderstandings between its members as they collaborate.
ToIP
ToIP
See: Trust Over IP
ToIP Foundation
ToIP
A non-profit project of the Linux Foundation chartered to define an overall architecture for decentralized digital trust infrastructure known as the ToIP stack.
See also: Decentralized Identity Foundation, OpenWallet Foundation.
For more information, see: https://trustoverip.org/.
ToIP Governance Architecture Specification
ToIP
The specification defining the requirements for the ToIP Governance Stack published by the ToIP Foundation.
For more information, see: https://trustoverip.org/our-work/deliverables/.
ToIP Governance Metamodel
ToIP
A structural model for ToIP governance frameworks that specifies the recommended governance documents that should be included depending on the objectives of the trust community.
ToIP Governance Stack
ToIP
The governance half of the four layer ToIP stack as defined by the ToIP Governance Architecture Specification.
See also: ToIP Technology Stack.
ToIP Layer 1
ToIP
The trust support layer of the ToIP stack, responsible for supporting the trust spanning protocol at ToIP Layer 2.
ToIP Layer 2
ToIP
The trust spanning layer of the ToIP stack, responsible for enabling the trust task protocols at ToIP Layer 3.
ToIP Layer 3
ToIP
The trust task layer of the ToIP stack, responsible for enabling trust applications at ToIP Layer 4.
ToIP Layer 4
ToIP
The trust application layer of the ToIP stack, where end users have the direct human experience of using applications that call trust task protocols to engage in trust relationships and make trust decisions using ToIP decentralized digital trust infrastructure.
ToIP Technology Architecture Specification
ToIP
The technical specification defining the requirements for the ToIP Technology Stack published by the ToIP Foundation.
For more information: ToIP Technology Architecture Specification.
ToIP Technology Stack
ToIP
The technology half of the four layer ToIP stack as defined by the ToIP Technology Architecture Specification.
See also: ToIP Governance Stack, ToIP layer.
ToIP Trust Registry Protocol
ToIP
The open standard trust task protocol defined by the ToIP Foundation to perform the trust task of querying a trust registry. The ToIP Trust Registry Protocol operates at Layer 3 of the ToIP stack.
ToIP Trust Spanning Protocol
ToIP
The ToIP Layer 2 protocol for verifiable messaging that implements the trust spanning layer of the ToIP stack. The ToIP Trust Spanning Protocol enables actors in different digital trust domains to interact in a similar way to how the Internet Protocol (IP) enables devices on different local area networks to exchange data.
Mental model: hourglass model, see the Design Principles for the ToIP Stack.
For more information, see: Section 7.3 of the ToIP Technology Architecture Specification and the Trust Spanning Protocol Task Force.
ToIP application
ToIP
A trust application that runs at ToIP Layer 4, the trust application layer.
ToIP channel
ToIP
See: VID relationship.[c]
ToIP communication
ToIP
Communication that uses the ToIP stack to deliver ToIP messages between ToIP endpoints, optionally using intermediary systems[d][e], to provide authenticity, confidentiality, and correlation privacy.
ToIP connection
ToIP
A connection formed using the ToIP Trust Spanning Protocol between two ToIP endpoints identified with verifiable identifiers. A ToIP connection is instantiated as one or more VID relationships.
ToIP controller
ToIP
The controller of a ToIP identifier.
ToIP endpoint
ToIP
An endpoint that communicates via the ToIP Trust Spanning Protocol as described in the ToIP Technology Architecture Specification.
ToIP governance framework
ToIP
A governance framework that conforms to the requirements of the ToIP Governance Architecture Specification.
ToIP identifier
ToIP
A verifiable identifier for an entity that is addressable using the ToIP stack.
See also: autonomous identifier, decentralized identifier.
For more information, see: Section 6.4 of the ToIP Technology Architecture Specification.
ToIP intermediary
ToIP
See: intermediary system.
ToIP layer
ToIP
One of four protocol layers in the ToIP stack. The four layers are ToIP Layer 1, ToIP Layer 2, ToIP Layer 3, and ToIP Layer 4.
For more information, see: ToIP Technology Architecture Specification, ToIP Governance Architecture Specification.
ToIP message
ToIP
A message communicated between ToIP endpoints using the ToIP stack.
ToIP stack
ToIP
The layered architecture for decentralized digital trust infrastructure defined by the ToIP Foundation. The ToIP stack is a dual stack consisting of two halves: the ToIP Technology Stack and the ToIP Governance Stack. The four layers in the ToIP stack are ToIP Layer 1, ToIP Layer 2, ToIP Layer 3, and ToIP Layer 4.
For more information, see: ToIP Technology Architecture Specification, ToIP Governance Architecture Specification.
ToIP system
ToIP
A computing system that participates in the ToIP Technology Stack. There are three types of ToIP systems: endpoint systems, intermediary systems, and supporting systems.
For more information, see: Section 6.3 of the ToIP Technology Architecture Specification.
ToIP trust community
ToIP
A trust community governed by a ToIP governance framework.
ToIP trust network
ToIP
A trust network implemented using the ToIP stack.
Transaction
Essif-Lab
the exchange of goods, services, funds, or data between some parties (called participant of the transaction).
Transaction Agreement
Essif-Lab
the set of rules that specify the rights (expectation) and duties (obligation) of participant towards one another in the context of a specific business transaction.
Transaction Form
Essif-Lab
the specification of the set of data that this party needs to (a) commit to a (proposed) business transaction of that kind, (b) fulfill its duties/obligation and (c) escalate if necessary.
Transaction Id
Essif-Lab
character string that this participant uses to identify, and refer to, that business transaction.
Transaction Proposal
Essif-Lab
a transaction agreement that is 'in-the-making' (ranging from an empty document to a document that would be a transaction agreement if it were signed by all participant).
Transaction Request
Essif-Lab
a message, send by a requesting party to a providing party, that initiates the negotiation of a new transaction agreement between these parties for the provisioning of a specific product or service.
Transmission Control Protocol
ToIP
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered, and error-checked delivery of a stream of octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the Transport Layer of the TCP/IP suite. SSL/TLS often runs on top of TCP.
Source: Wikipedia.
Also known as: TCP.
See also: User Datagram Protocol.
Transport Layer Security
ToIP
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and Voice over IP, but its use in securing HTTPS remains the most publicly visible. The TLS protocol aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of certificates, between two or more communicating computer applications.
Source: Wikipedia.
Also known as: TLS.
Note: TLS replaced the deprecated Secure Sockets Layer (SSL) protocol.
Tritet
TSWG (CESR)
3 bits. See Performant resynchronization with unique start bits
Trust
Essif-Lab
the (un)conscious decision by a party to believe that X is in fact the case.
Trust Pattern
Essif-Lab
a set of concepts and other semantic units that can be used to explain how the concept of trust relates to parties that do the trusting, and other concepts that express what it is that these parties trust.
Trust level
Essif-Lab
the (subjective) degree of belief or confidence that a party has in X (someone, something, ...).
Trust over IP
ToIP
A term coined by John Jordan to describe the decentralized digital trust infrastructure made possible by the ToIP stack. A play on the term Voice over IP (abbreviated VoIP).
Also known as: ToIP.
UDP
ToIP
See: User Datagram Protocol.
UI
Nist
The physical or logical means by which users interact with a system, device or process.WebOfTrust
URL
Nist
A uniform resource locator, or URL, is a short string containing an address which refers to an object in the "web." URLs are a subset of URIs.WebOfTrust
Uniform Resource Identifier (URI)
W3C (DID)
The standard identifier format for all resources on the World Wide Web asdefined by [RFC3986]. A DID is a type of URI scheme.
Universally Unique Identifier (UUID)
W3C (DID)
A type of globally unique identifier defined by [RFC4122]. UUIDs are similarto DIDs in that they do not require a centralized registration authority. UUIDsdiffer from DIDs in that they are not resolvable orcryptographically-verifiable.
Unpermissioned correlation
TSWG (ACDC)
a correlation established between two or more disclosed ACDCs whereby the discloser of the ACDCs does not permit the disclosee to establish such a correlation.
Untargeted ACDC
TSWG (ACDC)
an ACDC without the presence of the Issuee field in the attribute or attribute aggregate sections.
User Datagram Protocol
ToIP
In computer networking, the User Datagram Protocol (UDP) is one of the core communication protocols of the Internet protocol suite used to send messages (transported as datagrams in packets) to other hosts on an Internet Protocol (IP) network. Within an IP network, UDP does not require prior communication to set up communication channels or data paths.
Source: Wikipedia.
Also known as: UDP.
VC
Nist
Term found but the definition does not exist yet.ToIP
See: verifiable credential.
WebOfTrust
VC TEL
WebOfTrust
VDS
Nist
Term found but the definition does not exist yet.WebOfTrust
VID
ToIP
WebOfTrust
VID relationship
ToIP
The communications relationship formed between two VIDs using the ToIP Trust Spanning Protocol. A particular feature of this protocol is its ability to establish as many VID relationships as needed to establish different relationship contexts between the communicating entities.
VID-to-VID
ToIP
The specialized type of peer-to-peer communications enabled by the ToIP Trust Spanning Protocol. Each pair of VIDs creates a unique VID relationship.
Validate
Validator
Essif-Lab
a component that implements the capability to determine whether or not (verified) data is valid to be used for some specific purpose(s).TSWG (ACDC)
any entity or agent that evaluates whether or not a given signed statement as attributed to an identifier is valid at the time of its issuance. See validator.TSWG (Keri)
any entity or agent that evaluates whether or not a given signed statement as attributed to an identifier is valid at the time of its issuance.
Validator Policy
Essif-Lab
a digital policy that enables an operational validator component to function in accordance with the objective of its principal.
Variable Length
TSWG (CESR)
a type of count code allowing for vaiable size signatures or attachments which can be parsed to get the full size
Verifiable
TSWG (Keri)
a condition of a KEL: being internally consistent with integrity of its backward and forward chaining digest as well as authenticity of its non-repudiable signatures.
Verifiable data registry
TSWG (ACDC)
A role a system might perform by mediating issuance and verification of ACDCs. See verifiable data registry.
Verifier
Essif-Lab
a component that implements the capability to request peer agents to present (provide) data from credentials (of a specified kind, issued by specified parties), and to verify such responses (check structure, signatures, dates), according to its principal's verifier policy.TSWG (ACDC)
any entity or agent that cryptographically verifies the signature(s) and/or digests on an event Message. See verifier.TSWG (Keri)
any entity or agent that cryptographically verifies the signature(s) and digests on an event Message.
Verifier Policy
Essif-Lab
a digital policy that enables an operational verifier component to function in accordance with the objective of its principal.
Verify
Version
TSWG (CESR)
the CESR Version is provided by a special Count Code that specifies the Version of all the the CESR code tables in a given Stream or Stream section.TSWG (Keri)
an instance of a KEL for an AID in which at least one event is unique between two instances of the KEL
Version String
TSWG (CESR)
the first field in any top-level KERI field map in which it appears.
VoIP
ToIP
See: Voice over IP.
Vocabulary
Essif-Lab
the sum or stock of words employed by a language, group, individual, or work or in a field of knowledge.
Voice over IP
ToIP
Voice over Internet Protocol (VoIP), also called IP telephony, is a method and group of technologies for voice calls for the delivery of voice communication sessions over Internet Protocol (IP) networks, such as the Internet.
Also known as: VoIP.
W3C Verifiable Credentials Data Model Specification
ToIP
A W3C Recommendation defining a standard data model and representation format for cryptographically-verifiable digital credentials. Version 1.1 was published on 03 March 2022.
For more information, see: https://www.w3.org/TR/vc-data-model/
Wallet
Essif-Lab
a component that implements the capability to securely store data as requested by colleague agents, and to provide stored data to colleague agents or peer agents, all in compliance with the rules of its principal's wallet policy.
Wallet Policy
Essif-Lab
a digital policy that enables an operational wallet component to function in accordance with the objective of its principal.
Watcher
TSWG (Keri)
an entity or component that keeps a copy of a KERL for an identifier but that is not designated by the controller of the identifier as one of its witnesses. See annex watcher
Weight
TSWG (ACDC)
an optional field map in the Edge section that provides edge weight property that enables directed weighted edges and operators that use weights.
Witness
TSWG (Keri)
a witness is an entity or component designated (trusted) by the controller of an identifier. The primary role of a witness is to verify, sign, and keep events associated with an identifier. A witness is the controller of its own self-referential identifier which may or may not be the same as the identifier to which it is a witness. See Annex A under KAWA (KERIs Algorithm for Witness Agreement).
XBRL
WebOfTrust
ZKP
ToIP
See: zero-knowledge proof.
[a]@christine.martin@continuumloop.com you're good to go - start moving this to a
https://github.com/trustoverip/ctwg-main-glossary
put the content in specs/terms_and_definitions.md
ping me with questions.
_Assigned to christine.martin@continuumloop.com_
[b]focus on the terms - do [[def: first, then see how many [[ref: you can get done.
[c]Christine, I had forgotten this link. Just added it now.
[d]definition no longer in document
[e]My bad. As you can tell, aligning terms with the ToIP Technology Architecture Specification was the last step I took, and when I did that, I didn't check to see where I had used the old terms. I fixed this.
access control
ToIP
The process of granting or denying specific requests for obtaining and using information and related information processing services.
Source: NIST-CSRC.
Supporting definitions:
Wikipedia: In physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.
access controlled interaction
WebOfTrust
access controlled interaction
Definition
Access controlled actions like submitting a report. If you already have that report then load balancer needs a mechanism to drop repeated requests.
Source: Samuel Smith / Daniel Hardman / Lance Byrd - Zoom meeting KERI Suite Jan 16 2024; discussion minute 30-60 min
Replay attack prevention
Replay attacks are less of a concern, other than DDoS attack using resubmissions.
Also see
account
digital.govt.nz
an instance of entity information in a contextAdditional note:Note 1: A common term for the set of entity information relating to 1 entity to which an authenticator can be registered and from which credential subject information can be taken to establish a Credential.
accountable
digital.govt.nz
responsible for some action; answerable[Source: expanded Dictionary meaning of accountable]Additional note:Note 1: For roles such as Credential Provider and Relying Party, it is the primary publicly accessible party.
accreditation (of an entity)
ToIP
The independent, third-party evaluation of an entity, by a conformity assessment body (such as certification body, inspection body or laboratory) against recognised standards, conveying formal demonstration of its impartiality and competence to carry out specific conformity assessment tasks (such as certification, inspection and testing).
Source: Wikipedia.
accreditation body
ToIP
A legal entity that performs accreditation.
See also: certification body.
action
actor
ToIP
An entity that can act (do things/execute actions), e.g. people, machines, but not organizations. A digital agent can serve as an actor acting on behalf of its principal.
Source: eSSIF-Lab.
address
ToIP
See: network address.
administering authority
ToIP
See: administering body.
administering body
ToIP
A legal entity delegated by a governing body to administer the operation of a governance framework and governed infrastructure for a digital trust ecosystem, such as one or more trust registries.
Also known as: administering authority.
affected party
digital.govt.nz
a party that could be influenced; acted upon[Source: expanded Dictionary meaning of affected]Additional note:Note 1: For identification risk, the affected parties have been identified as:Entitled individual for example, an entitled individual applies for a service and is deemed ineligible because their identity has been used previously by someone else to claim the same service.Service provider for example, an organisations reputation suffers because of publicity that the agency has been defrauded by large numbers of individuals claiming false identities.Wider community for example, identification documents are mistakenly issued to people with false identities and are then used to commit fraud against other organisations.
agency
Nist
Any executive department, military department, government corporation, government controlled corporation, or other establishment in the executive branch of the government (including the Executive Office of the President), or any independent regulatory agency, but does not include: (i) the Government Accountability Office; (ii) the Federal Election Commission; (iii) the governments of the District of Columbia and of the territories and possessions of the United States, and their various subdivisions; or (iv) government-owned contractor-operated facilities, including laboratories engaged in national defense research and production activities.
agent
digital.govt.nz
a person, firm, etc. empowered to act for another[Source: Dictionary]ToIP
An actor that is executing an action on behalf of a party (called the principal of that actor). In the context of decentralized digital trust infrastructure, the term “agent” is most frequently used to mean a digital agent.
Source: eSSIF-Lab.
See also: wallet.
Note: In a ToIP context, an agent is frequently assumed to have privileged access to the wallet(s) of its principal. In market parlance, a mobile app performing the actions of an agent is often simply called a wallet or a digital wallet.
ambient verifiability
WebOfTrust
ambient verifiability
Definition
Verifiable by anyone, anywhere, at anytime. Although this seems a pretty general term, it was first used in the context of KERI by Sam Smith.
An example of ambient verifiability is Ambient Duplicity Detection that describes the possibility of detecting duplicity by anyone, anywhere, anytime.
ample
WebOfTrust
ample
Definition
The minimum required number of participants in an event to have a supermajority so that one and only one agreement or consensus on an event may be reached. This is a critical part of the KAACE agreement algorithm (consensus) in KERI for establishing consensus between witnesses on the key state of a KERI identifier. This consensus on key state forms the basis for accountability for a KERI controller, or what a person who controls a KERI identifier may be held legally responsible for.
This supermajority is also called a sufficient majority that is labeled immune from certain kinds of attacks or faults.
From section 11.4.2.4 Immune of v2.60 of the KERI whitepaper,
Satisfaction of this constraint guarantees that at most one sufficient agreement occurs or none atall despite a dishonest controller but where at most F of the witnesses are potentially faulty.
Ample Agreement Constraint:
Can apply to either
- a group of KERI witnesses for a witnessed event or
- a group of KERI identifier controllers participating in a multi-signature group.
Problems avoided by using
ampleAmple witnesses avoids problems of accidental lockout from a multisig group which would occur if the signing threshold for the multisig group was set lower than the "ample" number of participants.
Table of minimum required, or ample, number of participants
N = Number of total participants
M = Number of participants needed to get the guarantees of "ample"Code Example
Python code implementation from keri.core.eventing.py of the
amplealgorithm used in KAACE:def ample(n, f=None, weak=True): """ Returns int as sufficient immune (ample) majority of n when n >=1 otherwise returns 0 Parameters: n is int total number of elements f is int optional fault number weak is Boolean If f is not None and weak is True then minimize m for f weak is False then maximize m for f that satisfies n >= 3*f+1 Else weak is True then find maximum f and minimize m weak is False then find maximum f and maximize m n,m,f are subject to f >= 1 if n > 0 n >= 3*f+1 (n+f+1)/2 <= m <= n-f """ n = max(0, n) # no negatives if f is None: f1 = max(1, max(0, n - 1) // 3) # least floor f subject to n >= 3*f+1 f2 = max(1, ceil(max(0, n - 1) / 3)) # most ceil f subject to n >= 3*f+1 if weak: # try both fs to see which one has lowest m return min(n, ceil((n + f1 + 1) / 2), ceil((n + f2 + 1) / 2)) else: return min(n, max(0, n - f1, ceil((n + f1 + 1) / 2))) else: f = max(0, f) m1 = ceil((n + f + 1) / 2) m2 = max(0, n - f) if m2 < m1 and n > 0: raise ValueError("Invalid f={} is too big for n={}.".format(f, n)) if weak: return min(n, m1, m2) else: return min(n, max(m1, m2))
amplification attack
W3C (DID)
A class of attack where the attacker attempts to exhaust a target system'sCPU, storage, network, or other resources by providing small, valid inputs intothe system that result in damaging effects that can be exponentially more costlyto process than the inputs themselves.
anonymous
digital.govt.nz
not easily distinguished from others or from one another because of a lack of individual features or character[Source: Dictionary]ToIP
An adjective describing when the identity of a natural person or other actor is unknown.
See also: pseudonym.
anycast
ToIP
Anycast is a network addressing and routing methodology in which a single IP address is shared by devices (generally servers) in multiple locations. Routers direct packets addressed to this destination to the location nearest the sender, using their normal decision-making algorithms, typically the lowest number of BGP network hops. Anycast routing is widely used by content delivery networks such as web and name servers, to bring their content closer to end users.
Source: Wikipedia.
anycast address
ToIP
A network address (especially an IP address) used for anycast routing of network transmissions.
append only event logs
WebOfTrust
append only event logs
Definition
Append-only is a property of computer data storage such that new data can be appended to the storage, but where existing data is immutable.
A blockchain is an example of an append-only log. The events can be transactions. Bitcoin is a well-known Append only log where the events are totally ordered and signed transfers of control over unspent transaction output.
More on Wikipedia
application programming interface
WebOfTrust
application programming interface
Definition
An application programming interface (API) is a way for two or more computer programs to communicate with each other. It is a type of software interface, offering a service to other pieces of software.
API specification
A document or standard that describes how to build or use such a connection or interface is called an API specification. A computer system that meets this standard is said to implement or expose an API. The term API may refer either to the specification or to the implementation.
More on source Wikipedia.
appraisability (of a communications endpoint)
ToIP
The ability for a communication endpoint identified with a verifiable identifier to be appraised for the set of its properties that enable a relying party or a verifier to make a trust decision about communicating with that endpoint.
See also: trust basis, verifiability.
appropriate friction
architectural decision record
WebOfTrust
architectural decision record
Definition
Is a justified software design choice that addresses a functional or non-functional requirement that is architecturally significant.
Source adr.github.io
assurance
digital.govt.nz
a statement, assertion, etc. intended to inspire confidence or give encouragement[Source: Dictionary]
assurance level
ToIP
A level of confidence in a claim that may be relied on by others. Different types of assurance levels are defined for different types of trust assurance mechanisms. Examples include authenticator assurance level, federation assurance level, and identity assurance level.
attestation
ToIP
The issue of a statement, based on a decision, that fulfillment of specified requirements has been demonstrated. In the context of decentralized digital trust infrastructure, an attestation usually has a digital signature so that it is cryptographically verifiable.
Source: NIST-CSRC.
attribute
digital.govt.nz
(noun) a characteristic or quality of a person or thing[Source: Dictionary]ToIP
An identifiable set of data that describes an entity, which is the subject of the attribute.
See also: property.
Supporting definitions:
eSSIF-Lab: Data that represents a characteristic that a party (the owner of the attribute) has attributed to an entity (which is the subject of that attribute).
Note: An identifier is an attribute that uniquely identifies an entity within some context.
attribute-based access control
ToIP
An access control approach in which access is mediated based on attributes associated with subjects (requesters) and the objects to be accessed. Each object and subject has a set of associated attributes, such as location, time of creation, access rights, etc. Access to an object is authorized or denied depending upon whether the required (e.g., policy-defined) correlation can be made between the attributes of that object and of the requesting subject.
Source: NIST-CSRC.
Supporting definitions:
Wikipedia: Attribute-based access control (ABAC), also known as policy-based access control for IAM, defines an access control paradigm whereby a subject's authorization to perform a set of operations is determined by evaluating attributes associated with the subject, object, requested operations, and, in some cases, environment attributes.
attributional trust
WebOfTrust
attributional trust
Definition
KERI offers cryptographic root-of-trust to establish attributional trust. In the real world you'd also need reputational trust. You can't have reputation without attributional trust.
Read more in source Universal Identifier TheoryOOBI
Out-of-band Introductions (OOBIs) to establish attributional trust, like its done with OOBIs in KERI, is not the same as the high friction costs of establishing reputational trust by going through the heavy lifting of identity assurance by a to be trusted middle-men party, like GLEIF.
audit (of system controls)
audit log
ToIP
An audit log is a security-relevant chronological record, set of records, and/or destination and source of records that provide documentary evidence of the sequence of activities that have affected at any time a specific operation, procedure, event, or device.
Source: Wikipedia.
Also known as: audit trail.
See also: key event log.
auditor (of an entity)
ToIP
The party responsible for performing an audit. Typically an auditor must be accredited.
See also: human auditable.
authentic chained data container
WebOfTrust
authentic chained data container
Definition
In brief, an ACDC or ADC proves digital data consistency and authenticity in one go. An ACDC cryptographically secures commitment to data contained, and its identifiers are self-addressing, which means they point to themselves and are also contained ìn the data.
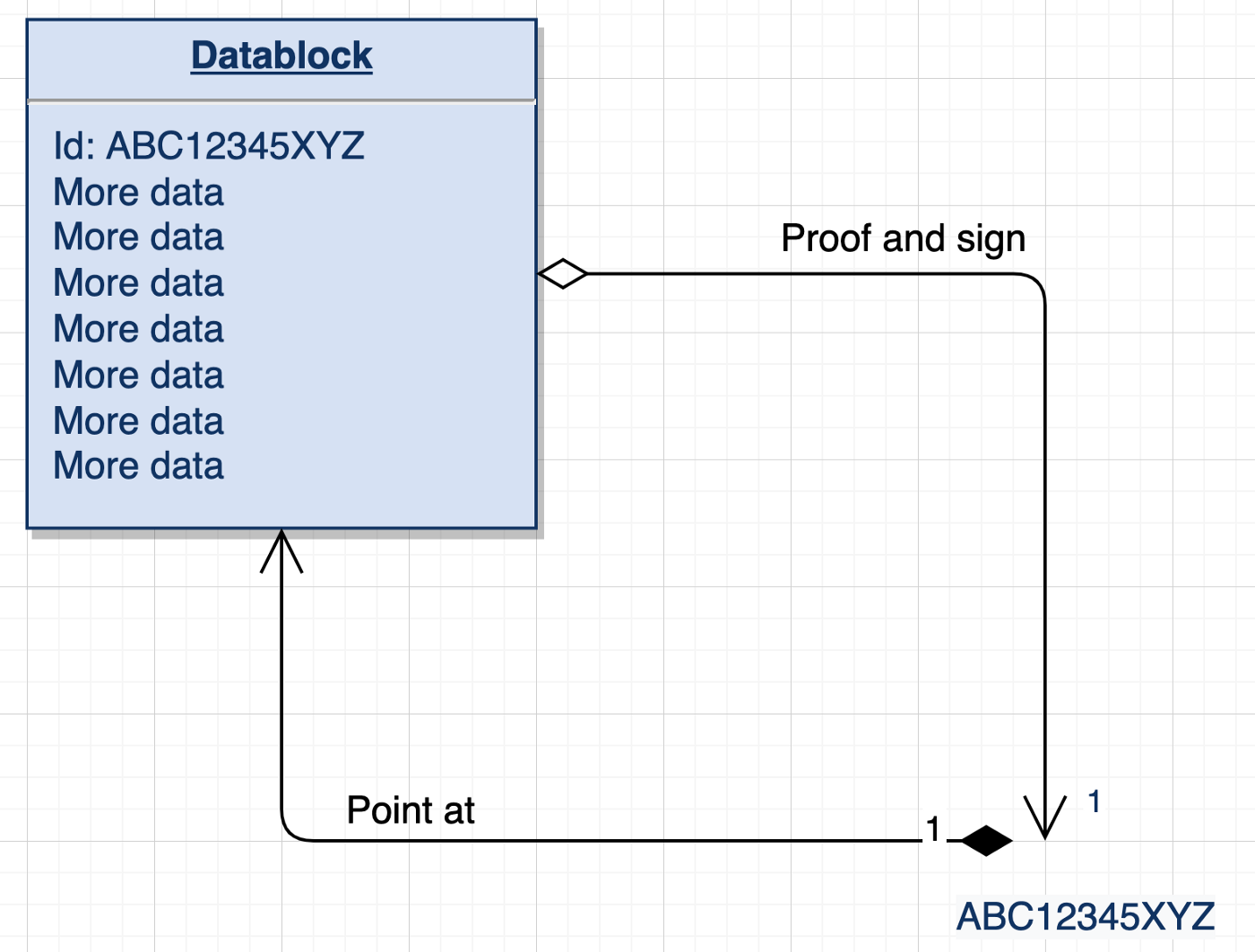
authentic chained data container (ACDC)
ToIP (DID:Webs)
a variant of the Verifiable Credential (VC) specification that inherits the security model derived from KERI, as defined by the ACDC specification. See WebOfTrust glossary for more detail.
authentic data
WebOfTrust
authentic data container
WebOfTrust
authentic data container
Definition
A mechanism for conveying data that allows the authenticity of its content to be proved.
Instance
A Verifiable Credential is an ACDC
authentic provenance chain
WebOfTrust
authentic provenance chain
Definition
Interlinked presentations of evidence that allow data to be tracked back to its origin in an objectively verifiable way.
authentic web
WebOfTrust
authentic web
Definition
The authentic web is the internet as a whole giant verifiable data structure. Also called Web5. The web will be one big graph. That's the mental model of the 'authentic web'.
Related
Signed at rest- the data never throws away any signature of data. Because otherwise we can't validate data in the futureKey state at rest- you need to solve this hard problem too. This is the hard problem KERI solves.Signed in motion- signatures get thrown away. You use ephemeral identifiers. You have to do everything anew every time you want to reconstruct a verifiable data structure. Therefore we need 'Signed at rest'.
Scalability of Key state at rest
- You can append to any part of the (directed-acyclic) graph
- You can hop into the graph to verify any fragment of the graph
- You don't have to sign the data,you just have to sign hashes of this data
- Every tree that gets integrated in this giant graph-forest has its own Root of Trust
KERI related
KERI solves all hard problems of the authentic web in a scalable manner.
Technically oriented deep dive
See more in Concepts behind KERI
authenticate
W3C (DID)
Authentication is a process by which an entity can prove it has a specificattribute or controls a specific secret using one or more verificationmethods. With DIDs, a common example would be proving control of thecryptographic private key associated with a public key published in a DIDdocument.
authentication
digital.govt.nz
process for establishing an authenticator is genuine or as represented[Source: expanded Dictionary meaning of authenticate]
authentication (of a user, process, or device)
ToIP
Verifying the identity of a user, process, or device, often as a prerequisite to allowing access to resources in an information system.
Source: NIST-CSRC.
See also: authenticator, verifiable message.
Supporting definitions:
Wikipedia: The act of proving an assertion, such as the identity of a computer system user.
authenticator
digital.govt.nz
things known and/or possessed and controlled by an entity that are used to be recognised when they return to an organisation[Source: Based on NIST SP 800-63-3 Digital Identity Guidelines]
authenticator (of an entity)
ToIP
Something the claimant possesses and controls (typically a cryptographic module or password) that is used to authenticate the claimant’s identity.
Source: NIST-CSRC.
authenticator assurance level
ToIP
A measure of the strength of an authentication mechanism and, therefore, the confidence in it.
Source: NIST-CSRC.
See also: federation assurance level, identity assurance level, identity binding.
Note: In NIST SP 800-63-3, AAL is defined in terms of three levels: AAL1 (Some confidence), AAL2 (High confidence), AAL3 (Very high confidence).
authenticator holder
digital.govt.nz
the entity to which an authenticator was initially bound; the rightful holder[Source: New definition]
authenticity
Nist
The property of being genuine and being able to be verified and trusted; confidence in the validity of a transmission, a message, or message originatorToIP
The property of being genuine and being able to be verified and trusted; confidence in the validity of a transmission, a message, or message originator.
Source: NIST-CSRC.
See also: confidentiality, correlation privacy, cryptographic verifiability.
WebOfTrust
authenticity
Definition
The quality of having an objectively verifiable origin ; contrast veracity. When a newspaper publishes a story about an event, every faithful reproduction of that story may be authentic — but that does not mean the story was true (has veracity).
Authenticity is strongly related to digital security. Ideally it should be verifiable (to a root-of-trust). The future picture therein is the Authentic Web.
KERI related
The three properties, authenticity, confidentiality, and privacy inhabit a trade space. ...One can have any two of the three (privacy, authenticity, confidentiality) at the highest level but not all three.
The trilemma insists that one must make a trade-off by prioritizing one or two properties over a third.The ToIP design goals reflect that trade-off and provide an order of importance. The design goals indicate that one should start with high authenticity, then high confidentiality, and then as high as possible privacy, given there is no trade-off with respect to the other two.
More on Source Samuel Smith SPAC whitepaper.
Also see
authoritative
digital.govt.nz
possessing or supported by authority; official[Source: Dictionary]Additional note:Note 1: Indigenous peoples, society and industry communities can nominate a party as authoritative. Its possible that such a party is subject to legal controls.WebOfTrust
authoritative
Definition
Established control authority over an identifier, that has received attestations to it, e.g. control over the identifier has been verified to its root-of-trust. So the (control over the) identifier is 'authoritative' because it can be considered accurate, renowned, honourable and / or respected.
Also used to describe PKI key pairs that have this feature.Four A’s of secure data control
- Author: creator, source-of-truth
- Authentic: provable origin, root-of-trust
- Authorized: consent, loci-of-control
- Authoritative: accurate, reputable
"A4" data control securely is established via self-certifying pseudonymous identifiers
Source Samuel M. Smith
authoritative source
ToIP
A source of information that a relying party considers to be authoritative for that information. In ToIP architecture, the trust registry authorized by the governance framework for a trust community is typically considered an authoritative source by the members of that trust community. A system of record is an authoritative source for the data records it holds. A trust root is an authoritative source for the beginning of a trust chain.
authority
WebOfTrust
authority
See ToIP glossary
authorization
ToIP
The process of verifying that a requested action or service is approved for a specific entity.
Source: NIST-CSRC.
See also: permission.
authorized organizational representative
A person who has the authority to make claims, sign documents or otherwise commit resources on behalf of an organization.
Source: Law Insider
WebOfTrust
authorization
Definition
Is the function of specifying access rights/privileges to resources, which is related to general information security and computer security, and to access control in particular.
More formally, "to authorize" is to define an access policy.
KERI specific
Authorizations have the form of a signed authorization statement where the statement typically includes the AID under which the authorization is issued. A verifier may then verify the authorization by verifying the attached signature using the keys that were authoritative at the time the authorization was issued. These authorizations are secure to the extent that the established control authority is secure. The authorizations inherit their security from their associated AID.
W3C VC form
Authorizations may take many forms. One form of particular interest is the W3C Verifiable Credential VC standard. Verifiable credentials use the W3C Decentralized Identifier DID standard. The DID standard provides name spacing syntax for decentralized identifiers that is evocative of URIs. A given DID may be a type of AID but not all DIDs are AIDs. Furthermore, because AIDs may use other name space syntax standards besides DIDs, not all AIDs are DIDs. KERI itself is name space agnostic so may be used to support AIDs in any name space that accepts pseudo-random strings as an element.
authorization graph
ToIP
A graph of the authorization relationships between different entities in a trust community. In a digital trust ecosystem, the governing body is typically the trust root of an authorization graph. In some cases, an authorization graph can be traversed by making queries to one or more trust registries.
See also: governance graph, reputation graph, trust graph.
authorized vlei representative
WebOfTrust
authorized vlei representative
Definition
Also 'AVR'. This a representative of a Legal Entity that are authorized by the DAR of a Legal Entity to request issuance and revocation of:
- vLEI Legal Entity Credentials
- Legal Entity Official Organizational Role vLEI Credentials (OOR vLEI Credentials)
- Legal Entity Engagement Context Role vLEI Credentials (ECR vLEI Credentials).
Paraphrased by @henkvancann from source Draft vLEI Ecosystem Governance Framework Glossary.
autonomic computing systems
WebOfTrust
autonomic computing systems
Definition
Self managing computing systems using algorithmic governance, from the 90's way way way before DAOs. KERI creator Sam Smith worked at funded Navy research in the 90's on autonomic survivable systems as in "self-healing" systems: "We called them autonomic way back then".
autonomic identifier
ToIP
The specific type of self-certifying identifier specified by the KERI specifications.
Also known as: AID.
WebOfTrust
autonomic identifier
Definition
An identifier that is self-certifying and self-sovereign (or self-managing).
KERI related requirements
A self-managing cryptonymous identifier that MUST be self-certifying (self-authenticating) and MUST be encoded in CESR as a qualified cryptographic primitive. An AID MAY exhibit other self-managing properties such as transferable control using key pre-rotation which enables control over such an AID to persist in spite of key weakness or compromise due to exposure. Authoritative control over the identifier persists in spite of the evolution of the key-state.
Source Samuel M. Smith, ietf-keri draftAutonomic Identifier more general
Autonomic Identifiers have been pretty well described in this piece as opposed to centralised (administrative) and blockchain-based (algorithmic) identifier systems: Architectural types of Identity Systems; originally by Phil Windley in this article.
A summarizing comparison table might say more than a hundred words:

autonomic identifier (AID)
ToIP (DID:Webs)
A self-certifying identifier (SCID) that is cryptographically bound cryptographically bound to a key event log (KEL), as defined by the KERI specification. An AID is either non-transferable or transferable. A non-transferable AID does not support key rotation while a transferable AID supports key rotation using a key pre-rotation mechanism that enables the AID to persist in spite of the evolution of its key state. See WebOfTrust glossary for more detail.
autonomic identity system
WebOfTrust
autonomic identity system
Definition
There's nobody that can intervene with the establishment of the authenticity of a control operation because you can verify all the way back to the root-of-trust.
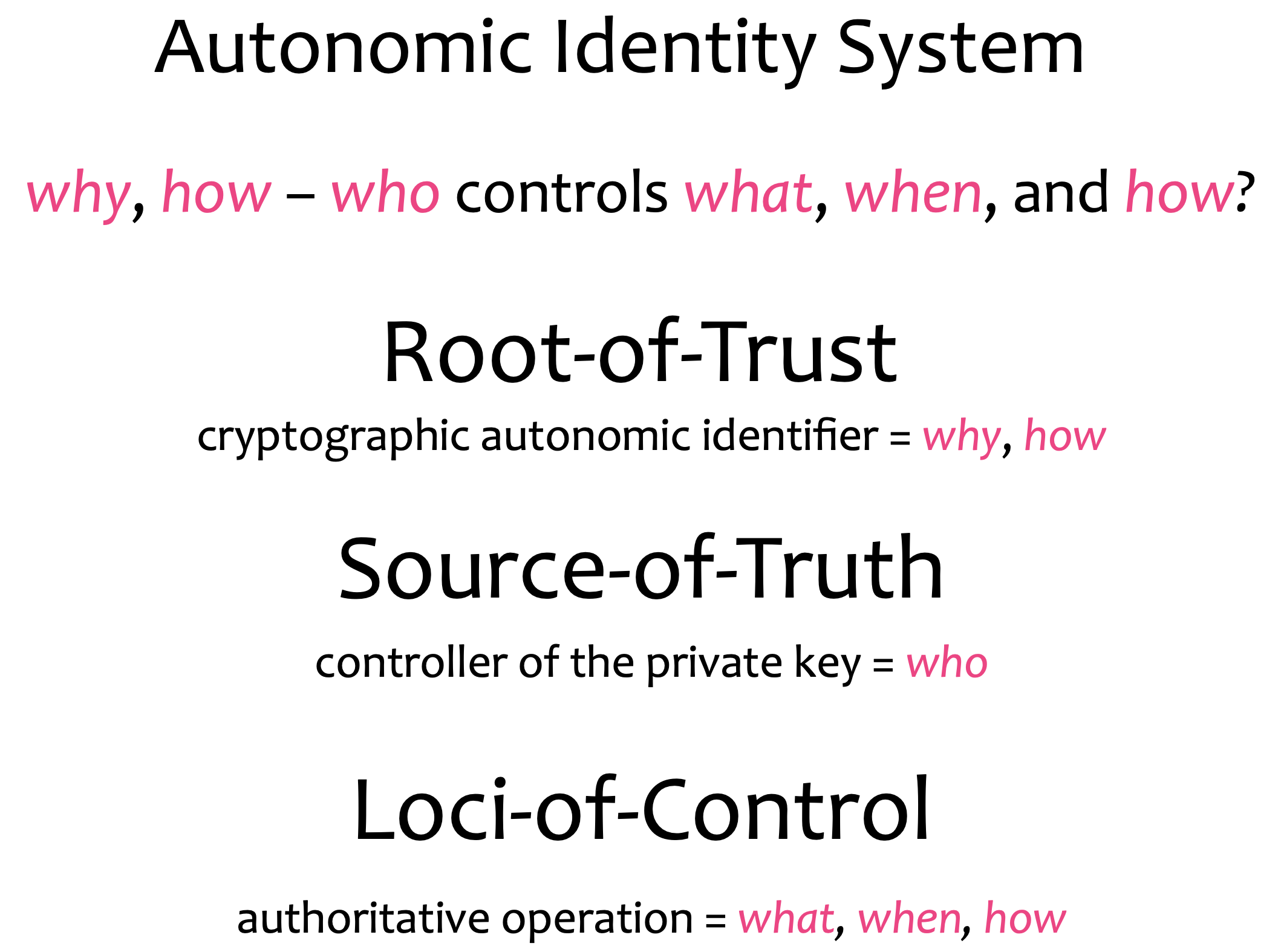
autonomic namespace
WebOfTrust
autonomic namespace
Definition
A namespace that is self-certifying and hence self-administrating. ANs are therefore portable = truly self sovereign.
autonomic trust basis
WebOfTrust
autonomic trust basis
Definition
When use an AID as the root-of-trust we form a so-called autonomic trust basis. This is diagrammed as follows:

Other trust bases
Two other trust bases are in common use for identifier systems. One we call algorithmic, the other is .
An algorithmic trust basis relies on some network of nodes running some type of Byzantine fault tolerant totally ordering distributed consensus algorithm for its root-of-trust. These networks are more commonly known as a shared ledger or blockchain such as Bitcoin, Ethereum, or Sovrin
The other commonly used trust basis in identifier systems is an administrative or organizational trust basis, i.e. a trusted entity. This is neither secure nor decentralized.
backer
WebOfTrust
backer
Definition
The terms Backer and Witness are closely related in KERI. Backers include both regular KERI witnesses and ledger-registered backers.
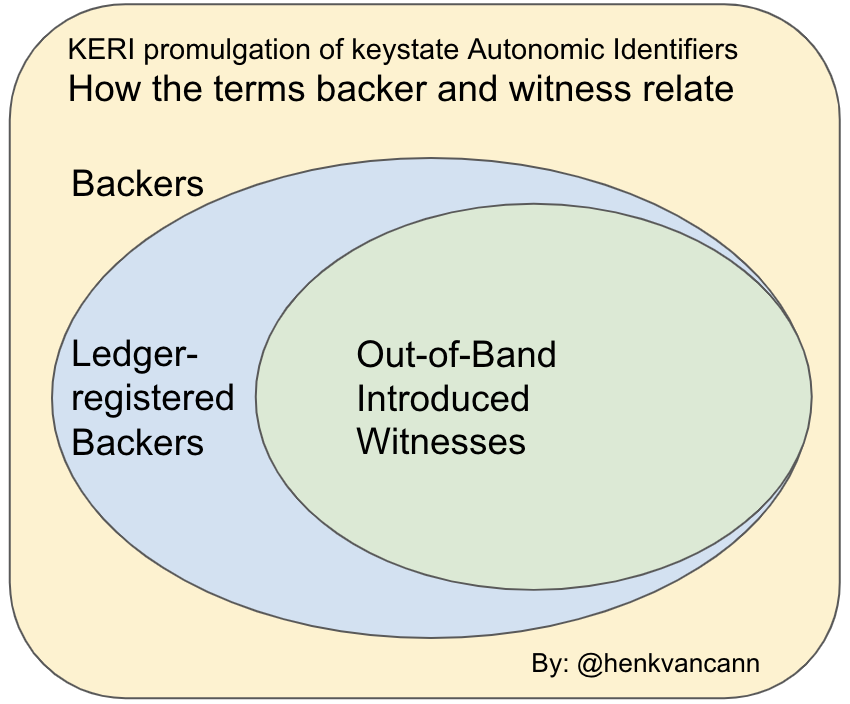
base media type
WebOfTrust
base media type
Definition
credentialplusldplusjson.Other media types of credentials are allowed by must provide either unidirectional or bidirectional transformations. So for example we would create credential+acdc+json and provide a unidirectional transformation to credential+ld+json.
We are going for
credentialplusacdcplusjsonwithout@context. The main objection to use@contextis that it can change the meaning of a credential. The other way around: ACDCs will include W3C credentials.Media types will be used to differentiate between types of credentials and verifiable credentials.
base64
WebOfTrust
base64
Definition
In computer programming, Base64 is a group of binary-to-text encoding schemes that represent binary data (more specifically, a sequence of 8-bit bytes) in sequences of 24 bits that can be represented by four 6-bit Base64 digits.
