<@U024CJMG22J> has joined the channel
<@U02PA6UQ6BV> has joined the channel
<@U03KLB48Q2E> has joined the channel
<@U03EUG009MY> has joined the channel
<@U035D255M0R> has joined the channel
<@U03N48D5VD1> has joined the channel
<@U02N7K951DW> has joined the channel
<@U03QRSUA87Q> has joined the channel
Thanks for getting this started Henk and Phil.
Minutes ready for review:
Thanks Henk
<@U02MD0HA7EJ> has joined the channel
Have a look at the kli interview and how it hopefully has become an
integrated eduction resource :
Join Zoom Meeting
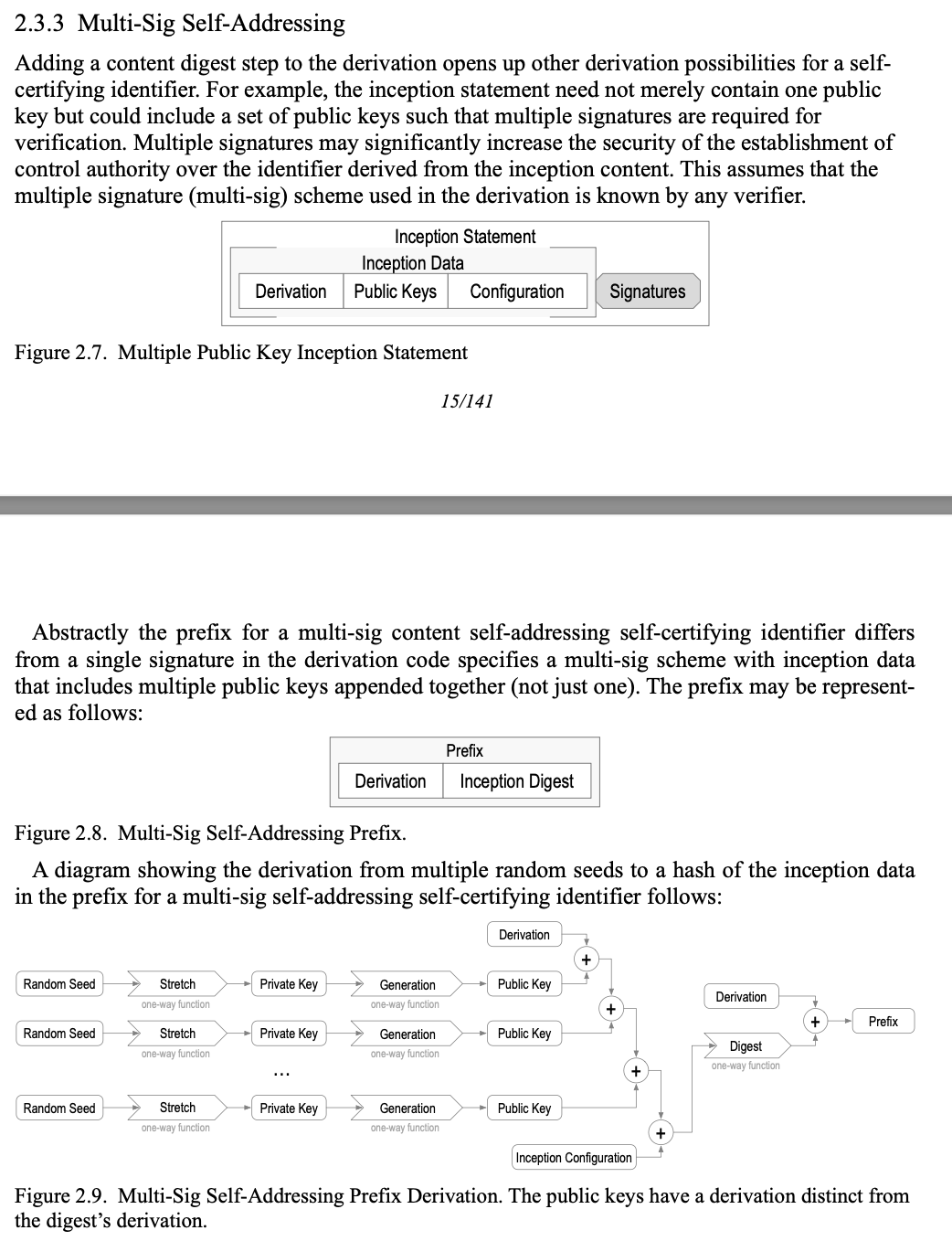
First draft KERI IETF draft specs mind map:
as I promised in the Meeting
here you could search & find “{TBW prio ..}“, To Be Written it means, and
then use the links to go to the right wiki-item to amend to my definition.
:pray:
As soon as an term is saved (at least in my case ) Github Action produces a
new static glossary within minutes… feel free to try it.
cool, thanks Henk.
For your convenience :
Sorry I missed this morning
I had a production deployment I was attending to
Oh crap, was it today? I don't have it on my calendar yet. So sorry to miss
today, thanks for the minutes <@U02PA6UQ6BV>
No worries, we got to good results, I think, even though we appreciate your
contribution!
<@U02PA6UQ6BV> That's wonderful! Thank you
Yeah, this is useful.
<@U03U37DM125> has joined the channel
I’ve added some of the Glossary terms from the GLEIF draft glossary (a pdf
downloadable) to our KERI/ACDC glossary :
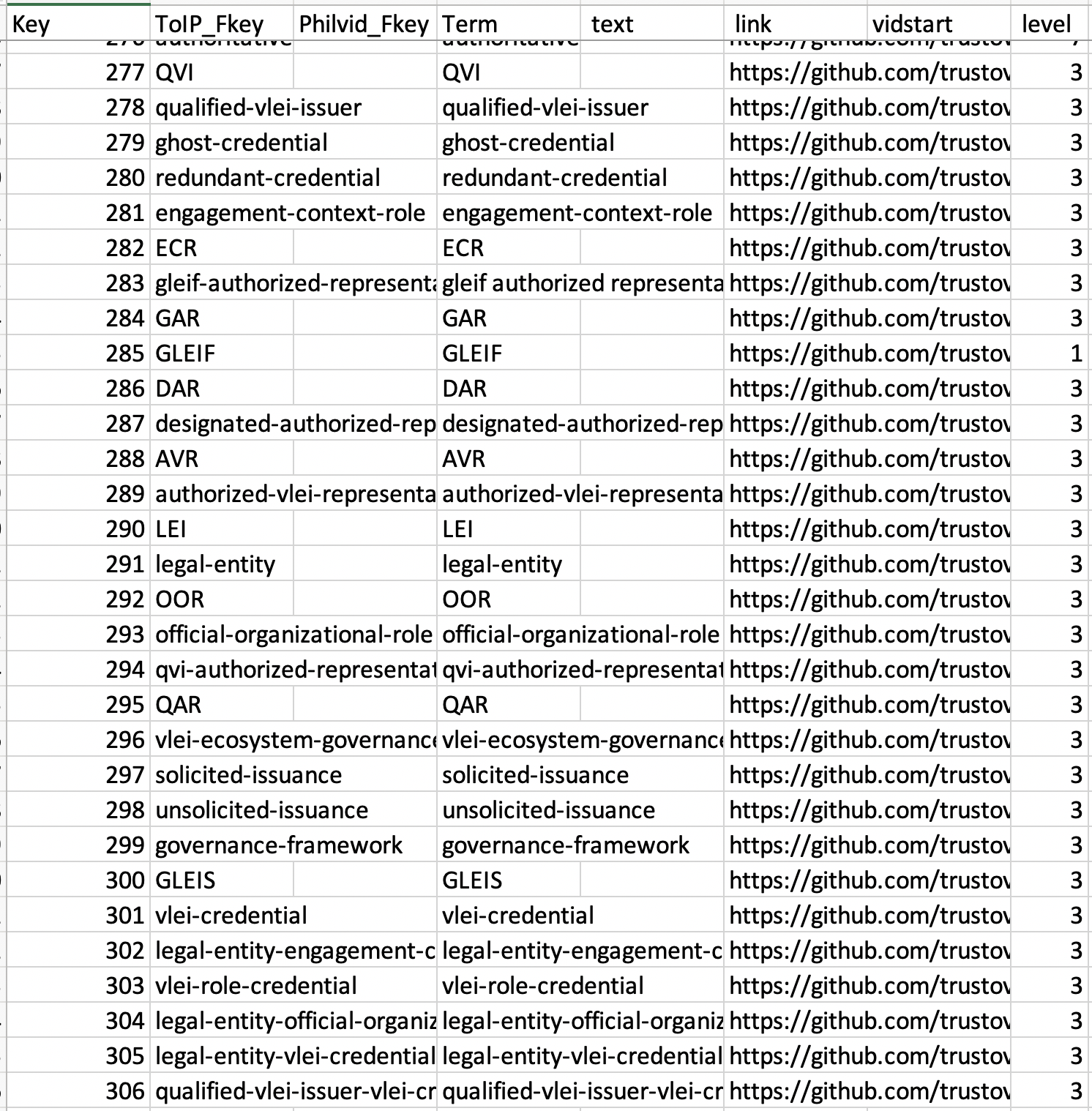
Nice work.