More on source Wikipedia
bespoke credential
WebOfTrust
bespoke credential
Definition
It's an issuance of the disclosure or presentation of other ACDCs. Bespoke means Custom or tailor made.A bespoke credential serves as an on-the-fly contract with the issuee; it's a self-referencing and self-contained contract between the issuer and the verifier. Mind you, here the issuer and issuee are merely the discloser and disclosee of another (set of) ACDC(s).
Example
If I want consent terms attached to a presentation of an (set of) ACDC(s).
Consider a disclosure-specific ACDC, aka tailor made, custom or bespoke. The Issuer is the Discloser, the Issuee is the Disclosee. The rule section includes a context-specific (anti) assimilation clause that limits the use of the information to a single one-time usage purpose, that is for example, admittance to a restaurant. The ACDC includes an edge that references some other ACDC that may for example be a coupon or gift card. The attribute section could include the date and place of admittance.
For the code of this example, see this section 11.1 in GithubAdvantage
We can use all the tools available for issuance and presentation we already have.
How the process work
Similar to a presentation exchange, a verifier will first be asked for what they are looking for, secondly the discloser creates the dataset and publishes only the structure and the fields. To accomplish this, thirdly a compact ACDC will be issued (you publish the fields, not the content) and then issuer asks to sign it first. After signing, the disclosee can get the content associated with the on-the-fly contract.
More at Github source
best available data acceptance mechanism
WebOfTrust
best available data acceptance mechanism
Definition
The BADA security model provides a degree of replay attack protection. The attributate originator (issuer, author, source) is provided by an attached signature couple or quadruple. A single reply could have multiple originators. When used as an authorization the reply attributes may include the identifier of the authorizer and the logic for processing the associated route may require a matching attachment.BADA is part of KERI's Zero Trust Computing Architecture for Data Management: How to support Secure Async Data Flow Routing in KERI enabled Applications.
See also
bexter
WebOfTrust
bexter
Definition
The class variable length text that is used in CESR and preserves the round-trip transposability using Base64 URL safe-only encoding even though the text variable length.
More details
From readthedocs.io
Bexter is subclass of Matter, cryptographic material, for variable length strings that only contain Base64 URL safe characters, i.e. Base64 text (bext).
When created using the 'bext' paramaeter, the encoded matter in qb64 format in the text domain is more compact than would be the case if the string were passed in as raw bytes. The text is used as is to form the value part of theqb64 version not including the leader.
Due to ambiguity that arises from pre-padding bext whose length is a multiple of three with one or more 'A' chars. Any bext that starts with an 'A' and whose length is either a multiple of 3 or 4 may not round trip. Bext with a leading 'A' whose length is a multiple of four may have the leading 'A' stripped when round tripping.
- Bexter(bext='ABBB').bext == 'BBB'
- Bexter(bext='BBB').bext == 'BBB'
- Bexter(bext='ABBB').qb64 == '4AABABBB' == Bexter(bext='BBB').qb64
To avoid this problem, only use for applications of base 64 strings that never start with 'A'
Examples: base64 text strings:
- bext = ""
- qb64 = '4AAA'
- bext = "-"
- qb64 = '6AABAAA-'
- bext = "-A"
- qb64 = '5AABAA-A'
- bext = "-A-"
- qb64 = '4AABA-A-'
- bext = "-A-B"
- qb64 = '4AAB-A-B'
Example uses:
- CESR encoded paths for nested SADs and SAIDs
- CESR encoded fractionally weighted threshold expressions
Attributes
Inherited Properties: (See Matter) .pad is int number of pad chars given raw .code is str derivation code to indicate cypher suite .raw is bytes crypto material only without code .index is int count of attached crypto material by context (receipts) .qb64 is str in Base64 fully qualified with derivation code + crypto mat .qb64b is bytes in Base64 fully qualified with derivation code + crypto mat .qb2 is bytes in binary with derivation code + crypto material .transferable is Boolean, True when transferable derivation code False otherwiseProperties: .text is the Base64 text value, .qb64 with text code and leader removed.Hidden: ._pad is method to compute .pad property ._code is str value for .code property ._raw is bytes value for .raw property ._index is int value for .index property ._infil is method to compute fully qualified Base64 from .raw and .code ._exfil is method to extract .code and .raw from fully qualified Base64Methods:"""
binding
digital.govt.nz
(noun) the action of a person or thing that binds[Source: Dictionary]Nist
Process of associating two related elements of information.WebOfTrust
binding
Definition
In short, the technique of connecting two data elements together. In the context of KERI it's the association of data or an identifier with another identifier or a subject (a person, organization or machine), thereby lifting the privacy of the subject through that connection, i.e. binding.
biometric
bis
WebOfTrust
bis
Definition
bis = backed vc issue, registry-backed transaction event log credential issuance
bivalent
WebOfTrust
bivalent
Definition
A nested set of layered delegations in a delegation tree, wraps each layer with compromise recovery protection of the next higher layer. This maintains the security of the root layer for compromise recovery all the way out to the leaves in spite of the leaves using less secure key management methods.

To elaborate, in a cooperative delegation, the key generation and storage functions of the delegator and delegate, in terms of the controlling private keys, may be completely isolated from each other. This means that each may use its own independent key management infrastructure with no movement of private keys between the two infrastructures. We call this a bivalent key management infrastructure.
Source Universal Identifier Theory by Samuel Smith
Also see
blake3
WebOfTrust
blake3
Definition
BLAKE3 is a relatively young (2020) cryptographic hash function based on Bao and BLAKE2.
Features and programming languages
BLAKE3 is a single algorithm with many desirable features (parallelism, XOF, KDF, PRF and MAC), in contrast to BLAKE and BLAKE2, which are algorithm families with multiple variants. BLAKE3 has a binary tree structure, so it supports a practically unlimited degree of parallelism (both SIMD and multithreading) given long enough input.
The official Rust and C implementations[24] are dual-licensed as public domain (CC0) and the Apache License.
Fast, parallel and streaming
BLAKE3 is designed to be as fast as possible. It is consistently a few times faster than BLAKE2. The BLAKE3 compression function is closely based on that of BLAKE2s, with the biggest difference being that the number of rounds is reduced from 10 to 7, a change based on the assumption that current cryptography is too conservative. In addition to providing parallelism, the Merkle tree format also allows for verified streaming (on-the-fly verifying) and incremental updates.
blind oobi
WebOfTrust
blind oobi
Definition
A blind OOBI means that you have some mechanisms in place for verifying the AID instead of via the OOBI itself. A blind OOBI is essentially a URL. It's called "blind" because the witness is not in the OOBI itself. You haves other ways of verifying the AID supplied.
Example
A blind OOBI through an AID that is on some witness list and has been verified to root-of-trust already. So you know the human being behind this referred AID. Because it's an AID that has a KEL out there, which has been securely established, you can trust it. So a blind OOBI makes a via-via commitment.
The working
A natural person that you trust is an owner of an AID. Then you cryptographically commit this AID to another AID through some mechanism (e.g. a witness list).
"Here's my public key and here's my AID and because this in an another witness list I trust it."
Unblind
A 'blind' AID becomes "unblind" when you establish a direct relationship with human being who controls the referenced AID. You shortcut the blind OOBI because you established a direct OOBI to the formerly reference AID.
Why is a blind OOBI interesting
type 2 authentication: minimise the friction| TBW prio 3 |
Related terms
Authentication by reference, latent authenticity
blinded revocation registry
WebOfTrust
blinded revocation registry
Definition
The current state of a transaction event log (TEL) may be hidden or blinded such that the only way for a potential verifier of the state to observe that state is when the controller of a designated AID discloses it at the time of presentation.
| TBW: BE CAREFUL WITH THE REST, JUST TEXT SNIPPETS TYPED IN FROM A CONVERSATION |
No information can be obtained via a rainbow table attack because the hash has enough entropy added to it.
| TBW | on the basis of the last half hour of the recording ACDC meetup Dec 6 }
The issuer creates and signs the bulk issuance set of credentials and shares a salt with the presenters.The shared salt correlates between the issuer and the issuee, but that is the worst problem we have to consider, which is acceptable.
See more in the section blindable state tel
Important observation
The presenter does the decomposition in a way that allows a verifier to conclude: "Yes that was an approved schema issued by the issuer!"
blockchain
ToIP
A distributed digital ledger of cryptographically-signed transactions that are grouped into blocks. Each block is cryptographically linked to the previous one (making it tamper evident) after validation and undergoing a consensus decision. As new blocks are added, older blocks become more difficult to modify (creating tamper resistance). New blocks are replicated across copies of the ledger within the network, and any conflicts are resolved automatically using established rules.
Source: NIST-CSRC
Supporting definitions:
Wikipedia: A distributed ledger with growing lists of records (blocks) that are securely linked together via cryptographic hashes. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data (generally represented as a Merkle tree, where data nodes are represented by leaves). Since each block contains information about the previous block, they effectively form a chain (compare linked list data structure), with each additional block linking to the ones before it. Consequently, blockchain transactions are irreversible in that, once they are recorded, the data in any given block cannot be altered retroactively without altering all subsequent blocks.
bran
WebOfTrust
bran
Definition
A cryptographic string used as a primary input, a seed, for creating key material for and autonomic-identifier.
Usages
This is used in Signify TS:
Controllerconstructor argumentconstructor(bran: string, tier: Tier, ridx: number = 0, state: any | null = null) { this.bran = MtrDex.Salt_128 + 'A' + bran.substring(0, 21) // qb64 salt for seed this.stem = "signify:controller" this.tier = tier this.ridx = ridx this.salter = new Salter({ qb64: this.bran, tier: this.tier })...
Sources
Quote, a Zoom chat message, from Dr. Sam Smith on 8/22/23 in the Tuesday morning KERI & ACDC ToIP specification discussion call:
We already use seed and salt for something else so bran is related to seed so we used a term that was evocative of its use but not conflict with already used seed
branch
WebOfTrust
branch
Definition
In software development a 'branch' refers to the result of branching: the duplication of an object under version control for further separate modification.
More info on Wikipedia
Branching, in version control and software configuration management, is the duplication of an object under version control (such as a source code file or a directory tree). Each object can thereafter be modified separately and in parallel so that the objects become different. In this context the objects are called branches. The users of the version control system can branch any branch.
broadcast
ToIP
In computer networking, telecommunication and information theory, broadcasting is a method of transferring a message to all recipients simultaneously. Broadcast delivers a message to all nodes in the network using a one-to-all association; a single datagram (or packet) from one sender is routed to all of the possibly multiple endpoints associated with the broadcast address. The network automatically replicates datagrams as needed to reach all the recipients within the scope of the broadcast, which is generally an entire network subnet.
Source: Wikipedia.
See also: anycast, multicast, unicast.
Supporting definitions:
NIST-CSRC: Transmission to all devices in a network without any acknowledgment by the receivers.
broadcast address
ToIP
A broadcast address is a network address used to transmit to all devices connected to a multiple-access communications network. A message sent to a broadcast address may be received by all network-attached hosts. In contrast, a multicast address is used to address a specific group of devices, and a unicast address is used to address a single device. For network layer communications, a broadcast address may be a specific IP address.
Source: Wikipedia.
broken object level authorization
WebOfTrust
broken object level authorization
Definition
Refers to security flaws where users can access data they shouldn't, due to inadequate permission checks on individual (sub)objects.
brv
WebOfTrust
brv
Definition
brv = backed vc revoke, registry-backed transaction event log credential revocation
byzantine agreement
WebOfTrust
byzantine agreement
Definition
(non PoW) Byzantine Agreement is Byzantine fault tolerance of distributed computing systems that enable them to come to consensus despite arbitrary behavior from a fraction of the nodes in the network. BA consensus makes no assumptions about the behavior of nodes in the system. Practical Byzantine Fault Tolerance (pBFT) is the prototypical model for Byzantine agreement, and it can reach consensus fast and efficiently while concurrently decoupling consensus from resources (i.e., financial stake in PoS or electricity in PoW).
Stellar
More about the Stellar consensus protocol
"What if PBFT and Stellar had a baby?that was missing liveness and total ordering but had safety and was completely decentralized, portable, and permission-less? It would be named KERI."SamMSmith
byzantine fault tolerance
WebOfTrust
byzantine fault tolerance
Definition
A Byzantine fault (also interactive consistency, source congruency, error avalanche, Byzantine agreement problem, Byzantine generals problem, and Byzantine failure) is a condition of a computer system, particularly distributed computing systems, where components may fail and there is imperfect information on whether a component has failed. The term takes its name from an allegory, the "Byzantine Generals Problem", developed to describe a situation in which, in order to avoid catastrophic failure of the system, the system's actors must agree on a concerted strategy, but some of these actors are unreliable.In a Byzantine fault, a component such as a server can inconsistently appear both failed and functioning to failure-detection systems, presenting different symptoms to different observers. It is difficult for the other components to declare it failed and shut it out of the network, because they need to first reach a consensus regarding which component has failed in the first place.Byzantine fault tolerance (BFT) is the dependability of a fault-tolerant computer system to such conditions.
Consensus two third
A system has Byzantine Fault Tolerance (BFT) when it can keep functioning correctly as long as two-thirds of the network agree or reaches consensus. BFT is a property or characteristic of a system that can resist up to one-third of the nodes failing or acting maliciously.
The pBFT model primarily focuses on providing a practical Byzantine state machine replication that tolerates Byzantine faults (malicious nodes) through an assumption that there are independent node failures and manipulated messages propagated by specific, independent nodes.The algorithm is designed to work in asynchronous systems and is optimized to be high-performance with an impressive overhead runtime and only a slight increase in latency. More on wikipedia about
More on Wikipedia
- Byzantine Fault
- pBFT : An article that explains practical BFT.
- Here's a complete beginners guide.
certificate authority
ToIP
The entity in a public key infrastructure (PKI) that is responsible for issuing public key certificates and exacting compliance to a PKI policy.
Source: NIST-CSRC.
Also known as: certification authority.
Supporting definitions:
Wikipedia: In cryptography, a certificate authority or certification authority (CA) is an entity that stores, signs, and issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. A CA acts as a trusted third party—trusted both by the subject (owner) of the certificate and by the party relying upon the certificate.[1] The format of these certificates is specified by the X.509 or EMV standard.
certificate transparency
WebOfTrust
certificate transparency
Definition
Certificate Transparency (CT) is an Internet security standard and open source framework for monitoring and auditing digital certificates. The standard creates a system of public logs that seek to eventually record all certificates issued by publicly trusted certificate authorities, allowing efficient identification of mistakenly or maliciously issued certificates. As of 2021, Certificate Transparency is mandatory for all SSL/TLS certificates.
2011 Diginotar Attack
Certificate Transparency was a response to the 2011 attack on DigiNotar and other Certificate Authorities. These attacks showed that the lack of transparency in the way CAs operated was a significant risk to the Web Public Key Infrastructure. It led to the creation of this ambitious project to improve security online by bringing accountability to the system that protects HTTPS.
More information
More on certificate.transparency.dev and Wikipedia.
certification (of a party)
ToIP
A comprehensive assessment of the management, operational, and technical security controls in an information system, made in support of security accreditation, to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system.
Source: NIST-CSRC.
certification authority
ToIP
See: certificate authority.
certification body
ToIP
A legal entity that performs certification.
For more information: https://en.wikipedia.org/wiki/Professional_certification
cesr proof signatures
WebOfTrust
cesr proof signatures
Definition
CESR Proof Signatures are an extension to the Composable Event Streaming Representation [CESR] that provide transposable cryptographic signature attachments on self-addressing data (SAD) [SAID]. Any SAD, such as an Authentic Chained Data Container (ACDC) Verifiable Credential [ACDC] for example, may be signed with a CESR Proof Signature and streamed along with any other CESR content. In addition, a signed SAD can be embedded inside another SAD and the CESR proof signature attachment can be transposed across envelope boundaries and streamed without losing any cryptographic integrity.
(Philip Feairheller, IETF-cesr-proof)
cesride
WebOfTrust
cesride
Definition
is concerned with parsing CESR primitives.
Cesride is built from cryptographic primitives that are named clearly and concisely. There are:
Each primitive will have methods attached to it that permit one to generate and parse the qualified base2 or base64 representation. Common methods you'll find:
.qb64()- qualified base-64 representation of cryptographic material as a string.qb64b()- qualified base-64 representation of cryptographic material as octets (bytes).qb2()- qualified base-2 representation of cryptographic material as octets (bytes).code()- qualifying code (describes the type of cryptographic material).raw()- raw cryptographic material (unqualified) as octets (bytes)
Source by Jason Colburne
Related
chain link confidentiality
WebOfTrust
chain link confidentiality
Definition
Chains together a sequence of Disclosees which may also include a set of constraints on data usage by both second and third parties expressed in legal language such that the constraints apply to all recipients of the disclosed data thus the phrase "chain link" confidentiality. Each Disclosee in the sequence in turn is the Discloser to the next Disclosee.
This is the primary mechanism of granting digital data rights through binding information exchange to confidentiality laws. Confidentiality is dynamically negotiated on a per-event, per-data exchange basis according to the data that is being shared in a given exchange.
Contrast
Disclosures via Presentations Exchanges may be contractually protected by Chain-Link Confidentiality (i.e. a Chain-Link Confidential disclosure). The chaining in this case is different from the chaining described above between Issuances in a DAG of chained Issuances. Chain-link confidentiality, in contrast, chains together a sequence of Disclosees.
More info at sourceArticle Woodrow Hartzog
An important article on the topic can be found here:
Woodrow Hartzog “Chain-Link Confidentiality”
chain of custody
WebOfTrust
chain of custody
Definition
From Wikipedia (Source):Chain of custody (CoC), in legal contexts, is the chronological documentation or paper trail that records the sequence of custody, control, transfer, analysis, and disposition of materials, including physical or electronic evidence. Of particular importance in criminal cases, the concept is also applied in civil litigation and more broadly in drug testing of athletes and in supply chain management, e.g. to improve the traceability of food products, or to provide assurances that wood products originate from sustainably managed forests.
New technology shortens CoC
It is often a tedious process that has been required for evidence to be shown legally in court. Now, however, with new portable technology that allows accurate laboratory quality results from the scene of the crime, the chain of custody is often much shorter which means evidence can be processed for court much faster.
(Source)
chain of trust
ToIP
See: trust chain.
chained credentials
ToIP
Two or more credentials linked together to create a trust chain between the credentials that is cryptographically verifiable.
Note: ACDCs are a type of digital credential that explicitly supports chaining.
chaining
ToIP
See: trust chain.
challenge
digital.govt.nz
(verb) to order (a person) to halt and be identified or to give a password[Source: Dictionary]Additional note:Note 1: A challenger issues a challenge and a responder replies.
channel
ToIP
See: communication channel.
cigar
WebOfTrust
ciphertext
ToIP
Encrypted (enciphered) data. The confidential form of the plaintext that is the output of the encryption function.
Source: NIST-CSRC.
claim
Nist
A true-false statement about the limitations on the values of an unambiguously defined property called the claims property; and limitations on the uncertainty of the propertys values falling within these limitations during the claims duration of applicability under stated conditions.ToIP
An assertion about a subject, typically expressed as an attribute or property of the subject. It is called a “claim” because the assertion is always made by some party, called the issuer of the claim, and the validity of the claim must be judged by the verifier.
Supporting definitions:
W3C VC: An assertion made about a subject.
Wikipedia: A claim is a statement that one subject, such as a person or organization, makes about itself or another subject. For example, the statement can be about a name, group, buying preference, ethnicity, privilege, association or capability.
Note: If the issuer of the claim is also the subject of the claim, the claim is self-asserted.
WebOfTrust
claim
Definition
An assertion of the truth of something, typically one which is disputed or in doubt. A set of claims might convey personally identifying information: name, address, date of birth and citizenship, for example. (Source).
clone
WebOfTrust
clone
Definition
A copy of a system that is - and works exactly as the original
More detail
In computing, a clone is hardware or software that is designed to function in exactly the same way as another system.
A specific subset of clones are remakes (or remades), which are revivals of old, obsolete, or discontinued products.
Source Wikipedia
cloud agent
WebOfTrust
cloud agent
Definition
Cloud agent is software that is installed on the cloud server instances in order to provide security, monitoring, and analysis solutions for the cloud. They actually provide information and helps to provide control over cloud entities.
Paraphrased by @henkvancann based on source.
Also see Agent.Cloud computing
Cloud computing[1] is the on-demand availability of computer system resources, especially data storage (cloud storage) and computing power, without direct active management by the user.
More at source on Wikipedia
code table
WebOfTrust
code table
Definition
a code table is the Internet's most comprehensive yet simple resource for browsing and searching for alt codes, ascii codes, entities in html, unicode characters, and unicode groups and categories.
SourceExample text code table from CESR
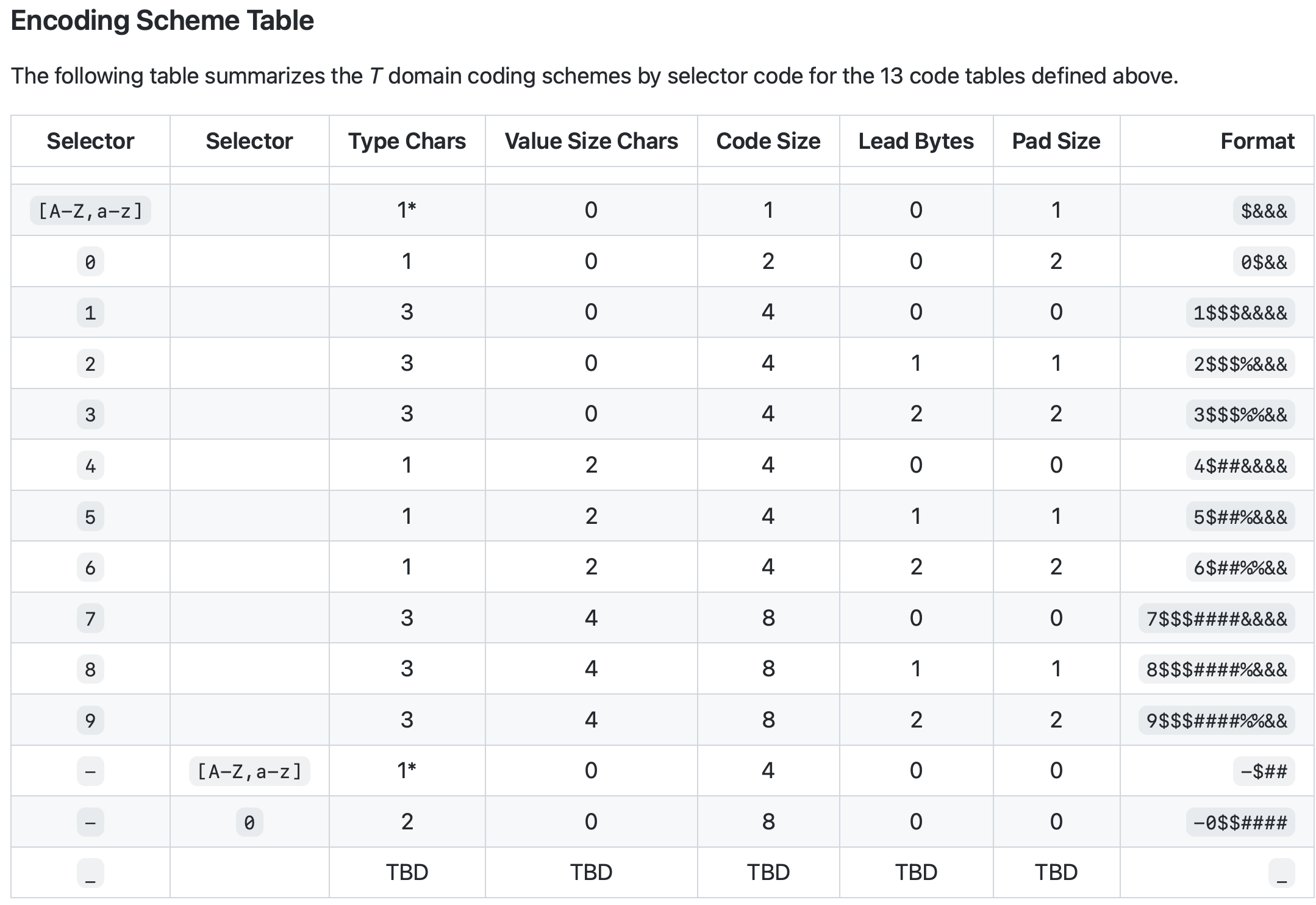
CESR related
Multiple text and binary code tables exist to pre-pend characters before the respective stream parts to characterize (self-framing) them or group them.
code table selector
WebOfTrust
code table selector
Definition
the first character in the text code of CESR stream that determines which code table to use, either a default code table or a code table selector character when not the default code table. Thus the 1 character text code table must do double duty. It must provide selectors for the different text code tables and also provide type codes for the most popular primitives that have a pad size of 1 that appear is the default code table.
Selector code table
See row 1.

cold start stream parsing
WebOfTrust
cold start stream parsing
Definition
After a reboot (or cold start), a stream processor looks for framing information to know how to parse groups of elements in the stream.
If that framing information is ambiguous then the parser may become confused and require yet another cold start. While processing a given stream a parser may become confused especially if a portion of the stream is malformed in some way. This usually requires flushing the stream and forcing a cold start to resynchronize the parser to subsequent stream elements.
re-synchronization
Better than flushing the stream and forcing a cold start is a re-synchronization mechanism that does not require flushing the in-transit buffers but merely skipping to the next well-defined stream element boundary in order to execute a cold start.
See an example in the sourceCESR related
Special CESR count codes support re-synchronization at each boundary between interleaved CESR and other serializations like JSON, CBOR, or MGPK.
collective signature
WebOfTrust
collective signature
Definition
a group signature scheme, that (i) is shared by a set of signing groups and (ii) combined collective signature shared by several signing groups and several individual signers. The protocol of the first type is constructed and described in detail. It is possible to modify the described protocol which allows transforming the protocol of the first type into the protocol of the second type. The proposed collective signature protocols have significant merits, one of which is connected with possibility of their practical using on the base of the existing public key infrastructures.
SourceCollective signature have a variable length as a function of the number of signers.
collision
Nist
An event in which two different messages have the same message digest.WebOfTrust
collision
Definition
In cryptography and identity collision generally refers to something going wrong because an identical result has been produced but it refers to - or points to - different sources or assets backing this result.
E.g. two hashes collide, meaning two different digital sources produce the same hash.
Another example is name(space) collision.Naming collision
A circumstance where two or more identifiers in a given namespace or a given scope cannot be unambiguously resolved.
Source Wikipedia
communication
ToIP
communication channel
ToIP
A communication channel refers either to a physical transmission medium such as a wire, or to a logical connection over a multiplexed medium such as a radio channel in telecommunications and computer networking. A channel is used for information transfer of, for example, a digital bit stream, from one or several senders to one or several receivers.
Source: Wikipedia.
See also: ToIP channel.
Supporting definitions:
eSSIF-Lab: a (digital or non-digital) means by which two actors can exchange messages with one another.
communication endpoint
ToIP
A type of communication network node. It is an interface exposed by a communicating party or by a communication channel. An example of the latter type of a communication endpoint is a publish-subscribe topic or a group in group communication systems.
Source: Wikipedia.
See also: ToIP endpoint.
communication metadata
ToIP
Metadata that describes the sender, receiver, routing, handling, or contents of a communication. Communication metadata is often observable even if the contents of the communication are encrypted.
See also: correlation privacy.
communication session
ToIP
A finite period for which a communication channel is instantiated and maintained, during which certain properties of that channel, such as authentication of the participants, are in effect. A session has a beginning, called the session initiation, and an ending, called the session termination.
Supporting definitions:
NIST-CSRC: A persistent interaction between a subscriber and an end point, either a relying party or a Credential Service Provider. A session begins with an authentication event and ends with a session termination event. A session is bound by use of a session secret that the subscriber’s software (a browser, application, or operating system) can present to the relying party or the Credential Service Provider in lieu of the subscriber’s authentication credentials.
Wikipedia: In computer science and networking in particular, a session is a time-delimited two-way link, a practical (relatively high) layer in the TCP/IP protocol enabling interactive expression and information exchange between two or more communication devices or ends – be they computers, automated systems, or live active users (see login session). A session is established at a certain point in time, and then ‘torn down’ - brought to an end - at some later point. An established communication session may involve more than one message in each direction. A session is typically stateful, meaning that at least one of the communicating parties needs to hold current state information and save information about the session history to be able to communicate, as opposed to stateless communication, where the communication consists of independent requests with responses. An established session is the basic requirement to perform a connection-oriented communication. A session also is the basic step to transmit in connectionless communication modes. However, any unidirectional transmission does not define a session.
compact event streaming representation (CESR)
ToIP (DID:Webs)
An encoding format that enables round-trip text-binary conversion of concatenated cryptographic primitives and general data types, as defined by the CESR specification and CESR Proof Signature specification. See WebOfTrust glossary for more detail.
compact variant
WebOfTrust
compact variant
Definition
Either a most compact version of an ACDC or the fully compact version of an ACDC. An Issuer commitment via a signature to any variant of ACDC (compact, full, etc) makes a cryptographic commitment to the top-level section fields shared by all variants of that ACDC because the value of a top level section field is either the SAD or the SAID of the SAD of the associated section.
Relation
All the variants of an ACDC are various degrees of expansion of the compact variant.
More at sourceAlso see
Fully (expanded) version of an ACDC
Fully compact(ed) version of an ACDC
Most compact version of an ACDC.
complementary integrity verification
WebOfTrust
complementary integrity verification
Definition
A mechanism that can verify integrity independent of needing access to a previous instance or reference version of the information for comparison.
Source: Neil ThomsonComplementary nature
Independent Integrity Verification is what is achieved by use of a public key from the data "controller" such that it does not need to compare received data/messages against the sent data/message.
The already verified chain up to a certain point in time in the past (previous instance or reference version) no longer needs to be verified.
Example: The tail of a KEL that has been verified to its root-of-trust on a certain date and time, can be cut off. You don't need to verify this any more from this date.
See also
complex password
ToIP
A password that meets certain security requirements, such as minimum length, inclusion of different character types, non-repetition of characters, and so on.
Supporting definitions:
Science Direct: According to Microsoft, complex passwords consist of at least seven characters, including three of the following four character types: uppercase letters, lowercase letters, numeric digits, and non-alphanumeric characters such as & $ * and !
compliance
ToIP
In the context of decentralized digital trust infrastructure, the extent to which a system, actor, or party conforms to the requirements of a governance framework or trust framework that pertains to that particular entity.
See also: Governance, Risk Management, and Compliance.
Supporting definitions:
eSSIF-Lab: The state of realization of a set of conformance criteria or normative framework of a party.
comply ~ance
digital.govt.nz
to act in accordance with rules, wishes, etc; be obedient (to)[Source: Dictionary]
composability
WebOfTrust
composable
WebOfTrust
composable event streaming representation
WebOfTrust
composable event streaming representation
Definition
Also called 'CESR'. This compact encoding scheme fully supports both textual and binary streaming applications of attached crypto material of all types. This approach includes composability in both the textual and binary streaming domains. The primitives may be the minimum possible but still composable size.
Making composability a guaranteed property allows future extensible support of new compositions of streaming formats based on pre-existing core primitives and compositions of core primitives. This enables optimized stream processing in both the binary and text domains.
concatenation
WebOfTrust
concatenation
In formal language theory and computer programming, string concatenation is the operation of joining character strings end-to-end. For example, the concatenation of "snow" and "ball" is "snowball".
More on source Wikipedia pageKERI related
In CESR Concatenation is an important property of CESR's Composability; it is associative and may be applied to any two primitives or any two groups or sets of concatenated primitives.
The composability property of CESR allows us to create arbitrary compositions of primitives via concatenation in either the text or binary domain and then convert the composition en masse to the other domain and then de-concatenate the result without loss. The self-framing property of the primitives enables de-concatenation.
concept
ToIP
An abstract idea that enables the classification of entities, i.e., a mental construct that enables an instance of a class of entities to be distinguished from entities that are not an instance of that class. A concept can be identified with a term.
Supporting definitions:
eSSIF-Lab: the ideas/thoughts behind a classification of entities (what makes entities in that class 'the same').
Wikipedia: A concept is defined as an abstract idea. It is understood to be a fundamental building block underlying principles, thoughts and beliefs. Concepts play an important role in all aspects of cognition.
concise binary object representation
WebOfTrust
concise binary object representation
Definition
It is a binary data serialization format loosely based on JSON authored by C. Bormann. Like JSON it allows the transmission of data objects that contain name–value pairs, but in a more concise manner. This increases processing and transfer speeds at the cost of human readability.
IETF specification
It is defined in IETF RFC 8949.[1]
MessagePack
CBOR was inspired by MessagePack, which was developed and promoted by Sadayuki Furuhashi. CBOR extended MessagePack, particularly by allowing to distinguish text strings from byte strings, which was implemented in 2013 in MessagePack.[4][5]
More on Wikipedia
confidential computing
ToIP
Hardware-enabled features that isolate and process encrypted data in memory so that the data is at less risk of exposure and compromise from concurrent workloads or the underlying system and platform.
Source: NIST-CSRC.
Supporting definitions:
Wikipedia: Confidential computing is a security and privacy-enhancing computational technique focused on protecting data in use. Confidential computing can be used in conjunction with storage and network encryption, which protect data at rest and data in transit respectively. It is designed to address software, protocol, cryptographic, and basic physical and supply-chain attacks, although some critics have demonstrated architectural and side-channel attacks effective against the technology.
confidentiality
ToIP
In a communications context, a type of privacy protection in which messages use encryption or other privacy-preserving technologies so that only authorized parties have access.
See also: authenticity, correlation privacy.
Supporting definitions:
NIST-CSRC: Preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information.
Wikipedia: Confidentiality involves a set of rules or a promise usually executed through confidentiality agreements that limits the access or places restrictions on certain types of information.
WebOfTrust
confidentiality
Definition
All statements in a conversation are only known by the parties to that conversation. Source: Samuel Smith, at IIW-37, Oct 2023.
Confidentiality involves a set of rules or a promise usually executed through confidentiality agreements that limits the access or places restrictions on certain types of information.
More on source WikipediaKERI related
The three properties, authenticity, confidentiality, and privacy inhabit a trade space. ...One can have any two of the three (privacy, authenticity, confidentiality) at the highest level but not all three.
The trilemma insists that one must make a trade-off by prioritizing one or two properties over a third.The ToIP design goals reflect that trade-off and provide an order of importance. The design goals indicate that one should start with high authenticity, then high confidentiality, and then as high as possible privacy, given there is no trade-off with respect to the other two.
More on Source Samuel Smith SPAC whitepaper.
Also see
configuration files
WebOfTrust
configuration files
Definition
In computing, configuration files (commonly known simply as config files) are files used to configure the parameters and initial settings for some computer programs. They are used for user applications, server processes and operating system settings.
More on source Wikipedia
connection
ToIP
A communication channel established between two communication endpoints. A connection may be ephemeral or persistent.
See also: ToIP connection.
consensus mechanism
WebOfTrust
consensus mechanism
Definition
How groups of entitities come to decisions. In general to learn about consensus mechanisms read any textbook on decision making, automated reasoning, multi-objective decision making, operations research etc.
Overall reliability
A fundamental problem in distributed computing and multi-agent systems is to achieve overall system reliability in the presence of a number of faulty processes. This often requires coordinating processes to reach consensus, or agree on some data value that is needed during computation.
More information
More on wikipedia or in this 2018 report from the cryptocurrency field.
consent management
ToIP
A system, process or set of policies under which a person agrees to share personal data for specific usages. A consent management system will typically create a record of such consent.
Supporting definitions:
Wikipedia: Consent management is a system, process or set of policies for allowing consumers and patients to determine what health information they are willing to permit their various care providers to access. It enables patients and consumers to affirm their participation in e-health initiatives and to establish consent directives to determine who will have access to their protected health information (PHI), for what purpose and under what circumstances. Consent management supports the dynamic creation, management and enforcement of consumer, organizational and jurisdictional privacy policies.
consequence
digital.govt.nz
outcome of an event affecting objectives[Source: ISO 31073:2022]Additional notes:Note 1: A consequence can have positive or negative, direct or indirect, effects on objectives.Note 2: Consequences can be expressed qualitatively or quantitatively.Note 3: Any consequences can escalate through cascading and cumulative effects.
content addressable hash
WebOfTrust
content addressable hash
Definition
Finding content by a hash of this content, generated by a one-way hash function applied to the content.
Content addressing is a way to find data in a network using its content rather than its location. The way we do is by taking the content of the content and hashing it. Try uploading an image to IPFS and get the hash using the below button.
Content Addressable Storage
Content Addressable Storage systems work by passing the content of the file through a cryptographic hash function to generate a unique key, the "content address". The file system's directory stores these addresses and a pointer to the physical storage of the content. Because an attempt to store the same file will generate the same key, CAS systems ensure that the files within them are unique, and because changing the file will result in a new key, CAS systems provide assurance that the file is unchanged.
IPFS
In the IPFS ecosystem, this hash is called Content Identifier, or CID.
context
digital.govt.nz
environment with defined boundary conditions in which entities exist and interact[Source: ITU-T X.1252]
contextual linkability
WebOfTrust
contextual linkability
Definition
Refers to the condition where vendors or other data capture points provide enough context at point of capture to be able to use statistical correlation with existing data sets to link any of a person's disclosed attributes to a set of already known data points about a given person.
This sort of linkability nullifies the perceived protection of selective disclosure through zero knowledge proofs since the disclosed data can be combined with context to easily link the disclosed data to an existing profile of the person.
These threats mainly focus on a subject (the entity) who wants to hide as much of his identifiable information (or at least make it as unlikable as possible). This can occur when the subject wants to authenticate himself to a certain service (multiple authentication principles are shown in the tree), but also during regular communication (browsing, client-server requests, etc.) by means of the contextual information connected or linked to the the activity or communication.
More at sourceContractually protected disclosure is the primary defense against contextual linkability.
Example
Cameras in stores are already able to identify you due to the extremely high prevalence of modern security systems who do facial recognition or mobile device ping recognition on each person entering the premises of a store. In the context of you buying stuff in their store they can capture data linked to you and then go and sell your data to third parties since there is an implicit grant of permission to use the data and also since there are no legal constraints on the distribution of that data.
Dangers
Just have a look at what "they" are doing:
https://linkgraph.io/blog/how-to-contextual-link-building/
contiguous
digital.govt.nz
immediately preceding or following in time[Source: Dictionary modified by adding immediately]Additional note:Note 1: When applied to authentication, multiple factors are tested in such adjacent steps, that they are considered part of a single process.
contingent disclosure
WebOfTrust
contingent disclosure
Definition
Chain link confidentiality is a form of contingent disclosure.
| TBW prio 1 |
contractually protected disclosure
WebOfTrust
contractually protected disclosure
Definition
Usage of schema-based and contract-based controls to limit the exchange of information to provide both mechanical and legal protection on the sharing of data.
Mechanical protection is composed of sharing the schema of the data to be shared prior to sharing the actual data contents. This mechanical protection is then combined through the IPEX protocol with disclosures of legal contracts to be agreed to prior to sharing the desired data contents.
Once the legal agreements have been met then the disclosure mechanism exchanges the desired data contents.
This is also the most elaborate form of disclosure by an IPEX. Contractually protected disclosure includes both chain-link confidential and contingent disclosure.
Paraphrased by @henkvancann based on sourceRelation
This IPEX protocol leverages important features of ACDCs and ancillary protocols such as CESR, SAIDs, and CESR-Proofs as well as Ricardian contracts and graduated disclosure (partial, selective, full) to enable contractually protected disclosure. Contractually protected disclosure includes both [chain-link confidential](chain-link confidential) and [contingent disclosure](contingent disclosure).
Rule
The disclosure performed by a presentation exchange MAY be graduated and MAY be contractually protected.
control
digital.govt.nz
(verb) to command, direct, or rule[Source: Dictionary]Additional note:Note 1: Control is also used outside the context of risk mitigation. For example, to indicate the ability for an authenticator holder to retain use of their authenticator.
control authority
WebOfTrust
control authority
Definition
In identity systems Control Authority is who controls what and that is the primary factor in determining the basis for trust in them. The entity with control authority takes action through operations that affect the
- creation (inception)
- updating
- rotation
- revocation
- deletion
- and delegation of the authentication factors and their relation to the identifier.
Source of truth
How these events are ordered and their dependence on previous operations is important. The record of these operations is the source of truth for the identity system.
Change control authority
In the 2022 implementation of KeriPy two rotations were required to change control authority.In new rotation rules, you can rotate to new keys that aren't in the prior next key digests. You just need to reach the appropriate thresholds of prior-next-threshold and current-signing-threshold. So you now only need one rotation to change control authority.
Note: This change was the forcing function to require dual indexed codes in CESR.
controlled document
ToIP
A governance document whose authority is derived from a primary document.
controller
ToIP (DID:Webs)
A controlling entity that can cryptographically prove the control authority (signing and rotation) over an AID as well as make changes on the associated KEL. A controller may consist of multiple controlling entities in a multi-signature scheme. See WebOfTrust glossary for more detail.WebOfTrust
controller
Definition
A controller is a controlling entity (person, organization, or autonomous software) of an identifier. For an autonomic identifier (AID), a controlling entity has the capability to make changes to the key event log (KEL) of the AID. This capability is typically asserted by the control of a set of cryptographic keys used by software acting on behalf of the controller, though it might also be asserted via other mechanisms.
At any point in time, an identifier has at least one but may have more than one controlling entity. This set of controlling entities constitutes the controller. Without loss of generality, when the context is unambiguous, the term controller may refer either to the whole set or a member of the set of controlling entities.
All key events on the identifier must include a signature from the sole controlling entity when there is only one controlling entity or at least one signature from one of the controlling entities when there is more than one. Typically, when there is more than one controlling entity, control is established via signatures from all or a subset of controlling entities. This is called multi-signature (multi-sig). In a threshold multi-sig scheme, the control authority is split among the controlling entities, where each is assigned a weight. In this case, the control authority over the identifier is established via signatures from a subset of controlling entities whose combined weights exceed an agreed threshold. These thresholded multiple signatures may be expressed as a single collective threshold signature when a collective signing scheme is used.
The control authority over an identifier can also be divided into signing authority and rotation authority. The controller of the identifier may grant their authority to other entities. For example, in custodial rotation, the controller grants a designated custodial agent the signing authority while retaining their rotation authority. In the case of a delegated identifier, the delegated identifier is granted some degree of control authority from its delegating identifier.
controller (of a key, vault, wallet, agent, or device)
ToIP
In the context of digital communications, the entity in control of sending and receiving digital communications. In the context of decentralized digital trust infrastructure, the entity in control of the cryptographic keys necessary to perform cryptographically verifiable actions using a digital agent and digital wallet. In a ToIP context, the entity in control of a ToIP endpoint.
See also: device controller, DID controller, ToIP controller.
Supporting definitions:
eSSIF-Lab: the role that an actor performs as it is executing actions on that entity for the purpose of ensuring that the entity will act/behave, or be used, in a particular way.
cooperative delegation
WebOfTrust
cooperative delegation
Definition
The way KERI addresses the security-cost-performance architecture trade-off is via delegation of identifier prefixes. Delegation includes a delegator and a delegate. For this reason we may call this a cooperative delegation. This is a somewhat novel form of delegation. A major advantage of cooperative delegation is the delegator’s key management protects the delegate’s via recovery by the delegator. With cooperative delegation, any exploiter that compromises only the delegate’s authoritative keys may not capture control authority of the delegate. Any exploit of the delegate only is recoverable by the delegator.
Source Universal Identifier Theory by Samuel Smith
coroutines
WebOfTrust
coroutines
Definition
Computer programs that can be suspended and resumed at will.
What is a coroutine exactly?
Coroutines are computer program components that generalize subroutines for non-preemptive multitasking, by allowing execution to be suspended and resumed. Coroutines are well-suited for implementing familiar program components such as cooperative tasks, exceptions, event loops, iterators, infinite lists and pipes.
More on source Wikipedia
correlate~ion
digital.govt.nz
to place or be placed in a mutual, complementary, or reciprocal relationship[Source: Dictionary]
correlation
WebOfTrust
correlation
Definition
In our scope this is an identifier used to indicate that external parties have observed how wallet contents are related.
Example
When a public key is reused, it conveys that some common entity is controlling both identifiers. Tracking correlation allows for software to warn when some new information might be about to be exposed, for example: "Looks like you are about to send cryptocurrency, from an account you frequently use to a new account you just created."
correlation privacy
ToIP
In a communications context, a type of privacy protection in which messages use encryption, hashes, or other privacy-preserving technologies to avoid the use of identifiers or other content that unauthorized parties may use to correlate the sender and/or receiver(s).
See also: authenticity, confidentiality.
corroborate~ing
digital.govt.nz
to confirm or support (facts, opinions, etc), esp by providing fresh evidence[Source: Dictionary]
count code
WebOfTrust
counterparty
ToIP
From the perspective of one party, the other party in a transaction, such as a financial transaction.
See also: first party, second party, third party.
Supporting definitions:
Wikipedia: A counterparty (sometimes contraparty) is a legal entity, unincorporated entity, or collection of entities to which an exposure of financial risk may exist.
credential
digital.govt.nz
an artefact created as the result of a series of processes that bind an entity with information and an authenticator, on which other parties relyAdditional note:Note 1: At a minimum a credential includes an authenticator and information to enable presentation.Nist
Evidence attesting to ones right to credit or authority. In this Standard, it is the PIV Card or derived PIV credential associated with an individual that authoritatively binds an identity (and, optionally, additional attributes) to that individual.ToIP
A container of claims describing one or more subjects. A credential is generated by the issuer of the credential and given to the holder of the credential. A credential typically includes a signature or some other means of proving its authenticity. A credential may be either a physical credential or a digital credential.
See also: verifiable credential.
Supporting definitions:
eSSIF-Lab: data, representing a set of assertions (claims, statements), authored and signed by, or on behalf of, a specific party.
WebOfTrust
credential
Definition
Evidence of authority, status, rights, entitlement to privileges, or the like.
(source)
A credential has its current state and a history, which is captured in a doc or a graph.ACDC specific
The credential is the whole graph.
The pointers in the doc that contain the whole graph are universally globally distributable references via the SAIDs. Whereas in other credential systems pointers are only local in a credential doc.
credential family
ToIP
A set of related digital credentials defined by a governing body (typically in a governance framework) to empower transitive trust decisions among the participants in a digital trust ecosystem.
credential governance framework
ToIP
A governance framework for a credential family. A credential governance framework may be included within or referenced by an ecosystem governance framework.
credential offer
ToIP
A protocol request invoked by an issuer to offer to issue a digital credential to the holder of a digital wallet. If the request is invoked by the holder, it is called an issuance request.
credential provider
digital.govt.nz
the party accountable for the establishment and presentation facilitation of a credentialAdditional note:Note 1: A Credential Provider may employ other parties in the carrying out of their function.
credential request
ToIP
See: issuance request.
credential schema
ToIP
A data schema describing the structure of a digital credential. The W3C Verifiable Credentials Data Model Specification defines a set of requirements for credential schemas.
criterion
ToIP
In the context of terminology, a written description of a concept that anyone can evaluate to determine whether or not an entity is an instance or example of that concept. Evaluation leads to a yes/no result.
crypto libraries
WebOfTrust
crypto libraries
Definition
Cryptography libraries deal with cryptography algorithms and have API function calls to each of the supported features.
Selection criteria
Criteria to chose one or the other:
- Open Source (most of them are)
- Compliant with standards
- Key operations include key generation algorithms, key exchange agreements and public key cryptography standards.
- Supported cryptographic hash functions
- Implementations of message authentication code (MAC) algorithms
- Implementations of block ciphers
- Hardware-assisted support
- Code size and code to comment ratio
- Composable derivation codes
See a comparison here at Wikipedia.
cryptocurrency
WebOfTrust
cryptocurrency
Definition
A digital asset designed to work as a medium of exchange wherein individual coin ownership records are stored in a digital ledger or computerized database using strong cryptography to secure transaction record entries, to control the creation of additional digital coin records.
See more on source Wikipedia.KERI related
KERI doesn't need total global ordering, whereas cryptocurrencies do need this. As a consequence has been designed, without the need of a consensus-based distributed ledger (blockchain).
KERI doesn't provide for a currency system, however a KERI-based system can be easily extended with a money - or token system.
See also Non Fungible Tokens.
cryptographic binding
ToIP
Associating two or more related elements of information using cryptographic techniques.
Source: NIST-CSRC.
cryptographic commitment scheme
WebOfTrust
cryptographic commitment scheme
Definition
is a cryptographic primitive that allows one to commit to a chosen value (or chosen statement) while keeping it hidden to others, with the ability to reveal the committed value later.
Commitment schemes are designed so that a party cannot change the value or statement after they have committed to it: that is, commitment schemes are binding.
More on wikipedia
cryptographic key
ToIP
A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic algorithm, can encode or decode cryptographic data. Symmetric cryptography refers to the practice of the same key being used for both encryption and decryption. Asymmetric cryptography has separate keys for encrypting and decrypting. These keys are known as the public keys and private keys, respectively.
Source: Wikipedia.
See also: controller.
cryptographic primitive
WebOfTrust
cryptographic primitive
Definition
Cryptographic primitives are well-established, low-level cryptographic algorithms that are frequently used to build cryptographic protocols for computer security systems. These routines include, but are not limited to, one-way hash functions and encryption functions.
More on source Wikipedia-pageKERI related
In KERI and ACDC it a serialization of a unitary value associated with a cryptographic operation including but not limited to a digest (hash), a salt, a seed, a private key, a public key, or a signature. All primitives in KERI MUST be expressed in CESR.
See also
The more general term primitive.
cryptographic strength
WebOfTrust
cryptographic strength
Definition
The term "cryptographically strong" is often used to describe an encryption algorithm, and implies, in comparison to some other algorithm (which is thus cryptographically weak), greater resistance to attack. But it can also be used to describe hashing and unique identifier and filename creation algorithms.
More on Wikipedia
cryptographic suite
W3C (DID)
A specification defining the usage of specific cryptographic primitives inorder to achieve a particular security goal. These documents are often usedto specify verification methods, digital signature types,their identifiers, and other related properties.
cryptographic trust
ToIP
A specialized type of technical trust that is achieved using cryptographic algorithms.
Contrast with: human trust.
cryptographic verifiability
ToIP
The property of being cryptographically verifiable.
Contrast with: human auditability.
cryptographically bound
ToIP
A state in which two or more elements of information have a cryptographic binding.
cryptographically verifiable
ToIP
A property of a data structure that has been digitally signed using a private key such that the digital signature can be verified using the public key. Verifiable data, verifiable messages, verifiable credentials, and verifiable data registries are all cryptographically verifiable. Cryptographic verifiability is a primary goal of the ToIP Technology Stack.
Contrast with: human auditable.
cryptonym
WebOfTrust
cryptonym
Definition
A code name, call sign or cryptonym is a code word or name used, sometimes clandestinely, to refer to another name, word, project, or person.
Source WikipediaKERI related
A cryptographic pseudonymous identifier represented by a string of characters derived from a random or pseudo-random secret seed or salt via a one-way cryptographic function with a sufficiently high degree of cryptographic strength (e.g. 128 bits, see appendix on cryptographic strength. A cryptonym is a type of primitive.
Due the entropy in its derivation, a cryptonym is a universally unique identifier and only the controller of the secret salt or seed from which the cryptonym is derived may prove control over the cryptonym. Therefore the derivation function MUST be associated with the cryptonym and MAY be encoded as part of the cryptonym itself.\
Source Smith, ietf-keri draft
custodial agent
WebOfTrust
custodial agent
Definition
An agent owned by an individual who has granted signing authority to a custodian who is usually also the host of the running agent software. Using partial rotation to facilitate custodial key management the owner of the identifier retains rotational authority and thus the ability to "fire" the custodian at any time without requiring the cooperation of the custodian.
Importance
Custodial Agents are important for individuals who may not be comfortable managing their own signing keys and agent software but still want to participate in a decentralized identity ecosystem and they enable a software as a service business model without centralizing control on the service provider.
(Source: Philip Feairheller)Key functionality
Since ninety-nine percent of people in the world might not feel comfortable taking responsibility for their own practical key management but still want to be stay in control over their assets and be able to hire and fire service providers, this functionality is considered a key feature for KERI and ACDC.
custodial rotation
WebOfTrust
custodial rotation
Definition
Rotation based on control authority that is split between two key sets. The first for signing authority and the second (pre-roateted) for rotation authority the associated thresholds and key list can be structured in such a way that a designated custodial agent can hold signing authority while the original controller can hold exclusive rotation authority.
Partial pre-rotation supports the important use case that of custodial key rotation to authorize a custodial agent.
Paraphrased by @henkvancann on the bases of the IETF-KERI draft 2022 by Samual Smith.
custodial wallet
ToIP
A digital wallet that is directly in the custody of a principal, i.e., under the principal’s direct personal or organizational control. A digital wallet that is in the custody of a third party is called a non-custodial wallet.
custodian
ToIP
A third party that has been assigned rights and duties in a custodianship arrangement for the purpose of hosting and safeguarding a principal��’s private keys, digital wallet and digital assets on the principal’s behalf. Depending on the custodianship arrangement, the custodian may act as an exchange and provide additional services, such as staking, lending, account recovery, or security features.
Contrast with: guardian, zero-knowledge service provider.
See also: custodial wallet.
Supporting definitions:
NIST-CSRC: A third-party entity that holds and safeguards a user’s private keys or digital assets on their behalf. Depending on the system, a custodian may act as an exchange and provide additional services, such as staking, lending, account recovery, or security features.
Note: While a custodian technically has the necessary access to in theory impersonate the principal, in most cases a custodian is expressly prohibited from taking any action on the principal’s account unless explicitly authorized by the principal. This is what distinguishes custodianship from guardianship.
custodianship arrangement
dark pattern
ToIP
A design pattern, mainly in user interfaces, that has the effect of deceiving individuals into making choices that are advantageous to the designer.
Source: Kantara PEMC Implementors Guidance Report
Also known as: deceptive pattern.
data
ToIP
In the pursuit of knowledge, data is a collection of discrete values that convey information, describing quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted. A datum is an individual value in a collection of data.
Source: Wikipedia.
See also: verifiable data.
Supporting definitions:
eSSIF-Lab: something (tangible) that can be used to communicate a meaning (which is intangible/information).
data anchor
WebOfTrust
data anchor
Definition
Data anchors are digests of digital data, that uniquely identify this data. The digest is the anchor and can be used to identify - and point to the data at the same time.
Anchoring data
The act of creating the digest of arbitrary data and then hook (or reference) the digest to (in) another data structure is called 'anchoring data'.
KERI related
SADs are a type of data anchors.
Beware
Link anchors are a totally different concepts.
data packet
ToIP
In telecommunications and computer networking, a network packet is a formatted unit of data carried by a packet-switched network such as the Internet. A packet consists of control information and user data; the latter is also known as the payload. Control information provides data for delivering the payload (e.g., source and destination network addresses, error detection codes, or sequencing information). Typically, control information is found in packet headers and trailers.
Source: Wikipedia.
data schema
ToIP
A description of the structure of a digital document or object, typically expressed in a machine-readable language in terms of constraints on the structure and content of documents or objects of that type. A credential schema is a particular type of data schema.
Supporting definitions:
Wikipedia: An XML schema is a description of a type of XML document, typically expressed in terms of constraints on the structure and content of documents of that type, above and beyond the basic syntactical constraints imposed by XML itself. These constraints are generally expressed using some combination of grammatical rules governing the order of elements, Boolean predicates that the content must satisfy, data types governing the content of elements and attributes, and more specialized rules such as uniqueness and referential integrity constraints.
data subject
ToIP
The natural person that is described by personal data. Data subject is the term used by the EU General Data Protection Regulation.
data vault
ToIP
See: digital vault.
datagram
ToIP
See: data packet.
dead drop
WebOfTrust
dead drop
Definition
| TBW | the presenter controls the disclosure so you can't re-identify the data
Tech meet KERI recording from minute 55, date June 29 2023.
decentralized identifier
ToIP
A globally unique persistent identifier that does not require a centralized registration authority and is often generated and/or registered cryptographically. The generic format of a DID is defined in section 3.1 DID Syntax of the W3C Decentralized Identifiers (DIDs) 1.0 specification. A specific DID scheme is defined in a DID method specification.
Source: W3C DID.
Also known as: DID.
See also: DID method, DID URL.
WebOfTrust
decentralized identifier
Definition
Decentralized identifiers (DID) are a new type of identifier that enables verifiable, decentralized digital identity. A DID refers to any subject (e.g., a person, organization, thing, data model, abstract entity, etc.) as determined by the controller of the DID.
Source W3C.org.Relation to federated identifiers
In contrast to typical, federated identifiers, DIDs have been designed so that they may be decoupled from centralized registries, identity providers, and certificate authorities. Specifically, while other parties might be used to help enable the discovery of information related to a DID, the design enables the controller of a DID to prove control over it without requiring permission from any other party.
Source W3C.org.Technical presence
DIDs are URIs that associate a DID subject with a DID document allowing trustable interactions associated with that subject.
Source W3C.org.
decentralized identifier (DID)
ToIP (DID:Webs)
A globally unique persistent identifier, as defined by DID Core.W3C (DID)
A globally unique persistent identifier that does not require a centralizedregistration authority and is often generated and/or registeredcryptographically. The generic format of a DID is defined in 3.1 DID Syntax. A specific DID scheme is defined in a DIDmethod specification. Manybut not allDID methods make use ofdistributed ledger technology (DLT) or some other form of decentralizednetwork.
decentralized identity
ToIP
A digital identity architecture in which a digital identity is established via the control of a set of cryptographic keys in a digital wallet so that the controller is not dependent on any external identity provider or other third party.
See also: federated identity, self-sovereign identity.
WebOfTrust
decentralized identity
Definition
is a technology that uses cryptography to allow individuals to create and control their own unique identifiers. They can use these identifiers to obtain
Verifiable Credentialsfrom trusted organizations and, subsequently, present elements of these credentials as proof of claims about themselves. In this model, the individual takes ownership of their own identity and need not cede control to centralized service providers or companies.KERIs definition of decentralization (centralization) is about control not spatial distribution. In our definition decentralized is not necessarily the same as distributed. By distributed we mean that activity happens at more than one site. Thus decentralization is about control and distribution is about place. To elaborate, when we refer to decentralized infrastructure we mean infrastructure under decentralized (centralized) control no matter its spatial distribution. Thus decentralized infrastructure is infrastructure sourced or controlled by more than oneentity.
decentralized identity management
W3C (DID)
Identitymanagement that is based on the use of decentralized identifiers.Decentralized identity management extends authority for identifier generation,registration, and assignment beyond traditional roots of trust such asX.500 directory services,the Domain Name System,and most national ID systems.
decentralized key management infrastructure
WebOfTrust
decentralized key management infrastructure
Definition
Decentralized Public Key Infrastructure (DPKI or Decentralized Key Management System (DKMS) goal is to ensure that no single third-party can compromise the integrity and security of the system as as whole.
Source
deceptive pattern
ToIP
See: dark pattern.
decryption
ToIP
The process of changing ciphertext into plaintext using a cryptographic algorithm and key. The opposite of encryption.
Source: NIST-CSRC.
deep link
ToIP
In the context of the World Wide Web, deep linking is the use of a hyperlink that links to a specific, generally searchable or indexed, piece of web content on a website (e.g. "https://example.com/path/page"), rather than the website's home page (e.g., "https://example.com"). The URL contains all the information needed to point to a particular item. Deep linking is different from mobile deep linking, which refers to directly linking to in-app content using a non-HTTP URI.
See also: out-of-band introduction.
Source: Wikipedia.
definition
ToIP
A textual statement defining the meaning of a term by specifying criterion that enable the concept identified by the term to be distinguished from all other concepts within the intended scope.
Supporting definitions:
eSSIF-Lab: a text that helps parties to have the same understanding about the meaning of (and concept behind) a term, ideally in such a way that these parties can determine whether or not they make the same distinction.
Wikipedia: A definition is a statement of the meaning of a term (a word, phrase, or other set of symbols). Definitions can be classified into two large categories: intensional definitions (which try to give the sense of a term), and extensional definitions (which try to list the objects that a term describes). Another important category of definitions is the class of ostensive definitions, which convey the meaning of a term by pointing out examples. A term may have many different senses and multiple meanings, and thus require multiple definitions.
delegate
digital.govt.nz
(noun) a person chosen or elected to act for or represent another or others[Source: Dictionary]Additional note:Note 1: Modified to remove reference to conference or meeting.
delegated identifier
WebOfTrust
delegated identifier
Definition
Matches the act of delegation with the appropriate digital twin. Consequently when applied recursively, delegation may be used to compose arbitrarily complex trees of hierarchical (delegative) key management event streams. This is a most powerful capability that may provide an essential building block for a generic universal decentralized key management infrastructure (DKMI) that is also compatible with the demand of generic event streaming applications.
More in the whitepaper
More KERI context
The KERI design approach is to build composable primitives instead of custom functionality that is so typical of other DKMI approaches:
- transferable identifiers
- non-transferable identifiers
- delegated identifiers
delegate~ed
digital.govt.nz
(verb) to give or commit (duties, powers, etc) to another as agent or representative; depute[Source: Dictionary]
delegation
ToIP
TODO
WebOfTrust
delegation
Definition
A person or group of persons officially elected or appointed to represent another or others.
Assign tasks but stay in control
Delegation can be defined as “the act of empowering to act for another”. With this bestowed power, a person, usually a subordinate, is able to carry out specific activities (normally given by a manager or supervisor). Delegation is a management tool designed to increase the efficiency of an organization. It allows for the goals of the organization to be broken down into tasks and assigned to the team member best suited for the duty.
delegation credential
ToIP
TODO
dependent
ToIP
An entity for the caring for and/or protecting/guarding/defending of which a guardianship arrangement has been established with a guardian.
Source: eSSIF-Lab
See also: custodian.
Mental Model: eSSIF-Lab Guardianship
derivation code
WebOfTrust
derivation code
Definition
To properly extract and use the public key embedded in a self-certifying identifier we need to know the cryptographic signing scheme used by the key pair. KERI includes this very compactly in the identifier, by replacing the pad character (a character used to fill a void to able to always end up with a fixed length public key) with a special character that encodes the derivation process. We call this the derivation code.
Example
For example suppose that the 44 character Base-64 with trailing pad character for the public key is as follows:
F5pxRJP6THrUtlDdhh07hJEDKrJxkcR9m5u1xs33bhp=If B is the value of the derivation code then the resultant self-contained string is as follows:BF5pxRJP6THrUtlDdhh07hJEDKrJxkcR9m5u1xs33bhpRelation with KERI
All crypto material appears in
KERIin a fully qualified representation. This includes a derivation code prepended to the crypto-material.
Example KERI derivation codes
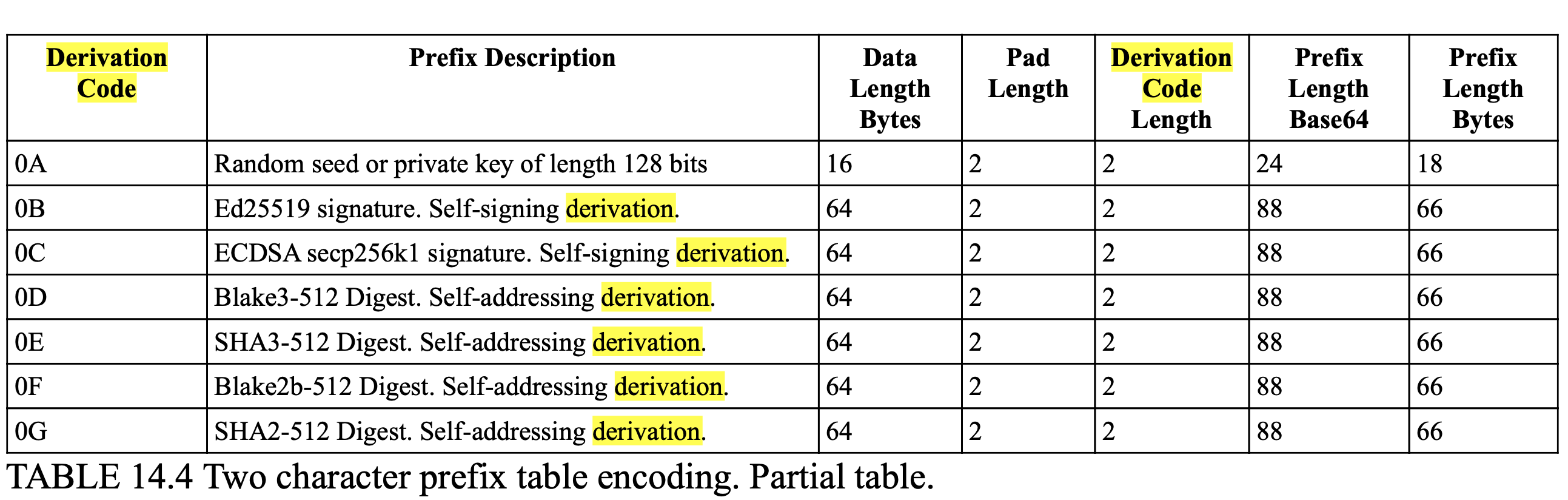
Beware
Key derivation functions are not related to the pre-pended derivation codes used in KERI.
derived value
digital.govt.nz
value obtained by reasoning; deduction or inference[Source: expanded Dictionary meaning of derive]
designated aliases
ToIP (DID:Webs)
An array of AID controlled identifiers that have been designated by the AID controller to be used as aliases for equivalentId and alsoKnownAs DID document metadata and to foster verification of redirection to different did:webs identifiers. See WebOfTrust glossary for more detail.WebOfTrust
designated aliases
Definition
An AID controller can designate aliases which are AID controlled identifiers such as a did:keri, did:webs, etc. The AID controller issues a designated aliases attestation (no issuee) that lists the identifiers and manages the status through a registry anchored to their KEL. See the designated aliases docs
designated authorized representative
WebOfTrust
designated authorized representative
Definition
Also 'DAR'. These are representatives of a Legal Entity that are authorized by the Legal Entity to act officially on behalf of the Legal Entity. DARs can authorize:
- vLEI Issuer Qualification Program Checklists
- execute the vLEI Issuer Qualification Agreement
- provide designate/replace Authorized vLEI Representatives (AVRs).
Paraphrased by @henkvancann from source Draft vLEI Ecosystem Governance Framework Glossary.
device controller
ToIP
The controller of a device capable of digital communications, e.g., a smartphone, tablet, laptop, IoT device, etc.
dictionary
ToIP
A dictionary is a listing of lexemes (words or terms) from the lexicon of one or more specific languages, often arranged alphabetically, which may include information on definitions, usage, etymologies, pronunciations, translation, etc. It is a lexicographical reference that shows inter-relationships among the data. Unlike a glossary, a dictionary may provide multiple definitions of a term depending on its scope or context.
Source: Wikipedia.
diger
digest
WebOfTrust
digest
Definition
verifiable cryptographic commitment. It's a collision resistant hash of content.
From Wikipedia (Source):
A digest is a cryptographic hash function (CHF) is a mathematical algorithm that maps data of an arbitrary size (often called the "message") to a bit array of a fixed size (the "hash value", "hash", or "message digest"). It is a one-way function, that is, a function for which it is practically infeasible to invert or reverse the computation.[1]
Digest and ACDCs
An important property of high-strength cryptographic digests is that a verifiable cryptographic commitment (such as a digital signature) to the digest of some data is equivalent to a commitment to the data itself. Authentic Chained Data Containers (ACDCs) leverage this property to enable compact chains of ACDCs that anchor data via digests. The data contained in an ACDC may therefore be merely its equivalent anchoring digest. The anchored data is thereby equivalently authenticated or authorized by the chain of ACDCs.
digital agent
ToIP
In the context of decentralized digital trust infrastructure, an agent (specifically a type of software agent) that operates in conjunction with a digital wallet.
Note: In a ToIP context, a digital agent is frequently assumed to have privileged access to the digital wallet(s) of its principal. In market parlance, a mobile app that performs the actions of a digital agent is often simply called a wallet or a digital wallet.
digital asset
ToIP
A digital asset is anything that exists only in digital form and comes with a distinct usage right. Data that do not possess that right are not considered assets.
Source: Wikipedia.
See also: digital credential.
digital certificate
ToIP
See: public key certificate.
digital credential
ToIP
A credential in digital form that is signed with a digital signature and held in a digital wallet. A digital credential is issued to a holder by an issuer; a proof of the credential is presented by the holder to a verifier.
See also: issuance request, presentation request, verifiable credential.
Contrast with: physical credential.
Supporting definitions:
Wikipedia: Digital credentials are the digital equivalent of paper-based credentials. Just as a paper-based credential could be a passport, a driver's license, a membership certificate or some kind of ticket to obtain some service, such as a cinema ticket or a public transport ticket, a digital credential is a proof of qualification, competence, or clearance that is attached to a person.
digital ecosystem
ToIP
A digital ecosystem is a distributed, adaptive, open socio-technical system with properties of self-organization, scalability and sustainability inspired from natural ecosystems. Digital ecosystem models are informed by knowledge of natural ecosystems, especially for aspects related to competition and collaboration among diverse entities.
Source: Wikipedia.
See also: digital trust ecosystem, trust community.
digital identity
ToIP
An identity expressed in a digital form for the purpose representing the identified entity within a computer system or digital network.
Supporting definitions:
eSSIF-Lab: Digital data that enables a specific entity to be distinguished from all others in a specific context.
Wikipedia: Digital identity refers to the information utilized by computer systems to represent external entities, including a person, organization, application, or device. When used to describe an individual, it encompasses a person's compiled information and plays a crucial role in automating access to computer-based services, verifying identity online, and enabling computers to mediate relationships between entities.
digital rights management
ToIP
Digital rights management (DRM) is the management of legal access to digital content. Various tools or technological protection measures (TPM) like access control technologies, can restrict the use of proprietary hardware and copyrighted works. DRM technologies govern the use, modification and distribution of copyrighted works (e.g. software, multimedia content) and of systems that enforce these policies within devices.
Source: Wikipedia.
Also known as: DRM.
digital signature
ToIP
A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents. A valid digital signature, where the prerequisites are satisfied, gives a recipient very high confidence that the message was created by a known sender (authenticity), and that the message was not altered in transit (integrity).
Source: Wikipedia.
Supporting definitions:
NIST-CSRC: The result of a cryptographic transformation of data which, when properly implemented, provides the services of: 1. origin authentication, 2. data integrity, and 3. signer non-repudiation.
WebOfTrust
digital signature
Definition
A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents. A valid digital signature, where the prerequisites are satisfied, gives a recipient very strong reason to believe that the message was created by a known sender (authentication), and that the message was not altered in transit (integrity).
Electronic signatures
There are
digital signaturesand Electronic signatures, the latter are quite different in purpose and practical use.
digital trust ecosystem
ToIP
A digital ecosystem in which the participants are one or more interoperating trust communities. Governance of the various roles of governed parties within a digital trust ecosystem (e.g., issuers, holders, verifiers, certification bodies, auditors) is typically managed by a governing body using a governance framework as recommended in the ToIP Governance Stack. Many digital trust ecosystems will also maintain one or more trust lists and/or trust registries.
digital trust utility
ToIP
An information system, network, distributed database, or blockchain designed to provide one or more supporting services to higher level components of decentralized digital trust infrastructure. In the ToIP stack, digital trust utilities are at Layer 1. A verifiable data registry is one type of digital trust utility.
digital vault
ToIP
A secure container for data whose controller is the principal. A digital vault is most commonly used in conjunction with a digital wallet and a digital agent. A digital vault may be implemented on a local device or in the cloud; multiple digital vaults may be used by the same principal across different devices and/or the cloud; if so they may use some type of synchronization. If the capability is supported, data may flow into or out of the digital vault automatically based on subscriptions approved by the controller.
Also known as: data vault, encrypted data vault.
See also: enterprise data vault, personal data vault, virtual vault.
For more information, see: https://en.wikipedia.org/wiki/Personal_data_service, https://digitalbazaar.github.io/encrypted-data-vaults/
digital wallet
ToIP
A user agent, optionally including a hardware component, capable of securely storing and processing cryptographic keys, digital credentials, digital assets and other sensitive private data that enables the controller to perform cryptographically verifiable operations. A non-custodial wallet is directly in the custody of a principal. A custodial wallet is in the custody of a third party. Personal wallets are held by individual persons; enterprise wallets are held by organizations or other legal entities.
See also: digital agent, key management system, wallet engine.
Supporting definitions:
eSSIF-Lab: a component that implements the capability to securely store data as requested by colleague agents, and to provide stored data to colleague agents or peer agents, all in compliance with the rules of its principal's wallet policy.
Wikipedia: A digital wallet, also known as an e-wallet, is an electronic device, online service, or software program that allows one party to make electronic transactions with another party bartering digital currency units for goods and services. This can include purchasing items either online or at the point of sale in a brick and mortar store, using either mobile payment (on a smartphone or other mobile device) or (for online buying only) using a laptop or other personal computer. Money can be deposited in the digital wallet prior to any transactions or, in other cases, an individual's bank account can be linked to the digital wallet. Users might also have their driver's license, health card, loyalty card(s) and other ID documents stored within the wallet. The credentials can be passed to a merchant's terminal wirelessly via near field communication (NFC).
Note: In market parlance, a mobile app that performs the actions of a digital agent and has access to a set of cryptographic keys is often simply called a wallet or a digital wallet.
dip
WebOfTrust
dip
Definition
dip = delcept, delegated inception
direct mode
ToIP (DID:Webs)
an operational mode of the KERI protocol where a controller and a verifier of an AID exchange the KEL of the AID directly, as defined by the KERI whitepaper. See WebOfTrust glossary for more detail.WebOfTrust
direct mode
Definition
Two primary trust modalities motivated the KERI design, One of these is the direct (one-to-one) mode, in which the identity controller establishes control via verified signatures of the controlling key-pair. The direct mode doesn't use witnesses nor KERLs, but has direct (albeit intermittent) network contact with the validator.
Operational mode
To protect a validator when engaging with some other controller’s identifier, be it verification, control authority establishment, or duplicity detection, are based on an ability to replay the sequence of key events (key event history or log) of that identifier. There are two main operational modes for providing replay capability that are distinguished by the degree of availability of the identifier’s controller when creating and promulgating the key events.
With direct mode, the promulgation of events to a validator does not happen unless the controller is attached to the network and able to communicate directly with a validator.
Direct mode assumes that the controller may have intermittent network availability, it also assumes that these mechanism may not be trusted in any persistent sense to promulgate key events. Nonetheless, direct mode is important as it is compatible with the use of mobile internet devices such as cell phones. A single direct mode identifier may be re-used in multiple one-to-one relationships as part of a select group.
More in Source: chapter Protocol Operational Modes in KERI white paperSecurity concerns
The protocol may operate in two basic modes, called direct and indirect. The availability and consistency attack surfaces are different for the two modes and hence the mitigation properties of the protocol are likewise mode specific.
Also see
directed acyclic graph
WebOfTrust
directed acyclic graph
Definition
From Wikipedia (source):
In mathematics, particularly graph theory, and computer science, a directed acyclic graph (DAG /ˈdæɡ/ (listen)) is a directed graph with no directed cycles. That is, it consists of vertices and edges (also called arcs), with each edge directed from one vertex to another.
Why a directed acyclic graph (DAG)
Following directions in a DAG will never form a closed loop. Steps through a DAG are finite. That's the main reason to choose for a DAG.
Unique properties
From Wikipedia (source):
A directed graph is a DAG if and only if it can be topologically ordered, by arranging the vertices as a linear ordering that is consistent with all edge directions.
Applications
From Wikipedia (source):
DAGs have numerous scientific and computational applications, ranging from biology (evolution, family trees, epidemiology) to information science (citation networks) to computation (scheduling).
disclosee
WebOfTrust
disclosee
Definition
an ACDC in a disclosure is disclosed to the Disclosee
discloser
WebOfTrust
discovery
WebOfTrust
discovery
Definition
A mechanism that helps systems or devices find each other automatically, often used in networks to identify services or resources. In decentralized identifier systems it helps to locate and verify digital identities without relying on a central authority.
Related but not the same
distributed hash table
WebOfTrust
distributed hash table
Definition
It is a distributed system that provides a lookup service similar to a hash table: key-value pairs are stored in a DHT, and any participating node can efficiently retrieve the value associated with a given key. The main advantage of a DHT is that nodes can be added or removed with minimum work around re-distributing keys. Keys are unique identifiers which map to particular values, which in turn can be anything from addresses, to documents, to arbitrary data.
(Source: Wikipedia)
distributed ledger
ToIP
A distributed ledger (also called a shared ledger or distributed ledger technology or DLT) is the consensus of replicated, shared, and synchronized digital data that is geographically spread (distributed) across many sites, countries, or institutions. In contrast to a centralized database, a distributed ledger does not require a central administrator, and consequently does not have a single (central) point-of-failure. In general, a distributed ledger requires a peer-to-peer (P2P) computer network and consensus algorithms so that the ledger is reliably replicated across distributed computer nodes (servers, clients, etc.). The most common form of distributed ledger technology is the blockchain, which can either be on a public or private network.
Source: Wikipedia.
distributed ledger (DLT)
W3C (DID)
A non-centralized system for recording events. These systems establishsufficient confidence for participants to rely upon the data recorded by othersto make operational decisions. They typically use distributed databases wheredifferent nodes use a consensus protocol to confirm the ordering ofcryptographically signed transactions. The linking of digitally signedtransactions over time often makes the history of the ledger effectivelyimmutable.
dnd
WebOfTrust
dnd
Definition
Do Not Delegate is a flag / attribute for a AID and this is default set to you can delegate.
| TBW |
domain
Nist
A set of elements, data, resources, and functions that share a commonality in combinations of (1) roles supported, (2) rules governing their use, and (3) protection needs.ToIP
See: security domain.
See also: trust domain.
WebOfTrust
domain name
WebOfTrust
domain name
Definition
A domain name is a string that identifies a realm of administrative autonomy, authority or control within the Internet. Domain names are used in various networking contexts and for application-specific naming and addressing purposes.
More on Source Wikipedia.
double spend proof
WebOfTrust
double spend proof
Definition
Total global ordering of transaction so that value can’t be spend twice at the same time from the unit of value. Or in common language: you can't spend your money twice.
| TBW |
KERI related
The most important feature of a cryptocurrency is that it must be double spend proof. Because KERI's key event operations are idempotent they do not need to be double spend proofed, so we can greatly simplify the distributed consensus algorithm in KERI. Which makes KERI relatively more attractive for many applications including IoT applications by comparison.
As a result of the relaxation of double spend proofing, KERI is able to break the distributed consensus algorithm into two halves and simplify it in the process. The two halves are the promulgation half (by witnesses) and the confirmation half (by valdators).
drt
WebOfTrust
drt
Definition
drt = deltate, delegated rotation
dual indexed codes
WebOfTrust
dual indexed codes
Definition
a context-specific coding scheme, for the common use case of thresholded multi-signature schemes in CESR.
Related to CESR
One way to compactly associated each signature with its public key is to include in the text code for that signature the index into the ordered set of public keys.A popular signature raw binary size is 64 bytes which has a pad size of 2. This gives two code characters for a compact text code. The first character is the selector and type code. The second character is the Base64 encoded integer index.
More at source Github Repo Ietf-CESR
dual text binary encoding format
WebOfTrust
dual text binary encoding format
Definition
An encoding format that allows for both text and binary encoding format, which is fully interchangeable. The composability property enables the round trip conversion en-masse of concatenated primitives between the text domain and binary domain while maintaining the separability of individual primitives.
Read more in source of Samuel SmithRelated
duplicitous event log
WebOfTrust
duplicitous event log
Definition
This is a record of inconsistent event messages produced by a given controller or witness with respect to a given KERL. The duplicitous events are indexed to the corresponding event in a KERL. A duplicitous event is represented by a set of two or more provably mutually inconsistent event messages with respect to a KERL. Each juror keeps a duplicitous event log (DEL) for each controller and all designated witness with respect to a KERL. Any validator may confirm duplicity by examining a DEL.
duplicity
WebOfTrust
duplicity
Duplicity
Duplicity is used to describe external inconsistency. Publication of two or more versions of a KEL, each of which is internally consistent is duplicity. Given that signatures are non-repudiable any duplicity is detectable and provable given possession of any two mutually inconsistent versions of a KEL. In KERI consistency is is used to described data that is internally consistent and cryptographically verifiably so.
KERI related
Duplicity means the existence of more than one version of a verifiable KEL for a given AID. Because every event in a KEL must be signed with non-repudiable signatures any inconsistency between any two instances of the KEL for a given AID is provable evidence of duplicity on the part of the signers with respect to either or both the key-state of that AID and/or any anchored data at a given key-state. A shorter KEL that does not differ in any of its events with respect to another but longer KEL is not duplicitous but merely incomplete. To clarify, duplicity evident means that duplicity is provable via the presentation of a set of two or more mutually inconsistent but independently verifiable instances of a KEL.Source Sam Smith
Outside world
In common language 'duplicity' has a slightly different connotation: 'two-facedness', 'dishonesty', 'deceitfulness', 'deviousness,'two-facedness', 'falseness'.
duplicity detection
WebOfTrust
duplicity detection
Definition
A mechanism to detect duplicity in cryptographically secured event logs.
KERI related
Duplicity detection, which protects, not against an external attacker, but against a malicious controller does require access to watchers that are also recording duplicitous events.
eIDAS
ToIP
eIDAS (electronic IDentification, Authentication and trust Services) is an EU regulation with the stated purpose of governing "electronic identification and trust services for electronic transactions". It passed in 2014 and its provisions came into effect between 2016-2018.
Source: Wikipedia.
eSSIF-Lab World Model
Essif-Lab
the set of concept, relations between them (pattern), and Principles (that are the starting point for eSSIF-Lab's thinking).
eclipse attack
WebOfTrust
eclipse attack
Definition
An eclipse attack is a P2P network-based attack. Eclipse attack can only be performed on nodes that accept incoming connections from other nodes, and not all nodes accept incoming connections.
In a bitcoin network, by default, there are a maximum of 117 incoming TCP connections and 8 outgoing TCP connections.
SourceKERI related
The only attack on KERI possible is an eclipse attack, so the larger your watcher network reach is the better your protection from this type of attack. The only limitation is a resource constraint.
Source Samuel Smith / Phil FeairhellerWorking of Eclipse Attack
Eclipse attacks are possible because nodes within the network are unable to connect with all other nodes and can connect with a limited number of neighboring nodes. This limitation might make it seem convenient for attackers to isolate a node from the rest of the network, but it is not an easy task.
More at Source GeeksforGeeks
ecosystem
ToIP
See: digital ecosystem.
ecosystem governance framework
ToIP
A governance framework for a digital trust ecosystem. An ecosystem governance framework may incorporate, aggregate, or reference other types of governance frameworks such as a credential governance framework or a utility governance framework.
electronic signature
WebOfTrust
electronic signature
Definition
An electronic signature, or e-signature, refers to data in electronic form, which is logically associated with other data in electronic form and which is used by the signatory to sign. This type of signature has the same legal standing as a handwritten signature as long as it adheres to the requirements of the specific regulation under which it was created (e.g., eIDAS in the European Union, NIST-DSS in the USA or ZertES in Switzerland).
Digital signature implementation of e-signatures
Electronic signatures are a legal concept distinct from digital signatures, a cryptographic mechanism often used to implement electronic signatures. While an electronic signature can be as simple as a name entered in an electronic document, digital signatures are increasingly used in e-commerce and in regulatory filings to implement electronic signatures in a cryptographically protected way.
encrypt sender sign receiver
WebOfTrust
encrypt sender sign receiver
Definition
An authenticated encryption approach, using PKI. It covers authenticity and confidentiality.
encrypted data vault
ToIP
See: digital vault.
encryption
ToIP
Cryptographic transformation of data (called plaintext) into a form (called ciphertext) that conceals the data’s original meaning to prevent it from being known or used. If the transformation is reversible, the corresponding reversal process is called decryption, which is a transformation that restores encrypted data to its original state.
Source: NIST-CSRC.
end role
end to end
WebOfTrust
end to end
Definition
Inter-host communication and data flow transformations, considered in motion and at rest.1. E2E Security. Inter-host communication must be end-to-end signed/encrypted and data must be stored signed/encrypted. Data is signed/encrypted in motion and at rest.
2. E2E Provenance. Data flow transformations must be end-to-end provenanced using verifiable data items (verifiable data chains or VCs). Every change shall be provenanced.Paraphrased from source Universal Identifier Theory by Samuel Smith
end verifiable
WebOfTrust
end verifiable
Definition
When a log is end verifiable, it means that the log may be verified by any end user that receives a copy. No trust in intervening infrastructure is needed to verify the log and validate the content.
end-to-end encryption
ToIP
Encryption that is applied to a communication before it is transmitted from the sender’s communication endpoint and cannot be decrypted until after it is received at the receiver’s communication endpoint. When end-to-end encryption is used, the communication cannot be decrypted in transit no matter how many intermediary systems are involved in the routing process.
Supporting definitions:
Wikipedia: End-to-end encryption (E2EE) is a private communication system in which only communicating users can participate. As such, no one, including the communication system provider, telecom providers, Internet providers or malicious actors, can access the cryptographic keys needed to converse. End-to-end encryption is intended to prevent data being read or secretly modified, other than by the true sender and recipient(s). The messages are encrypted by the sender but the third party does not have a means to decrypt them, and stores them encrypted. The recipients retrieve the encrypted data and decrypt it themselves.
endpoint
ToIP
See: communication endpoint.
See also: ToIP endpoint.
endpoint system
ToIP
The system that operates a communications endpoint. In the context of the ToIP stack, an endpoint system is one of three types of systems defined in the ToIP Technology Architecture Specification.
See also: intermediary system, supporting system.
engagement context role
WebOfTrust
engagement context role
Definition
A person that represents the Legal Entity in a functional or in another context role and is issued an ECR vLEI Credential.
Issuance of credentials
On the basis of Legal entity engagement context role vLEI credential governance framework an ECR vLEI Credential is issued to an engagement context role (ECR).
enrol ~ment
digital.govt.nz
to become or cause to become a member; enlist; register[Source: Dictionary]
enterprise data vault
ToIP
A digital vault whose controller is an organization.
enterprise wallet
ToIP
A digital wallet whose holder is an organization.
Contrast with: personal wallet.
entity
digital.govt.nz
something that has real or distinct existence from other things[Source: Dictionary]ToIP
Someone or something that is known to exist.
Source: eSSIF-Lab.
WebOfTrust
entropy
WebOfTrust
entropy
Definition
Unpredictable information. Often used as a secret or as input to a key generation algorithm.
More on Wikipedia
The term entropy is also used to describe the degree of unpredictability of a message. Entropy is then measured in bits. The degree or strength of randomness determines how difficult it would be for someone else to reproduce the same large random number. This is called collision resistance.
ephemeral
WebOfTrust
ephemeral
Definition
Lasting for a markedly brief time. Having a short lifespan.
In the context of identifiers is often referred to as identifiers for one time use; or throw-away identifiers.
ephemeral connection
ToIP
A connection that only exists for the duration of a single communication session or transaction.
Contrast with: persistent connection.
escrow
WebOfTrust
escrow
Definition
'Escrow' as a noun is a (legal) arrangement in which a third party temporarily holds money or property until a particular condition has been met.
'Escrow' as a verb: we use it in protocol design to handle out of order events. Store the event and wait for the other stuff to show up and then continue processing of the event. So escrowing is the process of storing this event. We root back to the event later.
escrow state
WebOfTrust
escrow state
Definition
The current state of all the temporary storage locations (what events are waiting for what other information) that KERI protocol needs to keep track of, due to its fully asynchronous nature.