Have a look at a few more “why’s” answered. I’d like to discuss this in NEXT
week’s Zoom session:
It would be cool to have a way to vote on different definitions as well as
see their source and supporters.
I’ve started with a commenting tool ; I pay
for them, in return they’re not selling our data :wink: like disqus does. Let me check out their
options; maybe up- / down voting is possible.
check : up- / down voting of comments is possible, so if we’re dropping
amendments in comments and have them up- or down voted, we’re well on the way with your tip?!
<@U03UV1EBVDF> has joined the channel
<@U02PA6UQ6BV> - Custodial Agent: An agent owned by an individual who has granted signing authority
to a custodian who is usually also the host of the running agent software. Using partial
rotation to facilitate custodial key management the owner of the identifier retains rotational
authority and thus the ability to "fire" the custodian at any time without requiring the
cooperation of the custodian.
Custodial Agents are important for individuals who may not be comfortable managing their own
signing keys and agent software but still want to participate in a decentralized identity
ecosystem and they enable a software as a service business model without centralizing control on
the service provider.
Could today’s Google/Facebook etc… be a “Custodial Agent” ?
Only if they are willing to give up complete control of an individuals
identity and data.
<@U035ZHBF21H> has joined the channel
thanks
<@U03P53FCYB1> has joined the channel
I mentioned a project at my work in the Authentication space.. for now I am
going to recommend and implement this so my company
can have its own Identity Provider.
I hope implementing this will help me gain me experience in the Identity
space. So I can be a more valuable contributor here (since I am still a noob)
If you guys have suggestions on implementing OICD with it being able to
support any form of SSI, then let me know.
It’ll surely earn you some experience!
I would still describe OpenID as old school SSO interoperability service, although they’re trying
hard to adopt Self-sovereign Identity as a bolt on?
In OpenID ‘SSI’ is more Self Service Identity instead of Self Sovereign Identity, because you have
to trust people for your identifiers and they’re not truly portable.
Just my 2 cents, worth the effort anyway, because the support/UX will be lots better than the
KERI/ACDC “suite” has to offer currently, for OpenID has been out there for a decade at least.
I’ll be late to the call. Checking in to my Airbnb in Dublin
I will miss this weeks call since I’ll be on a flight.
I’m excited to meet again though since I’m finally ready to review all of the
definitions <@U02PA6UQ6BV> has written and then prepare my opinion on how to effectively move
forward.
Apologies. I'm unable to attend today's call
Yet another apology, I haven't reviewed the GitHub Issues yet.
Minutes and recording of today’s meeting:
Thanks Henk.
Join Zoom Meeting
Meeting ID: 898 9352 7631
Passcode: 197037
Be right there
:pray:
Here’s a KERI Architecture Overview diagram to get our conversation going on
making useful pictures about KERI. I just posted it in <#C03TSFRNWLU|cesrox> as well:
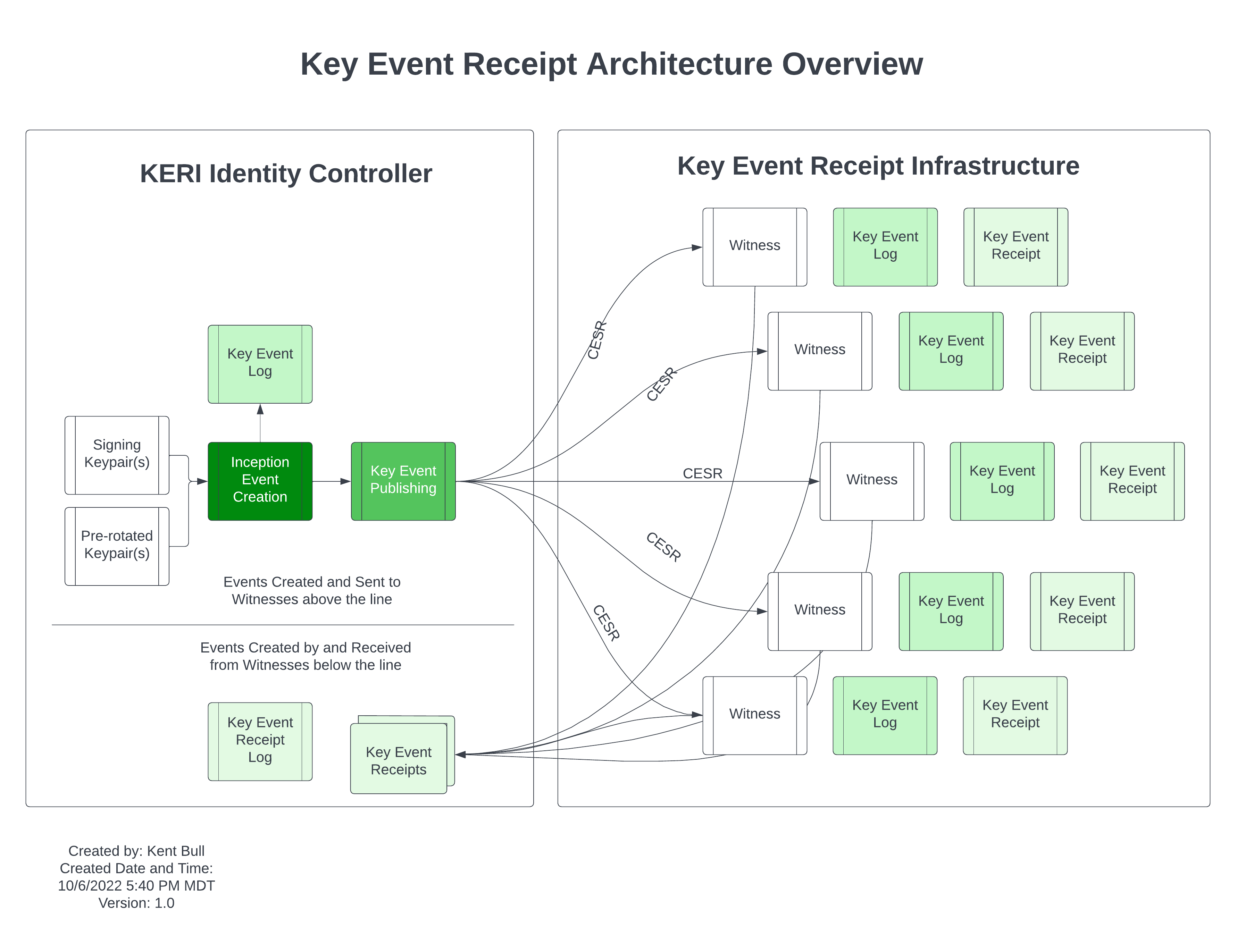
My goal with this diagram is to make it easy for someone to see that key
events go from controllers to witnesses and key event receipts come back from witnesses to
controllers. I also wanted to identify where CESR comes in to the process.
When I try to comment in the software you use, they start nagging me with
pop-ups and free-trials, so here’s my comment:
in the left side you introduce Key Event Publishing with a distinct shade of green. How is this
square different from the one on top? Is the ‘publishing’ action not exactly what you set off when
using CESR?
I would leave the ‘(s)’ in the left most square, for we only have one
inception event per KEL, the next signing and pre-rotated key pairs are relevant in rotation events
not in the initial ‘inception’ event.
It’s a good thing that we start drawing infographics! Well done. May many
more follow.
This is the drawing I wanted to create for some time. Mind you it’s a draft.
<@U035R1TFEET> has joined the channel
Sorry to say, I have miss today's meeting. Been pulled into a meeting for our
go live date that I can't miss.
Thx for letting me know!