Inner-working and motivation
Since the KERI protocol is fully asynchronous, there is no way to guarantee that events will arrive in order to be processed successfully. This includes things like anchoring events for transaction event logs for credentials (the TEL even could arrive before the anchoring event) and signatures arriving on a multisig event.
To account for this asynchronous nature, implementations need to "escrow" events (store them temporarily) while waiting for other events or additional signatures to show up. The current state of all the temporary storage locations (what events are waiting for what other information) is called the "escrow state".
Source: Philip FeairhellerBeware
An physical Escrow State that you might know from Real Estate transaction is not at all related to the one we define.
establishment event
WebOfTrust
establishment event
Definition
A key creation or rotation event that establishes or transfers control authority for an identifier.
Establishment events indicate which key pairs are authoritative (controlling) for an identifier at a given point in time.
The subset of a key event log (KEL) that are establishment events are an ordered subsequence of the full KEL.
For a non-transferable identifier this is one authoritative key pair and it never changes so there will only ever be one establishment event, the inception event.
For transferable identifiers there can be multiple establishment events which would include the initial rotation event and any subsequent rotation events.
Source Sam Smith
evidence
digital.govt.nz
to give proof of or evidence for[Source: Dictionary]
exn
WebOfTrust
exn
Definition
exn = exchange
exp
WebOfTrust
exp
Definition
exp = expose, sealed data exposition
expression language
ToIP
A language for creating a computer-interpretable (machine-readable) representation of specific knowledge.
Source: Wikipedia.
extensible business reporting language
WebOfTrust
extensible business reporting language
Definition
XBRL is the open international standard for digital business reporting, managed by a global not for profit consortium, XBRL International.
Practical
XBRL provides a language in which reporting terms can be authoritatively defined. Those terms can then be used to uniquely represent the contents of financial statements or other kinds of compliance, performance and business reports. XBRL lets reporting information move between organisations rapidly, accurately and digitally.
SourceTechnical
XBRL stands for eXtensible Business Reporting Language. It is one of a family of “XML” languages which is becoming a standard means of communicating information between businesses and on the internet.
Source
facilitate~ion
digital.govt.nz
to make easier; assist the progress of[Source: Dictionary]
facilitation providerFP
digital.govt.nz
the party accountable for the establishment and functioning of a facilitation mechanism[Source: New definition]Additional note:Note 1: A facilitation mechanism facilitates the presentation of 1 or more Credentials to a Relying Party.
federated identity
ToIP
A digital identity architecture in which a digital identity established on one computer system, network, or trust domain is linked to other computer systems, networks, or trust domains for the purpose of identifying the same entity across those domains.
See also: decentralized identity, self-sovereign identity.
Supporting definitions:
NIST-CSRC; A process that allows for the conveyance of identity and authentication information across a set of networked systems.
Wikipedia: A federated identity in information technology is the means of linking a person's electronic identity and attributes, stored across multiple distinct identity management systems.
federate~d~ion
digital.govt.nz
united by common agreement under an authority[Source: Dictionary modified to remove central government]
federation
ToIP
A group of organizations that collaborate to establish a common trust framework or governance framework for the exchange of identity data in a federated identity system.
See also: trust community
Supporting definitions:
NIST-CSRC: A collection of realms (domains) that have established trust among themselves. The level of trust may vary, but typically includes authentication and may include authorization.
federation assurance level
ToIP
A category that describes the federation protocol used to communicate an assertion containing authentication and attribute information (if applicable) to a relying party, as defined in NIST SP 800-63-3 in terms of three levels: FAL 1 (Some confidence), FAL 2 (High confidence), FAL 3 (Very high confidence).
Source: NIST-CSRC.
See also: authenticator assurance level, identity assurance level.
fiduciary
ToIP
A fiduciary is a person who holds a legal or ethical relationship of trust with one or more other parties (person or group of persons). Typically, a fiduciary prudently takes care of money or other assets for another person. One party, for example, a corporate trust company or the trust department of a bank, acts in a fiduciary capacity to another party, who, for example, has entrusted funds to the fiduciary for safekeeping or investment. In a fiduciary relationship, one person, in a position of vulnerability, justifiably vests confidence, good faith, reliance, and trust in another whose aid, advice, or protection is sought in some matter.
Source: Wikipedia.
field map
WebOfTrust
field map
Definition
A traditional
key:valuepair renamed to avoid confusing with the cryptographic use of the term 'key'.To avoid confusion with the cryptographic use of the term key we instead use the term field to refer to a mapping pair and the terms field label and field value for each member of a pair. These pairs can be represented by two tuples e.g (
label, value). We qualify this terminology when necessary by using the term field map to reference such a mapping.Nested field maps
Field maps may be nested where a given field value is itself a reference to another field map. We call this nested set of fields a nested field map or simply a nested map for short.
first party
ToIP
The party who initiates a trust relationship, connection, or transaction with a second party.
See also: third party, fourth party.
first seen
WebOfTrust
first seen
Definition
A "First seen" event in KERI refers to the first event received by validator such as a witness and that is valid and fits the available tail sequence number in the validator's KEL, and therefore is accepted into the validator's KEL. This rule has no effect on the timing of what has arrived in escrow for example; in escrow there can be garbage. Assuming a watched set of validators agree on the first-seen events and thus also agree on the KELs, the watchers of those validators will propagate only those first-seen events within microseconds.
The rule
From the perspective of a validator, the rule is "First seen, always seen, never unseen".
Key Compromise, Duplicity, and Recovery
Different validators might have a different first-seen number for the same originating transaction event. In the case of duplicitous (inconsistent) interaction events originating from the controller (of the current signing key(s)), which might not be discovered until after a key rotation, a recovery process involving judges and jury may be triggered. More here. Validators will not provide an outdated KEL or Event once an erroneous KEL has been corrected.
foreign function interface
WebOfTrust
foreign function interface
Definition
Is a mechanism by which a program written in one, usually an interpreted (scripted), programming language that can call routines or make use of services written or compiled in another one.
More on Source: https://en.wikipedia.org/wiki/Foreign_function_interfaceRelevance in CESR
To have the output from RUST-based developed (e.g. cesride) consumed by higher level languages.
forgery
digital.govt.nz
the act of reproducing something for a deceitful or fraudulent purpose[Source: Dictionary]
foundational identity
ToIP
A set of identity data, such as a credential, issued by an authoritative source for the legal identity of the subject. Birth certificates, passports, driving licenses, and other forms of government ID documents are considered foundational identity documents. Foundational identities are often used to provide identity binding for functional identities.
Contrast with: functional identity.
fourth party
ToIP
A party that is not directly involved in the trust relationship between a first party and a second party, but provides supporting services exclusively to the first party (in contrast with a third party, who in most cases provides supporting services to the second party). In its strongest form, a fourth party has a fiduciary relationship with the first party.
frame code
WebOfTrust
full disclosure
WebOfTrust
full disclosure
Definition
A disclosure of data in all its details.
When used in the context of selective disclosure, full disclosure means detailed disclosure of the selectively disclosed attributes not detailed disclosure of all selectively disclosable attributes. Whereas when used in the context of partial disclosure, full disclosure means detailed disclosure of the field map that was so far only partially disclosed.
fully compact
WebOfTrust
fully compact
definition
The most compact form of an ACDC. This is the only signed variant of an ACDC and this signature is anchored in a transaction event log (TEL) for the ACDC.This is one valid choice for an ACDC schema.
This form is part of the graduated disclosure mechanism in ACDCs.Anchoring to the TEL
The extra a fully compact version has to offer over a most compact version is the anchoring to the Tranaction event log. Here were various proofs (hashes) can be "stored" which are optional in all kind of ACDC variants.
See
Fully (expanded) version of an ACDC
Most compact version of an ACDC.Analogy
A fully compact ACDC is like the core of an onion and the fully expanded ACDC is like rest of the outer layers of the onion. Turn this onion inside-out: you only need to sign the core (most compact), and then the whole onion (expanded version) would verify. The complete (expanded) onion is the most user friendly information bulb you can get, and you don't need to peel off all the rings of the onion to securely attribute all the information to the controller of the SAID that signed the core.
You can present any version of the onion you like: only the core, one partially stripped back, one layer at a time, or the whole thing (fully expanded). This illustrates part of the rational for why ACDCs matter. They offer a layered, graduated disclosure mechanism of verifiable credentials never seen before in the SSI field.
fully expanded
WebOfTrust
fully expanded
Definition
The most user-friendly version of an ACDC credential. It doesn't need to be signed and typically is not signed since the most compact version which is signed can be computed from this form and then the signature can be looked up in the transaction event log of the ACDC in question.
Regarding the graduated disclosure objective this form is the one with the highest amount of disclosure for a given node of an ACDC graph.
See also
Fully compact(ed) version of an ACDC
Most compact version of an ACDC.
functional identity
ToIP
A set of identity data, such as a credential, that is issued not for the purpose of establishing a foundational identity for the subject, but for the purpose of establishing other attributes, qualifications, or capabilities of the subject. Loyalty cards, library cards, and employee IDs are all examples of functional identities. Foundational identities are often used to provide identity binding for functional identities.
gateway
ToIP
A gateway is a piece of networking hardware or software used in telecommunications networks that allows data to flow from one discrete network to another. Gateways are distinct from routers or switches in that they communicate using more than one protocol to connect multiple networks[1][2] and can operate at any of the seven layers of the open systems interconnection model (OSI).
See also: intermediary.
Source: Wikipedia.
ghost credential
WebOfTrust
ghost credential
Definition
Is a valid credential within in a 90 days grace period (the revocation transaction time frame before it's booked to revocation registry). | TBW prio 3 |
Design
When a relationship needs to be terminated with a QVI and the QVI has not revoked their credentials (yet) then those credentials become ghost credentials.
gleif authorized representative
glossary
ToIP
A glossary (from Ancient Greek: γλῶσσα, glossa; language, speech, wording), also known as a vocabulary or clavis, is an alphabetical list of terms in a particular domain of knowledge (scope) together with the definitions for those terms. Unlike a dictionary, a glossary has only one definition for each term.
Source: Wikipedia.
gnu privacy guard
WebOfTrust
gnu privacy guard
Definition
also GnuPG; is a free-software replacement for Symantec's PGP cryptographic software suite. It is compliant with RFC 4880, the IETF standards-track specification of OpenPGP. Modern versions of PGP are interoperable with GnuPG and other OpenPGP-compliant systems.
More on wikipedia
See more about the closely related and often-confusing term PGP.
governance
ToIP
The act or process of governing or overseeing the realization of (the results associated with) a set of objectives by the owner of these objectives, in order to ensure they will be fit for the purposes that this owner intends to use them for.
Source: eSSIF-Lab.
governance diamond
ToIP
A term that refers to the addition of a governing body to the standard trust triangle of issuers, holders, and verifiers of credentials. The resulting combination of four parties represents the basic structure of a digital trust ecosystem.
governance document
ToIP
A document with at least one identifier that specifies governance requirements for a trust community.
Note: A governance document is a component of a governance framework.
governance framework
ToIP
A collection of one or more governance documents published by the governing body of a trust community.
Also known as: trust framework.
Note: In the digital identity industry specifically, a governance framework is better known as a trust framework. ToIP-conformant governance frameworks conform to the ToIP Governance Architecture Specification and follow the ToIP Governance Metamodel.
WebOfTrust
governance framework
Definition
Also called 'Governance structure'. Governance frameworks are the structure of a government and reflect the interrelated relationships, factors, and other influences upon the institution. Governance frameworks structure and delineate power and the governing or management roles in an organization. They also set rules, procedures, and other informational guidelines.
More in source Wikipedia.Related to GLEIF and vLEI
In addition, governance frameworks define, guide, and provide for enforcement of these processes. These frameworks are shaped by the goals, strategic mandates, financial incentives, and established power structures and processes of the organization.
Within GLEIF context, governance frameworks manifest in a document that details the requirements for vLEI credentials.
governance graph
ToIP
A graph of the governance relationships between entities with a trust community. A governance graph shows which nodes are the governing bodies and which are the governed parties. In some cases, a governance graph can be traversed by making queries to one or more trust registries.Note: a party can play both roles and also be a participant in multiple governance frameworks.
See also: authorization graph, reputation graph, trust graph.
governance requirement
ToIP
A requirement such as a policy, rule, or technical specification specified in a governance document.
See also: technical requirement.
governed information
ToIP
Any information published under the authority of a governing body for the purpose of governing a trust community. This includes its governance framework and any information available via an authorized trust registry.
governed party
ToIP
A party whose role(s) in a trust community is governed by the governance requirements in a governance framework.
governed use case
ToIP
A use case specified in a governance document that results in specific governance requirements within that governance framework. Governed use cases may optionally be discovered via a trust registry authorized by the relevant governance framework.
governing authority
ToIP
See: governing body.
governing body
ToIP
The party (or set of parties) authoritative for governing a trust community, usually (but not always) by developing, publishing, maintaining, and enforcing a governance framework. A governing body may be a government, a formal legal entity of any kind, an informal group of any kind, or an individual. A governing body may also delegate operational responsibilities to an administering body.
Also known as: governing authority.
graduated disclosure
WebOfTrust
graduated disclosure
Definition
Lifting confidentiality step by step: Selectively disclosing more data as time and/or necessity progresses, offering backwards verifiability of earlier issued cryptographic proofs.
Example
You proof your insurance policy without disclosing details, before enjoying extreme sports. Only when something goes wrong, e.g. 1 in a 100, you disclose the data. This way confidentiality is kept in 99% of the cases.
KERI specific
Disclosure performed by a presentation exchange that has cross-variant (see compact variant) Issuer commitment verifiability as an essential property. It supports graduated disclosure by the Disclosee of any or all variants wether it be full, compact, metadata, partial, selective, bulk issued, or contractually protected.
Paraphrased by @henkvancann based on sourceReuse
The SAID of a given variant is useful even when it is not the SAID of the variant the Issuer signed because during graduated disclosure the Discloser MAY choose to sign that given variant to fulfil a given step in an IPEX graduated disclosure transaction.
Rule
The disclosure performed by a presentation exchange MAY be graduated and MAY be contractually protected.
Related terms
| TBW | check prio 1
graph fragment
WebOfTrust
graph fragment
Definition
An ACDC is a verifiable data structure and part of a graph, consisting of a node property and one or two edge proporties.
group code
WebOfTrust
group framing code
WebOfTrust
group framing code
Definition
special framing codes can be specified to support groups of primitives in CESR. Grouping enables pipelining. Other suitable terms for these special framing codes are group codes or count codes for short. These are suitable terms because these framing codes can be used to count characters, primitives in a group, or groups of primitives in a larger group when parsing and off-loading a stream of CESR primitives.\
SourceComposability property
One of the primary advantages of composable encoding is that we can use special framing code to support the above mentioned grouping.
guardian
ToIP
A party that has been assigned rights and duties in a guardianship arrangement for the purpose of caring for, protecting, guarding, and defending the entity that is the dependent in that guardianship arrangement. In the context of decentralized digital trust infrastructure, a guardian is issued guardianship credentials into their own digital wallet in order to perform such actions on behalf of the dependent as are required by this role.
Source: eSSIF-Lab
See also: custodian, zero-knowledge service provider.
Mental Model: eSSIF-Lab Guardianship
Supporting definitions:
Wikipedia: A legal guardian is a person who has been appointed by a court or otherwise has the legal authority (and the corresponding duty) to make decisions relevant to the personal and property interests of another person who is deemed incompetent, called a ward.
For more information, see: On Guardianship in Self-Sovereign Identity V2.0 (April, 2023).
Note: A guardian is a very different role than a custodian, who does not take any actions on behalf of a principal unless explicitly authorized.
guardianship arrangement
ToIP
A guardianship arrangement (in a jurisdiction) is the specification of a set of rights and duties between legal entities of the jurisdiction that enforces these rights and duties, for the purpose of caring for, protecting, guarding, and defending one or more of these entities. At a minimum, the entities participating in a guardianship arrangement are the guardian and the dependent.
Source: eSSIF-Lab
See also: custodianship arrangement.
Mental Model: eSSIF-Lab Guardianship
For more information, see: On Guardianship in Self-Sovereign Identity V2.0 (April, 2023).
guardianship credential
ToIP
A digital credential issued by a governing body to a guardian to empower the guardian to undertake the rights and duties of a guardianship arrangement on behalf of a dependent.
hab
habery
WebOfTrust
habery
Definition
'Hab' comes from ‘Habitat’. It’s a place where multi-sigs and AIDs are linked. Habery manages a collection of Habs. A Hab is a datastructure (a Python object).
| TBW |-prio2
Beware
The only hit (2022) in a Google search pointing to a github site 'habery DOT github DOT io' is NOT related.
hardware security module
ToIP
A physical computing device that provides tamper-evident and intrusion-resistant safeguarding and management of digital keys and other secrets, as well as crypto-processing.
Source: NIST-CSRC.
Also known as: HSM.
Supporting definitions:
NIST-CSRC: A physical computing device that provides tamper-evident and intrusion-resistant safeguarding and management of digital keys and other secrets, as well as crypto-processing. FIPS 140-2 specifies requirements for HSMs.
Wikipedia: A physical computing device that safeguards and manages secrets (most importantly digital keys), performs encryption and decryption functions for digital signatures, strong authentication and other cryptographic functions. These modules traditionally come in the form of a plug-in card or an external device that attaches directly to a computer or network server. A hardware security module contains one or more secure cryptoprocessor chips.
WebOfTrust
hardware security module
Definition
A HSM is a physical computing device that safeguards and manages secrets (most importantly digital keys), performs encryption and decryption functions for digital signatures, strong authentication and other cryptographic functions.
More in source Wikipedia
hash
ToIP
The result of applying a hash function to a message.
Source: NIST-CSRC.
Also known as: hash output, hash result, hash value.
hash function
ToIP
An algorithm that computes a numerical value (called the hash value) on a data file or electronic message that is used to represent that file or message, and depends on the entire contents of the file or message. A hash function can be considered to be a fingerprint of the file or message. Approved hash functions satisfy the following properties: one-way (it is computationally infeasible to find any input that maps to any pre-specified output); and collision resistant (it is computationally infeasible to find any two distinct inputs that map to the same output).
Source: NIST-CSRC.
hierarchical asynchronous coroutines and input output
WebOfTrust
hierarchical asynchronous coroutines and input output
Definition
HIO is an acronym which stands for 'Weightless hierarchical asynchronous coroutines and I/O in Python'.
It's Rich Flow Based Programming Hierarchical Structured Concurrency with Asynchronous IO. That mouthful of terms has been explained further on Github.
HIO builds on very early work on hierarchical structured concurrency with lifecycle contexts from ioflo, ioflo github, and ioflo manuals.
More info on Github
hierarchical composition
WebOfTrust
hierarchical composition
Definition
Encoding protocol that is composable in a hierarchy and enables pipelining (multiplexing and de-multiplexing) of complex streams in either text or compact binary. This allows management at scale for high-bandwidth applications.
Example
| TBW prio2 |
CESR related
Because of count codes and the composability - and concatenation property in CESR, pipelining is possible, which then uses multiplexing (combining self-framing primitives) and de-multiplexing (unravelling self-framing primitives).
hierchical deterministic keys
WebOfTrust
hierchical deterministic keys
Definition
A HDK type is a type of deterministic bitcoin wallet derived from a known seed, that allow for the creation of child keys from the parent key. Because the child key is generated from a known seed there is a relationship between the child and parent keys that is invisible to anyone without that seed. The HD protocol (BIP 32) can generate a near infinite number of child keys from a deterministically-generated seed (chain code) from its parent, providing the functionality of being able to recreate those exact same child keys as long as you have the seed.
More at W3 source
hio
WebOfTrust
hio
Definition
Weightless hierarchical asynchronous coroutines and I/O in Python.
Rich Flow Based Programming Hierarchical Structured Concurrency with Asynchronous IO.More on Github
This very technical topic can best be studied further at the Github Repository
Relation to KERI
Choosing HIO complies with the asynchronous nature of KERI, the minimal sufficient means design principle of KERI and the leading KERIpy implementation.
holder (of a claim or credential)
ToIP
A role an agent performs by serving as the controller of the cryptographic keys and digital credentials in a digital wallet. The holder makes issuance requests for credentials and responds to presentation requests for credentials. A holder is usually, but not always, a subject of the credentials they are holding.
Mental model: W3C Verifiable Credentials Data Model Roles & Information Flows
Supporting definitions:
eSSIF-Lab: a component that implements the capability to handle presentation requests from a peer agent, produce the requested data (a presentation) according to its principal's holder-policy, and send that in response to the request.
W3C VC: A role an entity might perform by possessing one or more verifiable credentials and generating presentations from them. A holder is usually, but not always, a subject of the verifiable credentials they are holding. Holders store their credentials in credential repositories.
holder binding
ToIP
The process of creating and verifying a relationship between the holder of a digital wallet and the wallet itself. Holder binding is related to but NOT the same as subject binding.
host
ToIP
A host is any hardware device that has the capability of permitting access to a network via a user interface, specialized software, network address, protocol stack, or any other means. Some examples include, but are not limited to, computers, personal electronic devices, thin clients, and multi-functional devices.
Source: NIST-CSRC.
Supporting definitions:
Wikipedia: A network host is a computer or other device connected to a computer network. A host may work as a server offering information resources, services, and applications to users or other hosts on the network. Hosts are assigned at least one network address. A computer participating in networks that use the Internet protocol suite may also be called an IP host. Specifically, computers participating in the Internet are called Internet hosts. Internet hosts and other IP hosts have one or more IP addresses assigned to their network interfaces.
ToIP (DID:Webs)
The part of a URL that can be either a domain name or an IP address. This component specifies the server that the client needs to communicate with in order to access the desired resource on the web.
hourglass model
ToIP
An architectural model for layered systems—and specifically for the protocol layers in a protocol stack—in which a diversity of supporting protocols and services at the lower layers are able to support a great diversity of protocols and applications at the higher layers through the use of a single protocol in the spanning layer in the middle—the “neck” of the hourglass.
See also: trust spanning protocol.
For more information, see: https://trustoverip.org/permalink/Design-Principles-for-the-ToIP-Stack-V1.0-2022-11-17.pdf and https://cacm.acm.org/magazines/2019/7/237714-on-the-hourglass-model/abstract
Note: The Internet’s TCP/IP stack follows the hourglass model, and it is the design model for the ToIP stack.
human auditability
ToIP
See: human auditable.
Contrast with: cryptographic verifiability.
human auditable
ToIP
A process or procedure whose compliance with the policies in a trust framework or governance framework can only be verified by a human performing an audit. Human auditability is a primary goal of the ToIP Governance Stack.
Contrast with: cryptographically verifiable.
human experience
ToIP
The processes, patterns and rituals of acquiring knowledge or skill from doing, seeing, or feeling things as a natural person. In the context of decentralized digital trust infrastructure, the direct experience of a natural person using trust applications to make trust decisions within one or more digital trust ecosystems.
Note: Human experience includes social experiences (e.g., rituals, behaviors, ceremonies and rites of passage), as well as customer experience, worker or employee experience, and user experience.
human trust
ToIP
A level of assurance in a trust relationship that can be achieved only via human evaluation of applicable trust factors.
human-readable
ToIP
Information that can be processed by a human but that is not intended to be machine-readable.
icp
WebOfTrust
icp
Definition
icp = incept, inception
identification
digital.govt.nz
the act of identifying or the state of being identified[Source: Dictionary]ToIP
The action of a party obtaining the set of identity data necessary to serve as that party’s identity for a specific entity.
Note: The act of identification of a specific entity is relational to each party that needs to perform that action. Therefore each party may end up with their own set of identity data that meets their specific requirements for their specific scope.
identifier
digital.govt.nz
information that is enough to uniquely represent an entity in a given context[Source: New definition]ToIP
A single attribute—typically a character string—that uniquely identifies an entity within a specific context (which may be a global context). Examples include the name of a party, the URL of an organization, or a serial number for a man-made thing.
Supporting definitions:
eSSIF-Lab: a character string that is being used for the identification of some entity (yet may refer to 0, 1, or more entities, depending on the context within which it is being used).
WebOfTrust
identifier
Definition
Something to uniquely identify (public) identities; pointing to something or someone else.
identifier system
WebOfTrust
identifier system
Definition
a system for uniquely identifying (public) identities
Example identifier system
The International Standard Name Identifier (ISNI) is an identifier system for uniquely identifying the public identities of contributors to media content such as books, television programmes, and newspaper articles. Such an identifier consists of 16 digits. It can optionally be displayed as divided into four blocks.More info on Wikipedia page
The properties of an identifier system:
- Completeness. Every unique object must be assigned an identifier.
- Uniqueness. Each identifier is a unique sequence.
- Exclusivity. Each identifier is assigned to a unique object, and to no other object.
- Authenticity. The objects that receive identification must be verified as the objects that they are intended to be.
- Aggregation. There must be a mechanism to aggregate all of the data, and only that data, that is properly associated with the identifier (i.e., to bundle all of the data that belong to the uniquely identified object).
- Permanence. The identifiers and the associated data must be permanent.
- Reconciliation. There should be a mechanism whereby the data associated with a unique, identified object in one resource can be merged with the data held in another resource, for the same unique object. This process, which requires comparison, authentication, and merging, is known as reconciliation.
- Immutability. In addition to being permanent (i.e., never destroyed or lost), the identifier must never change (
- Security. The identifier system should be as little vulnerable to malicious attack as possible.
- Documentation and quality assurance. Protocols must be written for establishing the identifier system, for assigning identifiers, for protecting the system, and for monitoring the system.
- Centrality. The subject's identifier is the central "key" to which every event for the subject is attached.
- Autonomy. An identifier system has a life of its own.
By (@henkvancann) based on this source
Relationship with KERI / ACDC plus example vLEI
KERI is an thin-layered identifier system generator, offering globally portable identifiers, secure attribution to their root-of-trust, and chained verifiable credential containers (ACDC) to them.
A first implementation of KERI and ACDC has been at GLEIF (.org)
Verifiable Credentials (VCs) and the emerging role of the LEI: Verifiable Credentials are digitally signed credentials that are not only tamper-resistant but capable of being verified in decentralized manner. vLEIs are based on the Trust over IP Authentic Chained Data Container (ACDC) specification (based on the Key Event Receipt Infrastructure (KERI) protocol (github.com/WebOfTrust/keri), both Internet Engineering Task Force (IETF) draft specifications).Verifiable Credentials are digitally signed credentials that are not only tamper-resistant but capable of being verified in decentralized manner. vLEIs are based on the Trust over IP Authentic Chained Data Container (ACDC) specification (based on the Key Event Receipt Infrastructure (KERI) protocol (github.com/WebOfTrust/keri), both Internet Engineering Task Force (IETF) draft specifications).More info on GLEIF site
identity
digital.govt.nz
one or more attributes that allow an entity record to be unique from all others in the contextAdditional noteNote 1: Due to the contextual nature of the attributes that make up an identity and its poor interaction with other words, use of the word identity as a descriptor should be avoided wherever possible.Nist
Unique group element \(0\) for which \(x+0=x\) for each group element \(x\), relative to the binary group operator \(+\).ToIP
A collection of attributes or other identity data that describe an entity and enable it to be distinguished from all other entities within a specific scope of identification. Identity attributes may include one or more identifiers for an entity, however it is possible to establish an identity without using identifiers.
Supporting definitions:
eSSIF-Lab: the combined knowledge about that entity of all parties, i.e. the union of all partial identities of which that entity is the subject.
Note: Identity is relational to the party performing the identification. For example, if 100 different parties have an identity for the same entity, each of them may hold a different set of identity data enabling identification of that entity.
WebOfTrust
identity assurance
WebOfTrust
identity assurance
Definition
The heavy-lifting to be done by a trusted (middle-man) party to establish - and then offer reputational trust. An example of such a party is GLEIF. Instead, KERI is for attributional trust. In the real world you need both.
Read more in source Universal Identifier TheoryOut-of-band
A trusted party might use out-of-band procedures to assure the identity of people (representing parties) but it's not the same as Out-of-band Introductions (OOBIs) to establish attributional trust, which is done with KERI.
identity assurance level
ToIP
A category that conveys the degree of confidence that a person’s claimed identity is their real identity, for example as defined in NIST SP 800-63-3 in terms of three levels: IAL 1 (Some confidence), IAL 2 (High confidence), IAL 3 (Very high confidence).
Source: NIST-CSRC.
See also: authenticator assurance level, federation assurance level.
identity binding
ToIP
The process of associating a set of identity data, such as a credential, with its subject, such as a natural person. The strength of an identity binding is one factor in determining an authenticator assurance level.
See also: identity assurance level, identity proofing.
identity data
identity document
ToIP
A physical or digital document containing identity data. A credential is a specialized form of identity document. Birth certificates, bank statements, and utility bills can all be considered identity documents.
identity proofing
ToIP
The process of a party gathering sufficient identity data to establish an identity for a particular subject at a particular identity assurance level.
See also: identity binding.
Supporting definitions:
NIST-CSRC: The process of providing sufficient information (e.g., identity history, credentials, documents) to establish an identity.
identity provider
ToIP
An identity provider (abbreviated IdP or IDP) is a system entity that creates, maintains, and manages identity information for principals and also provides authentication services to relying applications within a federation or distributed network.
Source: Wikipedia.
Note: The term “identity provider” is used in federated identity systems because it is a required component of their architecture. By contrast, decentralized identity and self-sovereign identity systems do not use the term because they are architected to enable entities to create and control their own digital identities without the need to depend on an external provider.
identity theft
digital.govt.nz
the theft or assumption of a pre-existing identity (or significant part thereof) with or without consent, and, whether, in the case of an individual, the person is living or deceased[Source: Australian Centre for Policing Research]
impersonation
ToIP
In the context of cybersecurity, impersonation is when an attacker pretends to be another person in order to commit fraud or some other digital crime.
Supporting definitions:
Wikipedia: An impersonator is someone who imitates or copies the behavior or actions of another. As part of a criminal act such as identity theft, the criminal is trying to assume the identity of another, in order to commit fraud, such as accessing confidential information, or to gain property not belonging to them. Also known as social engineering and impostors.
inception
WebOfTrust
inception
Definition
The operation of creating an AID by binding it to the initial set of authoritative keypairs and any other associated information. This operation is made verifiable and duplicity evident upon acceptance as the inception event that begins the AID's KEL.
Source Sam Smith
inception event
ToIP (DID:Webs)
A key event that provides the incepting information needed to derive an AID and establish its initial key state, as defined by the KERI specification. See WebOfTrust glossary for more detail.WebOfTrust
inception event
Definition
An inception event is an establishment key event that represents the creation operation of anidentifier including its derivation and its initial set of controlling keys as well as other inceptionor configuration data for supporting infrastructure.
This is the information needed to derive an AID and establish its initial key-state.
There may be one and only one inception event operation performed on an identifier.
Source KERI Whitepaper
Source Sam SmithInception Statement
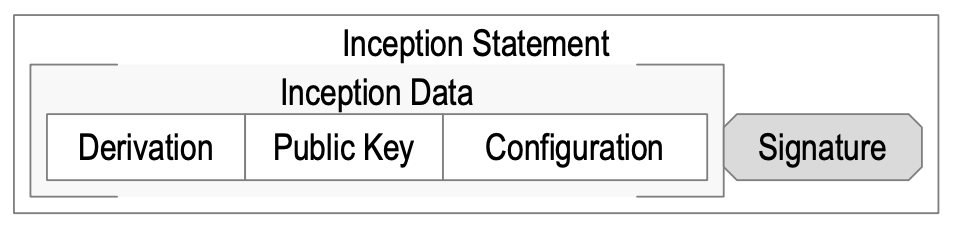
In brief: It's the signed version of a statement containing the inception event with some extra data.
(@henkvancann)Components and self-contained
The inception data must include the public key, the identifier derivation from that public key, and may include other configuration data. The identifier derivation may be simply represented by the
derivation code. A statement that includes the inception data with attached signature made with the private key comprises a cryptographic commitment to the derivation and configuration of the identifier that may be cryptographically verified by any entity that receives it.
A KERI inception statement is completely self-contained. No additional infrastructure is needed or more importantly must be trusted in order to verify the derivation and initial configuration (inception) of the identifier. The initial trust basis for the identifier is simply the signed inception statement.
(SamMSmith)
inconsistency
WebOfTrust
inconsistency
Definition
If a reason, idea, opinion, etc. is inconsistent, different parts of it do not agree, or it does not agree with something else. Data inconsistency occurs when similar data is kept in different formats in more than one file. When this happens, it is important to match the data between files.
KERI related
A data structure like a KEL can be internally inconsistent which is a clear indication that this data structure is not verifiable.
indexed signature
WebOfTrust
indexed signature
Definition
Also called siger. An indexed signature attachment is used when signing anything with a multi-key autonomic identifier. The index is included as part of the attachment, so a verifier knows which of the multiple public keys was used to generate a specific signature.
Source:Philip FeairhellerExample working
An indexed signature attachment would look something like:
03.<binary signature>All encoded as qualified base64. A verifier would then know to use the AID’s public key located at index 3 in the list of public keys to verify the signature.
Source:Philip FeairhellerWitness signatures indexed
In addition, witness signatures can also be attached as indexed signatures. So a verifier can determine which witness signed a particular receipt. This is useful when witnesses are receipting an event and only attaching their own signature. The controller knows which witness signed the receipt by looking up the index in their list of witnesses for that event.
Source:Philip Feairheller
indirect mode
ToIP (DID:Webs)
An operational mode of the KERI protocol where the KEL of an AID is discovered by a verifier via witnesses, as defined by the KERI whitepaper. See WebOfTrust glossary for more detail.WebOfTrust
indirect mode
Definition
Two primary trust modalities motivated the KERI design, One these is the indirect (one-to-many) mode, which depends on witnessed key event receipt logs (KERL) as a secondary root-of-trust for validating events. This gives rise to the acronym KERI for key event receipt infrastructure.
The indirect mode extends that trust basis with witnessed key event receipt logs (KERL) for validating events. The security and accountability guarantees of indirect mode are provided by KA2CE or KERI’s Agreement Algorithm for Control Establishment among a set of witnesses.
Source: Abstract KERI white paperOperational mode
To protect a validator when engaging with some other controller’s identifier, be it verification, control authority establishment, or duplicity detection, are based on an ability to replay the sequence of key events (key event history or log) of that identifier. There are two main operational modes for providing replay capability that are distinguished by the degree of availability of the identifier’s controller when creating and promulgating the key events.
With indirect mode, the promulgation of events to a validator may happen even when the controller is not attached to the network and therefore not able to communicate directly with a validator. Indirect mode supports high (nearly continuous) availability of the key event history to any validator. This means that other components must be trusted to promulgate key events when the controller is not attached to the network. Indirect mode is compatible with identifiers for one-to-many exchanges or any-wise relationships (a controller with any others). A single indirect mode identifier may be used for a public service or business or otherwise when building brand and reputation in that identifier is important. An indirect mode identifier may also be used for private one-to-one or select groups but where intermittent availability is not tolerable.
More in Source: chapter Protocol Operational Modes in KERI white paperSecurity concerns
The protocol may operate in two basic modes, called direct and indirect. The availability and consistency attack surfaces are different for the two modes and hence the mitigation properties of the protocol are likewise mode specific.Source: chapter Security concerns in KERI white paper
Also see
input output
WebOfTrust
input output
Definition
In computing, input/output (I/O, or informally io or IO) is the communication between an information processing system, such as a computer, and the outside world, possibly a human or another information processing system. Inputs are the signals or data received by the system and outputs are the signals or data sent from it. The term can also be used as part of an action; to "perform I/O" is to perform an input or output operation.
More on source Wikipedia
inquisitor
WebOfTrust
inquisitor
Definition
In the ACDC context it's a general term for someone (in a validating role) that launches an inquiry at some KERI witness.
More broadly accepted notion
An inquisitor was an official (usually with judicial or investigative functions) in an inquisition – an organization or program intended to eliminate heresy and other things contrary to the doctrine or teachings.
Source: Wikipedia
integrity
WebOfTrust
integrity
Definition
Integrity (of a message or data) means that the information is whole, sound, and unimpaired (not necessarily correct). It means nothing is missing from the information; it is complete and in intended good order. (Source: Neil Thomson)
KERI suite criteria
In KERI's "security first" approach Authenticity includes technical integrity of data involved. This includes:
- internal consistency
- external consistency or duplicity evident
Integrity in ACDCs is "self-verifying": the SAID that is contained in the data is also the of hash of the data.
The integrity of streaming data in CESR and CESR proof signatures is established by code tables and verifiable by the mere (killer-)feature: round-robin composability. If you can toggle between the text - and binary representation, then that's the integrity proof, if not, then it's provably lacking integrity.
A side-benefit of how integrity is implemented in KERI is non-repudiation - done via a crypto-hash verification via the signer's public key - is not inherent in the meaning of integrity.
Furthermore for KERI integrity, as an assessment of the substance or the content itself, does not fall within its narrow definition. Our criterium is cryptographic verifiability. Once you can't verify, for KERI this type of non-technical integrity is not included in
integrity. For the same reason we wouldn't use validation* as a mechanism to prove integrity.ToIP related
On today's Technology Architecture TF call,..., we defined authenticity to include integrity.
Source ToIP issue 10message integrity seems to be included in
technical integrity.The further separation of Authenticity and Integrity in the ToIP glossary can be largely adopted by KERI? | TBW prio 2 |
See also
verified integrity
(complementary) integrity verification*Validation in relation to integrity, in KERI's view would be an assessment of what's been verified before; in a certain context from a certain angle. And this mechanism is too close to veracity judgement, to be an objective verdict over integrity of data.
integrity (of a data structure)
ToIP
In IT security, data integrity means maintaining and assuring the accuracy and completeness of data over its entire lifecycle. This means that data cannot be modified in an unauthorized or undetected manner.
Source: Wikipedia.
interaction event
ToIP (DID:Webs)
A key event that anchors external data to an AID, as defined by the KERI specification. An interaction event does not change the key state of the AID. See WebOfTrust glossary for more detail.WebOfTrust
interaction event
Non-establishment Event that anchors external data to the key-state as established by the most recent prior establishment event.
Source Sam Smith
interactive authentication design
WebOfTrust
interactive authentication design
Definition
A group of approaches having an interactive mechanism that requires a set of requests and responses or challenge responses with challenge response replies for secure authentication.
More in source Keri Request Authentication Mechanism (KRAM) by Samuel SmithRelated
interceptor
WebOfTrust
interceptor
Definition
a keria class that allows to push events that are happening inside the cloud agent to other backend processes.It is similar to the notifier class but it is used to "notify" other web services.
Origin
interleaved serialisation
WebOfTrust
interleaved serialisation
Definition
Serializations of different types interleaved in an overarching format
CESR related
One extremely useful property of CESR is that special count codes enable CESR to be interleaved with other serializations. For example, Many applications use JSON RFC4627, CBOR RFC8949, or MsgPack (MGPK) to serialize flexible self-describing data structures based on field maps, also known as dictionaries or hash tables.
Source IETF-CESR
intermediary system
ToIP
A system that operates at ToIP Layer 2, the trust spanning layer of the ToIP stack, in order to route ToIP messages between endpoint systems. A supporting system is one of three types of systems defined in the ToIP Technology Architecture Specification.
See also: endpoint system, supporting system.
internal inconsistency
WebOfTrust
internal inconsistency
Definition
Internal is used to describe things that exist or happen inside an entity. In our scope of digital identifiers its (in)consistency is considered within the defining data structures and related data stores.
In KERI we are protected against internal inconsistency by the hash chain datastructure of the KEL, because the only authority that can sign the log is the controller itself.
internet assigned numbers authority
WebOfTrust
internet assigned numbers authority
Definition
is the organization that oversees the allocation of IP addresses to internet service providers (ISPs).
SourceWhat are IANA responsibilities?
In addition to global IP addressing, IANA is also responsible for domain name system (DNS) root zone management, autonomous system numbers and any "unique parameters and protocol values" for the internet community.
SourceMore information
interoperability
WebOfTrust
interoperability
Definition
Interoperability is a characteristic of a product or system to work with other products or systems. While the term was initially defined for information technology or systems engineering services to allow for information exchange.
More on source WikipediaTypes relevant for KERI and ACDC
Identifier interoperability enables users to re-use these identifiers (and their associated data) across different applications. Such interoperability of identifiers encompasses not only technical aspects of interoperability but consideration of the purpose and community of use of the identifiers.
SourceIf two or more systems use common data formats and communication protocols and are capable of communicating with each other, they exhibit syntactic interoperability. XML and SQL are examples of common data formats and protocols. Lower-level data formats also contribute to syntactic interoperability, ensuring that alphabetical characters are stored in the same ASCII or a Unicode format in all the communicating systems.
More on source WikipediaBeyond the ability of two or more computer systems to exchange information, semantic interoperability is the ability to automatically interpret the information exchanged meaningfully and accurately in order to produce useful results as defined by the end users of both systems.
Cross-domain interoperability involves multiple social, organizational, political, legal entities working together for a common interest or information exchange.
More on source Wikipedia
interoperable
WebOfTrust
ip address
WebOfTrust
ip address
An Internet Protocol address (IP address) is a numerical label such as '192.0.2.1' that is connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: network interface identification and location addressing.
Much more on source Wikipedia
iss
WebOfTrust
iss
Definition
iss = vc issue, verifiable credential issuance
issuance
ToIP
The action of an issuer producing and transmitting a digital credential to a holder. A holder may request issuance by submitting an issuance request.
See also: presentation, revocation.
issuance and presentation exchange protocol
WebOfTrust
issuance and presentation exchange protocol
Definition
provides a uniform mechanism for the issuance and presentation of ACDCs in a securely attributable manner.
Relation
A single protocol is able to work for both types of exchanges (issuance and presentation) by recognizing that all exchanges (both issuance and presentation) may be modeled as the disclosure of information by a Discloser to a Disclosee.
The difference between exchange types is the information disclosed not the mechanism for disclosure.More info at source
(Source)
issuance event
WebOfTrust
issuance event
Definition
The initial transaction event log event anchored to the issuing AID’s key event log that represents the issuance of an ACDC credential.
Source: Philip Feairheller.It's a sort of "inception event" of a verifiable credential.
issuance exchange
WebOfTrust
issuance exchange
Definition
A special case of a presentation exchange where the Discloser is the Issuer of the origin (Primary) ACDC of the DAG formed by the set of chained ACDCs so disclosed.
In an issuance exchange, when the origin ACDC has an Issuee, the Disclosee MAY also be the origin ACDC's Issuee.
issuance request
ToIP
A protocol request invoked by the holder of a digital wallet to obtain a digital credential from an issuer.
See also: presentation request.
issuee
WebOfTrust
issuee
Definition
An ACDC is optionally issued to the Issuee. When present, the Issuee identifier (AID) appears at the top level of the attribute section or in the attribute list at the top level of the attribute aggregate section of the ACDC.
Rule
Each ACDC MUST have an Issuer and MAY have an Issuee. The set of ACDCs so disclosed in a presentation exchange MUST be chained. This set of chained ACDCs define a directed acyclic graph that MUST have at least one vertex and MAY have zero or more edges pointing to other vertices.
issuer
Nist
The organization that is issuing the PIV Card to an applicant. Typically, this is an organization for which the applicant is working.WebOfTrust
issuer
Definition
An ACDC is issued by the Issuer. The Issuer identifier (AID) appears in the top level of the ACDC.
Rule
Each ACDC MUST have an Issuer and MAY have an Issuee. The set of ACDCs so disclosed in a presentation exchange MUST be chained. This set of chained ACDCs define a directed acyclic graph that MUST have at least one vertex and MAY have zero or more edges pointing to other vertices.
issuer (of a claim or credential)
ToIP
A role an agent performs to package and digitally sign a set of claims, typically in the form of a digital credential, and transmit them to a holder.
Mental model: W3C Verifiable Credentials Data Model Roles & Information Flows
Supporting definitions:
eSSIF-Lab: a component that implements the capability to construct credentials from data objects, according to the content of its principal's issuer-Policy (specifically regarding the way in which the credential is to be digitally signed), and pass it to the wallet-component of its principal allowing it to be issued.
W3C VC: A role an entity can perform by asserting claims about one or more subjects, creating a verifiable credential from these claims, and transmitting the verifiable credential to a holder.
ixn
WebOfTrust
ixn
Definition
JSON field name (attribute) for Interaction Event; its content (value) contains a hash pointer. All TEL events are anchored in a KEL in either ixn (interaction) or rot (rotation events). This is the foundation enabling a verifiable credential protocol to be built on top of KERI.
Source Kent Bull 2023Also see
javascript object notation (JSON)
WebOfTrust
javascript object notation (JSON)
Definition
JSON (JavaScript Object Notation, pronounced /ˈdʒeɪsən/; also /ˈdʒeɪˌsɒn/) is an open standard file format and data interchange format that uses human-readable text to store and transmit data objects consisting of attribute–value pairs and arrays (or other serializable values). It is a common data format with diverse uses in electronic data interchange, including that of web applications with servers.
Language independent
JSON is a language-independent data format. It was derived from JavaScript, but many modern programming languages include code to generate and parse JSON-format data. JSON filenames use the extension .json.
More on Wikipedia
javascript object signing and encryption
WebOfTrust
javascript object signing and encryption
Definition
is a framework intended to provide a method to securely transfer claims (such as authorization information) between parties. The JOSE framework provides a collection of specifications to serve this purpose.
Related and more info
Related:
JWK,JWT. More info
judge
WebOfTrust
judge
Definition
A judge is an entity or component that examines the entries of one or more KERLs and DELs of a given identifier to validate that the event history is from a non-duplicitous controller and has been witnessed by a sufficient number of non-duplicitous witnesses such that it may be trusted or conversely not-trusted by a validator.
Task and result
A judge determines current [authoritative] key set for identifier from the key event receipt logs from a set of witnesses. Judges transmit the 'judgement' of watchers concerning duplicity.
Where judges run
Example AT&T vs T-Mobile. The only "fault" that is apparent, is an attack on the KEL. And that can only occur via key compromise. So a successful multi-threshold attack causing duplicity is the only thing watchers are looking for.
Competitor and common interest
So even competitors will want to share across the entire ecosystem. Similar to certificate transparency, all competitors in the internet hosting space share the information with each other because it is in their best interest to eliminate fraud / duplicity.
Paraphrased by @henkvancann based on source Samuel Smith / Phil Feairheller
jurisdiction
ToIP
The composition of: a) a legal system (legislation, enforcement thereof, and conflict resolution), b) a party that governs that legal system, c) a scope within which that legal system is operational, and d) one or more objectives for the purpose of which the legal system is operated.
Source: eSSIF-Lab
Mental model: eSSIF-Lab Jurisdictions
juror
WebOfTrust
juror
Definition
A juror has a simpler task of performing duplicity detection on events and event receipts.
jury
WebOfTrust
keep
WebOfTrust
keep
Definition
Is KERI's and ACDC's user interface that uses the keripy agent for its backend. It uses the REST API exposed from the keripy agent.
Source: Philip FeairhellerInterface
Keep is a task orientated application for managing AIDs in ecosystems, e.g. the vLEI Ecosystem.
Usecases
Keep can be used to:
- establish and manage local AIDs
- create, join and manage distributed Multi-Sig AIDs (with or without delegation)
- issue and revoke credentials specified within the vLEI Ecosystem
More info on Github repo of Keep.
keri agreement algorithm for control establishment
WebOfTrust
keri agreement algorithm for control establishment
##DefinitionAgreement on an event in a key event log KEL means each witness has observed the same version of the event and each witness’ receipt has been received by every other witness.
Control establishment means that the set of agreeing witnesses along with the controller, of the identifier and associated keypairs, create a verifiable way to establish control authority for an identifier by reading all of the events in the KEL that have been agreed upon by the witnesses and the controller.
Acronyms: 'KA2CE' 'KA2CE' and 'KAACE'.
Whitepaper definition:
Agreement with KA2CE is as follows:"... the controller first creates its own receipt of the event and then promulgates the receipted event to witnesses in order to gather their promulgated receipts.
In this algorithm, an agreement consists of a specific version of an event with verifiable receipts(signatures) from the controller and a set of witnesses.
A state of agreement about a version of an event with respect to set of witnesses means that each witness in that set has witnessed the same version of that event and each witness’ receipt in that set has been promulgated to every other witness in that set."
Source [KERI Whitepaper Section 11.4.2 Agreement]Additional Definition
A newly invented algorithm that is a simplification of PBFT class algorithms, separation of control of distributed consensus using distinct promulgation (witness) and confirmation (watcher) networks (new invention) but many non-BFT consensus algorithms do something similar and one BFT algorithm Stellar does something similar but not the same.
What if PBFT and Stellar had a baby that was missing liveness and total ordering but had safety and was completely decentralized, portable, and permission less? It would be named KERI.
(SamMSmith)
keri command line interface
WebOfTrust
keri command line interface
Definition
Command line tool used to create identifiers, manage keys, query for KELs and participate in delegated identifiers or multi-signature group identifiers. It also includes operations for running witnesses, watchers and cloud agents to establish a cloud presence for any identifier.
Most commands require a “name” parameter which references a named Habitat (think wallet) for performing the operation.
More information
keri event stream
WebOfTrust
keri event stream
Definition
A stream of verifiable KERI data, consisting of the key event log and other data such as a transaction event log. This data is a CESR event stream (TODO: link to IANA application/cesr media type) and may be serialized in a file using CESR encoding. We refer to these CESR stream resources as KERI event streams to simplify the vocabulary.
Source
did:websToIP specification
keri improvement doc
WebOfTrust
keri improvement doc
Definition
These docs are modular so teams of contributors can independently work and create PRs of individual KIDs; KIDs answer the question "how we do it". We add commentary to the indivudual KIDs that elaborate on the why. It has been split from the how to not bother implementors with the why.
keri ox
WebOfTrust
keri request authentication method
WebOfTrust
keri request authentication method
Definition
All requests from a web client must use KRAM (KERI Request Authentication Method) for replay attack protection. The method is essentially based on each request body needing to include a date time string field in ISO-8601 format that must be within an acceptable time window relative to the server's date time. See the KRAM Github repo
Source SKWA GitHub repo, more info in HackMD.io write-up
Related
keri suite
WebOfTrust
keri suite
Definition
The KERI suite is the set of inter-related developments (KERI, ACDC, OOBI, CESR, IPEX, etc) under the Web-of -Trust user on Github
keri suite search engine
WebOfTrust
keri suite search engine
Definition
KERISSE is the Docusaurus self-education site of Web-of-Trust GitHub repo with Typesense search facilities. Because of its focus on well-versed developers in the field of SSI and the support of their journey to understand the structure of the code and how things work in the KERI suite it's more a search engine that drills down on documentation.
Related kerific
kerific is a front-end tool that show all available glossary-definition in KERISSE for matching words in any web text; combined in the Dictionary SSI. This is based on a large JSON file
keria
WebOfTrust
keria
Definition
KERI Agent in the cloud. The KERIA service will expose 3 separate HTTP endpoints on 3 separate network interfaces.
- Boot Interface - Exposes one endpoint for Agent Worker initialization.
- Admin Interface - The REST API for command and control operations from the Signify Client.
- KERI Protocol Interface - CESR over HTTP endpoint for KERI protocol interactions with the rest of the world.
More at Source Github repo
keride
WebOfTrust
keride
Definition
is a Rust programming language library for Key Event Receipt Infrastructure. Among its features is CESR, signing, prefixing, pathing, and parsing.
More on Github repo
keridemlia
WebOfTrust
keridemlia
Definition
It is a contraction of KERI and Kademlia. It's the distributed database of Witness IP-addresses based on a Distributed Hash Table. It also does the CNAME - stuff that Domain Name Services (DNS) offers for KERI: the mapping between an identifier and it's controller AID stored in the KEL to its current wittness AID and the wittness AID to the IP address.
(@henkvancann)
kerific
WebOfTrust
kerific
Definition
kerific is a front plugin or extension that currently only works for Chrome and Brave. It matches words in any text on the web that is parseable for kerific and offers buttons to various glossaries and definitions in the SSI field.
Relation with KERISSE
All glossaries that KERISSE is allowed to scrape are combined in the Dictionary SSI. This is based on a large JSON file, which kerific uses to match words in any text and serve the combined glossaries.
Download kerific
It is in the Chrome Webstore
keripy
WebOfTrust
kever
WebOfTrust
kever
Definition
Kever is a key event verifier.
key
Nist
A parameter used in conjunction with a cryptographic algorithm that determines the specific operation of that algorithm.ToIP
See: cryptographic key.
WebOfTrust
key
Definition
In our digital scope it's a mechanism for granting or restricting access to something. MAY be used to issue and prove, MAY be used to transfer and control over identity and cryptocurrency. More
key compromise
WebOfTrust
key compromise
Definition
Basically there are three infrastructures that are included in “key management” systems that must be protected:
- Key pair creation and storage
- Event signing
- Event signature verificationSo when we say “key compromise” we really mean compromise of one of those three things.
More information
More in the security sections of Universal Identifier Theory
key establishment
ToIP
A process that results in the sharing of a key between two or more entities, either by transporting a key from one entity to another (key transport) or generating a key from information shared by the entities (key agreement).
Source: NIST-CSRC.
key event
ToIP
An event in the history of the usage of a cryptographic key pair. There are multiple types of key events. The inception event is when the key pair is first generated. A rotation event is when the key pair is changed to a new key pair. In some key management systems (such as KERI), key events are tracked in a key event log.
ToIP (DID:Webs)
A serialized data structure of an entry in the key event log(KEL) for an AID, as defined by the KERI specification. There are three types of key events, namely inception event, rotation event, and interaction event. See WebOfTrust glossary for more detail.WebOfTrust
key event
Definition
Concretely, the serialized data structure of an entry in the key event log for an AID. Abstractly, the data structure itself. Key events come in different types and are used primarily to establish or change the authoritative set of keypairs and/or anchor other data to the authoritative set of keypairs at the point in the key event log actualized by a particular entry.
Source Sam SmithLoose definition in KERI
Events happening to controlling keys of an identifier recorded in a Key Event Log (KEL).
Data structure angle
A key event is data structure that consist of a header (Key Event header), a configuration section (Key Event Data spans Header and configuration) and signatures (Key event Message spans Data and signatures)
(@henkvancann)
key event log
ToIP
An ordered sequence of records of key events.
Note: Key event logs are a fundamental data structure in KERI.
WebOfTrust
key event log
Definition
A verifiable data structure that is a backward and forward chained, signed, append-only log of key events for an AID. The first entry in a KEL MUST be the one and only Inception Event of that AID.
Source Sam SmithPut differently
KELs are hash-chained Key Events. These are blockchains in a narrow definition, but not in the sense of ordering (not ordered) or global consensus mechanisms (which is not needed). (SamMSmith)
A KEL is KERI's VDS: the proof of key state of its identifier.
key event log (KEL)
ToIP (DID:Webs)
A verifiable append-only log of key events for an AID that is both backward and forward-chained, as defined by the KERI specification. See WebOfTrust glossary for more detail.
key event message
WebOfTrust
key event message
Definition
Message whose body is a key event and whose attachments may include signatures on its body.
Source Sam Smith
key event receipt
ToIP (DID:Webs)
A message whose body references a key event of an AID and includes one or more signatures on that key event, as defined by the KERI specification. See WebOfTrust glossary for more detail.WebOfTrust
key event receipt
Definition
Message whose body references a key event and whose attachments MUST include one or more signatures on that key event.
Source Sam Smith
key event receipt infrastructure
WebOfTrust
key event receipt infrastructure
Definition
Also
KERI. It's a new approach to decentralized identifiers and decentralized key management that promises significant benefits forSSI(self-sovereign identity) andToIP(Trust over IP) infrastructure.
(@drummondreed)KERI is an identifier system that fixes the internet. It's a fully decentralized permission-less key management architecture. It solves the
secure attribution problemto its identifiers and allows portability.
(@henkvancann)Trust spanning layer for the internet
While attribution has always been a non-exact science, we could come as close to attribution as “beyond a reasonable doubt”, those days are over with KERI.
KERI provides a trust spanning layer for the internet, because the protocol solves the secure attribution problem in a general, portable, fully decentralized way. There are more types of trust IN KERI but they all depend on the most important attributive trust.From KERI we've learned that secure attribution is the essential problem for anyidentifier systemto solve.
key event receipt infrastructure (KERI)
ToIP (DID:Webs)
A protocol that provides an identity system-based secure overlay for the internet and uses AIDs as the primary roots of trust, as defined by the KERI specification. See WebOfTrust glossary for more detail.
key event receipt log
WebOfTrust
key event receipt log
Definition
Signed Key Events, keeping track of establishment events. To begin with the inception event and any number of rotation events. We call that the establishment subsequence.The Key Event Receipt Logs are built from receipts of events signed by the witnesses of those events (these are called commitments); these are also append-only but not hash-chained.(@henkvancann)

key event receipt log (KERL)
ToIP (DID:Webs)
A verifiable append-only log that includes all the consistent key event receipt messages, as defined by the KERI specification. See WebOfTrust glossary for more detail.
key management
WebOfTrust
key management
Definition
management of cryptographic keys in a crypto-system. This includes dealing with the generation, exchange, storage, use, crypto-shredding (destruction) and replacement of keys (also rotation). It includes cryptographic protocol design, key servers, user procedures, and other relevant protocols.
Successful key management is critical to the security of a crypto-system. It is the more challenging side of cryptography in a sense that it involves aspects of social engineering such as system policy, user training, organizational and departmental interactions, and coordination between all of these elements, in contrast to pure mathematical practices that can be automated.
More on wikipedia
key management system
ToIP
A system for the management of cryptographic keys and their metadata (e.g., generation, distribution, storage, backup, archive, recovery, use, revocation, and destruction). An automated key management system may be used to oversee, automate, and secure the key management process. A key management is often protected by implementing it within the trusted execution environment (TEE) of a device. An example is the Secure Enclave on Apple iOS devices.
Also known as: KMS.
Source: NIST-CRSC.
key pair
WebOfTrust
key pair
Definition
is a private key and its corresponding public key resulting from a one-way crypto-graphical function; a key pair is used with an asymmetric-key (public-key) algorithm in a so called Public Key Infrastructure (PKI).
key state
ToIP (DID:Webs)
The set of currently authoritative key pairs (current keys) for an AID and any other information necessary to secure or establish control authority over the AID. See WebOfTrust glossary for more detail.WebOfTrust
key state
Definition
Includes the set of currently authoritative keypairs for an AID and any other information necessary to secure or establish control authority over an AID.
Source Sam Smith
key stretching
WebOfTrust
key stretching
Definition
In cryptography, key stretching techniques are used to make a possibly weak key, typically a password or passphrase, more secure against a brute-force attack by increasing the resources (time and possibly space) it takes to test each possible key.
Humans are predictable
Passwords or passphrases created by humans are often short or predictable enough to allow password cracking, and key stretching is intended to make such attacks more difficult by complicating a basic step of trying a single password candidate. Key stretching also improves security in some real-world applications where the key length has been constrained, by mimicking a longer key length from the perspective of a brute-force attacker.
More on source Wikipedia
key transparency
WebOfTrust
key transparency
Definition
provides a lookup service for generic records and a public, tamper-proof audit log of all record changes. While being publicly auditable, individual records are only revealed in response to queries for specific IDs.
Use cases
- Key Transparency can be used as a public key discovery service to authenticate users and provides a mechanism to keep the service accountable.
- Key Transparency empowers account owners to reliably see what public keys have been associated with their account, and it can be used by senders to see how long an account has been active and stable before trusting it. Source
Merkle tree
Key Transparency does this by using piece of blockchain technology called a Merkle Tree.
More on Stackexchange how key transparency works.
(@henkvancann)
keys-at-the-edge
ToIP
A key management architecture in which keys are stored on a user’s local edge devices, such as a smartphone, tablet, or laptop, and then used in conjunction with a secure protocol to unlock a key management system (KMS) and/or a digital vault in the cloud. This approach can enable the storage and sharing of large data structures that are not feasible on edge devices. This architecture can also be used in conjunction with confidential computing to enable cloud-based digital agents to safely carry out “user not present” operations.
Also known as: KATE.
keystore
WebOfTrust
keystore
Definition
A keystore in KERI is the encrypted data store that hold the private keys for a collection of AIDs.
Source: Philip Feairheller.KERI related
KERI explicitly distinguishes keystore and wallet; the latter being a superset of the former. Keep is KERI's and ACDC's user interface with Keripy agent API as a back end.
Beware
A Java Keystore is a non-related concept!
kli
WebOfTrust
knowledge
ksn
WebOfTrust
ksn
Definition
ksn = state, key state notice
large language model
WebOfTrust
large language model
Definition
A large language model (LLM) is a language model consisting of a neural network with many parameters (typically billions of weights or more), trained on large quantities of unlabeled text using self-supervised learning or semi-supervised learning.
More on Source Wikipedia
lead bytes
WebOfTrust
lead bytes
Definition
In order to avoid confusion with the use of the term pad character, when pre-padding with bytes that are not replaced later, we use the term lead bytes. So lead-bytes are added "pre-conversion".
CESR related
The term pad may be confusing not merely because both ways use a type of padding but it is also true that the number of pad characters when padding post-conversion equals the number of lead bytes when padding pre-conversion.
ledger backer
legal entity
ToIP
An entity that is not a natural person but is recognized as having legal rights and responsibilities. Examples include corporations, partnerships, sole proprietorships, non-profit organizations, associations, and governments. (In some cases even natural systems such as rivers are treated as legal entities.)
See also: Legal Entity Identifier, legal person, organization.
WebOfTrust
legal entity
Definition
Unique parties that are legally or financially responsible for the performance of financial transactions or have the legal right in their jurisdiction to enter independently into legal contracts.
More detailed and inclusive
As defined in ISO 17442:2020, includes, but is not limited to, the unique parties above, regardless of whether they are incorporated or constituted in some other way (e.g., trust, partnership, contractual). It includes governmental organizations and supranationals and individuals when acting in a business capacity but excludes natural persons. It also includes international branches.
Paraphrased by @henkvancann from source Draft vLEI Ecosystem Governance Framework Glossary.
legal entity engagement context role vlei credential governance framework
WebOfTrust
legal entity engagement context role vlei credential governance framework
Definition
A document that details the requirements for vLEI Role Credentials issued to representatives of a Legal Entity in other than official roles but in functional or other context of engagement.
Source: Draft vLEI Ecosystem Governance Framework Glossary.Related
legal entity official organizational role vlei credential governance framework
WebOfTrust
legal entity official organizational role vlei credential governance framework
Definition
A document that details the requirements for vLEI Role Credentials issued to official representatives of a Legal Entity.
Source: Draft vLEI Ecosystem Governance Framework Glossary.Related
legal entity vlei credential governance framework
WebOfTrust
legal entity vlei credential governance framework
Definition
A document that details the requirements for vLEI Credential issued by a Qualified vLEI Issuer to a Legal Entity.
legal identity
ToIP
A set of identity data considered authoritative to identify a party for purposes of legal accountability under one or more jurisdictions.
See also: foundational identity, functional identity.
legal person
ToIP
In law, a legal person is any person or 'thing' that can do the things a human person is usually able to do in law – such as enter into contracts, sue and be sued, own property, and so on.[3][4][5] The reason for the term "legal person" is that some legal persons are not people: companies and corporations are "persons" legally speaking (they can legally do most of the things an ordinary person can do), but they are not people in a literal sense (human beings).
Source: Wikipedia.
Contrast with: natural person.
See also: legal entity, organization.
legal system
ToIP
A system in which policies and rules are defined, and mechanisms for their enforcement and conflict resolution are (implicitly or explicitly) specified. Legal systems are not just defined by governments; they can also be defined by a governance framework.
Source: eSSIF-Lab
legitimized human meaningful identifier
WebOfTrust
legitimized human meaningful identifier
Definition
An AID and its associated self-certifying trust basis gives rise to a trust domain for associated cryptographically verifiable non-repudiable statements. Every other type of identifier including human meaningful identifiers may then be secured in this resultant trust domain via an end-verifiable authorization. This authorization legitimizes that human meaningful identifier as an LID through its association with an AID. The result is a secured trust domain specific identifier couplet of aid|lid.
Problematic human meaningfulness
Human meaningfulness has two limiting characteristics: scarcity and security. Scarcity exhibits itself in various undesirable ways such as name squatting, or race conditions to register or otherwise assert control. More importantly, there is no inherent security property of a human meaningful identifier. This makes them insecure by default. Happily an AID comes to rescue.
Couplet for scarcity and security
The trust domain of an AID provides a context in which to interpret the appearance of any LID. The AID is implied by the context. This means that the AID may not need to be prepended or appear with the LID. This allows the human meaningfulness of the LID to exhibit itself without being encumbered by the AID.
This model of an aid|lid couplet unifies all desirable identifier properties into one identifier system model. The AID part provides the security infrastructure while the LID part provides the application specific human meaningfulness. The connection between the two is provided by a legitimizing authorization represented by the |.
level of assurance
ToIP
See: assurance level.
level of risk
digital.govt.nz
magnitude of a risk or combination of risks, expressed in terms of the combination of consequences and their likelihood[Source: ISO 31073:2022]
levels of assurance
WebOfTrust
levels of assurance
Definition
Identity and other trust decisions are often not binary. They are judgement calls. Any time that judgement is not a simple “Yes/No” answer, you have the option for levels of assurance. Also 'LoA'.
Relationship with KERI
KERI has the same LOAs for entropy and trust in human behavior preserving the security of key pairs and preserving their own privacy. It has high LOAs for the cryptographic bindings of controllers and identifiers. Also the validation of witnesses and watchtowers has high a LOA.
likelihood
digital.govt.nz
chance of something happening[Source: ISO 31073:2022]Additional notes:Note 1: In risk management terminology, the word likelihood is used to refer to the chance of something happening, whether defined, measured or determined objectively or subjectively, qualitatively or quantitatively, and described using general terms or mathematically (such as a probability or a frequency over a given time period).Note 2: The English term likelihood does not have a direct equivalent in some languages instead, the equivalent of the term probability is often used. However, in English, probability is often narrowly interpreted as a mathematical term. Therefore, in risk management terminology, likelihood is used with the intent that it should have the same broad interpretation as the term probability has in many languages other than English.
listed identifier
WebOfTrust
listed identifier
Definition
Is a list in an ACDC of authorised did:webs identifier + method; the list appears in the metadata of the did:webs DID-doc.
Source: paraphrased Samuel Smith, Zoom meeting KERI dev Thursday Nov 9 2023
liveness
WebOfTrust
liveness
Definition
Liveness refers to a set of properties of concurrent systems, that require a system to make progress despite the fact that its concurrently executing components ("processes") may have to "take turns" in critical sections, parts of the program that cannot be simultaneously run by multiple processes.
Meaning
A liveness property in concurrent systems states that "something good will eventually occur".
Liveness guarantees are important properties in operating systems and distributed systems.
Unlike liveness properties, safety properties can be violated by a finite execution of a distributed system. All properties can be expressed as the intersection of safety and liveness properties.
| TBW | prio 2 how is liveness important in distributed systems? how does KERI guarantee liveness}More information
On wikipedia
liveness detection
ToIP
Any technique used to detect a presentation attack by determining whether the source of a biometric sample is a live human being or a fake representation. This is typically accomplished using algorithms that analyze biometric sensor data to detect whether the source is live or reproduced.
Also known as: proof of presence.
loci of control
WebOfTrust
loci of control
Definition
Locus of control is the degree to which people believe that they, as opposed to external forces (beyond their influence), have control over the outcome of events in their lives. Also 'LoC'.
More on wikipediaIn SSI domain
In SSI loci-of-control was decribed by Tim Bouma in 2019:

KERI development
In KERI this is further developed:
- Key Event Promulgation Service = from the
controller's point. - key event confirmation service = from the
validator's point.
The separation of promulgation and confirmation into two separate loci-of-control, one the controller’s, and the other the validator’s simplifies the interaction space between these two parties.
The design principle of separating the loci-of-control between controllers and validators removes one of the major drawbacks of total ordered distributed consensus algorithms, that is, shared governance over the pool of nodes that provide the consensus algorithm.
The primary purpose of the KA2CE algorithm is to protect the controller’s ability to promulgate the authoritative copy of its key event history despite external attack. This includes maintaining a sufficient degree of availability such that any validator may obtain an authoritative copy on demand.- Key Event Promulgation Service = from the
locked state
WebOfTrust
locked state
Definition
The default status a KERI data store is in once it has been created using a passcode; it is by default encrypted.
locus of control
ToIP
The set of computing systems under a party’s direct control, where messages and data do not cross trust boundaries.
machine-readable
ToIP
Information written in a computer language or expression language so that it can be read and processed by a computing device.
Contrast with: human-readable.
man-made thing
ToIP
A thing generated by human activity of some kind. Man-made things include both active things, such as cars or drones, and passive things, such as chairs or trousers.
Source: Sovrin Foundation Glossary V3
Contrast with: natural thing.
Note: Active things are the equivalent of non-human actors in the eSSIF-Lab mental model Parties, Actors, Actions. Also see Appendix B and Appendix C of the Sovrin Glossary.
management TEL
WebOfTrust
management transaction event log
WebOfTrust
management transaction event log
Definition
A 'management TEL' will signal the creation of the Virtual Credential Registry (VCR) and track the list of Registrars that will act as Backers for the individual _ transaction event logs (TELs)_ for each virtual credential (VC).
mandatory
ToIP
A requirement that must be implemented in order for an implementer to be in compliance. In ToIP governance frameworks, a mandatory requirement is expressed using a MUST or REQUIRED keyword as defined in IETF RFC 2119.
See also: recommended, optional.
For more information, see: https://www.rfc-editor.org/rfc/rfc2119.
mechanism
digital.govt.nz
a process or technique, esp. of execution[Source: Dictionary]
media type
WebOfTrust
media type
Definition
A Media type (formerly known as MIME type) is a standard way to indicate the nature and format of a file, like 'image/jpeg' for JPEG images, used on the internet.
It is a two-part identifier for file formats and format contents transmitted on the internet. Their purpose is somewhat similar to file extensions in that they identify the intended data format.
The Internet Assigned Numbers Authority (IANA) is the official authority for the standardization and publication of these classifications.
More on source Wikipedia
message
ToIP
A discrete unit of communication intended by the source for consumption by some recipient or group of recipients.
Source: Wikipedia.
See also: ToIP message, verifiable message.
WebOfTrust
message
Definition
serialized data structure event, an actionable message
KERI details
Consists of a serialized data structure that comprises its body and a set of serialized data structures that are its attachments. Attachments may include but are not limited to signatures on the body.
Source Sam Smith
messagepack
WebOfTrust
messagepack
Definition
MessagePack is a computer data interchange format. It is a binary form for representing simple data structures like arrays and associative arrays. MessagePack aims to be as compact and simple as possible. The official implementation is available in a variety of languages
More on Wikipedia
metadata
ToIP
Information describing the characteristics of data including, for example, structural metadata describing data structures (e.g., data format, syntax, and semantics) and descriptive metadata describing data contents (e.g., information security labels).
Source: NIST-CSRC.
See also: communication metadata.
Supporting definitions:
Wikipedia: Metadata (or metainformation) is "data that provides information about other data", but not the content of the data itself, such as the text of a message or the image itself.
method-specific identifier
ToIP (DID:Webs)
The method-specific-id part of DID Syntax, as defined in DID Core. See section Method-Specific Identifier.
mobile deep link
ToIP
In the context of mobile apps, deep linking consists of using a uniform resource identifier (URI) that links to a specific location within a mobile app rather than simply launching the app. Deferred deep linking allows users to deep link to content even if the app is not already installed. Depending on the mobile device platform, the URI required to trigger the app may be different.
Source: Wikipedia.
moobi
WebOfTrust
moobi
Definition
Multi OOBI would allow to share a bunch of different end-points (oobis) all at once. A way for a single store to share multiple endpoints for that store.
Limitation
Those oobis would still need a way to authorize the endpoint provider, the endpoint role, for each of the different things. A multi-sig becomes a messy collaboration effort, especially when you take into account signing at the edge. You would need an authorization record for each end-point. And then pass this to all the members and ask them to collaborate.
Also see
Source: Philip Feairheller KERI-dev meeting July 27 2023
most compact
WebOfTrust
most compact
Definition
An ACDC that, for a given level of disclosure, is as compact as it can be which means
- it has the SAIDs for each section that are not disclosed
- it has expanded sections that are disclosed
Multiple forms of a single ACDC can be called the "most compact" version given that each level of graduated disclosure will have a "most compacted" version. If all the blocks are expanded of a most compact version then it becomes fully expanded. If all the blocks are replaced with SAIDs then it becomes fully compacted.
This form is a part of the graduated disclosure objective.
See also
Fully (expanded) version of an ACDC
Fully compact(ed) version of an ACDC
multi factor authentication
WebOfTrust
multi factor authentication
Definition
Authentication by combining multiple security factors. Well-known factors are what you know, what you have and what you are.
Wikipedia citation
Multi-factor authentication (MFA; two-factor authentication, or 2FA, along with similar terms) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism.
Source Wikipedia
multi valent
WebOfTrust
multi valent
Definition
A delegator may have multiple delegates thereby enabling elastic horizontal scalability. Multiple delegates from a single delegator. Furthermore, each delegate may act as a delegator for its own delegates to form a nested delegation tree.
This allows mapping key management infrastructures to any hierarchically structured organization's computing infrastructure. With this construction, both security and performance trade-offs may be made as appropriate. Such an extended delegation setup we call a multivalent key management infrastructure.
Source Universal Identifier Theory by Samuel Smith
Also see
multi-party computation
ToIP
Secure multi-party computation (also known as secure computation, multi-party computation (MPC) or privacy-preserving computation) is a subfield of cryptography with the goal of creating methods for parties to jointly compute a function over their inputs while keeping those inputs private. Unlike traditional cryptographic tasks, where cryptography assures security and integrity of communication or storage and the adversary is outside the system of participants (an eavesdropper on the sender and receiver), the cryptography in this model protects participants' privacy from each other.
Source: Wikipedia.
Also known as: MPC, secure multi-party computation.
multi-party control
ToIP
A variant of multi-party computation where multiple parties must act in concert to meet a control requirement without revealing each other’s data. All parties are privy to the output of the control, but no party learns anything about the others.
multi-signature
ToIP
A cryptographic signature scheme where the process of signing information (e.g., a transaction) is distributed among multiple private keys.
Source: NIST-CSRC.
ToIP (DID:Webs)
A mechanism that enables multiple parties to sign a message, as defined by the KERI specification. See Controller Application in the KERI spec for more detail.
multicast
ToIP
In computer networking, multicast is group communication where data transmission is addressed (using a multicast address) to a group of destination computers simultaneously. Multicast can be one-to-many or many-to-many distribution. Multicast should not be confused with physical layer point-to-multipoint communication.
Source: Wikipedia.
multicast address
ToIP
A multicast address is a logical identifier for a group of hosts in a computer network that are available to process datagrams or frames intended to be multicast for a designated network service.
Source: Wikipedia.
See also: broadcast address, unicast address.
multicodec
WebOfTrust
multicodec
Definition
Is a self-describing multi-format, it wraps other formats with a tiny bit of self-description. A multi-codec identifier is both a variant (variable length integer) and the code identifying data.
See more at GitHub Multi-codec
Multi-codec is an agreed-upon codec table. It is designed for use in binary representations, such as keys or identifiers (i.e CID). It is then used as a prefix to identify the data that follows.
multiplexing
WebOfTrust
multiplexing
Definition
In telecommunications and computer networking, multiplexing (sometimes contracted to muxing) is a method by which multiple analog or digital signals are combined into one signal over a shared medium. The aim is to share a scarce resource - a physical transmission medium.
More on source Wikipedia-pageCESR related
Because of count codes and the composability - and concatenation property in CESR, pipelining is possible, which then uses multiplexing (combining self-framing primitives) and de-multiplexing (unravelling self-framing primitives). The addition of group framing codes as independently composable primitives enables hierarchical compositions.
multisig
WebOfTrust
multisig
Definition
also multi-signature or multisignature; is a digital signature scheme which allows a group of users to sign a single piece of digital data.
Paraphrased by @henkvancann from Wikipedia sourceKERI multi-signatures
The KERI team has conceptually chosen for minimal sufficient means and so-called dumb crypto: "'Dumb technology' is freely available, understandable to everyone and easy to implement. In our case: just hashes and digital signatures."
KERI has thresholded set of non-repudiable signatures.
KERI's CESR, and therefore KERI and ACDC is extensible with the latest more sophisticated multi-signature schemes like Schnorr signatures.
naive conversion
WebOfTrust
naive conversion
Definition
Non-CESR Base64 conversion. How people are used to using the Base64 encode and decode. Without pre-padding etc all the stuff CESR does to ensure aligns on 24 bit boundaries so CESR never uses the '=' pad character. But naive Base64 will pad if the length is not 24 bit aligned.
Source: Samuel Smith in issue 34Naive conversion is a text to binary conversion or vice versa that doesn't anticipate on either composability and / or on the concatenation capability of the result of such an operation.
CESR related
In the IETF draft CESR there's much attention for naive Base64 conversions, because it helps explaining the necessity of stable code characters and padding in CESR to achieve:
- self-framing
- round-robin composability
- concatenation options
- pipelined streaming
namespace
WebOfTrust
namespace
Definition
In an identity system, an identifier can be generalized to a namespace to provide a systematic way of organizing identifiers for related resources and their attributes. A namespace is a grouping of symbols or identifiers for a set of related objects.
A namespace employs some scheme for assigning identifiers to the elements of the namespace. A simple name-spacing scheme uses a prefix or prefixes in a hierarchical fashion to compose identifiers. The following is an example of a namespace scheme for addresses within the USA that uses a hierarchy of prefixes:
state.county.city.zip.street.number.An example element in this namespace may be identified with the following:
utah.wasatch.heber.84032.main.150S.
natural person
ToIP
A person (in legal meaning, i.e., one who has its own legal personality) that is an individual human being, distinguished from the broader category of a legal person, which may be a private (i.e., business entity or non-governmental organization) or public (i.e., government) organization.
Source: Wikipedia.
See also: legal entity, party.
Contrast with: legal person
natural thing
ToIP
A thing that exists in the natural world independently of humans. Although natural things may form part of a man-made thing, natural things are mutually exclusive with man-made things.
Source: Sovrin Foundation Glossary V3.
Contrast with: man-made thing.
For more information see: Appendix B and Appendix C of the Sovrin Glossary
Note: Natural things (those recognized to have legal rights) can be parties but never actors in the eSSIF-Lab mental model Parties, Actors, Actions.
ndigs
WebOfTrust
ndigs
Definition
Digests of public keys, not keys themselves. The reason to use ndigs is to prove control over public keys or to hide keys. It's used in Keripy and consists of a list of qualified base64 digests of public rotation key derivations.
nested cooperative delegated identifiers
WebOfTrust
nested cooperative delegated identifiers
Definition
In KERI delegations are cooperative, this means that both the delegator and delegate must contribute to a delegation. The delegator creates a cryptographic commitment in either a rotation or interaction event via a seal in a delegated establishment event. The delegate creates a cryptographic commitment in its establishment event via a seal to the delegating event. Each commitment is signed respectively by the committer. This cooperative delegation together with special superseding recovery rules for events enables cooperative recovery.
Recursive application
This superseding rule may be recursively applied to multiple levels of delegation, thereby enabling recovery of any set of keys signing or pre-rotated in any lower levels by a superseding rotation delegation at the next higher level. This cascades the security of the key management infrastructure of higher levels to lower levels. This is a distinctive security feature of the cooperative delegation of identifiers in KERI.
More information
More in chapter Nested Delegation Recovery of the whitepaper
network address
ToIP
A network address is an identifier for a node or host on a telecommunications network. Network addresses are designed to be unique identifiers across the network, although some networks allow for local, private addresses, or locally administered addresses that may not be unique. Special network addresses are allocated as broadcast or multicast addresses. A network address designed to address a single device is called a unicast address.
Source: Wikipedia.
node
ToIP
In telecommunications networks, a node (Latin: nodus, ‘knot’) is either a redistribution point or a communication endpoint. The definition of a node depends on the network and protocol layer referred to. A physical network node is an electronic device that is attached to a network, and is capable of creating, receiving, or transmitting information over a communication channel.
Source: Wikipedia.
non establishment event
WebOfTrust
non establishment event
Definition
A key event tieing or anchoring a data payload to the key event log of an identifier. This data payload includes a set of one or more seals each of which anchor data to the key event.
The data payload event may be used to make verifiable, authoritative statements on behalf of the identifier controller.
These might include authorizations of encryption keys, communication routes, service endpoints, and so forth.Transactions or workflows composed of non-establishment events are secured by virtue of being included in the verifiable key eventsequence with the verifiable authoritative establishment events.
A non-establishment event is a key event that does not change the current key-state for an AID.
Source KERI Whitepaper Section 7.22 page 46
Source Sam SmithMade easier
A non-establishment event is a key event that does not change the current key-state for an identifier. The event (only) ties or anchors digital data to the key event log of the identifier.
(@henkvancann)
non fungible token
WebOfTrust
non fungible token
Definition
A non-fungible token (NFT) is a financial security consisting of digital data stored in a blockchain, a form of distributed ledger.
Ownership
The ownership of an NFT is recorded in a blockchain, and can be transferred by the owner, allowing NFTs to be sold and traded. NFTs can be created by anybody, and require few or no coding skills to create. NFTs typically contain references to digital files such as photos, videos, and audio.
Fungible
Because NFTs are uniquely identifiable assets, they differ from cryptocurrencies, which are fungible.
KERI / ACDC related
There's nothing "non fungible" to a Non-fungible Token in our perspective. It's just another unique identifier controlled by a public private key pair. The fact that an NFT uniquely identifies a digital entity isn't very impressing, because of their
- security fault : the security is dependent of the host ledger the NFT is anchored to.
- transferability fault : you need a transaction to transfer ownership on the host blockchain, controlling keys can't be rotated
- monitization fault : there's no good reason whatsoever to mingle the value aspect and the uniqueness property of a digital asset, and unfortunately that's what NFTs are doing.
Because uniqueness tokenization "done right" is to be praised, it's recommended to look into KERI identifiers and ACDC veracity claims to support the value of the identifiers, whose monetary value can be recorded elsewhere and separate from the identifier system. Key (pre-)rotation can transfer ownership of a unique digital asset without the need of a transaction on a blockchain.
Asset backing
Sometimes an NFT doesn't only uniquely represent a digital asset. It can be the digital twin of - and is also (hopefully) backed by - a real-life asset. Even in this perspective KERI and ACDC are more emcompassing too, because in the KERI/ACDC case we are dealing with globally portable unique digital twins, not anchored to (read
locked in) a blockchain.
non interactive authentication design
WebOfTrust
non interactive authentication design
Definition
A group of approaches having non-interactive mechanisms that pose unique problems because they do not allow a challenge response reply handshake. A request is submitted that is self-authenticating without additional interaction. The main benefits of non-interactive authentication are scalability and path independent end-to-end verifiability. These benefits become more important in decentralized applications that employ zero-trust architectures.
More in source Keri Request Authentication Mechanism (KRAM) by Samuel SmithRelated
non normative
WebOfTrust
non repudiable
WebOfTrust
non repudiable
Definition
Non-repudiation refers to a situation where a statement's author cannot successfully dispute its authorship or the validity of an associated contract, signature or commitment.
The term is often seen in a legal setting when the authenticity of a signature is being challenged. In such an instance, the authenticity is being "repudiated".KERI related
Any non-repudiable signature made with the private key may be verified by extracting the public key from either the identifier itself or incepting information uniquely associated with the cryptographic derivation process for the identifier. In a basic SCID, the mapping between an identifier and its controlling public key is self-contained in the identifier itself.
Source Sam SmithThe inner-working of KERI's non-repudiation
The function of KERI's identifier-system security overlay is to establish the authenticity (or authorship) of the message payload in an IP Packet by verifiably attributing it to a cryptonymous self-certifying identifier (AID) via an attached set of one or more asymmetric keypair-based non-repudiable digital signatures. The current valid set of associated asymmetric keypair(s) is proven via a verifiable data structure called a key event log (KEL).
An authenticatable (verifiable) internet message (packet) or data item includes the identifier and data in its payload. Attached to the payload is a digital signature(s) made with the private key(s) from the controlling keypair(s). Given the identifier in a message, any verifier of a message (data item) can use the identifier system mapping to look up the public key(s) belonging to the controlling keypair(s). The verifier can then verify the attached signature(s) using that public key(s). Because the payload includes the identifier, the signature makes a non-repudiable cryptographic commitment to both the source identifier and the data in the payload.
Source Sam Smith
non transferable
WebOfTrust
non transferable
Definition
No capacity to transfer (the control over) a certain digital asset in an unobstructed or loss-less manner. As opposed to transferable.
For example not legally transferable to the ownership of another entity.
KERI related
A specific type of identifier we distinguish is a non-transferable identifier; it is has specific positive features like short-lived, peer to peer, one-time use, discardable, etc. that are very practical in certain use cases.
non transferable identifier
WebOfTrust
non transferable identifier
Definition
Controlling keys over this identifier cannot be rotated and therefore this identifier is non-transferable to other control.
An identifier of this type has specific positive features like short-lived, peer to peer, one-time use, discardable, etc. that are very practical in certain use cases. Moreover non-transferable identifiers are much easier to govern than persistent identifiers that are transferable.KERI related
The KERI design approach is to build composable primitives instead of custom functionality that is so typical of other DKMI approaches:
- transferable identifiers
- non-transferable identifiers
- delegated identifiers
non-custodial wallet
ToIP
A digital wallet that is directly in the control of the holder, usually because the holder is the device controller of the device hosting the digital wallet (smartcard, smartphone, tablet, laptop, desktop, car, etc.) A digital wallet that is in the custody of a third party is called a custodial wallet.
normative
WebOfTrust
normative
Definition
a theory is “normative” if it, in some sense, tells you what you should do - what action you should take. If it includes a usable procedure for determining the optimal action in a given scenario.
Source.
objective
official organizational role
WebOfTrust
official organizational role
Definition
Also 'OOR'. A person that represents the Legal Entity in an official organizational role and is issued an OOR vLEI Credential.
Source Draft vLEI Ecosystem Governance Framework Glossary.
one way function
WebOfTrust
one way function
Definition
In computer science, a one-way function is a function that is easy to compute on every input, but hard to invert given the image of a random input. Here, "easy" and "hard" are to be understood in the sense of computational complexity theory, specifically the theory of polynomial time problems.
More on Wikipedia
one-time password OTP
digital.govt.nz
a password that is valid for only 1 login session or transaction[Source: Wikipedia]Additional notes:Note 1: Also known as one-time pin or dynamic password.Note 2: Generation can be time-based OTP (TOTP) or event-based OTP also known as hash-based message authentication codes (HMAC) (HOTP).
opcode
WebOfTrust
opcode
Definition
Opcodes are meant to provide stream processing instructions that are more general and flexible than simply concatenated primitives or groups of primitives.
Why opcodes
A yet to be determined stack based virtual machine could be executed using a set of opcodes that provides primitive, primitive group, or stream processing instructions. This would enable highly customizable uses for CESR.
Opcode tables
The ‘_’ selector is reserved for the yet to be defined opcode table or tables.
operational circumstances
ToIP
In the context of privacy protection, this term denotes the context in which privacy trade-off decisions are made. It includes the regulatory environment and other non-technical factors that bear on what reasonable privacy expectations might be.
Source: PEMC IGR
optional
ToIP
A requirement that is not mandatory or recommended to implement in order for an implementer to be in compliance, but which is left to the implementer’s choice. In ToIP governance frameworks, an optional requirement is expressed using a MAY or OPTIONAL keyword as defined in IETF RFC 2119.
See also: mandatory, recommended.