Is it the same zoom each week? Can we put it in the channel topic? Just
waking up and I cannot find the link
try that
KERI’s magical mix :wink:
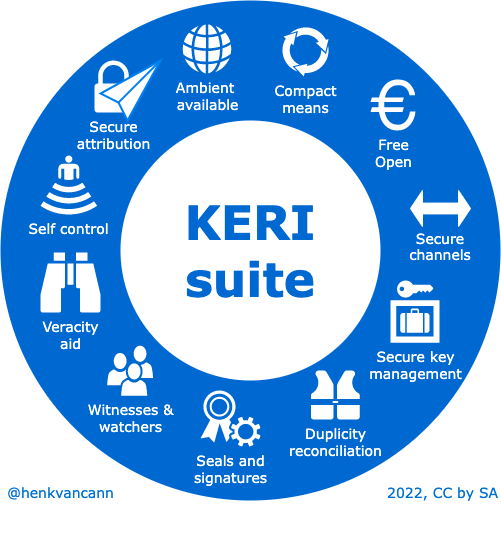
Problem solving : discomfort on the web -> gone with KERI
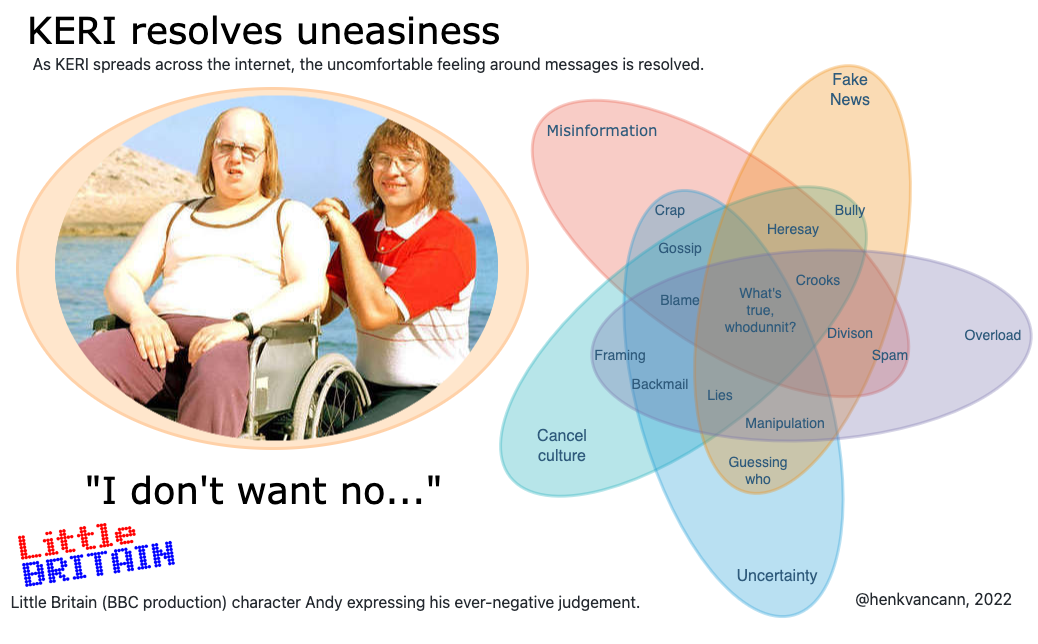
please check the effectiveness of the wording in the visuals above (“me no
native”)
I like the big circle those some of the graphics don’t make sense to me like
the life jacket on duplicity reconciliation
This is a good first draft. I would substitute bad data for crap and unknown
bad actors for crooks. Those two words, crap and crooks, are a little less professional and a little
more incendiary than what it seems you want.
When I need to explain it, that’s your proof :slightly_smiling_face:
Do you have other icon suggestions for those that don’t make sense to you?
‘bad data’ and ‘bad actors’ would never be Andy’s vocabulary
but I see what you mean. Thanks.
Crooks -> cheaters
Crap -> junk / trash
Many did make sense though seems as if they could be slightly improved.
Others didn’t make sense. The ones that didn’t make sense are
• compact means
• Free open
• Secure channels
• Secure attribution
What would you suggest as an icon for those. Could you describe it in words?
Then I can ask somebody to create an icon that matches a prescription we relate to.
I’ll explain my view on the icons:
Secure attribution: the paper arrow with a lock. For me it’s a picture of somebody sending a message
and I can be 100% sure it’s from him or her. Like a snowball in the school yard; it landed cold and
wet in your neck, you turned around and wondered ‘who did it’?! Relatable?
You look around and a few class mates are laughing, some are smiling at you. You can’t be sure, so
you try to hit the one with the biggest smile on his face with the snowball you had just been
preparing when one of them hit you off guard.
Same with paper arrows through a class room, it lands on your desk, our in your hair, but again… who
dunnit?
I changed free and open into a flying bird, unfortunately the twitter bird because the set of
symbols I can choose from is limited.
“Compact means” when we design long living, all encompassing identifier
systems for people, orgs and IoT devices, we have to take of every single bit and byte we use. And
happily KERI, ACDC, CESR, OOBI etc, do so. So it’s the minimal sufficient means variant and the best
environmental friendly approach we can have for persistent identifiers.
Secure channels: peer-to-peer, OOBI and CESR. Backwards:
If you can’t read what going over the line, security is no more than pure trust. CESR is round robin
composable and makes it cryptographically verifiable and visually verifiable and solves this
problem.
OOBI is an extra, time-gap-bridging guarantee (by authentication) that some entity is the one who
you think it is while being introduced to it. OOBI is discovery via URI, trust via KERI.
Confidentiality and Verifiability is preserved; therefor a (just authenticated) secure one-to-one
channel.
The two-headed arrow symbolizes the p2p nature of this exchange.
Again, if I have to explain the icon, it’s not a good-enough icon. But if we
describe the analogy we all can relate to, I can find somebody to draw a matching icon from this.
<@U02PA6UQ6BV>Is there a call 03 Nov? The original calendar was only for 7 occurrences.
I added new dates to the agenda
Thx for the discussion guys.
For <@U024CJMG22J>’s use case about authenticating video… that got me
thinking, and I just want to express my thoughts here if you don’t mind. Usually the videos that
go viral are controversial … like “I cannot believe they said that”… And you are never going to
get a politician or rioter anyone someone to “sign” your video. But this got me thinking… how
can one of those videos be authenticated in general? It would take a fundamental shift in how
the world works (which I am still able to believe can happen) -- It must stem from lower level
(or common) attestations that people are willing to make. For example… Politician A was in
location X giving a speech. They attest to time and location for that event. (maybe they should
verifiably attest to their location all the time as a public servant?). The video that was taken
was taken by person B also verifiably attested to be at location X. The camera C may need to
have some “verifiable video” mechanism internally? Maybe another verifiable record of the
purchase of camera C by person B… So much needs to be in place, in order for someone to write a
“reputation algorithm” And the algorithms could use this or any number of other types of
attestations (key event logs?)
So much needs to be in place for some of these higher level scenarios.. but
even just one of these components could be valuable
Like if we had a “time and place” signature app that attests to where your
phone has been (notice I said your phone, not necessarily YOU) … but then that combined with
biometric unlocks of the phone can certainly verifiably place YOU at place and time
Just that can be something used in a court of law … “Where were you on the
night of… ” type of legal questions.
“Authentic Location” app
I would love it if politicians had to have this :joy:
or if they CHOSE to have it
in order to say “I am an authentic politician and I share my authentic
location” ( I suppose that could be dangerous LIVE… but it could be shared publicly from the past
weeks or months)
I know Google already tracks us. I have seen the data of where I have been
Good thoughts! I too believe that you could have an authentic web closing in
on anyone trying to repudiate something they’ve said or done.
Like the “alternative facts” around the inauguration of Trump. Just as an
example. There was at least ‘duplicity’ in play.:joy:
meeting minutes and links
I am coming at this problem from a different angle. I'm not trying to create
a solution that can help us prove that someone said something they are claiming they didn't say.
That's a much more complicated problem. I wanted to provide a solution to deep fakes. If we only
ever trust videos that the subjects of the video attest to, then we won't be at risk of trusting
deep fakes.
However... I do think there is a place for non-repudiable reputation systems to help with the other
problem. While we can never prove definitively that someone said what a video suggests they said, we
can provide a system that allows for non-repudiable attestations from autonomic identifiers that
they "saw" that person say those things. Then we can leave it up to the consumer of those
attestations to decide how much trust they want to put into the reputation of the identifiers making
those attestations. In the end, you are no longer listening to trolls shouting into the wind. You
are relying on provable reputation that can't be faked. If someone wants to burn their AID by lying
about a fact, they can't get away with it.