For more information, see: https://www.rfc-editor.org/rfc/rfc2119.
organization
ToIP
A party that consists of a group of parties who agree to be organized into a specific form in order to better achieve a common set of objectives. Examples include corporations, partnerships, sole proprietorships, non-profit organizations, associations, and governments.
See also: legal entity, legal person.
Supporting definitions:
eSSIF-Lab: a party that is capable of setting objectives and making sure these are realized by actors that it has onboarded and/or by (vetted) parties that are committed to contribute to these objectives.
organizational authority
ToIP
A type of authority where the party asserting its right is an organization.
orphan ~ed
digital.govt.nz
entity information that is not bound to an entity or authenticator
out of band introduction
WebOfTrust
out of band introduction
Definition
Out-of-band Introductions (OOBIs) are discovery and validation of IP resources for KERI autonomic identifiers. Discovery via URI, trust via KERI.
The simplest form of a KERI OOBI is a namespaced string, a tuple, a mapping, a structured message, or structured attachment that contains both a KERI AID and a URL. The OOBI associates the URL with the AID. In tuple form this abstractly:
(url, aid)and concretely
("http://8.8.5.6:8080/oobi", "EaU6JR2nmwyZ-i0d8JZAoTNZH3ULvYAfSVPzhzS6b5CM")Validation
Validation is done based on BADA More in KERI OOBI draft spec and KERI OOBI explained - draft.
High-end definition

From the IETF draft specification:
An Out-Of-Band Introduction (OOBI) provides a discovery mechanism that associates a given URI or URL with a given AID (autonomic identifier or self-addressing identifier (SAID)). The URI provided by an OOBI acts as a service endpoint for the discovery of verifiable information about the AID or SAID. As such an OOBI itself is not trusted but must be verified.
To clarify, any information obtained from the service endpoint provided in the OOBI must be verified by some other mechanism. An OOBI, however, enables any internet and web search infrastructure to act as an out-of-band infrastructure to discover information that is verified using an in-band mechanism or protocol.The primary in-band verification protocol is KERI.
out-of-band introduction
ToIP
A process by which two or more entities exchange VIDs in order to form a cryptographically verifiable connection (e.g., a ToIP connection), such as by scanning a QR code (in person or remotely) or clicking a deep link.
Also known as: OOBI.
out-of-band introduction (OOBI)
ToIP (DID:Webs)
A protocol for discovering verifiable information on an AID or a SAID, as defined by the KERI specification. The OOBI by itself is insecure, and the information discovered by the OOBI must be verified. See WebOfTrust glossary for more detail.
owner
WebOfTrust
owner (of an entity)
ToIP
The role that a party performs when it is exercising its legal, rightful or natural title to control a specific entity.
Source: eSSIF-Lab.
See also: controller.
ownership
WebOfTrust
pad
WebOfTrust
pad
Definition
is a character used to fill empty space, because many applications have fields that must be a particular length.
SourceKERI related
In order to avoid confusion with the use of the term pad character, when pre-padding with bytes that are not replaced later, we use the term lead bytes.
parside
WebOfTrust
parside
Definition
is a bunch of generators. Responsible for pulling out a stream of bits from a CESR stream and parse it.Sam Smith suggested for Parside to not iterate stuff, only parse chunks delimited by the count code. (Source Cesride: meeting Feb 2 2023)
Background
CESR primitives are self-framing (which is relatively new). That means that you can construct your parser modually. We can dispatch the parsing of the stream to an entity. The strip parameter tells us what part will be parsed be which code.
Design ideas Feb 2023
- Parside should be concerned with parsing group codes, cesride concerned with parsing primitives.
- Parside will contain a count code at the beginning of the stream, each cesr primitive is self framing, JSON is not; hence the Version string.
- Parside could "load" the tables it supports for dynamically loaded code tables
- Parside could look at how/if we can return an interator/generator
Source Cesride: meeting Feb 2 2023 notes
Cesride parses the CESR primitives
Parside parses the group codes
| TBW |
Related
Source Cesride: meeting Feb 2 2023
Working
Parside should start with a default version for CESR. Anytime it gets a version count code it changes the version and also elevates to the top level (the version count code must appear at the top level). The version count code determines which CESR table to load when parsing the stream. The sniffer detects if CESR binary, CESR Text, JSON, CBOR, MGPK. If any of the last three then the parser regexes to find the version string inside the JSON, CBOR, and MGPK and from the version string extracts the number of characters/bytes that is the length of the JSON, CBOR, or MGPK. The parser then resumes sniffing. When the sniff is CESR then when at the top level looks for the CESR version count code or any other count codes. The interpretation of the count codes is dependent on the version count code that is why the Parser has to start with a default version count code because the stream may not begin with a version code or may have resumed after a cold restart. When a count code is parsed then the parser may descend into parsing whats inside group for a group count code which may recursively nest down a ways.
Source Slack Cesride thread: Feb 2 2023
partial disclosure
WebOfTrust
partial disclosure
Definition
An ACDC attribute section can be a nested branch in a tree. Partial disclosure is the weaker version because you can either decide to disclose or not. Selective disclosure is more fine grained.
Related
Selective disclosure is a from partial disclosure that has a different cryptographic fundament: a sort of cryptographic aggregator (not an accumulator).
Source: distilled from ACDC Zoom meeting, date March 28, 2023
partial pre rotation
WebOfTrust
partial rotation
WebOfTrust
partial rotation
Definition
The pre-rotation mechanism supports partial pre-rotation or more exactly partial rotation of pre-rotated keypairs. It's a rotation operation on a set of pre-rotated keys that may keep some keys in reserve (i.e unexposed) while exposing others as needed.
Partial rotation serves two important purposes:
Paraphrased by @henkvancann on the bases of the IETF-KERI draft 2022 by Samual Smith.
More detailed explanation
A valid rotation operation requires the satisfaction of two different thresholds. These are the current threshold of the given rotation (establishment) event with respect to its associated current public key list and the next threshold from the given rotation event's most recent prior establishment event with respect to its associated blinded next key digest list. For short, we denote the next threshold from the most recent prior establishment event as the prior next threshold, and the list of unblinded public keys taken from the blinded key digest list from the most recent prior establishment event as the prior next key list. Explication of the elements of the prior next key list requires exposing or unblinding the underlying public keys committed to by their corresponding digests that appear in the next key digest list of the most recent prior establishment event. The unexposed (blinded) public keys MAY be held in reserve.
More in Source
party
digital.govt.nz
an entity who participates or is concerned in an action, proceeding, plan, etc.[Source: Dictionary modified to include non-persons]Nist
An individual (person), organization, device, or a combination thereof. In this Recommendation, an entity may be a functional unit that executes certain processes.ToIP
An entity that sets its objectives, maintains its knowledge, and uses that knowledge to pursue its objectives in an autonomous (sovereign) manner. Humans and organizations are the typical examples.
Source: eSSIF-Lab.
See also: first party, second party, third party, natural person
WebOfTrust
party
Definition
An entity who participates or is concerned in an action, proceeding, plan, etc.
Source: ToIP
passcode
password
ToIP
A string of characters (letters, numbers and other symbols) that are used to authenticate an identity, verify access authorization or derive cryptographic keys.
Source: NIST-CSRC.
See also: complex password.
pathing
WebOfTrust
pathing
Definition
It was designed send to sign portions of a credential. Designed for complex cases like
- a credential embedded in another credential
- multiple signers, only signing portions of a credential (partial signing)
In these cases we provide a path (using SAD path language) to what is signed.We have never used it for credentials, however we do need it forforwarding in KERI embedded messages - see video discussion.
Important
We don't sign our credentials, you shouldn't either!
Source: Philip Feairheller, July 20 2023, KERI-dev meeting
payload
WebOfTrust
payload
Definition
The term 'payload' is used to distinguish between the 'interesting' information in a chunk of data or similar, and the overhead to support it. It is borrowed from transportation, where it refers to the part of the load that 'pays': for example, a tanker truck may carry 20 tons of oil, but the fully loaded vehicle weighs much more than that - there's the vehicle itself, the driver, fuel, the tank, etc. It costs money to move all these, but the customer only cares about (and pays for) the oil, hence, 'pay-load'. Source.
KERI context
Now payload in
KERI. The payload of an item in anEvent Logis one the following cryptographic building blocks in KERI:- a content digest hash
- a root hash of a Merkle-tree
- a public keyNote tha KERI never puts raw data or privacy-sensitive data in a
KELorKERL.
peer
ToIP
In the context of digital networks, an actor on the network that has the same status, privileges, and communications options as the other actors on the network.
See also: peer-to-peer.
Supporting definitions:
eSSIF-Lab: the actor with whom/which this other actor is communicating in that communication session.
peer to peer
WebOfTrust
peer to peer
Definition
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network. They are said to form a peer-to-peer network of nodes
More on source Wikipedia
peer-to-peer
percolated information discovery
WebOfTrust
percolated information discovery
Definition
In the OOBI protocol, a discovery mechanism for the KERI and the ACDC protocols is provided by a bootstrap that enables Percolated Information Discovery (PID), which is based on Invasion Percolation Theory.
After related information for discovery and verification is bootstrapped from the OOBI, subsequent authorization is non-interactive thus making it highly scalable. This provides what we call zero-trust percolated discovery or speedy percolated discovery. Percolation means that each discoverer in turn may share what it discovers with any subsequent discoverers. Since the information so discovered is end-verifiable, the percolation mechanism and percolating intermediaries do not need to be trusted.
Percolation Theory
Percolation theory is a mathematical framework used to study the behavior of connected clusters in random systems. It was originally developed to understand the flow of fluids through porous media, but it has since found applications in various fields, including physics, mathematics, computer science, and social sciences.
Invasion Percolation Theory
Invasion percolation is a specific variant of percolation theory that models the infiltration of a fluid into a porous medium. It is used to study how a fluid, such as a gas or liquid, spreads through a random network of interconnected sites or pores.
The invasion process follows the principle of least resistance, where the fluid seeks the path of least resistance through the porous medium. As the invasion progresses, the fluid selectively infiltrates the sites with lower resistance, forming a connected cluster of invaded sites. The invaded cluster grows by adding new invaded sites through the neighboring dry sites with the lowest resistance.
permission
ToIP
Authorization to perform some action on a system.
Source: NIST-CSRC.
persistent connection
ToIP
A connection that is able to persist across multiple communication sessions. In a ToIP context, a persistent connection is established when two ToIP endpoints exchange verifiable identifiers that they can use to re-establish the connection with each other whenever it is needed.
Contrast with: ephemeral connection.
persistent data structure
WebOfTrust
persistent data structure
Definition
An append only verifiable data structure. What we sign may not change.
Related Work
The approach that ACDCs take to data structures -- making them immutable and thus distributable and concurrency-friendly -- is very similar to the one advocated and implemented by Clojure.
ACDC Related
The persistent data structure is a graph
persistent identifier
WebOfTrust
personal data
ToIP
Any information relating to an identified or identifiable natural person (called a data subject under GDPR).
Source: NIST-CSRC.
personal data store
ToIP
See: personal data vault.
Note: In the market, the term “personal data store” has also been used to generally mean a combination of the functions of a personal digital agent, personal wallet, and personal data vault.
personal data vault
ToIP
A digital vault whose controller is a natural person.
personal wallet
ToIP
A digital wallet whose holder is a natural person.
Contrast with: enterprise wallet.
personally identifiable information
ToIP
Information (any form of data) that can be used to directly or indirectly identify or re-identify an individual person either singly or in combination within a single record or in correlation with other records. This information can be one or more attributes/fields/properties in a record (e.g., date-of-birth) or one or more records (e.g., medical records).
Source: NIST-CSRC
Also known as: PII.
See also: personal data, sensitive data.
physical credential
ToIP
A credential in a physical form such as paper, plastic, or metal.
Contrast with: digital credential.
pii
WebOfTrust
pii
Definition
personally identifiable information
pipelining
WebOfTrust
pipelining
Definition
In computing, a pipeline, also known as a data pipeline, is a set of data processing elements connected in series, where the output of one element is the input of the next one. The elements of a pipeline are often executed in parallel or in time-sliced fashion. Some amount of buffer storage is often inserted between elements.
More on source Wikipedia-pageWhy CESR needs to anticipate pipelining
If you have a stream coming in, you have to look ahead how big a chunk of data can be. We call this a logical atomic data chunk.
JSON is slow
With JSON I don’t know where the end is, so I have to parse the initial stream to find out. That's slow.
Meaning of Pipelining
That once you have a block of data, that you can pull off chunks and de-multiplex from the stream into cores and multiplex them back into the streams. Cores in big datacenters are now max 5 GHz, a pipeline is 40 GHz. So you have to be able to do pipelining (split off over many cores). CESR is the only streaming protocol that has this anticipation on board.
Source: Samuel Smith, KERI Zoom meeting Dec 5 2023.Related
plaintext
ToIP
Unencrypted information that may be input to an encryption operation. Once encrypted, it becomes ciphertext.
Source: NIST-CSRC.
policy
ToIP
Statements, rules or assertions that specify the correct or expected behavior of an entity. For example, an authorization policy might specify the correct access control rules for a software component. Policies may be human-readable or machine-readable or both.
Source: NIST-CSRC
See also: governance framework, governance requirement, rule.
post pad
WebOfTrust
post pad
Definition
the action and / or result of extending a string with trailing pad characters to align to a certain length in bits or bytes.
CESR related
There are two ways to provide the required alignment on 24-bit boundaries to satisfy the composability property. One is post-pad, with trailing pad characters
=, the text domain encoding to ensure that the text domain primitive has a total size (length) that is an integer multiple of 4. This is what naive Base64 encoding does.
The other way is to pre-pad leading bytes of zeros to the raw binary value before conversion to Base64 to ensure the total size of the raw binary value with pre-pad bytes is an integer multiple of 3 bytes. This ensures that the size in characters of the Base64 conversion of the pre-padded raw binary is an integer multiple of 4 characters.
Source IEFT CESR draft
post quantum
WebOfTrust
post quantum
Definition
In cryptography, post-quantum cryptography (PQC) (sometimes referred to as quantum-proof, quantum-safe or quantum-resistant) refers to cryptographic algorithms (usually public-key algorithms) that are thought to be secure against a cryptanalytic attack by a quantum computer.
More on source WikipediaKERI pre-rotation related
Although individual public-private key pairs are most probably not post-quantum proof, by design the pre-rotation mechanism in KERI is post-quantum proof; which means that in the projected future presence of quantum computers KERI will still be safe. Basically, this safety is established by rotating keys before a brute force quantum attack can be effective. As quantum computers might get faster or more effective over time, the rotation intervals simply become shorter and/or increased entropy might be used for key generation.
pre pad
WebOfTrust
pre pad
Definition
the action and / or result of prepending a string with leading pad characters to align to a certain length in bits or bytes.
CESR related
There are two ways to provide the required alignment on 24-bit boundaries to satisfy the composability property. One is post-pad, with trailing pad characters
=, the text domain encoding to ensure that the text domain primitive has a total size (length) that is an integer multiple of 4. This is what naive Base64 encoding does.
The other way is to pre-pad leading bytes of zeros to the raw binary value before conversion to Base64 to ensure the total size of the raw binary value with pre-pad bytes is an integer multiple of 3 bytes. This ensures that the size in characters of the Base64 conversion of the pre-padded raw binary is an integer multiple of 4 characters.
Source IEFT CESR draft
pre rotation
WebOfTrust
pre rotation
Definition
Cryptographic commitment to next rotated key set in previous rotation or inception event.
Rotation
The main purpose of key rotation it to either prevent or recover from a successful compromise of one or more private keys by an exploiter. Given a potentially compromised private key, an exploiter could sign statements and even capture full control over the identifier by rotating the current key pair.
Pre-rotation
Pre-rotation mitigates successful exploit of a given set of signing private keys. There are several assumptions listed in chapter Pre-rotation of the KERI white paper about the circumstances under which pre-rotation is able to sustain this mitigation, e.g. it assumes that the private keys remains private until after issuance of the associated identifier.
Origin and technique
Pre-rotation is a new invention in KERI. Pre-rotation is a cryptographic commitment (a hash) to the next private/public key in the rotation-scheme.
Source: chapter Pre-rotation in whitepaper
pre-rotation
ToIP (DID:Webs)
A key rotation mechanism whereby a set of rotation keys are pre-commited using cryptographic digests, as defined by the KERI specification. See WebOfTrust glossary for more detail.
prefix
WebOfTrust
prefix
Definition
A prefix that is composed of a basic Base-64 (URL safe) derivation code pre-pended to Base-64 encoding of a basic public digital signing key.
Including the derivation code in the prefix binds the derivation process along with the public key to the resultant identifier.An example of the prefix with a one character derivation code and a 32 byte public key encoded into a 44 character Based-64 string follows:
BDKrJxkcR9m5u1xs33F5pxRJP6T7hJEbhpHrUtlDdhh0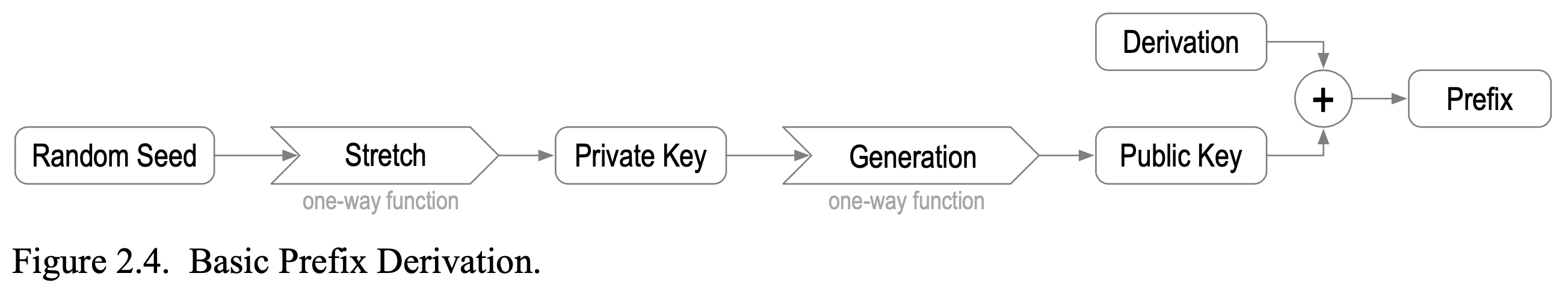
present ~ation
digital.govt.nz
(verb) to offer or hand over for action or settlement[Source: Dictionary]
presentation
ToIP
A verifiable message that a holder may send to a verifier containing proofs of one or more claims derived from one or more digital credentials from one or more issuers as a response to a specific presentation request from a verifier.
Supporting definitions:
eSSIF-Lab: A (signed) digital message that a holder component may send to a verifier component that contains data derived from one or more verifiable credentials (that (a colleague component of) the holder component has received from issuer components of one or more parties), as a response to a specific presentation request of a � verifier component.
presentation attack
ToIP
A type of cybersecurity attack in which the attacker attempts to defeat a biometric liveness detection system by providing false inputs.
Supporting definitions:
NIST-CSRC: Presentation to the biometric data capture subsystem with the goal of interfering with the operation of the biometric system.
presentation exchange
WebOfTrust
presentation exchange
Definition
An exchange that provides disclosure of one or more ACDCs between a Discloser and a Disclosee.
A presentation exchange is the process by which authenticatable information may be exchanged between two parties, namely, the Discloser and Disclosee.
Rule
Each ACDC MUST have an Issuer and MAY have an Issuee. The set of ACDCs so disclosed in a presentation exchange MUST be chained. This set of chained ACDCs define a directed acyclic graph that MUST have at least one vertex and MAY have zero or more edges pointing to other vertices.
presentation request
ToIP
A protocol request sent by the verifier to the holder of a digital wallet to request a presentation.
See also: issuance request.
pretty good privacy
WebOfTrust
pretty good privacy
Definition
Is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991.
More on wikipedia
So also the often confusing GPG term.
primary document
ToIP
The governance document at the root of a governance framework. The primary document specifies the other controlled documents in the governance framework.
primary root of trust
WebOfTrust
primary root of trust
Definition
In KERI a root-of-trust that is cryptographically verifiable all the way to its current controlling key pair in a PKI.
The characteristic primary is one-on-one related to the entropy used for the creation of (the seed of) the private keys.
primitive
WebOfTrust
primitive
Definition
In general in computing a 'primitive' is the simplest type of programming language item. It may also refer to the smallest processing unit accessible by a programmer.
SourceCryptographic primitive
KERI related
In KERI and ACDC it a serialization of a unitary value. A cryptographic primitive is the KERI-suite sense is the serialization of a value associated with a cryptographic operation including but not limited to a digest (hash), a salt, a seed, a private key, a public key, or a signature. All primitives in KERI MUST be expressed in CESR.
principal
privacy
WebOfTrust
privacy
Definition
Privacy is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively.
The domain of privacy partially overlaps with security, which can include the concepts of appropriate use and protection of information. Privacy may also take the form of bodily integrity.
More on source WikipediaKERI related
The three properties, authenticity, confidentiality, and privacy inhabit a trade space. ...One can have any two of the three (privacy, authenticity, confidentiality) at the highest level but not all three.
The trilemma insists that one must make a trade-off by prioritizing one or two properties over a third.The ToIP design goals reflect that trade-off and provide an order of importance. The design goals indicate that one should start with high authenticity, then high confidentiality, and then as high as possible privacy, given there is no trade-off with respect to the other two.
More on Source Samuel Smith SPAC whitepaper.
Also see
privacy policy
ToIP
A statement or legal document (in privacy law) that discloses some or all of the ways a party gathers, uses, discloses, and manages a customer or client's data.
Source: Wikipedia
See also: security policy.
privacy washing
WebOfTrust
privacy washing
Definition
De-identification so that it provides a personal data safe harbour and could be legally acceptable forwarded.
Possible solution
We might need legally enforced pressure for it to be no longer acceptable that you've un-seen the (re-identifiable) personal data.
"Once you see, you can't un-see".
private key
ToIP
In public key cryptography, the cryptographic key which must be kept secret by the controller in order to maintain security.
Supporting definitions:
NIST-CSRC: The secret part of an asymmetric key pair that is typically used to digitally sign or decrypt data.
promiscuous mode
WebOfTrust
promiscuous mode
Definition
It is the mode a watcher runs in. A watcher uses the same code as a witness. However a watcher does so "lacking standards of selection; acting without careful judgment; indiscriminate". Or "Showing little forethought or critical judgment; casual."
SourceMeaning
The function of watcher is different from a witness, however they can both use the same protocol and code, just in a distinct mode.
proof
ToIP
A digital object that enables cryptographic verification of either: a) the claims� from one or more digital credentials, or b) facts about claims that do not reveal the data itself (e.g., proof of the subject being over/under a specific age without revealing a birthdate).
See also: zero-knowledge proof.
proof of authority
WebOfTrust
proof of authority
Definition
Proof that somebody or something has certain rights or permissions. It's about data. Whereas proof of authorship is about data and its original creator.
A proof-of-authority provides verifiable authorizations or permissions or rights or credentials.ACDC and proofs
Proof of authorship and proof of authority are integrated in Authentic Chained Data Containers (ACDCs):
- ACDCs provide a verifiable chain of proof-of-
authorshipof the contained data - A proof-of-
authoritymay be used to provide verifiable authorizations or permissions or rights or credentials. A chained (treed) proof-of-authority enables delegation of authority and delegated authorizations.These proofs of authorship and/or authority provide provenance of an ACDC itself and by association any data that is so conveyed.
(source)
Example APC : book rights sold
The data contained in an ACDC is a book written by Terlalu Bonito; the ACDC also contains anchoring digest, signed by the author at publishing date. Terlalu has sold all rights to publish the book to Liz Smiley The ownership of the book matches the current control over the book and its digital twin: the proof of authority by the chain of ACDCs.
Do not confuse blockchains or consensus algorithms
Proof of authority (PoA) is also an algorithm used with blockchains that delivers comparatively fast transactions through a consensus mechanism based on identity as a stake.
(Source)This is NOT what we mean in SSI, KERI and ACDC.
- ACDCs provide a verifiable chain of proof-of-
proof of authorship
WebOfTrust
proof of authorship
Definition
Proof that somebody or something has originally created certain content. It's about data's inception. Whereas proof-of-authority is about rights attached to this data.
For example, a signature constitutes direct proof of authorship; less directly, handwriting analysis may be submitted as proof of authorship of a document.[21] Privileged information in a document can serve as proof that the document's author had access to that information; such access might in turn establish the location of the author at certain time, which might then provide the author with an alibi.
SourceACDC and proofs
Proof of authorship and proof of authority are integrated in Authentic Chained Data Containers (ACDCs) constituting an Authentic Provenance Chain (APC):
- ACDCs provide a verifiable chain of proof-of-
authorshipof the contained data - A proof-of-
authoritymay be used to provide verifiable authorizations or permissions or rights or credentials. A chained (treed) proof-of-authority enables delegation of authority and delegated authorizations.These proofs of authorship and/or authority provide provenance of an ACDC itself and by association any data that is so conveyed.
(source)
Example APC : book rights sold
The data contained in an ACDC is a book written by Terlalu Bonito; the ACDC also contains anchoring digest, signed by the author at publishing date. Terlalu has sold all rights to publish the book to Liz Smiley The ownership of the book matches the current control over the book and its digital twin: the proof of authority by the chain of ACDCs.
- ACDCs provide a verifiable chain of proof-of-
proof of control
ToIP
See: proof of possession.
proof of personhood
ToIP
Proof of personhood (PoP) is a means of resisting malicious attacks on peer-to-peer networks, particularly, attacks that utilize multiple fake identities, otherwise known as a Sybil attack. Decentralized online platforms are particularly vulnerable to such attacks by their very nature, as notionally democratic and responsive to large voting blocks. In PoP, each unique human participant obtains one equal unit of voting power, and any associated rewards.
Source: Wikipedia.
Also known as: PoP.
proof of possession
ToIP
A verification process whereby a level of assurance is obtained that the owner of a key pair actually controls the private key associated with the public key.
Source: NIST-CSRC.
proof of presence
ToIP
See: liveness detection.
property
protected data
ToIP
Data that is not publicly available but requires some type of access control to gain access.
protocol
WebOfTrust
protocol
Definition
Generic term to describe a code of correct conduct. Also called "etiquette": a code of personal behavior.
KERI and ACDC related
We can distinguish three relevant elaborations on the term 'protocol' to make the concept more specific:
- Communication protocol, a defined set of rules and regulations that determine how data is transmitted in telecommunications and computer networking
- Cryptographic protocol, a protocol for encrypting messages
- Decentralized network protocol, a protocol for operation of an open source peer-to-peer network where no single entity nor colluding group controls a majority of the network nodes
Paraphrased by @henkvancann from source on Wikipedia (click on individual links).
protocol layer
ToIP
In modern protocol design, protocols are layered to form a protocol stack. Layering is a design principle that divides the protocol design task into smaller steps, each of which accomplishes a specific part, interacting with the other parts of the protocol only in a small number of well-defined ways. Layering allows the parts of a protocol to be designed and tested without a combinatorial explosion of cases, keeping each design relatively simple.
Source: Wikipedia.
See also: hourglass model, ToIP stack.
protocol stack
ToIP
The protocol stack or network stack is an implementation of a computer networking protocol suite or protocol family. Some of these terms are used interchangeably but strictly speaking, the suite is the definition of the communication protocols, and the stack is the software implementation of them.
Source: Wikipedia
See also: protocol layer.
provenance
WebOfTrust
provenance
Defintion
From Wikipedia (Source):
Provenance (from the French provenir, 'to come from/forth') is the chronology of the ownership, custody or location of a historical object. The term was originally mostly used in relation to works of art but is now used in similar senses in a wide range of fields, including archaeology, paleontology, archives, manuscripts, printed books, the circular economy, and science and computing.
Purpose
The primary purpose of tracing the provenance of an object or entity is normally to provide contextual and circumstantial evidence for its original production or discovery, by establishing, as far as practicable, its later history, especially the sequences of its formal ownership, custody and places of storage. The practice has a particular value in helping authenticate objects. Comparative techniques, expert opinions and the results of scientific tests may also be used to these ends, but establishing provenance is essentially a matter of documentation. The term dates to the 1780s in English. Provenance is conceptually comparable to the legal term chain of custody.
(Source)Provenance and ACDC
Authentic chained data containers (ACDC) establish provenance in two coherent ways:
- historic documentation of cryptographic verifiable key states and data consistency (result: secure attribution)
- historic documentation of credentials (result: attested veracity)
(@henkvancann)
provenanced
WebOfTrust
provenanced
Definition
The act of verifying authenticity or quality of documented history or origin of something
KERI specific
Focus on authenticity. See provenance.
pseudo random number
WebOfTrust
pseudo random number
Definition
A (set of) value(s) or element(s) that is statistically random, but it is derived from a known starting point and is typically repeated over and over. Pseudo-random numbers provide necessary values for processes that require randomness, such as creating test signals or for synchronizing sending and receiving devices in a spread spectrum transmission.
It is called "pseudo" random, because the algorithm can repeat the sequence, and the numbers are thus not entirely random.
Source
pseudonym
ToIP
A pseudonym is a fictitious name that a person assumes for a particular purpose, which differs from their original or true name (orthonym). This also differs from a new name that entirely or legally replaces an individual's own. Many pseudonym holders use pseudonyms because they wish to remain anonymous, but anonymity is difficult to achieve and often fraught with legal issues.
Source: Wikipedia.
pseudonymous
digital.govt.nz
using a pseudonym[Source: Dictionary]Additional note:Note 1: A pseudonym being an identifier that may relate to an individual entity but does not allow the entity to be identifiable outside the context.
public key
ToIP
Drummond Reed: In public key cryptography, the cryptographic key that can be freely shared with anyone by the controller without compromising security. A party’s public key must be verified as authoritative in order to verify their digital signature.
Supporting definitions:
NIST-CSRC: The public part of an asymmetric key pair that is typically used to verify signatures or encrypt data.
public key certificate
ToIP
A set of data that uniquely identifies a public key (which has a corresponding private key) and an owner that is authorized to use the key pair. The certificate contains the owner’s public key and possibly other information and is digitally signed by a certification authority (i.e., a trusted party), thereby binding the public key to the owner.
Source: NIST-CSRC.
See also: public key infrastructure.
Supporting definitions:
Wikipedia : In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the validity of a public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate's subject. In email encryption, code signing, and e-signature systems, a certificate's subject is typically a person or organization. However, in Transport Layer Security (TLS) a certificate's subject is typically a computer or other device, though TLS certificates may identify organizations or individuals in addition to their core role in identifying devices.
public key cryptography
ToIP
Public key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security.
Source: Wikipedia.
See also: public key infrastructure.
public key description
W3C (DID)
A data object contained inside a DID document that contains all themetadata necessary to use a public key or a verification key.
public key infrastructure
ToIP
A set of policies, processes, server platforms, software and workstations used for the purpose of administering certificates and public-private key pairs, including the ability to issue, maintain, and revoke public key certificates. The PKI includes the hierarchy of certificate authorities that allow for the deployment of digital certificates that support encryption, digital signature and authentication to meet business and security requirements.
Source: NIST-CSRC.
Supporting definitions:
Wikipedia: A public key infrastructure (PKI) is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email.
WebOfTrust
public key infrastructure
Definition
Is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption.
More on Wikipedia
public transaction event log
WebOfTrust
public transaction event log
Definition
is a public hash-linked data structure of transactions that can be used to track state anchored to a KEL.
Public Verifiable Credential Registry
A Public Verifiable Credential Registry can be represented in several TELs to establish issuance or revocation state of a Verifiable Credential (VC).
Control authority vs. issuance and revocation of VCs
The KEL is used to establish control authority over the keys used to commit to the events of the TEL and sign the VC. The events of the TEL are used to establish the issuance or revocation state of the VCs issued by the controller of the identifier represented by the KEL.
public verifiable credential registry
WebOfTrust
public verifiable credential registry
Definition
is a form of a Verifiable Data Registry that tracks the issuance/revocation state of credentials issued by the controller of the KEL.
Two types of TELs will be used for this purpose. The first type of TEL is the management TEL and will signal the creation of the Registry and track the list of Registrars that will act as Backers for the individual TELs for each VC. The second type of TEL is the VC TEL which will track the issued or revoked state of each VC and will contain a reference to it's corresponding management TEL.
Why do we need this?
| TBW | prio2
qry
WebOfTrust
qry
Definition
qry = query
qualified
WebOfTrust
qualified
Definition
When qualified, a cryptographic primitive includes a prepended derivation code (as a proem) that indicates the cryptographic algorithm or suite used for that derivation. This simplifies and compactifies the essential information needed to use that cryptographic primitive. All cryptographic primitives expressed in either text or binary CESR are qualified by definition [CESR-ID]. Qualification is an essential property of CESR [CESR-ID].¶
Sam Smith, IETF-keri
qualified vlei issuer
WebOfTrust
qualified vlei issuer
Definition
The contracting party to the vLEI Issuer Qualification Agreement that has been qualified by GLEIF as a Qualified vLEI Issuer.
Source: Draft vLEI Ecosystem Governance Framework Glossary.Function
Is an authoritative role at the GLEIF organization that is mandated to issue vLEI credentials to others.
qualified vlei issuer vlei credential governance framework
WebOfTrust
qualified vlei issuer vlei credential governance framework
Definition
A document that details the requirements to enable this Credential to be issued by GLEIF to Qualified vLEI Issuers which allows the Qualified vLEI Issuers to issue, verify and revoke Legal Entity vLEI Credentials, Legal Entity Official Organizational Role vLEI Credentials, and Legal Entity Engagement Context Role vLEI Credentials.
qvi authorized representative
WebOfTrust
qvi authorized representative
A designated representative of a QVI authorized, to conduct QVI operations with GLEIF and Legal Entities. Also referring to a person in the role of a QAR.
Paraphrased by @henkvancann from source Draft vLEI Ecosystem Governance Framework Glossary.
race condition
WebOfTrust
race condition
Definition
A race condition or race hazard is the condition of an electronics, software, or other system where the system's substantive behavior is dependent on the sequence or timing of other uncontrollable events. It becomes a bug when one or more of the possible behaviors is undesirable.
Source.KERI related
| TBW prio 2 |
rainbow table attack
WebOfTrust
rainbow table attack
Definition
A rainbow table attack is a password cracking method that uses a special table (a “rainbow table”) to crack the password hashes in a database. Applications don’t store passwords in plaintext, but instead encrypt passwords using hashes. After the user enters their password to login, it is converted to hashes, and the result is compared with the stored hashes on the server to look for a match. If they match, the user is authenticated and able to log
More on source
rct
WebOfTrust
rct
Definition
rct = receipt
read update nullify
WebOfTrust
read update nullify
Definition
Read, update, nullify are a set of actions you (or a server) can take on data. "Read" means to view it, "update" means to change it, and "nullify" means to invalidate it, but not "Delete" it. Mind you, there's also no "Create".
See also
real world identity
ToIP
A term used to describe the opposite of digital identity, i.e., an identity (typically for a person) in the physical instead of the digital world.
Also known as: RWI.
See also: legal identity.
receipt
WebOfTrust
receipt
Definition
event message or reference with one or more witness signatures.
See Also:
key event receipt
receipt log
WebOfTrust
receipt log
Definition
ordered record of all key event receipts for a given set of witnesses
recommended
ToIP
A requirement that is not mandatory to implement in order for an implementer to be in compliance, but which should be implemented unless the implementer has a good reason. In ToIP governance frameworks, a recommendation is expressed using a SHOULD or RECOMMENDED keyword as defined in IETF RFC 2119.
See also: mandatory, optional.
For more information, see: https://www.rfc-editor.org/rfc/rfc2119.
reconciliation
WebOfTrust
reconciliation
Definition
Reconciliation is the process in which you decide to accept a fork of the KEL or not.
Source: Samuel Smith, Zoom meeting Jan 2 2024.Advantage
- You might not have to abandon your identifier after key compromise
- Only few people will see your reconciliation or clean up
record
ToIP
A uniquely identifiable entry or listing in a database or registry.
redundant credential
WebOfTrust
redundant credential
Definition
Multiple credentials issued by the same issuer (e.g. a QVI). They do not have anything to do with each other. They are independently valid.
Misbehaviour
If a QVI issues two instances of the same credential, and is able to only revoke one. This is a governance issue and this behaviour of a QVI is not recommended. But it can be done this way (issue two revoke one) and it leaves the outside world with one other valid credential.
registrant
ToIP
The party submitting a registration record to a registry.
registrar
ToIP
The party who performs registration on behalf of a registrant.
WebOfTrust
registrar
Definition
identifiers that serve as backers for each transaction event log (TEL) under its provenance. This list of Registrars can be rotated with events specific to a certain type of TEL. In this way, a Registrar is analogous to a Backer in KERI KELs and Registrar lists are analogous to Backer lists in KERI KELs.
registration
ToIP
The process by which a registrant submits a record to a registry.
registration agent
A party responsible for accepting registration requests and authenticating the entity making the request. The term may also apply to a party accepting issuance requests for digital credentials.
registration interaction
WebOfTrust
registration interaction
Definition
Setup/Registration interaction, new AID and authorization to establish access control. You present a (vLEI) credential. You don't want that captured and misused. Narrowing the scope to a certain role (e.g. Document Submitter) is a pre-registration via delegatable authority.
The Credential is like a bearer token. Does it matter if the credential was delivered by the issuee? The token is proof of the authorization, but does the delivery require the issuee signature? Depends on the context. If it is an idempotent process resubmission has no effect.
Source: Samuel Smith / Daniel Hardman / Lance Byrd - Zoom meeting KERI Suite Jan 16 2024; discussion minute 30-60 minReplay attack prevention
is important, depending on the context or governance model the issuance itself needs / should / could be signed.
Also see
registry
ToIP
A specialized database of records that serves as an authoritative source of information about entities.
See also: trust registry.
WebOfTrust
registry
Definition
In our digital mental model it's an official digital record book. When people refer to a registry, they usually mean a specific instance, within a multi-tenant registry. E.g. Docker Hub is a multi-tenant registry, where there’s a set of official / public images.
Unique Registries
A unique registry can be referenced in one of two ways, by namespace, or by domain.

ACDC related
ACDCs and SAIDS eliminated the need for a centrally controlled namespace registry for credential schemas. schema registry.
relationship context
ToIP
A context established within the boundary of a trust relationship.
relying party
ToIP
A party who consumes claims or trust graphs from other parties (such as issuers, holders, and trust registries) in order to make a trust decision.
See also: verifier.
Note: The term “relying party” is more commonly used in federated identity architecture; the term “verifier” is more commonly used with decentralized identity architecture and verifiable credentials.
relying party (RP)
digital.govt.nz
the accountable party who relies on presented credential(s) in order to make decisionsAdditional notesNote 1: A Relying Party may employ other parties in the carrying out of their function.
replay attack
WebOfTrust
replay attack
Definition
A replay attack occurs when a cybercriminal eavesdrops on a secure network communication, intercepts it, and then fraudulently delays or resends it to misdirect the receiver into doing what the hacker wants. The added danger of replay attacks is that a hacker doesn't even need advanced skills to decrypt a message after capturing it from the network. The attack could be successful simply by resending the whole thing.
More on how it works and stopping replay attacks at source
replication
digital.govt.nz
the act of repeating, duplicating, copying, or reproducing[Source: Dictionary]
repo
WebOfTrust
repo
Definition
Software is our line of work. In this, 'repo' is the short hand for 'Repository', mostly referring to a software repo(sitory) on Github.com, Gitlab (https://gitlab.com) or other software repository hosting services.
What is a software repository?
A software repository, is a storage location for software packages. Often a table of contents is also stored, along with metadata. A software repository is typically managed by source control or repository managers. Package managers allow automatically installing and updating repositories (sometimes called "packages").
More on Wikipedia
representation
W3C (DID)
As defined for HTTP by [RFC7231]: "information that is intended to reflect apast, current, or desired state of a given resource, in a format that can bereadily communicated via the protocol, and that consists of a set ofrepresentation metadata and a potentially unbounded stream of representationdata." A DID document is a representation of information describing aDID subject. See 6. Representations.
representation-specific entries
W3C (DID)
Entries in a DID document whose meaning is particular to a specificrepresentation. Defined in 4. Data Model and6. Representations. For example, @context inthe JSON-LD representation is arepresentation-specific entry.
reputation
ToIP
The reputation or prestige of a social entity (a person, a social group, an organization, or a place) is an opinion about that entity – typically developed as a result of social evaluation on a set of criteria, such as behavior or performance.
Source: Wikipedia.
WebOfTrust
reputation
Definition
Consistent behaviour over time on the basis of which anyone else makes near-future decisions.
Source: Samuel Smith at IIW37.
reputation graph
ToIP
A graph of the reputation relationships between different entities in a trust community. In a digital trust ecosystem, the governing body may be one trust root of a reputation graph. In some cases, a reputation graph can be traversed by making queries to one or more trust registries.
See also: authorization graph, governance graph, trust graph.
reputation system
ToIP
Reputation systems are programs or algorithms that allow users to rate each other in online communities in order to build trust through reputation. Some common uses of these systems can be found on e-commerce websites such as eBay, Amazon.com, and Etsy as well as online advice communities such as Stack Exchange.
Source: Wikipedia.
reputational trust
WebOfTrust
requirement
ToIP
A specified condition or behavior to which a system needs to comply. Technical requirements are defined in technical specifications and implemented in computer systems to be executed by software actors. Governance requirements are defined in governance documents that specify policies and procedures to be executed by human actors. In ToIP architecture, requirements are expressed using the keywords defined in Internet RFC 2119.
See also: mandatory, recommended, optional.
For more information, see: https://www.rfc-editor.org/rfc/rfc2119.
reserve rotation
WebOfTrust
reserve rotation
Definition
One important use case for partial rotation is to enable pre-rotated key pairs designated in one establishment event to be held in reserve and not exposed at the next (immediately subsequent) establishment event.
Source IETF-KERI draft 2022 by Samual Smith.
resource
W3C (DID)
As defined by [RFC3986]: "...the term 'resource' is used in a general sensefor whatever might be identified by a URI." Similarly, any resource might serveas a DID subject identified by a DID.
rev
WebOfTrust
rev
Definition
rev = vc revoke, verifiable credential revocation
revocation
Nist
The process of permanently ending the binding between a certificate and the identity asserted in the certificate from a specified time forward.ToIP
In the context of digital credentials, revocation is an event signifying that the issuer no longer attests to the validity of a credential they have issued. In the context of cryptographic keys, revocation is an event signifying that the controller no longer attests to the validity of a public/private key pair for which the controller is authoritative.
See also: issuance, presentation.
Supporting definitions:
eSSIF-Lab: the act, by or on behalf of the party that has issued the credential, of no longer vouching for the correctness or any other qualification of (arbitrary parts of) that credential.
NIST-CSRC: For digital certificates: The process of permanently ending the binding between a certificate and the identity asserted in the certificate from a specified time forward. For cryptographic keys: A process whereby a notice is made available to affected entities that keys should be removed from operational use prior to the end of the established cryptoperiod of those keys.
WebOfTrust
revocation
Definition
Revocation is the act of recall or annulment. It is the cancelling of an act, the recalling of a grant or privilege, or the making void of some deed previously existing.
More on source WikipediaIn identity
The term revocation has two completely different meanings in the identity space. In key management one may speak of revoking keys. With statement issuance, authorization issuance, or credential issuance, one may speak of revoking an authorization statement, a token, or a credential.
This becomes confusing when the act of revoking keys also implicitly revokes the authorization of statements signed with those keys. Any statement may be effectively authorized by virtue of the attached signature(s) made with a set of authoritative keys. The statement itself may be authorizing some other function in the system. So, the verification of the signature on an authorizing statement is essential to determining the authoritativeness of the associated authorized function. To clarify when an authorization is conveyed via a signed statement, the signature acts to authorize the statement.How KERI avoids confusion
KERI terminology usually avoids confusion between rotation and revocation because a key rotation operation is the equivalent of a key revocation operation followed by a key replacement operation. So one operation, rotate, is implemented instead of two operations (revoke and replace).
A bare key revocation is indicated by replacement with a null key. So only one operation is needed, that is, rotate where a special case of rotation is to rotate to a null key.Also see
revocation event
WebOfTrust
revocation event
Definition
Considerations
KERI related
An event that revokes control authority over an identifier. From that point in time the authoritative key-pairs at hand are not valid anymore.
The time stamp of a revocation is useful but not for security purposes, it can be gamed by an attacker. KERI should be fitted in a way so that it's not possible to rewrite history. The tool we have is the ordering of the events in a KEL.
Also see
Beware: Suspension is non-existing
A temporary revocation of a grant or privilege is called a suspension. We don't have this type of state or event in KERI.
ricardian contract
WebOfTrust
ricardian contract
Definition
The Ricardian contract, as invented by Ian Grigg in 1996, is a method of recording a document as a contract at law, and linking it securely to other systems, such as accounting, for the contract as an issuance of value.
It is robust through use of identification by cryptographic hash function, transparent through use of readable text for legal prose and efficient through markup language to extract essential information.
More at source WikipediaRelated to KERI and ACDC
Ricardian contracts provide a human readable twin to the seals and and signatures (commitments) in binary format in ACDC.
risk
digital.govt.nz
effect of uncertainty on objectives[Source: ISO 31073:2022]Additional notes:Note 1: An effect is a deviation from the expected. It can be positive, negative or both, and can address, create or result in opportunities and threats.Note 2: Objectives can have different aspects and categories and can be applied at different levels.Note 3: Risk is usually expressed in terms of risk sources, potential events, their consequences and their likelihood.ToIP
The effects that uncertainty (i.e. a lack of information, understanding or knowledge of events, their consequences or likelihoods) can have on the intended realization of an objective of a party.
Source: eSSIF-Lab
Supporting definitions:
NIST-CSRC: A measure of the extent to which an entity is threatened by a potential circumstance or event, and typically a function of: (i) the adverse impacts that would arise if the circumstance or event occurs; and (ii) the likelihood of occurrence.
risk assessment
ToIP
The process of identifying risks to organizational operations (including mission, functions, image, reputation), organizational assets, individuals, other organizations, and the overall ecosystem, resulting from the operation of an information system. Risk assessment is part of risk management, incorporates threat and vulnerability analyses, and considers risk mitigations provided by security controls planned or in place.
Source: NIST-CSRC.
Also known as: risk analysis.
Supporting definitions:
Wikipedia: Risk assessment determines possible mishaps, their likelihood and consequences, and the tolerances for such events.[1] The results of this process may be expressed in a quantitative or qualitative fashion. Risk assessment is an inherent part of a broader risk management strategy to help reduce any potential risk-related consequences. More precisely, risk assessment identifies and analyses potential (future) events that may negatively impact individuals, assets, and/or the environment (i.e. hazard analysis). It also makes judgments "on the tolerability of the risk on the basis of a risk analysis" while considering influencing factors (i.e. risk evaluation).
risk decision
ToIP
See: trust decision.
risk management
ToIP
The process of managing risks to organizational operations (including mission, functions, image, or reputation), organizational assets, or individuals resulting from the operation of an information system, and includes: (i) the conduct of a risk assessment; (ii) the implementation of a risk mitigation strategy; and (iii) employment of techniques and procedures for the continuous monitoring of the security state of the information system.
Source: NIST-CSRC.
Supporting definitions:
eSSIF-Lab: a process that is run by (or on behalf of) a specific party for the purpose of managing the risks that it owns (thereby realizing specific risk objectives).
Wikipedia: Risk management is the identification, evaluation, and prioritization of risks (defined in ISO 31000 as the effect of uncertainty on objectives) followed by coordinated and economical application of resources to minimize, monitor, and control the probability or impact of unfortunate events or to maximize the realization of opportunities.
risk mitigation
ToIP
Prioritizing, evaluating, and implementing the appropriate risk-reducing controls/countermeasures recommended from the risk management process.
Source: NIST-CSRC.
role
digital.govt.nz
proper or customary function[Source: Dictionary]ToIP
A defined set of characteristics that an entity has in some context, such as responsibilities it may have, actions (behaviors) it may execute, or pieces of knowledge that it is expected to have in that context, which are referenced by a specific role name.
Source: eSSIF-Lab.
See also: role credential.
role credential
ToIP
A credential claiming that the subject has a specific role.
role-based access control
ToIP
Access control based on user roles (i.e., a collection of access authorizations a user receives based on an explicit or implicit assumption of a given role). Role permissions may be inherited through a role hierarchy and typically reflect the permissions needed to perform defined functions within an organization. A given role may apply to a single individual or to several individuals.
Source: NIST-CSRC.
Supporting definitions:
Wikipedia: In computer systems security, role-based access control (RBAC) or role-based security is an approach to restricting system access to authorized users, and to implementing mandatory access control (MAC) or discretionary access control (DAC).
root autonomic identifier
WebOfTrust
root autonomic identifier
Definition
An entity may provide the root-of-trust for some ecosystem (with delegation )via its root AID. Let’s call this the RID for "root AID". The RID must be protected using the highest level of security in its key management. Although through the use of a multi-valent key management infrastructure, the entity can employ extreme protection of the RID while still enabling more performant key management infrastructure for its operations.
Source Universal Identifier Theory by Samuel Smith
root of trust
WebOfTrust
root of trust
Definition
A root-of-trust is some component of a system that is secure by design and its security characteristics may be inherently trusted or relied upon by other components of the system.
Root-of-trust
Replace human basis-of-trust with cryptographic root-of-trust. With verifiable digital signatures from asymmetric key cryptography we may not trust in “what” was said, but we may trust in “who” said it.
The root-of-trust is consistent attribution via verifiable integral non-repudiable statements.A root of trust is a foundational component or process in the identity system that is relied on by other components of the system and whose failure would compromise the integrity of the bindings. A root of trust might be primary or secondary depending on whether or not it is replaceable. Primary roots of trust are irreplaceable. Together, the roots of trust form the trust basis for the system.
KERI related
We distinguish a primary root-of-trust in a KEL and a secondary root-of-trust, for example in a TEL or data on a blockchain.
rot
WebOfTrust
rot
Definition
JSON field name (attribute) for Rotation Event; its content (value) contains a hash pointer. All TEL events are anchored in a KEL in either ixn (interaction) or rot (rotation events). This is the foundation enabling a verifiable credential protocol to be built on top of KERI.
Source Kent Bull 2023Also see
rotation
rotation authority
WebOfTrust
rotation authority
Definition
The (exclusive) right to rotate the authoritative key pair and establish changed control authority.
Relation to rotation authority
The original controller of an AID can hold exclusive rotation authority. Because control authority is split between two key sets, the first for signing authority and the second (pre-rotated) for rotation authority, the associated thresholds and key list can be structured in such a way that a designated custodial agent can hold signing authority while the original controller can hold exclusive rotation authority.
rotation event
ToIP (DID:Webs)
A key event that provides the information needed to change the key state for an AID using pre-rotation, as defined by the KERI specification. See WebOfTrust glossary for more detail.WebOfTrust
rotation event
Definition
An establishment event representing a transfer of root control authority of an identifier from the current set of controlling keys to new set committed to in the prior establishment event (inception or rotation) as the pre-rotated key pair set.
Source KERI Whitepaper Section 7.21 page 46This event provides the information needed to change the key-state including a change to the set of authoritative keypairs for an AID.
Source Sam SmithThe inner working
We start with a root-of-trust in public/private key-pair that is bound to an identifier derived from the key-pair. From this key-pair and then we can rotate controlling authority to other key-pairs with signed rotation messages (events). These rotation messages are witnessed by witnesses designated in the inception event and any subsequent rotation events. Upon completion of successful witnessing a receipt message is sent back to the identity controller performing the rotation and the controller keeps track of these receipts in a key event receipt log.
The infrastructure needed to keep track of these key events including inception events, rotation events, and non-establishment events is key event receipt infrastructure, thus the acronym "KERI": Key Event Receipt Infrastructure.\
(SamASmith)
router
ToIP
A router is a networking device that forwards data packets between computer networks. Routers perform the traffic directing functions between networks and on the global Internet. Data sent through a network, such as a web page or email, is in the form of data packets. A packet is typically forwarded from one router to another router through the networks that constitute an internetwork (e.g. the Internet) until it reaches its destination node. This process is called routing.
Source: Wikipedia.
routing
ToIP
Routing is the process of selecting a path for traffic in a network or between or across multiple networks. Broadly, routing is performed in many types of networks, including circuit-switched networks, such as the public switched telephone network (PSTN), and computer networks, such as the Internet. A router is a computing device that specializes in performing routing.
Source: Wikipedia.
rpy
WebOfTrust
rpy
Definition
rpy = reply
rule
ToIP
A prescribed guide for conduct, process or action to achieve a defined result or objective. Rules may be human-readable or machine-readable or both.
See also: governance framework, policy.
run off the crud
WebOfTrust
run off the crud
Definition
RUN off the CRUD
RUN stands for Read , Update, Nullify. Why is it preferred ('run off') over the CRUD (Create, Update, Delete)?
Consider the need to protect 'authentic data' in a decentralized environment.
In a decentralized control model, the data always originates from a controller (aka client). The data created (sourced) by the controller follows the principle of 'Non-Interactive Replay Monotonicity' to be able to protect the data from a replay (events are changed) or a deletion (some events are deleted) attacks. That is to say, the data (or events comprising it) is never deleted, it's rather always added to via updates. Each update, therefore, forms a verifiable, continuous log ( e.g. by providing growing sequence number, date timestamp, etc for each update). To enable invalidation of data, a special update, called Nullify, is used.
The client, therefore, updates the server (it's peer or peers), which just maintains the log following certain rules (see BADA - Best Available Data Acceptance).
To summarise, the server can only Read the log, add Updates to it, including Nullifying ones. So no Create or Delete.
sally
WebOfTrust
sally
Definition
is an implementation of a verification service and acting as a reporting server. It is purpose-built software for the vLEI ecosystem to allow participants in the vLEI ecosystem present credentials, so the GLEIF Reporting API can show what vLEIs are; issued to Legal Entities.
Inner working
The Sally vLEI Audit Reporting Agent receives presentations of credentials and notices of revocation, verifies the structure and cryptographic integrity of the credential or revocation event and performs a POST to the configured webhook URL
Source
salt
Nist
As used in this Recommendation, a byte string (which may be secret or non-secret) that is used as a MAC key by either: 1) a MAC-based auxiliary function H employed in one-step key derivation or 2) a MAC employed in the randomness-extraction step during two-step key derivation.WebOfTrust
salt
Definition
In cryptography, a salt is random data that is used as an additional input to a one-way function that hashes data, a password or passphrase.
Usage
Salts are used to safeguard passwords in storage. Historically, only a cryptographic hash function of the password was stored on a system, but over time, additional safeguards were developed to protect against duplicate or common passwords being identifiable (as their hashes are identical).[2] Salting is one such protection.
More in source
salter
salty nonce blinding factor
WebOfTrust
salty nonce blinding factor
Definition
For ease of sharing a secret and hiding information with this secret of Blindable State TELs we use a Salty Nonce Blinding Factor. You’d like to hide the state of certain credentials to some verifiers in the future, while keeping the state verifiable for others.
How
A way to share the key to blind/unblind the state of a TEL is
- HTOP, HMAC-Based One-Time Password
- Time-Based One-Time Password
- HDKM, Hierarchical Deterministic Key Management, based on a shared master key you could split off subkeys in a predictable manner.
The blinding is performed by the issuer, the issuee could request the blinding.
Example
I don’t want my employment states shared in the future with former possible employers.
More info
schema
ToIP
A framework, pattern, or set of rules for enforcing a specific structure on a digital object or a set of digital data. There are many types of schemas, e.g., data schema, credential verification schema, database schema.
For more information, see: W3C Data Schemas.
Note: credentialSchema is a Property Definition in the W3C VC Data Model, see 3.2.1
schema namespace registry
WebOfTrust
schema namespace registry
Definition
a centrally managed schema registry where corporations or individuals reserve schemas within a specific namespace in order to have an interoperable schema that is labeled with a corporation-specific or individual-specific namespace.
ACDC related
Graphs in ACDC have decentralised the old-school schema registry, so it's interoperable by design.
schema registry
WebOfTrust
schema registry
Definition
Central registry for credential schemas based on namespaces.
ACDC related
ACDCs and SAIDS eliminated the need for a centrally controlled namespace registry for credential schemas.
KERI related and ToIP definitions
From our vocabulary that contains the term "Public verifiable credential registry" there's follow-up on ToIP definitions like | TBW |
Comparison and explanation
Syntio comparison of (old-school?) centralized schema registries.
This source has conceptual explanations in diagrams like the one below and code examples. However, be aware that ACDC solves this in a different way with KERI-based verifiable data structures and graph fragments.

scope
ToIP
In the context of terminology, scope refers to the set of possible concepts within which: a) a specific term is intended to uniquely identify a concept, or b) a specific glossary is intended to identify a set of concepts. In the context of identification, scope refers to the set of possible entities within which a specific entity must be uniquely identified. In the context of specifications, scope refers to the set of problems (the problem space) within which the specification is intended to specify solutions.
Supporting definitions:
eSSIF-Lab: the extent of the area or subject matter (which we use, e.g., to define pattern, concept, term and glossaries in, but it serves other purposes as well).
seal
WebOfTrust
seal
Definition
A cryptographic commitment in the form of a cryptographic digest or hash tree root (Merkle root) that anchors arbitrary data or a tree of hashes of arbitrary data to a particular event in the key event sequence.
Source KERI Whitepaper section 7.23 page 47A seal is a cryptographic proof in a secondary root-of-trust (e.g. TEL) that is anchored in a primary-root-of-trust (e.g.KEL).
Source Same SmithWhat is it worth?
The payload of the seal becomes immutable and the controller commits a signature to the seal.
| TBW prio 2 |
second party
ToIP
The party with whom a first party engages to form a trust relationship, establish a connection, or execute a transaction.
See also: third party.
secondary root of trust
WebOfTrust
secondary root of trust
Definition
In KERI its a root-of-trust that, for its secure attribution, depends on another verifiable data structure (VDS) which MUST be a primary root-of-trust.
By its nature and cryptographic anchoring via seals to a primary root-of-trust, a secondary root-of-trust still has a high level of trustability and can be automatically verified.
secure
WebOfTrust
secure asset transfer protocol
WebOfTrust
secure asset transfer protocol
Definition
An IETF protocol (and working group) in the making (as of mid 2022) for moving assets between blockchains.
More information at IETF
Relationship with KERI
KERI has portable identifiers per definition. KERI identifier are not locked into silos like distributed ledgers. KERI IDs have their own native hash-chained data structures (KEL, KERL and TEL).
secure attribution
WebOfTrust
secure attribution
Definition
In short: secure attribution is "whodunit?!" in cyberspace.
Secure attribution is strongly related to making and proving statements. A controller makes statements to the a validator or verifier, who in turn validates the statements issued. A controller "owns" the statement: content and attribution via digital signatures.
Secure attribution of a statement is a way of proving that the statement is an authentic statement of thecontroller.Relationship with KERI
In the context of KERI and ACDC secure means a
Validatormay cryptographically verify the statement.
secure multi-party computation
ToIP
See: multi-party computation.
secure private authentic confidentiality
WebOfTrust
secure private authentic confidentiality
Definition
ToIP Trust Spanning Layer Group realized we do have a secure authentication layer (KERI) but we don't have a secure confidentiality and privacy mechanism. Sam Smith proposes SPAC paper to define this.Related:https://www.usenix.org/system/files/sec22-cohen.pdf
Reason
If someone has set up a public AID, with public Witnesses we don't have a mechanism to support private communication with this AID| TBW |
Details
Tech meet KERI recording from minute 35, date June 29 2023 and also discussed Tech meeting KERI Aug 3 2023 from minute 30 or so till end.
security
Nist
A condition that results from the establishment and maintenance of protective measures that enable an organization to perform its mission or critical functions despite risks posed by threats to its use of systems. Protective measures may involve a combination of deterrence, avoidance, prevention, detection, recovery, and correction that should form part of the organizations risk management approach.WebOfTrust
security
Definition
'secure' is free from or not exposed to danger or harm; safe. For identifiers security typically means secure from exploit or compromise. More specifically an identifier is secure with respect to an entity if there is a mechanism by which that entity may prove it has control over the identifier.
security cost performance architecture trade off
WebOfTrust
security cost performance architecture trade off
Definition
The degree of protection offered by a key management infrastructure usually forces a trade-off between security, cost, and performance.
Typically, key generation happens relatively infrequently compared to event signing. But highly secure key generation may not support highly performant signing. This creates an architecture trade-off problem.
Paraphrased from source Universal Identifier Theory by Samuel Smith
security domain
ToIP
An environment or context that includes a set of system resources and a set of system entities that have the right to access the resources as defined by a common security policy, security model, or security architecture.
Source: NIST-CSRC
See also: trust domain.
security overlay properties trillema
WebOfTrust
security overlay properties trillema
Definition
An identifier system has some degree of any combination of the three properties authenticity, privacy and confidentiality, but not all three completely.
Why a trillema?
The reason a system may not provide all three completely is that no single cryptographic operation provides all three properties.
As a result any cryptographic system must layer the operations. But layering exposes weaknesses due to the separation between the layers. Because no single layer can exhibit all three properties, one must pick one or two properties for the bottom layer and then layer on top the remaining property or properties on one or more layers.
Source: Universal Identifier Theory by Samuel Smith
security policy
ToIP
A set of policies and rules that governs all aspects of security-relevant system and system element behavior.
Source: NIST-CSRC
See also: privacy policy.
seed
WebOfTrust
seed
Definition
In cryptography a 'seed' is a pseudorandomly generated number, often expressed in representation of a series of words.
Paraphrased from wikipediaExample 24-word seed
broken toddler farm argue elder behind sea ramp cake rabbit renew option combine guilt inflict sentence what desert manage angry manual grit copy hundredTest here yourself.
Pseudorandom is not exactly random
Although sequences that are closer to truly random can be generated using hardware random number generators, pseudorandom number generators are important in practice for their speed in number generation and their reproducibility.
Source wikipedia
selective disclosure
WebOfTrust
selective disclosure
Definition
Selective disclosure is a from partial disclosure that has a different cryptographic fundament: a sort of cryptographic aggregator (not an accumulator).
Selective disclosure is a list of field maps. You can choose to blind and publish every single field map, but you have to disclosure all the field maps, either blinded or published.
It is an aggregator because you have to disclosure all the blinded fields when you do the selective disclosure.
Related
Source: distilled from ACDC Zoom meeting, date March 28, 2023
self addressing data
WebOfTrust
self addressing data
Definition
While all KERI event messages are self-addressing data (SAD), there is a broad class of SADs that are not KERI events but that require signature attachments. ACDC Verifiable credentials fit into this class of SADs. With more complex data structures represented as SADs, such as verifiable credentials, there is a need to provide signature attachments on nested subsets of SADs.
(Philip Feairheller, ietf-cesr-proof)
self addressing identifier
WebOfTrust
self addressing identifier
Definition
An identifier that is deterministically generated from and embedded in the content it identifies, making it and its data mutually tamper-evident.
To generate a SAID
- Fully populate the data that the SAID will identify, leaving a placeholder for the value of the SAID itself.
- Canonicalize the data, if needed. The result is called the SAID's identifiable basis.
- Hash the identifiable basis. The result is the value of the SAID.
- Replace the placeholder in identifiable basis the with the newly generated identifier, so the SAID is embedded in the data it identifies. The result is called the saidified data.
To verify that a SAID truly identifies a specific chunk of data
- Canonicalize the data, if needed. The result is claimed saidified data.
- In the claimed saidified data, replace the SAID value with a placeholder. The result is the identifiable basis for the SAID.
- Hash the identifiable basis.
- Compare the hash value to the SAID. If they are equal, then the SAID identifies the claimed saidified data.
Differences in SAID algorthms manifest in the following choices
- how data is canonicalized
- which hash algorithm is used
- which placeholder is used
- how the bytes produced by the hash algorithm are encoded
- how the SAID value is formatted
Notation
A terse way to describe a SAID and its data is to write an expression that consists of the token
SAIDfollowed by a token with field names in canonical order, where the field containing the SAID itsef is marked by the suffix=said. For example, the saidification of a simpleContactInfodata structure might be given asSAID(name, address, phone, email, id=said).
self certifying identifier
WebOfTrust
self certifying identifier
Definition
A Self-Certifying Identifier (SCID) cryptographically binds an identifier to a public and private key pair. It is an identifier that can be proven to be the one and only identifier tied to a public key using cryptography alone.
Signing
A controller issues an own Identifier by binding a generated public private key pair to an identifier. After this a controller is able to sign the identifier and create a certificate. Also called a cryptonym. The simplest form of a self-certifying identifier includes either the public key or a unique fingerprint of the public key as a prefix in the identifier.
Important SCID properties:
- Self-contained secure cryptographic root-of-trust
- Decentralized control via private key management
- Universally unique identifiers
Related to KERI
A self-certifying identifier (SCID) is a type of cryptonym that is uniquely cryptographically derived from the public key of an asymmetric non-repudiable signing keypair, (public, private).
It is self-certifying or more precisely self-authenticating because it does not rely on a trusted entity. The authenticity of a non-repudiable signature made with the private key may be verified by extracting the public key from either the identifier itself or incepting information uniquely associated with the cryptographic derivation process for the identifier. In a basic SCID, the mapping between an identifier and its controlling public key is self-contained in the identifier itself. A basic SCID is ephemeral i.e. it does not support rotation of its keypairs in the event of key weakness or compromise and therefore must be abandoned once the controlling private key becomes weakened or compromised from exposure.
self framing
WebOfTrust
self framing
Definition
a textual encoding that includes type, size, and value is self-framing.
Source Samual M SmithDetailed explanation
A self-framing text primitive may be parsed without needing any additional delimiting characters. Thus a stream of concatenated primitives may be individually parsed without the need to encapsulate the primitives inside textual delimiters or envelopes. Thus a textual self-framing encoding provides the core capability for a streaming text protocol like STOMP or RAET.
Related to CESR
Although a first class textual encoding of cryptographic primitives is the primary motivation for the CESR protocol defined herein, CESR is sufficiently flexible and extensible to support other useful data types, such as, integers of various sizes, floating point numbers, date-times as well as generic text. Thus this protocol is generally useful to encode in text data data structures of all types not merely those that contain cryptographic primitives.
self sovereign identity
WebOfTrust
self sovereign identity
Definition
Self-Sovereign Identity (SSI) is a term that has many different interpretations, and that we use to refer to concepts/ideas, architectures, processes and technologies that aim to support (autonomous) parties as they negotiate and execute electronic transactions with one another.
Paraphrased by @henkvancann, sources eSSIF-lab and ToIP.More in ToIP glossary
eSSIF-lab excerpt
The definition started in the blog "The Path to Self-Sovereign Identity" by Christopher Allen in 2016. has not resulted in a consensus today. While some see the ten principles of SSI that Allen proposed as the definition of SSI, he formulated them as "a departure point to provoke a discussion about what's truly important". And it is obvious that what is important differs per party.
Source eSSIF-lab
self sovereignty
WebOfTrust
self-addressing identifier (SAID)
ToIP (DID:Webs)
An identifier that is uniquely and cryptographically bound to a serialization of data (content-addressable) while also being included as a component in that serialization (self-referential), as defined by the CESR specification. See WebOfTrust glossary for more detail.
self-asserted
ToIP
A term used to describe a claim or a credential whose subject is also the issuer.
self-certified
ToIP
When a party provides its own certification that it is compliant with a set of requirements, such as a governance framework.
self-certifying identifier
ToIP
A subclass of verifiable identifier that is cryptographically verifiable without the need to rely on any third party for verification because the identifier is cryptographically bound to the cryptographic keys from which it was generated.
See also: autonomic identifier.
Also known as: SCID.
self-sovereign
digital.govt.nz
(concept) an entity having sole ownership over the ability to control their accounts and information[Source: Based on searchsecurity.techtarget.com]
self-sovereign identity
ToIP
A decentralized identity architecture that implements the Principles of SSI.
See also: federated identity.
Supporting definitions:
eSSIF-Lab: SSI (Self-Sovereign Identity) is a term that has many different interpretations, and that we use to refer to concepts/ideas, architectures, processes and technologies that aim to support (autonomous) parties as they negotiate and execute electronic transactions with one another.
Wikipedia: Self-sovereign identity (SSI) is an approach to digital identity that gives individuals control over the information they use to prove who they are to websites, services, and applications across the web. Without SSI, individuals with persistent accounts (identities) across the internet must rely on a number of large identity providers, such as Facebook (Facebook Connect) and Google (Google Sign-In), that have control of the information associated with their identity.
sensitive data
ToIP
Personal data that a reasonable person would view from a privacy protection standpoint as requiring special care above and beyond other personal data.
Supporting definitions:
PEMC IGR: While all Personal Information may be regarded as sensitive in that an unauthorized processing of an individual’s data may be offensive to that person, we use the term here to denote information that a reasonable person would view as requiring special care above and beyond other personal data. For reference see GDPR Recital #51 or Sensitive Personal Data in the W3C Data Privacy Vocabulary.
server sent event
WebOfTrust
server sent event
Definition
Mailbox notifications; a streaming service for the agent U/I, to get notifications from the KERI system itself.
service
digital.govt.nz
a system or method of providing people with the use of something, as electric power, water, transportation, mail delivery.[Source: Dictionary]Additional notes:Note 1: Today service has a broader application than utilities, such as finance, employment and compliance services.Note 2: A service may contain 1 or more transactions.
service endpoint
W3C (DID)
A network address, such as an HTTP URL, at which services operate onbehalf of a DID subject.
services
W3C (DID)
Means of communicating or interacting with the DID subject orassociated entities via one or more service endpoints.Examples include discovery services, agent services, social networkingservices, file storage services, and verifiable credential repository services.
session
digital.govt.nz
an unbroken interactive information interchange between 2 or more entities[Source: Wikipedia (computer science) modified]ToIP
See: communication session.
siger
WebOfTrust
siger
See Indexed signature
signed digest
WebOfTrust
signed digest
Definition
commitment to content, by digitally signing a digest of this content.
signer
WebOfTrust
signer
Definition
A primitive that represents a private key. It has the ability to create Sigers and Cigars (signatures).
Source by Jason Colburne
signify
WebOfTrust
signify
Definition
Signify is a web client (key) event signing - and key pair creation app that minimizes the use of KERI on the client.
The main reason is that we want to minimize what needs to be put in the client or the cloud. Most proofs should be cryptographically verifiable and it should not be able to be repudiated (successful pointing fingers should be prevented), and this happens when the signatures come straight from the controller.
Background
On a small set of activities that need to be protected in infrastructure for key management
- key pair creation
- key pair storage
- event generating
- event signing
- event verification
Finger pointing
What are the liabilities do a cloud host has to worry about?
- Cloud host does not want to see keys (non-repudiation). So we want to move event signing out of the cloud agent.
- Key state (next digest and current signing key) come from the client
- Cloud host ensures that the code supply chain is secure and never sees the private keys
signify keria request authentication protocol
WebOfTrust
signify keria request authentication protocol
Definition
SKRAP is a client to the KERIA server. Mobile clients will be using SKRAP to connect to KERI AIDs via agents in the new, multi-tenant Mark II Agent server, KERIA. Also, browser extensions will use SKRAP in order to use a wallet similar to MetaMask, except it will be KERIMask, and it will be a browser extension.KERIMask will connect to KERIA servers in order for a person to control AIDs from their browser extension.
SKRAP is also usable from HSMs and hardware wallets because the keys from the hardware wallet, along with some app code, connect through SKRAP to agents running in a KERIA server.
Signify signs things at the edge. This includes ACDCs. KERIA will be used to send communications between agents. The things KERIA sends are signed by Signify.
Source: Kent Bull in KERI Slack May 2023
Related to KERIA
The KERIA service will expose 3 separate HTTP endpoints on 3 separate network interfaces.
- Boot Interface - Exposes one endpoint for Agent Worker initialization.
- Admin Interface - The REST API for command and control operations from the Signify Client.
- KERI Protocol Interface - CESR over HTTP endpoint for KERI protocol interactions with the rest of the world.
This separation allows for the Boot interface to be expose to internal infrastructure only (or disabled all together) while exposing the other two interfaces externally. If a KERIA instance is launched in static worker mode, meaning all agent workers are configured at start up only the Boot interface can be disabled completely.
More at source Github Signify
signing authority
WebOfTrust
signing authority
Definition
The authority to sign on behalf of the controller of the authoritative key pair. Often in situation where delegation has taken place, e.g. a custodial agent. These are limited rights because rotation authority is not included.
Relation to rotation authority
The original controller of an AID can hold exclusive rotation authority. Because control authority is split between two key sets, the first for signing-authority and the second (pre-rotated) for rotation authority, the associated thresholds and key list can be structured in such a way that a designated custodial agent can hold signing authority while the original controller can hold exclusive rotation authority.
signing threshold
WebOfTrust
signing threshold
Definition
Is the minimum number of valid signatures to satisfy the requirement for successful verification in a Threshold Signature Scheme.
Example 2-of-3 signature
In a 2-of-3 signature scheme the threshold is 2. This means that 2 valid signatures are enough to fulfil the required signature.
simple keri for web auth
WebOfTrust
simple keri for web auth
Definition
A KERI implementation that sacrifices performance or other non-security feature for usability. In general a narrow application of KERI may not require all the features of KERI but those features that it does support must still be secure.
More on source Github Repo SKWA.Design
Designed for private clouds, just like Keep. Signify is designed for public clouds.
single signature identifier
WebOfTrust
single signature identifier
Definition
or single sig identifier; is an identifier controlled by a one-of-one signing keypair
sniffable
WebOfTrust
sniffable
Definition
A stream is sniffable as soon as it starts with a group code or field map; in fact this is how our parser (Parside) works. and detects if the CESR stream contains a certain datablock. The datablock of CESR binary, CESR Text, JSON, CBOR, MGPK have an Object code or the Group code (binary or text) and it's always a recognizable and unique three bit combination.
Challenge
We have the Cold start problem of a stream: you don't where to start recognizing structured data.
Criterium
So a stream is either sniffable or not, when it has or has not the fore-mentioned group- or object-codes.
Source: Sam Smith, Zoom Meeting KERI, Dec 5 2023Related
sniffer
Nist
See packet sniffer and passive wiretapping.WebOfTrust
sniffer
Definition
The sniffer is part of Parside and detects if the CESR stream contains CESR binary, CESR Text, JSON, CBOR, MGPK.
Working
If any of JSON, CBOR, MGPK then the parser regexes to find the version string inside the JSON, CBOR, and MGPK and from the version string extracts the number of characters/bytes that is the length of the JSON, CBOR, or MGPK. The parser then resumes sniffing. When the sniff result is 'CESR' then when at the top level looks for the CESR version count code or any other count codes.
Source Slack Cesride thread: Feb 2 2023
Related
sociotechnical system
ToIP
An approach to complex organizational work design that recognizes the interaction between people and technology in workplaces. The term also refers to coherent systems of human relations, technical objects, and cybernetic processes that inhere to large, complex infrastructures. Social society, and its constituent substructures, qualify as complex sociotechnical systems.
Source: Wikipedia
software agent
ToIP
In computer science, a software agent is a computer program that acts for a user or other program in a relationship of agency, which derives from the Latin agere (to do): an agreement to act on one's behalf. A user agent is a specific type of software agent that is used directly by an end-user as the principal.
Source: Wikipedia.
See also: digital agent.
solicited issuance
source of truth
WebOfTrust
source of truth
Definition
The source of truth is a trusted data source that gives a complete picture of the data object as a whole.
Source: LinkedIN.KERI and ACDC context
Source of a particular piece of information from one place, considered to present the truth. However both KERI and ACDC only commit to the secure attribution of who said something and not whether what has been said is true or not. Veracity is an individual (organisational) conclusion that needs governance and virtual credentials. KERI and ACDC support veracity (concluding it's the "the truth") but doesn't solve it.
Compound description by @henkvancann from sources: 1, 2Truth
Truth is the property of being in accord with fact or reality. In everyday language, truth is typically ascribed to things that aim to represent reality
Source: Wikipedia.
spanning layer
ToIP
A specific layer within a protocol stack that consists of a single protocol explicitly designed to provide interoperability between the protocols layers above it and below it.
See also: hourglass model, trust spanning layer.
For more information, see: https://www.isi.edu/newarch/iDOCS/final.finalreport.pdf, National Academies of Sciences, Engineering, and Medicine. 1997. The Unpredictable Certainty: White Papers. Washington, DC: The National Academies Press. https://doi.org/10.17226/6062.
WebOfTrust
spanning layer
Definition
An all encompassing layer horizontal layer in a software architecture. Each trust layer only spans platform specific applications. It bifurcates the internet trust map into domain silos (e.g. twitter.com), because there is no spanning trust layer.

specification
ToIP
See: technical specification.
spoofing
digital.govt.nz
presenting a recorded image or other biometric data sample, or an artificially derived biometric characteristic, in order to impersonate an individual[Source: ISO/IEC TR 24714-1:2008]
spurn
WebOfTrust
ssi system
WebOfTrust
ssi system
Definition
The SSI Infrastructure consists of the technological components that are deployed all over the world for the purpose of providing, requesting and obtaining data for the purpose of negotiating and/or executing electronic transactions.Paraphrased by @henkvancann based on source eSSIF-lab
Purpose
The SSI Infrastructure supports the sustainable functionality of parties by providing IT services and facilities necessary for (electronic) transactions to be negotiated and executed.
Source eSSIF-labKERI and ACDC related
The team has put stress on the principle 'security first, confidentiality second and privacy third'. All systems and infrastructure KERI and ACDC has presented therefore constitute a rather small subset of all self-sovereign identity systems (SSI) available nowadays.
stale event
WebOfTrust
stale event
Definition
A stale key event is an outdated or irrelevant (key) event involving an expired encryption key that may compromise security.
stale key
WebOfTrust
stale key
Definition
A stale key is an outdated or expired encryption key that should no longer be used for securing data
Also see
stream
ToIP
In the context of digital communications, and in particular streaming media, a flow of data delivered in a continuous manner from a server to a client rather than in discrete messages.
streaming media
ToIP
Streaming media is multimedia for playback using an offline or online media player. Technically, the stream is delivered and consumed in a continuous manner from a client, with little or no intermediate storage in network elements. Streaming refers to the delivery method of content, rather than the content itself.
Source: Wikipedia.
strip parameter
sub shell
WebOfTrust
sub shell
Definition
A subshell is basically a new shell just to run a desired program. A subshell can access the global variables set by the 'parent shell' but not the local variables. Any changes made by a subshell to a global variable is not passed to the parent shell.
SourceParent - and child process
A child process in computing is a process created by another process (the parent process). This technique pertains to multitasking operating systems, and is sometimes called a subprocess or traditionally a subtask.
More on source Wikipedia
subject
digital.govt.nz
entity that is the focus of entity informationToIP
The entity described by one or more claims, particularly in the context of digital credentials.
Supporting definitions:
W3C VC: A thing about which claims are made.
eSSIF-Lab: the (single) entity to which a given set of coherent data relates/pertains. Examples of such sets include attributes, Claims/Assertions, files/dossiers, (verifiable) credentials, (partial) identities, employment contracts, etc.
subscription
ToIP
In the context of decentralized digital trust infrastructure, a subscription is an agreement between a first digital agent—the publisher—to automatically send a second digital agent—the subscriber—a message when a specific type of event happens in the wallet or vault managed by the first digital agent.
supermajority
WebOfTrust
supermajority
Definition
Sufficient majority that is labeled immune from certain kinds of attacks or faults.
supporting system
ToIP
A system that operates at ToIP Layer 1, the trust support layer of the ToIP stack. A supporting system is one of three types of systems defined in the ToIP Technology Architecture Specification.
See also: endpoint system, intermediary system.
synchronise ~ous
digital.govt.nz
to occur or recur or cause to occur or recur at the same time or in unison[Source: Dictionary]
system of record
ToIP
A system of record (SOR) or source system of record (SSoR) is a data management term for an information storage system (commonly implemented on a computer system running a database management system) that is the authoritative data source for a given data element or piece of information.
Source: Wikipedia
See also: authoritative source, trust registry, verifiable data registry.
tamper resistant
tcp endpoint
WebOfTrust
tcp endpoint
Definition
This is a service endpoint of the web transmission control protocol
More details
Because TCP packets do not include a session identifier, both endpoints identify the session using the client's address and port. Whenever a packet is received, the TCP implementation must perform a lookup on this table to find the destination process.
More on source Wikipedia
technical requirement
ToIP
A requirement for a hardware or software component or system. In the context of decentralized digital trust infrastructure, technical requirements are a subset of governance requirements. Technical requirements are often specified in a technical specification.
For more information, see: https://datatracker.ietf.org/doc/html/rfc2119
Note: In ToIP architecture, both technical requirements and governance requirements are expressed using the keywords defined in IETF RFC 2119.
technical specification
ToIP
A document that specifies, in a complete, precise, verifiable manner, the requirements, design, behavior, or other characteristics of a system or component and often the procedures for determining whether these provisions have been satisfied.
Source: NIST-CSRC
See also: governance framework, governance requirement, policy, rule.
technical trust
ToIP
A level of assurance in a trust relationship that can be achieved only via technical means such as hardware, software, network protocols, and cryptography. Cryptographic trust is a specialized type of technical trust.
Contrast with: human trust.
term
ToIP
A unit of text (i.e., a word or phrase) that is used in a particular context or scope to refer to a concept (or a relation between concepts, or a property of a concept).
Supporting definitions:
eSSIF-Lab: a word or phrase (i.e.: text) that is used in at least one scope/context to represent a specific concept.
Merriam Webster: a word or expression that has a precise meaning in some uses or is peculiar to a science, art, profession, or subject.
Note: A term MUST NOT be confused with the concept it refers to.
terminology
ToIP
Terminology is a group of specialized words and respective meanings in a particular field, and also the study of such terms and their use; the latter meaning is also known as terminology science. A term is a word, compound word, or multi-word expressions that in specific contexts is given specific meanings—these may deviate from the meanings the same words have in other contexts and in everyday language.[2] Terminology is a discipline that studies, among other things, the development of such terms and their interrelationships within a specialized domain. Terminology differs from lexicography, as it involves the study of concepts, conceptual systems and their labels (terms), whereas lexicography studies words and their meanings.
Source: Wikipedia.
terms community
ToIP
A group of parties who share the need for a common terminology.
See also: trust community.
terms wiki
ToIP
A wiki website used by a terms community to input, maintain, and publish its terminology. The ToIP Foundation Concepts and Terminology Working Group has established a simple template for GitHub-based terms wikis.
text binary concatenation composability
WebOfTrust
text binary concatenation composability
Definition
An encoding has composability when any set of self-framing concatenated primitives expressed in either the text domain or binary domain may be converted as a group to the other domain and back again without loss.
CESR related
CESR is fully text binary concatenation composable.
Example in analogy
Use Google Translate to translate a piece of text from English to Dutch. Subsequently, keep copy pasting the resulting “to:” text into the “from:” field. The message changes until it comes to a standstill where you can keep swapping the texts without them changing.


The conclusion is: Google Translate is not composable!
By contrast, CESR is composable. The analogy lies in the fact that we consider two languages. Suppose the English in the Google Translate example is readable, text based in CESR and Dutch is the binary form in CESR. Within these two CESR “languages”, text-based and binary, you can concatenate and swap freely as many times as you like — the data won’t change in between in their binary or text form no matter what content you express with them.
More explanation in source.
thing
ToIP
An entity that is neither a natural person nor an organization and thus cannot be a party. A thing may be a natural thing or a man-made thing.
third party
ToIP
A party that is not directly involved in the trust relationship between a first party and a second party, but provides supporting services to either or both of them.
tholder
WebOfTrust
three party model
ToIP
The issuer—holder—verifier model used by all types of physical credentials and digital credentials to enable transitive trust decisions.
Also known as: trust triangle.
threshold of accountable duplicity
WebOfTrust
threshold of accountable duplicity
Definition
The threshold of accountable duplicity (TOAD) is a threshold number
Mthat the controller declares to accept accountability for an event when any subsetMof theNwitnesses confirm that event. The thresholdMindicates the minimum number of confirming witnesses the controller deems sufficient given some numberFof potentially faulty witnesses, given thatM >= N - F. This enables a controller to provide itself with any degree of protection it deems necessary given this accountability.Note that what may be sufficient for a controller may not be sufficient for a validator. To clarify, let
MCdenote the threshold size of a sufficient agreement from the perspective of a controller and letMVdenote the threshold size of a sufficient agreement from the perspective of a validator. Typically,MV >= MC.TOAD in KEL
A controller declares TOAD in its key event log (KEL) during the key inception event and may edit it during subsequent key rotation events.
Purpose of TOAD
A highly available system needs some degree of fault tolerance. The purpose of the threshold of accountability is to enable fault tolerance of the key event service with respect to faulty behavior by either the controller or witnesses. The principal controller fault exhibits duplicitous behavior in the use of its keys. In this case, the threshold serves as the threshold of accountable duplicity. The threshold lets a validator know when it may hold the controller accountable for duplicitous behavior. Without a threshold, a validator may choose to hold a controller accountable upon any evidence of duplicity which may make the service fragile in the presence of any degree of such faulty behavior. The primary way that a validator may hold a controller accountable is to stop trusting any use of the associated identifier. This destroys any value in the identifier and does not allow the controller to recover from an exploit. Recall that the one purpose of rotation keys (pre-rotated unexposed) is to enable recovery from compromised interaction signing keys. A compromised interaction signing key may exhibit duplicitous behavior on the part of the controller. A threshold of accountable duplicity enables a validator to distinguish between potentially recoverable duplicity such as the use of a compromised signing key and non-recoverable duplicity such as the use of a compromised rotation key. This better protects both the validator and the controller and improves the robustness of the service.
threshold signature scheme
WebOfTrust
threshold signature scheme
Definition
or TSS; is a type of digital signature protocol used by Mutli-party Computation (MPC) wallets to authorize transactions or key state changes.
Source Cryptoapis
threshold structure security
WebOfTrust
threshold structure security
Definition
A threshold structure for security allows for weaker key management or execution environment infrastructure individually, but achieve greater overall security by multiplying the number of attack surfaces that an attacker must overcome to compromise a system.
In other words, with threshold structures, overall security may be greater than the security of any of the individual parts.For example, in MFA the combination of two factors, something you have and something you know, may be much more secure than either of the factors by themselves.
Threshold Structure Security vs. TEE Security
Threshold structures may be employed in a complementary manner to trusted execution environments (TEE) for security. The two types of security are complementary.
KERI related
This applies to KERI as well. The witnesses and watchers independently multiply the attack surfaces of the promulgation and the confirmation networks such that each witness or watcher respectively may be relatively insecure but the system as a whole may be highly secure.
Considerations
Numerous papers discuss how secure a distributed consensus pool may be. But when comparing apples (key management and trusted execution environment (TEE) approach to security) to oranges (distributed consensus approach to security) its hard to say that the security of a distributed consensus algorithm is necessarily less secure than the key management infra-structure root-of-trust of any of its nodes. Although as a general rule, in an apples to apples comparison, more complex is less secure.
Source: Universal Identifier Theory by Samuel Smith
timestamp
ToIP
A token or packet of information that is used to provide assurance of timeliness; the timestamp contains timestamped data, including a time, and a signature generated by a trusted timestamp authority (TTA).
Source: NIST-CSRC.
Supporting definitions:
TechTarget: A timestamp is the current time of an event that a computer records. Through mechanisms, such as the Network Time Protocol, a computer maintains accurate current time, calibrated to minute fractions of a second. Such precision makes it possible for networked computers and applications to communicate effectively.
top level section
WebOfTrust
top level section
Definition
The fields of an ACDC in compact variant. The value of a top level section field is either the SAD or the SAID of the SAD of the associated section.An Issuer commitment via a signature to any variant of ACDC (compact, full, etc) makes a cryptographic commitment to the top-level section fields shared by all variants of that ACDC.