I see where you’re coming from and thanks for the explanation!
Isn’t the end result of the example I gave, more or less the same: one of the pictures of the
inauguration ceremony is false(ly dated) and / or a deep fake. And there will be a whole bunch of
people attesting to either version of the truth; whether it’s the real one or the fake one (or both
:slightly_smiling_face: ). Or we might be looking at two fakes. Both sides of the “reality and
facts” could hire trolls to support their “truth”.
I follow your reasoning 1 on 1 about attesting what somebody ‘said’ or ‘did’ at the time it happened
“live”. But I am more sceptical about what we can do about deep fakes that are surrounded by
(sincere and insincere) attestations of true believers and people with an agenda putting the the
credibility of their AID on the line. How can we make a trustworthy decision when there are ‘camps’
and major interests at stake. Even the subjects of a faked video might be enticed to attest to it,
when the end result is more in their interest than the original footage.
Am I missing something?
Because of IIW35 going on, we skip todays edu meeting. See you in two weeks!
Thanks for the heads-up!
<@U047UUDAHUY> has joined the channel
Hi! I have a question.
The introduction to KERI draft says:
> There was no built-in mechanism for secure attribution to the source of a packet. Specifically,
the IP packet header includes a source address field that indicates the IP address of the device
that sent the packet. Anyone (including any intermediary) can forge an IP (Internet Protocol)
packet. [...] This means that secure attribution mechanisms for the Internet must be overlaid
(bolted-on). KERI provides such a security overlay.
Now consider a situation: Alice is sending her inception event to Bob (direct mode). Bob can verify
that the identifier belongs to the inception event. But *how can Bob verify that this inception
event came from Alice* and not from Eve? If I understood KERI's introduction correctly, this is the
objective of KERI: to provide a way to ascertain Alice's identity.
I understand that once the identity of Alice is verified at the beginning, all future data received
can be verified by her identifier that the data are from Alice, because only she could sign the
data. But how can Bob verify Alice's inception event (the first data sent to bob)?
From an in
this channel, I'm guessing the initial attribution is done through OOBI. I have yet to read up
on it, so I don't know if this assumption is correct.
If I understood KERI’s introduction correctly, this is the objective of KERI:
to provide a way to ascertain Alice’s identity. -> As a byproduct of Secure Attribution (which is
a more overarching objective of KERI) the inception event (and the key event log as a whole) is
verifiable to the root of trust.
The OOBI merely jump starts authenticated discovery. This means that KERI is going to rely on its
own inner workings (verifiability to the root-of-trust, “first seen” and duplicity detection) as a
next step after having set off the validation proces by the ‘first seen’ discovery of an IP address
related to a KERI AID.
more to this in
Thanks for the article.
You said, "[T]he inception event [...] is verifiable to the root of trust." The root of trust is
just the key-pairs, right? If so, then I am with you on that. But my question was: how do I know
that the key-pairs belong to Alice? Why can't Eve pretend to be Alice?
Great question <@U047UUDAHUY> what you are asking is a 'Governance' question
which goes beyond the KERI technology, into the human realm. Essentially once humans properly
connect to their identifiers through a Governance process, then we have a measurable amount of
risk. If the Governance is thorough and the incentive to maintain your identifier is well
positioned then most of the risk is found in the possibility of getting your keys hacked/stolen.
The hope is that the KERI ecosystem provides the less points of attack for hackers and it
provides a mechanism called pre-rotation that can help you reduce your key-pair being
compromised. Then also elements of multi sig can help raise the bar of a successful attack, etc
Trust over IP and GLEIF are closely related to KERI and deal with Governance
topics
Understood. Thanks.
(Understood in the sense that I now know the answer to my question resides outside KERI. I need to
read up on “Trust over IP” and “Governance” in general.)
<@U04BRS1MUAH> has joined the channel
Next Thursday the EDU meeting needs to be cancelled for I am driving a car at
that very moment.
Kor Dwarshuis is my fellow countryman who started supporting us a few weeks
ago. He will join the next Edu meeting on Dec 15.
The search is really cool. There must be a linking problem though since when
I click through then I get a 404:
Yes, that is a known error
Sorry folks, we are in the middle of creating the final 2 AIDs for the GLEIF
Root of Trust and I won't be able make today's meeting
(Like, I'm sitting in the meeting and we are waiting for one of the Root AID
key holders to approve the deletation!)
It was cancelled today since Henk is on vacation. It’s exciting to hear GLIEF
is moving along!
<@U04DQE2G36F> has joined the channel
<@U03R27M4FM3> has joined the channel
Correct in understanding EDU mtg Thurs, Dec 15?
yes, 8:00 AM MST.
Right, same time as KERI / ACDC / Cesrox call, alternating with Cesrox
One small topic from KERI call to discuss / receive clarity: definitions of
“judge” (), “jury” and “juror”, as popped up in the
chat of the KERI call. Synonyms or different?
A judge looks at many sets of KERLs and DELs (duplicity event logs) to
validate a controller is trusted by a threshold of witnesses.
A juror has a simpler task of performing duplicity detection on events and event receipts.
The jury is the set of entities or components acting as jurors.
From the whitepaper:
> 7.38 Juror
> _A juror is an entity or component that performs duplicity detection on events and event
receipts…_
>
> _7.40 Judge_
> _A judge is an entity or component that examines the entries of one or more KERLs and DELs_
> _of a given identifier to validate that the event history is from a non-duplicitous controller
and has_
> _been witnessed by a sufficient number of non-duplicitous witnesses such that it may be
trusted_
> _or conversely not-trusted by a validator._
Great, that’s work I needed to do
I’ll add the defs accordingly
They have good starting definitions. It will be fun when we can enhance the
acdc terms wiki with links to examples that people can run to see them in action.
Is there an EDU meeting today?
It looks like I'm the only one
Yes there is
Was the link changed?
thanks, I forgot about the link in the channel description
Recording and minutes available of the Edu meeting today.
NEXT meeting will be on Thu Jan 12 - usual time
So we SKIP the one between Christmas and new year!
:pray:
The 3 slides Q&A about Algolia search configuration options
Compliments to <@U024CJMG22J> on today's "architecture walk through". I
learned more in one hour about how this is all put together (and why it's put together that way)
than spending weeks reading.
More Please.
Compliments as well to <@U02PA6UQ6BV> on the (really useful looking, want to
play with) integration of Jekyll & Algolia. Should really lower the learning curve for KERI
& ACDC
<@U02PA6UQ6BV>, the calendar .ics invite link posted in the agenda is broken. Is there a new one
somewhere? Thanks
Is there a meeting tomorrow?
Nope, I’ve skipped this week’s meeting bc of Christmas / New Year holidays.
Next one will be Jan 12
<@U04HMQT1XFV> has joined the channel
<@U04H17ZEX9R> has joined the channel
This is the corresponding page on github:
<@U02PA6UQ6BV> Can you please add a link for the latest terms?
The latests new terms added to the ToIP wiki concerning KERI / ACDC:
396 keri-ox keri-ox RUST implementation of KERI
397 pii pii personally identifiable information
398 contextual-linkability contextual-linkability
399 blinded-revocation-registry blinded-revocation-registry
400 rainbow-table-attack rainbow-table-attack
401 SKWA SKWA Simple KERI for Web Auth
402 simple-keri-for-web-auth simple-keri-for-web-auth A KERI implementation
that sacrifices performance or other non-security feature for usability.
403 KRAM KRAM KERI Request Authentication Method for replay protection
404 keri-request-authentication-method
keri-request-authentication-method KERI Request Authentication
Method for replay protection
405 juror juror performs duplicity detection on events and event
receipts
406 jury jury set of entities or components acting as jurors
407 opcode opcode provide stream processing instructions
that are more general and flexible
Small typo - 202*_3_-*01-12 - fixed in the HackMD minutes
Looking forward to the recording (regrets on not attending - Thurs is still
to full of double booking in 2023)
Thx Neil, I corrected it on Github already as a quickfix.
<@U02PA6UQ6BV> looking forward to the recording, I hear it was a quite the session. I'll check back
here.
<@U03R27M4FM3> I post the link to the recording always within an hour after the meeting.
But oops, this time, it got lost :slightly_smiling_face:
repaired now and here it is directly:
Grasping at Straws here: Is OCA and ACDC related?
Yes, an ACDC has a schema tied to it
No.
KERI/ACDC do not implement OCA
The way <@U03KLB48Q2E> was using OCA seemed very familar to him, this is the
first time I am hearing OCA
And the schema itself can be converted using OCA into something readable for
a local hero
it looks interesting, and I see its related to semantics and schemas and so
is ACDC, that is why I ask
I believe the reason is OCA is not lightweight enough
It’s conceptually related I would say
Yeah, it seems heavy
I've worked with OCA & have a small demo
Myself I decided to skip the problem of localization for a while and just
concentrate on English.
And the concept that unifies them is “Decentralized Semantics” ? Yes?
There's a Decentralized Semantics call going on now
> The primary objective of decentralised semantics is “data
harmonisation”, which refers to all efforts to combine data from different sources and provide users
with an equivalent view of data from various studies
Wish I had the luxury to “do what I want”, I am still chained to the man
(i.e. I have a Job, no financial independence as of yet)
It's being recorded
There are some fundamental differences between the approaches. I have heard
it said that OCA believes that semantics comes first where as with KERI/ACDC security always comes
first.
I have not spent much time studying OCA so I may be misrepresenting.
Apologies if so
Interesting question for Robert
I am curious about the ACDC and OCA overlap
Human Colossus Foundation is part of the OCA community. Interesting.
I think there could be a direct relationship to the KERI/ACDC schema and a
more verbose/versatile OCA representation
As an ACDC noob, I hear “append to extend” and that rings truly universally
acceptable to me. I wonder if this is a fundamental difference.
> Here are the notes and the link to the recording.
That will be a wonderful day.
Looking forward to it for myself as well.
I would like to write an (unofficial) glossary for all terms related to KERI.
(I would like to do it as part of my learning process.)
Since I have never had a chance to attend a meeting from the education grounp yet, may I ask if this
is already on the agenda, and if someone is already working on an official glossary?
Thank you :slightly_smiling_face:
You're in the right place! <@U02PA6UQ6BV> can point you to the latest work in
process
Some of the terms are defined here, did you check that?
Technically authenticity comes first. When describing the domain, however,
much like in the DDD approach, integrity (OCA) comes first.
At the same time OCA isn't bound in any manner to any particular authenticity layer. It is out of
scope.
Last year there was a debate of one vs. another (JSON-schema vs. OCA) . Long story short, ACDC gradually
protected selective disclosure benefits from JSON-schema branching attributes (ie. `one-of` )
that OCA doesn't support
Yes we’re well on our way here (371 glossary terms):
Thank you :)
It seems that this official glossary is meant to be comprehensive and include
terms that are not exclusive for KERI.
Personally, I would like to write a much shorter one where only the terms unique to KERI & ACDC
are included.
Would something like that be useful for the community? At least for beginners like me
:slightly_smiling_face:.
Yes of course, we could also tag the KERI/ACDC/CESR/etc. terms with this
notion.
Currently, I have this structure:
This is not a shared database yet, because it’s still under construction.
There are _categories_ and user _levels_ defined as well. Both haven’t been applied very well to
the terms yet.
You might be interested in tagging the terms (general, SSI-specific and KERI/ACDC unique) and
formulating level 1 definitions: . And you’re welcome to do so!
Could you post a few examples of how you would formulate things differently?
Be aware that our focus starting level 1 (of 3), a ‘beginner’, is still an expert in the field of
identity! Target groups like friends, family, and other laymen are out of scope for us. If you’d
like to reach out to this type of student, you might have to create a level 0 by yourself.
I just posted a simple tutorial on using KERI for signing and verification of
messages.
Take a look if you’d like. There’s a companion YouTube video (27 minutes) that walks you through the
post.
I am looking for critiques and overall general impressions. This is the first
ever public technical tutorial I have written and I want to learn how to do this better so I can
make my next tutorial even better.
awesome. Looks fantastic at first view!!!! I'l try to go through each step on
those days. How do you want the feedback
here in slack works great. Or via email at
I want to do a video and written tutorial on the Cardano backer as one of my
next tutorials.
I don’t want to steal your thunder though, so if you haven’t written a blog
post or something and you’d like to then I’ll wait.
I only wrote a "how to run the demo" (that I need to update). I'd be great to
have a tutorial from you, and happy to help also! By the way, just finished watching your video, it
is excellent. Cristal clear.
High praise from a fellow engineer. Many thanks!
Thank you so much for the information!
Hello all! Could someone possibly give me some pointers on the concept of
“backers” in KERI? They’re mentioned without explanation in the IETF draft, and I can see their
inclusion in the GLEIF root inception event, but I don’t really understand what their function.
we’re working on a Docusaurus Educational site, will take some time though
Thanks!
<@U024CJMG22J> is an OOBI like a “Contact Card”? If someone shares their OOBI with me, could I
(should I) keep it around? If I kept it, it would be more like a “Contact Card” right? And if I
collected my friends OOBI Contact Cards, I could share it with another friend right? Maybe this
is where ACDCs come in - the OOBI may have information on “how” in can/should be shared. Or
maybe its one level deeper. OOBIs can be shared freely, but the ACDC will help not expose all
the information associated with the OOBI. Like if someone just “found” my OOBI somewhere on the
internet (maybe I post it on my website) then all they get is my email address or something.
I would like to extend this article with more symbols and analogies you’re
currently exploring
So cool. Thx.
The best way to teach these concepts is using the “sticky platform” method.
You need to start with something that someone already knows (like an ID card or a Contact Card) and
tell them how it is different.
Yes, like ‘horse power’ was used as a measure in cars
Thanks to <@U03QRSUA87Q> for his first PR to the Concepts, Terms &
Eduction site !
<@U024CJMG22J> had asked who would be willing to build the governance doc for <@U02PA6UQ6BV>’s idea
of a KERI governance framework for securely attributing edu-statements in our documentation.
I’m doing a 5 day deep dive into GLEIF and would like to use that use case to organize my
learnings. Any pointers to documentation for how to set it up would be appreciated
You'd have to start with the EGF documents themselves:
As mentioned in intros, the EFG was modeled using the ToIP Ecosystem
Governance Framework model so reading up on the ToIP documentation for creating an EGF is also
recommended (sorry I don't have the links handy).
I think this would be a great topic for tomorrow morning's Edu call if you
can attend!
I’ll have to skip my coveted Aries Framework Javascript meeting with Timo and
friends…. but worth it :slightly_smiling_face: See you all then
bah time zones, okay it’s in an hour from now, i’ll probably be a little
late, but will jump in after a shorter other meeeting
Great discussion, thanks folks, here the report & recordings:
feel free to amend!
video still processing, can wait :grinning:
<@U025GFV1SJC> has joined the channel
This content can't be displayed.
/github subscribe WebOfTrust/keridoc
undefined
:white_check_mark: Subscribed to . This channel will receive notifications
for `issues`, `pulls`, `commits`, `releases`, `deployments`
I made a utility for SAIDifying a graph of ACDC schemas called . It is based off of Kevin’s work on the `generate.py`
script in the vLEI project.
Great! What is it going to do for / in Education? I don’t have a clue
:slightly_smiling_face:
It is going to make learning about how to make ACDC schema graphs easy.
The blog post tutorial I am writing will be using it.
And explaining it.
Ah great, interested in the link to it as soon as you’re done
<@U02PA6UQ6BV>
If you wouldn’t mind, I have a question regarding the definition of “Controller”. Here, you
wrote, “In KERI an AID has one single controller.” I wonder if this definition still holds in
the case of a multi-signature scheme.
Let’s say there are 3 people holding three separate sets of signing and pre-rotated keys for a
multi-sig AID. Does this mean the 3 people act collectively as a single controller for the AID?
Most probably not :slightly_smiling_face: , feel free to correct / amend the
definition !
I would say the weighted threshold of current set of the multisig controls
the AID.
Cool! Good to know.
Do we then need to also consider delegated AIDs where there is some shared
control (establishment vs non-establishment)…..
Also, in direct-mode there is one controller
So, maybe Sam’s descriptions about binding should be the focus…. that the
controller is strongly bound to an AID if their key pair is included in the most recent
establishment event?
<@U035R1TFEET>
Please correct me if I am wrong, my understanding is that you can use a multi-sig scheme for the
direct replay mode. The protocol operational mode becomes indirect only when other supporting
entities (witnesses, watchers, etc.) come into the picture.
<@U02PA6UQ6BV> I just wrote a new definition based on Page 41 of the white paper. I hope this is
helpful.

<@U04H17ZEX9R> well done, this would be a KERI specific definition of controller (“level 7” we
called this so far). We also need a more basic version.
There is yet no standard way of doing this in one definition md-file.
I think you are right
great job!