Paraphrased by @henkvancann based on source.Example

trans contextual value
WebOfTrust
trans contextual value
Definition
Value that is transferrable between contexts
Related to KERI
How do we recapture the value in our data? 1- Leverage cooperative network effects 2- Retake control of our data.
Source Samuel Smith1. Leverage cooperative network effects
How to remove primary barriers to cooperation? Different value contexts implies 'not directly competitive'. So we need to find value that is transferrable between contexts. Therefore: Use trans-contextual value creation and capture to fuel cooperative network effects.
2. Retake control of our data
KERI assists in this.
transaction
digital.govt.nz
one or more exchanges between an individual and an organisation in a process related to a specific outcomeAdditional notes:Note 1: A single transaction may constitute a step in a segmented process or result in the completion of an end to end process.Note 2: A service is usually made up of several transactions.ToIP
A discrete event between a user and a system that supports a business or programmatic purpose. A digital system may have multiple categories or types of transactions, which may require separate analysis within the overall digital identity risk assessment.
Source: NIST-CSRC.
See also: connection.
Supporting definitions:
eSSIF-Lab: the exchange of goods, services, funds, or data between some parties (called participants of the transaction).
transaction event log
WebOfTrust
transaction event log
Definition
The set of transactions that determine registry state form a log called a Transaction Event Log (TEL). The TEL provides a cryptographic proof of registry state by reference to the corresponding controlling KEL. Any validator may therefore cryptographically verify the authoritative state of the registry.
Put differently
An externally anchored transactions log via cryptographic commitments in a KEL.

transaction event log (TEL)
ToIP (DID:Webs)
A verifiable append-only log of transaction data that are cryptographically anchored to a KEL. The transaction events of a TEL may be used to establish the issuance or revocation state of ACDCs. See WebOfTrust glossary for more detail.
transfer off ledger
WebOfTrust
transfer off ledger
Definition
The act of transferring control authority over an identifier from a ledger (or blockchain) to the native verifiable KERI data structure Key Event Log.
Transition option
If you want to transition to using KERI, you could do that by anchoring your KERI identifiers in, for example, your Indy ledger. The neat thing is, you could then transfer the identifier off the ledger and then have non-ledger based portable identifiers.
One at a time
Although it's portable, you can be anchored to any one ledger at a time, or you could move it to an identifier (witness, backer, watcher, etc) can only be represented different ledger, or you could move to using just witnesses, all with the same identifier by justdoing rotation events and changing your anchor, your backers here.
So an identifier cannot be anchored, let's say to multiple Indies or Ethereum. You could be only anchored in one at a time.Move identifiers across networks
You can move identifiers across networks with KERI, but it's not what it has been designed for.
transferable
WebOfTrust
transferable
Definition
Capable of being transferred or conveyed from one place or person to another. Place can be its and bits. The adjective transferable also means 'Negotiable', as a note, bill of exchange, or other evidence of property, that may be conveyed from one person to another by indorsement or other writing; capable of being transferred with no loss of value. As opposed to non-transferable.
SourceKERI related
Focus is on the digital space and concerning the loss-less transfer of control over identifiers, private keys, etc.
transferable identifier
WebOfTrust
transferable identifier
Definition
Control over the identifier can be transferred by rotating keys.
A synonym is 'persistent identifier'.| TBW prio 1 |
KERI related
The KERI design approach is to build composable primitives instead of custom functionality that is so typical of other DKMI approaches:
- transferable identifiers
- non-transferable identifiers
- delegated identifiers
transitive trust decision
ToIP
A trust decision made by a first party about a second party or another entity based on information about the second party or the other entity that is obtained from one or more third parties.
Note: A primary purpose of digital credentials, chained credentials, and trust registries is to facilitate transitive trust decisions.
For more information, see: Design Principles for the ToIP Stack.
transmission control protocol
WebOfTrust
transmission control protocol
Definition
One of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP).
More on source Wikipedia.
tribal knowledge
trust
ToIP
A belief that an entity will behave in a predictable manner in specified circumstances. The entity may be a person, process, object or any combination of such components. The entity can be of any size from a single hardware component or software module, to a piece of equipment identified by make and model, to a site or location, to an organization, to a nation-state. Trust, while inherently a subjective determination, can be based on objective evidence and subjective elements. The objective grounds for trust can include for example, the results of information technology product testing and evaluation. Subjective belief, level of comfort, and experience may supplement (or even replace) objective evidence, or substitute for such evidence when it is unavailable. Trust is usually relative to a specific circumstance or situation (e.g., the amount of money involved in a transaction, the sensitivity or criticality of information, or whether safety is an issue with human lives at stake). Trust is generally not transitive (e.g., you trust a friend but not necessarily a friend of a friend). Finally, trust is generally earned, based on experience or measurement.
Source: NIST Special Publication 800-39 p.24
See also: transitive trust decision.
For more information, see: Design Principles for the ToIP Stack.
trust anchor
ToIP
See: trust root.
Note: The term “trust anchor” is most commonly used in cryptography and public key infrastructure.
trust application layer
ToIP
In the context of the ToIP stack, the trust application layer is ToIP Layer 4. Applications running at this layer call trust task protocols at ToIP Layer 3.
trust assurance
ToIP
A process that provides a level of assurance sufficient to make a particular trust decision.
trust basis
ToIP
The properties of a verifiable identifier or a ToIP system that enable a party to appraise it to determine a trust limit.
See also: appraisability.
trust boundary
ToIP
The border of a trust domain.
trust chain
ToIP
A set of cryptographically verifiable links between digital credentials or other data containers that enable transitive trust decisions.
See also: chained credentials, trust graph.
For more information, see: Design Principles for the ToIP Stack.
trust community
ToIP
A set of parties who collaborate to achieve a mutual set of trust objectives.
See also: digital trust ecosystem, ToIP trust community.
Note: A trust community may be large or small, formal or informal. In a formal trust community, the set of policies and rules governing behavior of members are usually published in a governance framework or trust framework. In an informal trust community, the policies or rules governing the behavior of members may be tribal knowledge.
trust context
ToIP
The context in which a specific party makes a specific trust decision. Many different factors may be involved in establishing a trust context, such as: the relevant interaction or transaction; the presence or absence of existing trust relationships; the applicability of one or more governance frameworks; and the location, time, network, and/or devices involved. A trust context may be implicit or explicit; if explicit, it may be identified using an identifier. A ToIP governance framework an example of an explicit trust context identified by a ToIP identifier.
See also: trust domain.
For more information, see: Design Principles for the ToIP Stack.
trust decision
ToIP
A decision that a party needs to make about whether to engage in a specific interaction or transaction with another entity that involves real or perceived risks.
See also: transitive trust decision.
For more information, see: Design Principles for the ToIP Stack.
trust domain
ToIP
A security domain defined by a computer hardware or software architecture, a security policy, or a trust community, typically via a trust framework or governance framework.
See also: trust context, digital trust ecosystem.
WebOfTrust
trust domain
Definition
A trust domain is the ecosystem of interactions that rely on a trust basis. A trust basis binds controllers, identifiers, and key-pairs. For example the Facebook ecosystem of social interactions is a trust domain that relies on Facebook’s identity system of usernames and passwords as its trust basis.
(Source whitepaper)Broader definition
A trust domain is a domain that the system trusts to authenticate users. In other words, if a user or application is authenticated by a trusted domain, this authentication is accepted by all domains that trust the authenticating domain.
Domain name
A more technical meaning of 'domain' is on the internet: domain name.
trust ecosystem
ToIP
trust establishment
ToIP
The process two or more parties go through to establish a trust relationship. In the context of decentralized digital trust infrastructure, trust establishment takes place at two levels. At the technical trust level, it includes some form of key establishment. At the human trust level, it may be accomplished via an out-of-band introduction, the exchange of digital credentials, queries to one or more trust registries, or evaluation of some combination of human-readable and machine-readable governance frameworks.
trust framework
ToIP
A term (most frequently used in the digital identity industry) to describe a governance framework for a digital identity system, especially a federation.
trust graph
ToIP
A data structure describing the trust relationship between two or more entities. A simple trust graph may be expressed as a trust list. More complex trust graphs can be recorded or registered in and queried from a trust registry. Trust graphs can also be expressed via trust chains and chained credentials. Trust graphs can enable verifiers to make transitive trust decisions.
See also: authorization graph, governance graph, reputation graph.
trust limit
ToIP
A limit to the degree a party is willing to trust an entity in a specific trust relationship within a specific trust context.
For more information, see: Design Principles for the ToIP Stack.
trust list
ToIP
A one-dimensional trust graph in which an authoritative source publishes a list of entities that are trusted in a specific trust context. A trust list can be considered a simplified form of a trust registry.
trust network
ToIP
A network of parties who are connected via trust relationships conforming to requirements defined in a legal regulation, trust framework or governance framework. A trust network is more formal than a digital trust ecosystem; the latter may connect parties more loosely via transitive trust relationships and/or across multiple trust networks.
See also: ToIP trust network.
trust objective
ToIP
An objective shared by the parties in a trust community to establish and maintain trust relationships.
trust registry
ToIP
A registry that serves as an authoritative source for trust graphs or other governed information describing one or more trust communities. A trust registry is typically authorized by a governance framework.
See also: trust list, verifiable data registry.
trust registry protocol
ToIP
trust relationship
ToIP
A relationship between a party and an entity in which the party has decided to trust the entity in one or more trust contexts up to a trust limit.
Supporting definitions:
NIST: An agreed upon relationship between two or more system elements that is governed by criteria for secure interaction, behavior, and outcomes relative to the protection of assets.
For more information, see: Design Principles for the ToIP Stack.
trust root
ToIP
The authoritative source that serves as the origin of a trust chain.
For more information, see: Design Principles for the ToIP Stack.
trust service provider
ToIP
In the context of specific digital trust ecosystems, such as the European Union’s eIDAS regulations, a trust service provider (TSP) is a legal entity that provides specific trust support services as required by legal regulations, trust frameworks, or governance frameworks. In the larger context of ToIP infrastructure, a TSP is a provider of services based on the ToIP stack. Most generally, a TSP is to the trust layer for the Internet what an Internet service provider (ISP) is to the Internet layer.
Also known as: TSP.
Supporting definitions:
Wikipedia: A trust service provider (TSP) is a person or legal entity providing and preserving digital certificates to create and validate electronic signatures and to authenticate their signatories as well as websites in general. Trust service providers are qualified certificate authorities required in the European Union and in Switzerland in the context of regulated electronic signing procedures.
trust spanning layer
ToIP
A spanning layer designed to span between different digital trust domains. In the ToIP stack, ToIP Layer 2 is the trust spanning layer.
See also: ToIP layer.
Mental model: hourglass model, see ToIP Technology Architecture Specification
For more information, see: Section 7.3 of the ToIP Technology Architecture Specification.
trust spanning protocol
ToIP
WebOfTrust
trust spanning protocol
Definition
Protocol using VIDs that signs every single message on the internet and makes them verifiable.
trust support
ToIP
A system, protocol, or other infrastructure whose function is to facilitate the establishment and maintenance of trust relationships at higher protocol layers. In the ToIP stack, the trust support layer is Layer 1.
trust support layer
ToIP
In the context of the ToIP stack, the trust support layer is ToIP Layer 1. It supports the operations of the ToIP Trust Spanning Protocol at ToIP Layer 2.
trust task
ToIP
A specific task that involves establishing, verifying, or maintaining trust relationships or exchanging verifiable messages or verifiable data that can be performed on behalf of a trust application by a trust task protocol at Layer 3 of the ToIP stack.
For more information, see Section 7.4 of the ToIP Technology Architecture Specification.
trust task layer
ToIP
In the context of the ToIP stack, the trust task layer is ToIP Layer 3. It supports trust applications operating at ToIP Layer 4.
trust task protocol
ToIP
A ToIP Layer 3 protocol that implements a specific trust task on behalf of a ToIP Layer 4 trust application.
trust triangle
ToIP
See: three-party model.
trusted execution environment
ToIP
A trusted execution environment (TEE) is a secure area of a main processor. It helps code and data loaded inside it to be protected with respect to confidentiality and integrity. Data integrity prevents unauthorized entities from outside the TEE from altering data, while code integrity prevents code in the TEE from being replaced or modified by unauthorized entities, which may also be the computer owner itself as in certain DRM schemes.
Source: Wikipedia.
Also known as: TEE.
See also: Secure Enclave.
WebOfTrust
trusted execution environment
Definition
Protected hardware/software/firmware security system. The controller may protect its key generation, key storage, and event signing infrastructure by running it inside a trusted execution environment (TEE).
Examples
SGX, TrustZone, an HSM, a TPM, or other similarly protected hardware/software/firmware environment
trusted platform module
WebOfTrust
trusted platform module
Definition
A device that enhances the security and privacy (of identity systems) by providing hardware-based cryptographic functions.
Functions
A TPM can generate, store, and protect encryption keys and authentication credentials that are used to verify the identity of a user or a device.
A TPM can also measure and attest the integrity of the software and firmware that are running on a system, to ensure that they have not been tampered with or compromised.Form
A TPM can be implemented as a physical chip, a firmware module, or a virtual device.
Source: Bing chat sept 2023
trusted role
ToIP
A role that performs restricted activities for an organization after meeting competence, security and background verification requirements for that role.
trusted third party
ToIP
In cryptography, a trusted third party (TTP) is an entity which facilitates interactions between two parties who both trust the third party; the third party reviews all critical transaction communications between the parties, based on the ease of creating fraudulent digital content. In TTP models, the relying parties use this trust to secure their own interactions. TTPs are common in any number of commercial transactions and in cryptographic digital transactions as well as cryptographic protocols, for example, a certificate authority (CA) would issue a digital certificate to one of the two parties in the next example. The CA then becomes the TTP to that certificate's issuance. Likewise transactions that need a third party recordation would also need a third-party repository service of some kind.
Source: Wikipedia.
Also known as: TTP.
Supporting definitions:
NIST-CSRC: A third party, such as a CA, that is trusted by its clients to perform certain services. (By contrast, the two participants in a key-establishment transaction are considered to be the first and second parties.)
trusted timestamp authority
trustworthiness
ToIP
An attribute of a person or organization that provides confidence to others of the qualifications, capabilities, and reliability of that entity to perform specific tasks and fulfill assigned responsibilities. Trustworthiness is also a characteristic of information technology products and systems. The attribute of trustworthiness, whether applied to people, processes, or technologies, can be measured, at least in relative terms if not quantitatively. The determination of trustworthiness plays a key role in establishing trust relationships among persons and organizations. The trust relationships are key factors in risk decisions made by senior leaders/executives.
Source: NIST Special Publication 800-39 p.24
trustworthy
ToIP
A property of an entity that has the attribute of trustworthiness.
trust application
ToIP
An application that runs at ToIP Layer 4 in order to perform trust tasks or engage in other verifiable messaging using the ToIP stack.
ts node
WebOfTrust
ts node
Definition
npm package that lets you run typescript from a shell
unicast
ToIP
In computer networking, unicast is a one-to-one transmission from one point in the network to another point; that is, one sender and one receiver, each identified by a network address (a unicast address). Unicast is in contrast to multicast and broadcast which are one-to-many transmissions. Internet Protocol unicast delivery methods such as Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are typically used.
Source: Wikipedia.
See also: anycast.
unicast address
ToIP
A network address used for a unicast.
uniform resource locator
WebOfTrust
uniform resource locator
Definition
A Uniform Resource Locator (URL), colloquially termed a web address, is a reference to a web resource that specifies its location on a computer network and a mechanism for retrieving it.
Broader context
A URL is a specific type of Uniform Resource Identifier (URI),although many people use the two terms interchangeably. URLs occur most commonly to reference web pages (HTTP) but are also used for file transfer (FTP), email (mailto), database access (JDBC), and many other applications.
More on source Wikipedia
univalent
WebOfTrust
univalent
Definition
In identifier systems, univalent means having a unique and non-ambiguous identifier for each entity or resource. This means that there is a one-to-one correspondence between the identifiers and the entities, and that no two different entities share the same identifier. Source: Bing chat, Sept 2023
Universal Identity Theory specific
(Paraphrased from source Universal Identifier Theory by Samuel Smith)In key management key pairs (public, private) are created in the key-pair generation and storage infrastructure and then may be moved to the key event generation and signing infrastructure in order to sign events. To protect both the key generation and storage and the event signing infrastructures. . Consequently, a given protection mechanism may co-locate both infrastructures. This means facilities are shared. This combined infrastructure is refered to as a univalent key management infrastructure.

A more secure albeit less convenient or performant univalent key management infrastructure may use special computing devices or components to store private keys and/or create signatures.
Also see
unsolicited issuance
WebOfTrust
unsolicited issuance
Definition
Issuance of a Legal Entity vLEI Credential upon notice by a QAR to the AVR(s) of the Legal Entity that a Legal Entity vLEI Credential has been solicited on the Legal Entity’s behalf.
Source: Draft vLEI Ecosystem Governance Framework Glossary.Related
user agent
ToIP
A software agent that is used directly by the end-user as the principal. Browsers, email clients, and digital wallets are all examples of user agents.
Supporting definitions:
Wikipedia: On the Web, a user agent is a software agent capable of and responsible for retrieving and facilitating end user interaction with Web content.[1] This includes all common web browsers, such as Google Chrome, Mozilla Firefox, and Safari, some email clients, standalone download managers like youtube-dl, other command-line utilities like cURL, and arguably headless services that power part of a larger application, such as a web crawler.
The user agent plays the role of the client in a client–server system. The HTTP User-Agent header is intended to clearly identify the agent to the server. However, this header can be omitted or spoofed, so some websites use other agent detection methods.
user interface
WebOfTrust
user interface
Definition
A user interface (UI or U/I) is the space where interactions between humans and machines occur.
More on Wikipedia
The Reactable, an example of a tangible user interfaceIn the industrial design field of human–computer interaction, a user interface (UI) is the space where interactions between humans and machines occur. The goal of this interaction is to allow effective operation and control of the machine from the human end, while the machine simultaneously feeds back information that aids the operators' decision-making process.
Source page
utility governance framework
ToIP
A governance framework for a digital trust utility. A utility governance framework may be a component of or referenced by an ecosystem governance framework or a credential governance framework.
vLEI
WebOfTrust
validate
WebOfTrust
validate
See
ESSIF-lab definition of validate. Although this definition is very general, in the KERI/ACDC vocabulary 'validate' currently has extra diverse meanings extending the one of eSSIF-lab, such as
- evaluate
- verify
In contrast, validator and verifier have been clearly outlined in the WebofTrust vocabulary.
validation
ToIP
An action an agent (of a principal) performs to determine whether a digital object or set of data meets the requirements of a specific party.
See also: verification.
Supporting definitions:
eSSIF-Lab: The act, by or on behalf of a party, of determining whether or not that data is valid to be used for some specific purpose(s) of that party.
NIST: Confirmation, through the provision of objective evidence, that the requirements for a specific intended use or application have been fulfilled.
validator
WebOfTrust
validator
Definition
determines current authoritative key set for identifier from at least one key event (receipt) log. Types:
- Validator of any verifiable data structure
- Validator as a node in distributed consensus or participant
Validator and verifier are close to synonyms for our purposes.
A
validatorin KERI and ACDC is anybody that wants to establish control-authority over an identifier, created by the controller of the identifier. Validators verify the log, they apply duplicity detection or they leverage somebody else's duplicity detection or apply any other logic so they can say "Yes, these are events I can trust".Example
During validation of virtual credentials for example, a verifier checks to see if a verifiable credential (VC) has been signed by the controller of this VC using the applicable verification method.
To be Sam-Smith precise in KERI
Any entity or agent that evaluates whether or not a given signed statement as attributed to an identifier is valid at the time of its issuance. A valid statement MUST be verifiable, that is, has a verifiable signature from the current controlling keypair(s) at the time of its issuance. Therefore a Validator must first act as a Verifier in order to establish the root authoritative set of keys. Once verified, the Validator may apply other criteria or constraints to the statement in order to determine its validity for a given use case. When that statement is part of a verifiable data structure then the cryptographic verification includes verifying digests and any other structural commitments or constraints. To elaborate, with respect to an AID, for example, a Validator first evaluates one or more KELs in order to determine if it can rely on (trust) the key state (control authority) provided by any given KEL. A necessary but insufficient condition for a valid KEL is it is verifiable i.e. is internally inconsistent with respect to compliance with the KERI protocol. An invalid KEL from the perspective of a Validator may be either unverifiable or may be verifiable but duplicitous with respect to some other verifiable version of that KEL. Detected duplicity by a given validator means that the validator has seen more than one verifiable version of a KEL for a given AID. Reconciliable duplicity means that one and only one version of a KEL as seen by a Validator is accepted as the authoritative version for that validator. Irreconcilable duplicity means that none of the versions of a KEL as seen by a validator are accepted as the authoritative one for that validator. The conditions for reconcilable duplicity are described later.
Source Sam Smith
vault
ToIP
See: digital vault.
vcp
WebOfTrust
vcp
Definition
vcp = vdr incept, verifiable data registry inception
vdr
WebOfTrust
veracity
WebOfTrust
veracity
Definition
The quality of being true; contrast authenticity. When a newspaper publishes a story about an event, every faithful reproduction of that story may be authentic — but that does not mean the story was true (has veracity).
verfer
verifiability (of a digital object, claim, or assertion)
ToIP
The property of a digital object, assertion, claim, or communication, being verifiable.
See also: appraisability.
verifiable
ToIP
In the context of digital communications infrastructure, the ability to determine the authenticity of a communication (e.g., sender, contents, claims, metadata, provenance), or the underlying sociotechnical infrastructure (e.g., governance, roles, policies, authorizations, certifications).
See also: appraisability (of a communications end-point); digital signature.
WebOfTrust
verifiable
Definition
able to cryptographically verify a certain data structure on its consistency and its authenticity
KERI related
A KEL is verifiable means all content in a KEL including the digests and the signatures on that content is verifiably compliant with respect to the KERI protocol. In other words, the KEL is internally consistent and has integrity vis-a-vis its backward and forward chaining digests and authenticity vis-a-vis its non-repudiable signatures. As a verifiable data structure, the KEL satisfies the KERI protocol-defined rules for that verifiability. This includes the cryptographic verification of any digests or signatures on the contents so digested or signed.
Source Sam Smith
verifiable credential
ToIP
A standard data model and representation format for cryptographically-verifiable digital credentials as defined by the W3C Verifiable Credentials Data Model specification.
Source: W3C DID
See also: digital credential.
Mental model: W3C Verifiable Credentials Data Model Roles & Information Flows
Supporting definitions:
W3C VC: A verifiable credential is a tamper-evident credential that has authorship that can be cryptographically verified. Verifiable credentials can be used to build verifiable presentations, which can also be cryptographically verified. The claims in a credential can be about different subjects.
W3C (DID)
A standard data model and representation format for cryptographically-verifiabledigital credentials as defined by the W3C Verifiable Credentials specification[VC-DATA-MODEL].WebOfTrust
verifiable credential
Definition
Verifiable credentials (VCs) are an open standard for digital credentials. They can represent information found in physical credentials, such as a passport or license, as well as new things that have no physical equivalent, such as ownership of a bank account.
The ToIP definition
More on source Wikipedia
W3C DID standardization
Importantly, there are VC specification that provide a mechanism to express these sorts of credentials on the Web in a way that is cryptographically secure, privacy respecting, and machine-verifiable. More
verifiable data
ToIP
Any digital data or object that is digitally signed in such a manner that it can be cryptographically verified.
Note: In the context of ToIP architecture, verifiable data is signed with the cryptographic keys associated with the ToIP identifier of the data controller.
verifiable data registry
ToIP
A registry that facilitates the creation, verification, updating, and/or deactivation of decentralized identifiers and DID documents. A verifiable data registry may also be used for other cryptographically-verifiable data structures such as verifiable credentials.
Source: W3C DID
Mental model: W3C Verifiable Credentials Data Model Roles & Information Flows
See also: authoritative source, trust registry, system of record.
For more information, see: the W3C Verifiable Credentials specification [VC-DATA-MODEL].
Note: There is an earlier definition in the W3C VC 1.1. glossary that is not as mature (it is not clear about the use of cryptographically verifiable data structures). We do not recommend that definition.
W3C (DID)
A system that facilitates the creation, verification, updating, and/ordeactivation of decentralized identifiers and DID documents. Averifiable data registry might also be used for othercryptographically-verifiable data structures such as verifiablecredentials. For more information, see the W3C Verifiable Credentialsspecification [VC-DATA-MODEL].WebOfTrust
verifiable data registry
Definition
a Verifiable Data Structure that has actual content.
It contains either a log of signed statements or a cryptographic commitment (digest) to those statements (via a Merkle tree or hash chained data structure).
verifiable data structure
WebOfTrust
verifiable data structure
Definition
A verifiable data structure is a data structure that incorporates cryptographic techniques to ensure the integrity and authenticity of its contents. It allows users to verify the correctness of the data stored within the structure without relying on a trusted third party.Source ChatGPT
Related to KERI
Provides proof of key state for its identifier. In KERI it is the Key Event Log (
KEL). Key management is embedded in KELs, including recovery from key compromise.Sources Definition ChatGPT
- Boneh, D., & Shacham, H. (2018). Verifiable data structures for outsourced data. Foundations and Trends® in Privacy and Security, 2(1-2), 1-116.
- Bamert, T., Decker, C., Elsen, L., Wattenhofer, R., & Welten, S. (2017). Have a snack, pay with bitcoins. Distributed Computing, 30(1), 69-93.
- Ateniese, G., Kamara, S., & Katz, J. (2014). Provable data possession at untrusted stores. ACM Transactions on Information and System Security (TISSEC), 7(2), 222-238.
- Andrychowicz, M., Dziembowski, S., Malinowski, D., & Mazurek, Ł. (2014). Secure multiparty computations on Bitcoin. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security (pp. 628-639).
- Pomarole, M., Zhang, Y., Rosulek, M., & Katz, J. (2014). Secure cloud backup and inference control. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security (pp. 812-823).
verifiable identifier
ToIP
An identifier over which the controller can provide cryptographic proof of control.
See also: decentralized identifier, autonomous identifier.
WebOfTrust
verifiable identifier
Definition
Cryptographically verifiable authentic decentralized identifier (verfiable DID)
verifiable legal entity identifier
WebOfTrust
verifiable legal entity identifier
Definition
vLEIs are digital verifiable credentials issued by (delegates) of GLEIF to prove that information about a legel entity is verifiably authentic.
| TBW | prio1 : check definition |
Explanation
The v in vLEI stands for “verifiable”, but what does that mean? The term verifiable in this case comes from the term “Verifiable Credential”. A verifiable credential is just a collection of information with a mechanism that allows a computer to verify that the information has not been modified and that the information was originally stated to be correct by some third party (maybe a bank, or the driving license authority). Often (almost always really) the information will include a link to the entity the information is about.
More information
Here at Rapidlei.
verifiable message
ToIP
A message communicated as verifiable data.
See also: ToIP messages
verifiable timestamp
W3C (DID)
A verifiable timestamp enables a third-party to verify that a data objectexisted at a specific moment in time and that it has not been modified orcorrupted since that moment in time.If the data integrity could reasonably havebeen modified or corrupted since that moment in time, the timestamp is notverifiable.
verification
ToIP
An action an agent (of a principal) performs to determine the authenticity of a claim or other digital object using a cryptographic key.
See also: validation.
Mental model: W3C Verifiable Credentials Data Model Roles & Information Flows
Supporting definitions:
eSSIF-Lab: The act, by or on behalf of a party, of determining whether that data is authentic (i.e. originates from the party that authored it), timely (i.e. has not expired), and conforms to other specifications that apply to its structure.
WebOfTrust
verification
Definition
An action an agent (of a principal) performs to determine the authenticity of a claim or other digital object using a cryptographic key.
Source: ToIP glossary, Jan 2024.In more technical words: the capability to (cryptographically) verify data received from peers (check structure, signatures, dates)
See also
verification method
W3C (DID)
A set of parameters that can be used together with a process to independentlyverify a proof. For example, a cryptographic public key can be used as averification method with respect to a digital signature; in such usage, itverifies that the signer possessed the associated cryptographic private key. "Verification" and "proof" in this definition are intended to apply broadly. Forexample, a cryptographic public key might be used during Diffie-Hellman keyexchange to negotiate a shared symmetric key for encryption. This guarantees theintegrity of the key agreement process. It is thus another type of verificationmethod, even though descriptions of the process might not use the words"verification" or "proof."
verification relationship
W3C (DID)
An expression of the relationship between the DID subject and averification method. An example of a verification relationship is5.3.1 Authentication.
verified integrity
WebOfTrust
verified integrity
Definition
A mechanism that can unambiguously assess whether the information is/continues to be whole, sound and unimpaired
KERI suite related
- In KERI's secure attribution focus integrity is verified by internal consistency of KE(R)L and TEL plus duplicity detection.
- In ACDC the self addressing identifier (SAID) takes of verified integrity at all times by design
- The streaming protocol CESR has verifiable integrity due to it's code tables and round-robin composability.
See also
verifier
Nist
An entity that verifies the claimants identity by verifying the claimants possession and control of a token using an authentication protocol. To do this, the Verifier may also need to validate credentials that link the token and identity and check their status.ToIP (DID:Webs)
An entity or component that cryptographically verifies the signature(s) on an event message. See WebOfTrust glossary for more detail.WebOfTrust
verifier
Definition
the entity that (cryptographically) verifies data received from peers (check structure, signatures, dates). More narrowly defined for the KERI suite: cryptographically verifies signature(s) on an event message.
Notice the subtile difference between validator and verifier.
KERI related
Any entity or agent that cryptographically verifies the signature(s) and/or digests on an event message. In order to verify a signature, a verifier must first determine which set of keys are or were the controlling set for an identifier when an event was issued. In other words, a verifier must first establish control authority for an identifier. For identifiers that are declared as non-transferable at inception, this control establishment merely requires a copy of the inception event for the identifier. For identifiers that are declared transferable at inception, this control establishment requires a complete copy of the sequence of establishment events (inception and all rotations) for the identifier up to the time at which the statement was issued.
Source Sam SmithESSIF-lab definitions
- verify definition is in sync with the definition in the KERI/ACDC vocabulary
- verifier definition is in sync with the definition in the KERI/ACDC vocabulary
- validate definition is very general, however in the KERI/ACDC vocabulary 'validate' currently has diverse meanings including this one
- validator definition is a generalisation of the much more specific definition in the KERI/ACDC vocabulary
verifier (of a claim or credential)
ToIP
A role an agent performs to perform verification of one or more proofs of the claims in a digital credential.
See also: relying party; issuer, holder.
Mental model: W3C Verifiable Credentials Data Model Roles & Information Flows
Supporting definitions:
W3C VC: A role an entity performs by receiving one or more verifiable credentials, optionally inside a verifiable presentation for processing. Other specifications might refer to this concept as a relying party.
eSSIF-Lab: a component that implements the capability to request peer agents to present (provide) data from credentials (of a specified kind, issued by specified parties), and to verify such responses (check structure, signatures, dates), according to its principal's verifier policy.
NIST: The entity that verifies the authenticity of a digital signature using the public key.
verify
WebOfTrust
verify
Definition
The act, by or on behalf of a party, of determining whether that data is authentic (i.e. originates from the party that authored it), timely (i.e. has not expired), and conforms to other specifications that apply to its structure.
Source eSSIF-lab in eSSIF-lab glossarySee also
verify signature
WebOfTrust
verify signature
Definition
Applying an algorithm that, given the message, public key and signature, either accepts or rejects the message's claim to authenticity.
Related ESSIF-lab definitions
- verify definition is in sync with the definition in the KERI/ACDC vocabulary
- verifier definition is in sync with the definition in the KERI/ACDC vocabulary
- validate definition is very general, however in the KERI/ACDC vocabulary 'validate' currently has diverse meanings including this one
- validator definition is a generalisation of the much more specific definition in the KERI/ACDC vocabulary
version
WebOfTrust
version
Definiton
In software engineering, version control (also known as revision control, source control, or source code management) is a class of systems responsible for managing changes to computer programs, documents, large web sites, or other collections of information.
SourceKERI related
More than one version of a KEL for an AID exists when for any two instances of a KEL at least one event is unique between the two instances.
Source Sam Smith
version code
WebOfTrust
version code
Definition
tells you which set of tables to load, it tells the table state. It's a unique code. what version of the table is going to load.
Compare
version string
WebOfTrust
version string
Definition
The Version String in JSON, CBOR and MGPK is a workaround to make those self-framing.
Compare
virtual credential transaction event log
WebOfTrust
virtual credential transaction event log
Definition
will track the issued or revoked state of each virtual credential (VC) and will contain a reference to its corresponding management transaction event log (management TEL).
virtual vault
ToIP
A digital vault enclosed inside another digital vault by virtue of having its own verifiable identifier (VID) and its own set of encryption keys that are separate from those used to unlock the enclosing vault.
vlei credential
WebOfTrust
vlei credential
Definition
Credential concerning a verifiable Legal Entity Identifier, residing in the GLEIS and compliant with one or more of the GLEIF Governance Frameworks
vlei ecosystem governance framework
WebOfTrust
vlei ecosystem governance framework
Definition
The Verifiable LEI (vLEI) Ecosystem Governance Framework Information Trust Policies. It's a document that defines the information security, privacy, availability, confidentiality and processing integrity policies that apply to all vLEI Ecosystem Members.
Paraphrased by @henkvancann from source Draft vLEI Ecosystem Governance Framework Glossary.
vlei role credential
WebOfTrust
vrt
WebOfTrust
vrt
Definition
vrt = vdr rotate, verifiable data registry rotation
wallet
ToIP
See: digital wallet.
WebOfTrust
wallet
Definition
A crypto wallet is a device, physical medium, program or a service which stores the public and/or private keys for cryptocurrency transactions and digital identifiers.
Paraphrased by @henkvancann from source WikipediaKERI and ACDC context
A wallet is a collection of data stores; made up of a keystore, local and remote key event log database and credential database. So it is a superset of a keystore.
Source: Philip Feairheller.In a broader context a wallet can be seen as software and sometimes hardware that serves as a keystore and functionality. Keys can be private keys and public keys, and the wallet could contain hashes and pointers. Functionality can be signing, invoices (receive), send, virtual credentials, delegation, etc. This functionality is the
agencypart of a wallet.
More about digital ID Wallets
More about cryto Wallets.Functions
In addition to this basic function of storing the keys, it's also used to storing verifiable credentials (VCs). A cryptocurrency wallet more often also offers the functionality of encrypting and/or signing information.\
Signing can for example result in executing a smart contract, a cryptocurrency transaction, identification or legally signing a 'document'.
More on source WikipediaKERI and ACDC related
A 'wallet' in KERI would typically refer to the basic function of storing the keys, a wallet in ACDC is more focussed on storing verifiable credentials (VCs).\
KERI explicitly distinguishes keystore and wallet; the latter being a superset of the former. Keep is KERI's and ACDC's user interface with Keripy agent API as a back end.
wallet engine
ToIP
The set of software components that form the core of a digital wallet, but which by themselves are not sufficient to deliver a fully functional wallet for use by a digital agent (of a principal). A wallet engine is to a digital wallet what a browser engine is to a web browser.
For more information: The charter of the OpenWallet Foundation is to produce an open source digital wallet engine.
watcher
ToIP (DID:Webs)
An entity that keeps a copy of a KERL of an AID to detect duplicity of key events, as defined by the KERI whitepaper. See WebOfTrust glossary for more detail.WebOfTrust
watcher
Definition
KERI alternative to total global ordering and consensus protocols is a mechanism called duplicity detection. In the verification and validation watchers are all that matter; they guarantee that logs are immutable by one very simple rule: "first seen wins".
KERI operational
This would be a set of watchers (that the validators trust) that record any and all copies of key event logs (KEL) that they see. Because these watchers can be anyone and anywhere, any controller of a public identifier is at peril should they choose to publish inconsistent copies of their KEL. This removes the incentive to be duplicitous.
web of trust
WebOfTrust
web of trust
Definition
In cryptography, a web of trust is a concept used in PGP, GnuPG, and other
OpenPGP-compatible systems to establish the authenticity of the binding between a public key and its owner.
Its decentralized trust model is an alternative to the centralized trust model of a public key infrastructure (PKI), which relies exclusively on a certificate authority (or a hierarchy of such). As with computer networks, there are many independent webs of trust, and any user (through their identity certificate) can be a part of, and a link between, multiple webs. The web of trust concept was first put forth by PGP creator Phil Zimmermann in 1992 in the manual for PGP.
More on Wikipedia
weight of weights
WebOfTrust
weight of weights
Definition
There are 2 levels in the multi-sign weighted thresholds of multi-signatures in KERI because the solution only needs to focus on tightly cooperating teams.
- An individual using split keys over devices
- A team of teams
All other use cases can be solved by other means in KERI (e.g. delegation).
CESR related
It also gives the advantage that the resulting CESR is more straightforward. It's hard to implement a recursive weight - of weights in CESR. And because of the alleged lack of use cases, KERI don't need to go beyond two levels.
well known witnesses
WebOfTrust
well known witnesses
Definition
Witness identifier creation by using salts to initialize their key stores so that you can predict what identifiers will be created. For testing purposes only!
Security
Don't use the creation of well-known witnesses in a production environment, but for running tests it's suitable.
witness
Nist
An appropriately cleared (if applicable) and designated individual, other than the COMSEC Account Manager, who observes and testifies to the inventory or destruction of COMSEC material.ToIP
A computer system that receives, verifies, and stores proofs of key events for a verifiable identifier (especially an autonomous identifier). Each witness controls its own verifiable identifier used to sign key event messages stored by the witness. A witness may use any suitable computer system or database architecture, including a file, centralized database, distributed database, distributed ledger, or blockchain.
Note: KERI is an example of a key management system that uses witnesses.
ToIP (DID:Webs)
An entity that is designated by the controller of an AID to verify, sign, and keep the key events associated with the AID, as defined by the KERI whitepaper. See WebOfTrust glossary for more detail.WebOfTrust
witness
Definition
In KERI and ACDC context, a witness is an entity or component designated (trusted) by the controller of an identifier. The primary role of a witness is to verify, sign, and keep events associated with an identifier. A witness is the controller of its own self-referential identifier which may or may not be the same as the identifier to which it is a witness.
An identifier witness therefore is part of its trust basis and may be controlled (but not necessarily so) by its controller. The purpose of a pool of witnesses is to protect the controller from external exploit of its identifier.
The term Backer and Witness are closely related in KERI but not synonyms or interchangeable.KERI witness confusing
Be sure to understand the narrow KERI definition of Witness well. You could easily be confused, for there are dozens of papers that use the term Witness in a similar way to KERI; for example https://ieeexplore.ieee.org/document/8644609 or 'segregated witness' in bitcoin, but it's far from the same concept.
More in the whitepaperOperational description in KERI
Entity that may receive, verify, and store key events for an identifier. Each witness controls its own identifier used to sign key event messages, a controller is a special case of a witness.
Source Sam Smith
xip
WebOfTrust
xip
Definition
A XIP message allows a transaction set to be a mini peer to peer exchange to become a verifiable data structure. It makes the transaction become duplicity evident.
Source KERI meeting 2024-03-12
zero trust
WebOfTrust
zero trust
Definition
a Zero Trust approach trusts no one.
KERI related concepts
Zero Trust is a shift of network defenses toward a more comprehensive IT security model that allows organizations to restrict access controls to networks, applications, and environment without sacrificing performance and user experience. As more organizations do more computing outside their perimeter in the cloud, security teams find it increasingly difficult to trust or identify who and what should be allowed or trusted with access to their networks. As a result, an increasing number of organizations are adopting Zero Trust as an element or a component of their trust network architecture and enterprise security strategy.
Zero Trust is a security concept that requires all users, even those inside the organization’s enterprise network, to be authenticated, authorized, and continuously validating security configuration and posture, before being granted or keeping access to applications and data. This approach leverages advanced technologies such as multi-factor authentication, identity and access management (IAM), and next-generation endpoint security technology to verify the user’s identity and maintain system security.
zero trust computing
WebOfTrust
zero trust computing
Definition
Best practices for implementation of an autonomic identifier system should follow zero trust computing principles. These principles are described at more length elsewhere but may be summarized as follows:
- Network Hostility. The network is always hostile, internally & externally; Locality is not trustworthy. Solutions must provide means to mitigate network layer security vulnerabilities (man-in-the-middle, DNS hijacking, BGP attacks).
- E2E Security. Inter-host communication must be end-to-end signed/encrypted and data must be stored signed/encrypted. Data is signed/encrypted in motion and at rest.
- E2E Provenance. Data flow transformations must be end-to-end provenanced using verifiable data items (verifiable data chains or VCs). Every change shall be provenanced.
- Verify every-time for every-thing. Every network interaction or data flow must be authenticated and authorized using best practice cryptography.
- Authorization is behavioral. Policies for authentication and authorization must be dynamically modified based on behavior (reputation).
- No single point of trust. Policies for authentication and authorization must be governed by end-verified diffuse-trust distributed consensus. Policy is protected by diffuse trust.
- Hosts locked down. Hosts or host components executing any of the logic mentioned above must be locked down. Any changes to the host execution logic or behavior must be fully security tested and validated over the respective possible combinations of hardware and software platform. This means locking down key management and cryptographic operations on the devices. This includes key generation and storage, as well as signature generation and signature verification. These may benefit from the use of some form of trusted execution environment (TEE) either generally or specially as in a trusted platform module (TPM) or a hardware security module (HSM). In addition to key management and cryptographic operations, special security measures must be implemented regarding secure execution of the application logic (e.g. code injection, insecure object references, cross-site/service request forgery, cross-service scripting, etc.).
Source: Universal Identity Theory by Samuel Smith
Also see
zero-knowledge proof
ToIP
A specific kind of cryptographic proof that proves facts about data to a verifier without revealing the underlying data itself. A common example is proving that a person is over or under a specific age without revealing the person’s exact birthdate.
Also known as: zero-knowledge protocol.
Supporting definitions:
Ethereum: A zero-knowledge proof is a way of proving the validity of a statement without revealing the statement itself.
Wikipedia: a method by which one party (the prover) can prove to another party (the verifier) that a given statement is true, while avoiding conveying to the verifier any information beyond the mere fact of the statement's truth.
zero-knowledge service
ToIP
In cloud computing, the term “zero-knowledge” refers to an online service that stores, transfers or manipulates data in a way that maintains a high level of confidentiality, where the data is only accessible to the data's owner (the client), and not to the service provider. This is achieved by encrypting the raw data at the client's side or end-to-end (in case there is more than one client), without disclosing the password to the service provider. This means that neither the service provider, nor any third party that might intercept the data, can decrypt and access the data without prior permission, allowing the client a higher degree of privacy than would otherwise be possible. In addition, zero-knowledge services often strive to hold as little metadata as possible, holding only that data that is functionally needed by the service.
Source: Wikipedia.
Also known as: no knowledge, zero access.
zero-knowledge service provider
ToIP
The provider of a zero-knowledge service that hosts encrypted data on behalf of the principal but does not have access to the private keys in order to be able to decrypt it.
zero-trust architecture
ToIP
A network security architecture based on the core design principle “never trust, always verify”, so that all actors are denied access to resources pending verification.
Also known as: zero-trust security, perimeterless security.
Contrast with: attribute-based access control, role-based access control.
Supporting definitions:
NIST-CSRC: A security model, a set of system design principles, and a coordinated cybersecurity and system management strategy based on an acknowledgement that threats exist both inside and outside traditional network boundaries. The zero trust security model eliminates implicit trust in any one element, component, node, or service and instead requires continuous verification of the operational picture via real-time information from multiple sources to determine access and other system responses.
Wikipedia: The zero trust security model, also known as zero trust architecture (ZTA), and sometimes known as perimeterless security, describes an approach to the strategy, design and implementation of IT systems. The main concept behind the zero trust security model is "never trust, always verify," which means that users and devices should not be trusted by default, even if they are connected to a permissioned network such as a corporate LAN and even if they were previously verified.