I published a WIP blog post here:
Password is `keri-edu-rocks`
The post isn’t even 10% done yet. I will post here when it is ready for review.
Looking forward to that recording <@U02PA6UQ6BV> so I can continue collecting
the (amazing) thoughts
Oh there are already 7 levels :exploding_head:
I unpublished the blog post since it accidentally went out on my RSS feed. I
will republish it towards the end of this week when it is complete.
Can't wait to see your blog post and follow step by step with wireshark
capture on!!
You’re gonna like it
I am looking forward to your blog as well!
Great, I’ll get it out. I will release the scripts I am using to build the
blog post off of so you can get going before I finish the prose.
The source repo is here:
The scripts will be pushed later today or early tomorow.
For anyone who wants a sneak peek at what will be in the blog post check out
the `workflow.sh` script in my repo.
You can run that with `kli vc present --name explorer --alias richard --said
<any_SAID_from_list> --recipient zaqiel --include`
with any SAID from `kli vc list --name explorer --alias richard`
to trigger the webhook for any of the credential types.
A postman collection will be added tomorrow with all requests needed to perform the same steps
as the `kli` does.
You need of Sally to finish the
process as well as installed.
If you don’t want to struggle through any dependency or setup issues then just wait until
Friday :stuck_out_tongue:
I am struggling with the definitions of “non-establishment event” and
“interaction event”. I hope this can be clarified in the wiki.
From the whitepaper they are defined as follows:
`A _non-establishment event_ is a type of _key event_ that is interleaved into the key event
history with the events from the _establishment event_ subsequence (history) in order that
the current control authority (root authoritative key-pairs) may be cryptographically
verified at the point in the interleaved sequence order where the _non-establishment event_
appears. An _non-establishment_ event includes an event specific _data payload._`
`An _interaction event_ is a type of _non-establishment key event_ that is interleaved into
the key event history with the events from the _establishment event_ subsequence (history)
in order that the current control authority (root authoritative key-pairs) may be
cryptographically verified at the point in the interleaved sequence order where the
_interaction event_ appears.`
If an interaction event is a type of a non-establishment event, what are the other types?
There are two main types of events in a key event log:
1. establishment events
2. non-establishment events
Establishment events change control authority. The inception event establishes control authority
with the initial keypair(s). Any rotation events establish control authority with the newly rotated
keypair(s). This seems to be why they are labelled as “establishment” events.
Non-establishment events do not make any change to control authority. So, all interaction events are
non-establishment events. There are no other categories of non-establishment event types for a key
event log (KEL) I am aware of.
However, for a transaction event log (TEL) used in ACDCs there are events that could be considered
non-establishment events yet I hesitate to apply the phrase non-establishment events to those events
since it may only apply in the context of the KEL rather than the TEL. Clarification on this point
would be helpful and would come primarily from Sam Smith.
The Postman Collection for the Abydos Tutorial is posted along with the Postman
Environment to make it all work.
Thanks for the clarification! It seems odd to me to say that it is “a type
of” when there is only one type.
Yes, I agree, that was odd to me as well. Maybe there are plans in Sam’s mind
for other non-establishment events.
I am realizing much of what happens in the dev meetings really should happen
in the Edu group.
Even the creation of a community set of witness/watcher networks and trust anchors, learning about
all of that could happen first in the Edu group.
Ideally the dev meeting is about development priorities and PRs. Currently we spend most of our time
in the dev meeting teaching and asking questions. This is a big opportunity for the Edu group to
come in and save the dev group a lot of time.
Do you agree?
Educational group discussions on KERI fundamentals are best had in the Edu group.
What dev meetings? Is this a formal/scheduled thing?
Yes, we lose valuable time on side stuff if you ask me in the dev meetings
(introductions of new people; why haven’t we recorded ours and link it for the newcomers?).
<@U03QRSUA87Q> the regular Tue meeting are dev meetings alternating KERI / ACDC
We have GOT to get an educational article out on SSH access with KERI. That
is something that will resonate with every developer who sees it. It is a perfect way to get up and
running with KERI and ACDC on a use case we all are familiar with.
That was so cool!
What problem does it solve? (don’t kill the interviewer)
Secure rotatable SSH access to any VM
(Plus it gave Phil something to do last weekend)
haha
it kept him from talking to his family
How many cases of severe damage have we witnessed because of not having
Secure rotatable SSH access so far?
Technically it kept him from bugging his family because they were all busy
with something else and didn't want to drink and watch basketball with him.
So real answer... the problem I was trying to solve was unifying the
authorization of SSH access to a VM with the authorization for signing a document submission.
Specifically, the question was asked, can we issue a credential to just one identifier of the signer
of the report and have them use that identifier to both sign the report as a holder of a vLEI and
gain access to upload capabilities.
Great presentation, Phil, I loved it, I think we’re looking at a pretty easy
to understand application of KERI/OOBI/ACDC, I am trying to figure out how it could be a killer app.
“to both sign the report as a holder of a vLEI and gain access to upload
capabilities.” So for my understanding: I could no way get this going with my PGP based SSH key.
<@U024CJMG22J> i was super late to today's call (forgot about the time change) and listened to the
last few mins of your presentation.
About a year ago we did an exercise exactly with KERI+SSH , employing Unix pam modules. I dont
know how you solved it in your case, because I joined too late, but with a pam module you have
broader support for unix-based tools that rely on PAM
<@U02PA6UQ6BV> Not unless you can convince GLEIF to issue a vLEI to your PGP public key
That's cool, sorry I don't remember that demo. I see integration with a great
many auth mechanisms as I mentioned. In particular we are interested in integrating with cloud
provider directory services.
Hey guys, we had a very brief meeting today, nothing has happened on the
action points of last time due to the remnants of a flu I am coping with: .
We’ll pick up stuff to do in the next two weeks!
<@U02PA6UQ6BV> take care
<@U03EUG009MY>
<@U04H17ZEX9R> and I are meeting… maybe at the wrong link?
Henk we are talking about Nuttawut’s article and my blog post
Morning Guys- Henk is under the weather so we waited on the meeting for 5
minutes and when it was only 3 of us we called it off
I am wondering if anyone had expressed an interest to host a “KERI 101”
session at the next IIW?
On the first morning of every IIW, there are always a few 101 sessions, such as Fido, OIDC, SSI etc.
I suggest we do that for KERI as well and perhaps keep doing it for every future IIW.
I think this is an excellent idea. I already have 2 sessions planned and
wasn't looking to add more. However, I'd be glad to help with this. Previous I've done, "Practical
KERI" which walked through the kli scripts one at a time to show inception, rotation, credential
issuance, etc etc. Perhaps we could work that into a 101 type presentation?
I am actually thinking about something similar to Drummond’s “KERI for
muggles”, which is an introduction for absolute beginners.
I think “Practical KERI” would already assume some familiarity with KERI.
Or maybe the session can be split in half—first half on the theory and the
second half on the code demo.
I am willing to prepare the material for the theory part, but I don’t think I have sufficient
technical expertise to do the latter.
I don't want to force the practical stuff on your idea of a 101, but if you
think it would help, I'll be glad to co-present and do that side of it.
A stupid question.... How does a SAID (Say for a schema or arbitrary document
- a SAD) get resolved and retrieved?
In other words; given a SAID for a document/SAD, what service do I talk to/invoke in order to return
the object itself so it can be read/processed?
The problem is solvable if I have an AID, which has a collection of SAIDs (associated with different
versions of the SAD (content) to which the AID is attached) as I can use the DID:Keri resolver for
the AID, which I presume will have mechanisms to point to the container (say, in the DID Document)
of the related SADs with SAID identifiers.
But if there is no AID (or other flavour of DID that has a resolver), just the SAID, how does that
resolve?
SAD content can be hosted anywhere and shared via an OOBI. That being said,
the notion that you are given a SAID and need to resolve the content behind it is solved with
percolated discovery. If someone is sharing a credential for example with the SAID of the schema,
they will have had access to the schema and can also share that or an OOBI to that with you along
with the credential. That is the heart of percolated discovery.
That sounds fantastic! Thank you for offering to help. I can prepare some
slides over the next few weeks and see what you think. I have also seen your video on Youtube where
I can include some basic kli commands.
Great, let me know how I can help.
As discussed @ IIW (
)?
yes, exactly
So, for an ACDC, which heavily uses SAIDs to point to fragments of JSON
Schema structure, internally to the ACDC, it will have a lookup for those fragments where the lookup
"index" is the SAID.
Percolation is away of sharing that across, say different ACDCs, and the OOBI allows arbitrary
storage (solution dependent) on storage and reference mechanism which leverages the SAID's unique
identifier "feature"
Yes, you got it. And the value of the SAID is that you have one single
identifier for the content that is both externally verifiable _and_ contained in the content. So you
never have to guess what identifier to use to reference or store the content.
I suspect that the option to have an AID for the object as well as it's SAID
will be used as an alternative to percolated discovery as the AID is resolvable to an end point
(e.g. storage resolver).
Finally the KERI and ACDC tutorial you’ve been waiting for!
Join me in Abydos:
I’ve been anticipating this more than any movie, show, etc. Looking forward
to going through it!
Haha! That’s a big compliment. Thanks <@U035R1TFEET> :slightly_smiling_face:
Amazing!!!
<@U02PA6UQ6BV>
<@U03EUG009MY>
It seems TOAD is a commonly misunderstood term in KERI. It is in the config file for the KLI
incept command, but it is not really explained anywhere (except in the whitepaper). So, I
just wrote one in the wiki.
well done
and added to the WOT-terms database

Good work! This is valuable to have. Thank you.
We’ve only used 001, 011 and 111 (“1,3,7”) so far :slightly_smiling_face:
Finally I’ve been able to read a large part of . Great work! I like the
sequence in which you explain stuff, the supporting diagrams and the language used.
I think we should try and integrate your definitions and explanations in amended versions of
glossary terms.
Maybe do this together? I’ve planned the operation to get “Max 1 criterium with 1 term matching
1 knowledge artefact from 1 conceptual model.” as a guide to create a more consistent glossary
and rename the glossary, because it’s not only ACDC terms in there.
According to the terminology pro Rieks Joosten I’ve been too “active”
creating the glossary. His advice:
As soon as you want to develop an activity -> stop!, First ask yourself and others: what is the
result of this, who is going to use this and what should they be able to do with it?
Ask people that come up to the team to know more about the KERI suite:
What is this? Who is going to use this? and what can he do with it, that he can’t do with anything
else.
I’m convinced Rieks is right because we come to a grinding halt trying to use the glossary in the
Education site. Too many angles combined in the acdc wiki texts… We’ve to discuss this with the
team. And then reorganise the glossary according to the answers on Rieks’ questions.
If there’s anyone interested in progress and discussion around KERI
education, join Join Zoom Meeting
it’s now
Sorry to miss but I’m on vacation today
No worries, we might have to revise the format anyway, because nobody showed
up :sweat_smile:
Enjoy your vacation!
I’m stuck in a meeting, hated to miss our meeting today
That sounds fantastic. I am happy to contribute to the amended version. May I
ask what is the rough plan/outline for the new glossary?
Could give an example for “Max 1 criterium with 1 term matching 1 knowledge artefact from 1
conceptual model.“?
I am not a specialist, what I got from Rieks is this. Example: has two target groups to begin with (general and
KERI explorers). That should be one. If we focus on the more general definition (above), we
could agree on the one criterion “is the data real content? (and not overhead)“. The knowledge
artifact & conceptual model are virtual things in our heads.
And if we think of result, who uses, and what they can do with it, we could say: boundary set
(result) between the proof itself and data or control over keys being proved, used by verifiers
(who) to regenerate the prove based on data and signatures (what to do)
Thank you!
I was on vacation as well. I’ll catch you later.
I just got ChatGPT to write an ACDC schema for me after giving it one
example.
My example is here:
The ChatGPT Plus output is here:
{
"$id": "",
"$schema": "",
"title": "Personal Information",
"description": "All of the facts regarding an individual's personal information, including birth date, first name, and last name",
"type": "object",
"credentialType": "PersonalInformation",
"version": "1.0.0",
"properties": {
"v": {
"description": "Credential Version",
"type": "string",
"pattern": "^[a-zA-Z0-9_.-]+$"
},
"d": {
"description": "Credential SAID",
"type": "string",
"pattern": "^[a-zA-Z0-9_.-]+$"
},
"u": {
"description": "One time use nonce - optional",
"type": "string",
"pattern": "^[a-zA-Z0-9_.-]*$"
},
"i": {
"description": "Issuer AID",
"type": "string",
"pattern": "^[a-zA-Z0-9_.-]+$"
},
"ri": {
"description": "Credential Registry Identifier",
"type": "string",
"pattern": "^[a-zA-Z0-9_.-]+$"
},
"s": {
"description": "Schema SAID",
"type": "string",
"pattern": "^[a-zA-Z0-9_.-]+$"
},
"a": {
"oneOf": [
{
"description": "Attributes block SAID",
"type": "string",
"pattern": "^[a-zA-Z0-9_.-]+$"
},
{
"description": "Attributes block",
"type": "object",
"properties": {
"d": {
"description": "Attributes block SAID",
"type": "string",
"pattern": "^[a-zA-Z0-9_.-]+$"
},
"i": {
"description": "Issuee AID",
"type": "string",
"pattern": "^[a-zA-Z0-9_.-]+$"
},
"dt": {
"description": "Issuance date time",
"type": "string",
"format": "date-time"
},
"firstName": {
"description": "The first name of the individual",
"type": "string",
"maxLength": 100
},
"lastName": {
"description": "The last name of the individual",
"type": "string",
"maxLength": 100
},
"birthDate":
"description": "The birth date of the individual",
"type": "string",
"format": "date"
}
},
"additionalProperties": false,
"required": [
"i",
"firstName",
"lastName",
"birthDate"
]
}
]
}
},
"additionalProperties": false,
"required": [
"v",
"i",
"ri",
"s",
"d",
"a"
]
}
After providing the example my prompt was as follows:
Now write me a similar ACDC schema with an attributes (“a”) section containing a birth date, first name, and last name.
ask for the code! :grinning:
My excitement has cooled somewhat after playing a bit more with ChatGPT and the extension that supposedly enabled reading of the internet, which it doesn’t. It never really read the text behind the URLs I sent it.
I am on the waiting list for OpenAI’s plugins. When they are released I will try again.
I like the idea of for interrogating codebases. I am going to offer something like this for KERI and ACDC once it seems to offer promise.
Right now it’s a bit janky.
It would be cool to have ChatGPT trained on all the KERI and ACDC specifications and repositories so we could easily look up information and process the code of the ecosystem. This would be an excellent tool for learners.
The info in the current version of ChatGPT is older than 2021. Their servers have been overloaded. Maybe that’s the reason for the poor experience?
And I think too that GPT has flaws, but it still is a game changer. We tend to overestimate the short-term consequences and underestimate the ones in the long run.
> We tend to overestimate the short-term consequences and underestimate the ones in the long run.
I like this.
Agreed. ChatGPT, until it can consume and respond to whatever dataset I send it, is limited. I look forward to the plugins being added. I’m going to experiment with it so I can learn if “prompt engineering” is worth my time, though ChatGPT is clearly not going to replace any competent programmer worth their salt in its current form.
Writing boilerplate and documentation lookup, yeah, go ahead, take that one off my plate. Thanks ChatGPT.
I want something like with ChatGPT mixed in. Maybe I’ll try my hand.
Due to IIW, I'd like to cancel next Thursday's Edu meeting. So the next one I am looking at is May 4.
We might want to evaluate these bi-weekly Edu meetings first, before continuing them anyway. The interest in it gradually decreases. Is the Edu Zoom much needed, what should be on the agenda, should there be an agenda in the first place, who should run the meeting, etc.
That makes sense. We could consolidate the CESR and Edu meetings so there is one less meeting. I would be happy to assist in running the Edu meetings
Is there a call today?
We decided to suspend the meeting for now during the last KERI call
Good morning <@U024CJMG22J>! Thanks for the clarification
Sorry I have not been for a while. I was ready today :slightly_smiling_face:
No call
Oh sorry, yes, as I suggested above we have indeed evaluated the need for an Edu meeting last Tuesday. The interest in it gradually decreased over the last two months. As Philip explained we decided to suspend the meeting.
Thank you for joining and for helping to shape to education website over the last 8 months or so. We’ll continue to develop the website
Hey folks, we've been having some discussion and it seems given the direction and momentum of signing at the edge (signifypy, signify-TS, and signifide) and the drop off in the need for an edu call, alongside the completion of CESR (way to go Jason) that we could re-purpose both calls for a weekly signify dev call.
We've seen increased interest from multiple parties and it seems wise to utilize this (Thursdays 10am EST) slot moving forward.
The call will be focused on those implementing "signing at the edge", integration with KERIA etc, and not focused on spec Q&A (we have Tuesday calls for that). We'll likely try rotate the focus between implementations if we find the need to do so.
I'd like one more cesride call to discuss cesride/parside/keride and we need a week or so to gather peoples opinions.
Please respond in the <#C04G1KR5R6D|signify> channel, that's where we'll try gather consensus.
<@U02PA6UQ6BV> I added a ACDC wiki page on percolated information discovery.
May I ask also how and are related? Are they synched and should I contribute to WOT-terms instead?
We scrape for WOT-terms.
So it’s safe to contribute there
May I ask a dumb question about how to add a new page?
Of course, there are no dumb questions, just dumb UserInterface :slightly_smiling_face:.
If you’re logged in, there should be a green button that says New Page.
Today, I’ve sent a personal letter to people that I think are in the second group of KERI suite developers; real developers who came just after the leading group (Sam, Philip and Kevin).
Why? Because that’s the group we aim our Edu site at, to start with.
If I, by mistake, considered you in this group and that’s not correct, just forget about the PM.
If I, by mistake, considered you out of this group and that’s not correct, just drop me a line and I will correct my error.
Why do target this group with the site? Because they’ve just experienced what it’s like to have to find your way through the code and concepts. We think there will be more developers trying to deep dive into KERI soon. We want to give them the gift of your experience and our work on the Edu site.
This is the letter:
Hey <recipient>,
I wanted to reach out and give you an update on the exciting progress we’ve made with our site, the “KERI suite search engine (): Personal learning environment and consensus building with others.” As someone with exceptional technical skills, your expertise and input are incredibly valuable in shaping the design of KERI / ACDC but could also be of great value for functionality of the KERI suite search engine (KERISSE).
Before we delve into the specifics, I wanted to share an important piece of advice we received from Rieks Joosten (eSSIF-lab) regarding our development approach of KERISSE. Rieks emphasized the significance of pausing and reflecting before diving headfirst into new activities. Instead of rushing into implementation, it’s crucial for us to take a step back and consider the results we want to achieve, identify our target users, and determine what they should be able to accomplish with the platform. This thoughtful approach will help us avoid potential roadblocks and ensure a streamlined development process.
With that in mind, I would love to hear your insights on the following design considerations for the KERI suite search engine:
1. What is the result of this platform?
The platform aims to serve as a comprehensive collection of relevant resources where consensus can be achieved regarding the meaning of specific terms, but only in the context of the full KERI suite. Our goal is to facilitate a high level of understanding among our target group, with a minimum output level of 7 (or ‘111’).
2 Who is going to use this platform?
We are targeting Technical Self-Sovereign Identity experts who possess both development skills and fundamental knowledge in the areas of cryptography, SSI, and governance. The intended users should have a minimum input level of understanding of 3 (or ‘011’).
3 What should users be able to do with the platform?
Users should have confidence in the completeness and timeliness of the resource-scraping process that powers the platform. Additionally, we aim to provide a glossary service at various levels of understanding, enabling users to achieve consensus and share their search results with others for effective communication. Moreover, we want to offer users the opportunity to delve into the historical concepts and choices underlying all KERI parts, enabling a deeper comprehension of the “Why” behind the suite. Lastly, we aim to enhance the visibility and dynamic questioning of code structure in various programming languages, similar to the capabilities found in Rust.
To summarize:
• What is this platform?
The KERI suite search engine (KERISSE) and a personal learning environment for consensus building with others.
• Who is going to use this platform?
Technical Self-Sovereign Identity experts who are developers as well, while also welcoming guest users starting at level 1 (or ‘001’).
• What can users do with this platform that they can’t do with anything else?
Unlike other platforms, ours incorporates intelligent features such as resource selection, labeling, categorization, and ranking. By combining these capabilities with scraping, indexing, and a customized search engine, we provide manageable and appropriately ranked search results. Users can also utilize tailor-made filters in the left menu of KERISSE to access these results. Presently, neither Github, Google, nor existing AI systems can deliver this level of content.
We would be thrilled to hear your thoughts and suggestions regarding the design and functionality we’ve outlined above.
You could this straight into the source or comments to the source in HackMD .
Your input holds immense value in shaping the KERI suite search engine and ensuring its efficacy as a valuable resource for our target users of which, we image, you could be one. Your technical expertise and unique perspective are indispensable and will undoubtedly contribute to the success of this endeavor.
Thank you for taking the time to consider our request. We eagerly look forward to hearing your valuable insights. Please feel free to reach out to me directly or join our Edu team in Slack for further discussions.
Looking forward to collaborating with you on this exciting project!
Warm regards,
Henk van Cann
The levels mentioned in the letter explained:
The levels mentioned in the letter explained:
Not quite sure why, but there is no “New page” button for me.
I have added the notes and actions of THurdays dev meeting:
Yes, Kor is working on it.
this entrypoint works, the homepage crashes
got it
Here are some diagrams I created of the KERIpy codebase while reading through it yesterday and today:
Diagram of the core modules in a Witness node, minus the HTTP API:
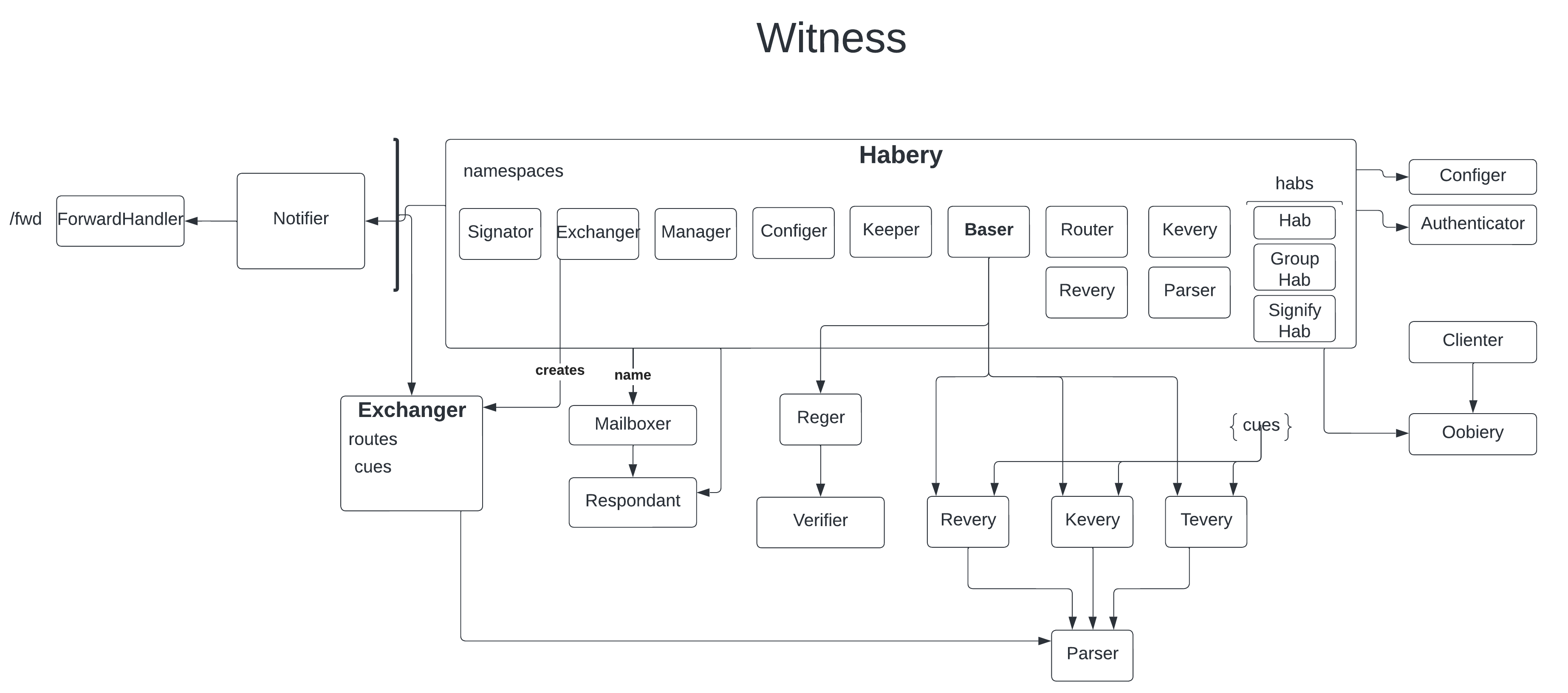
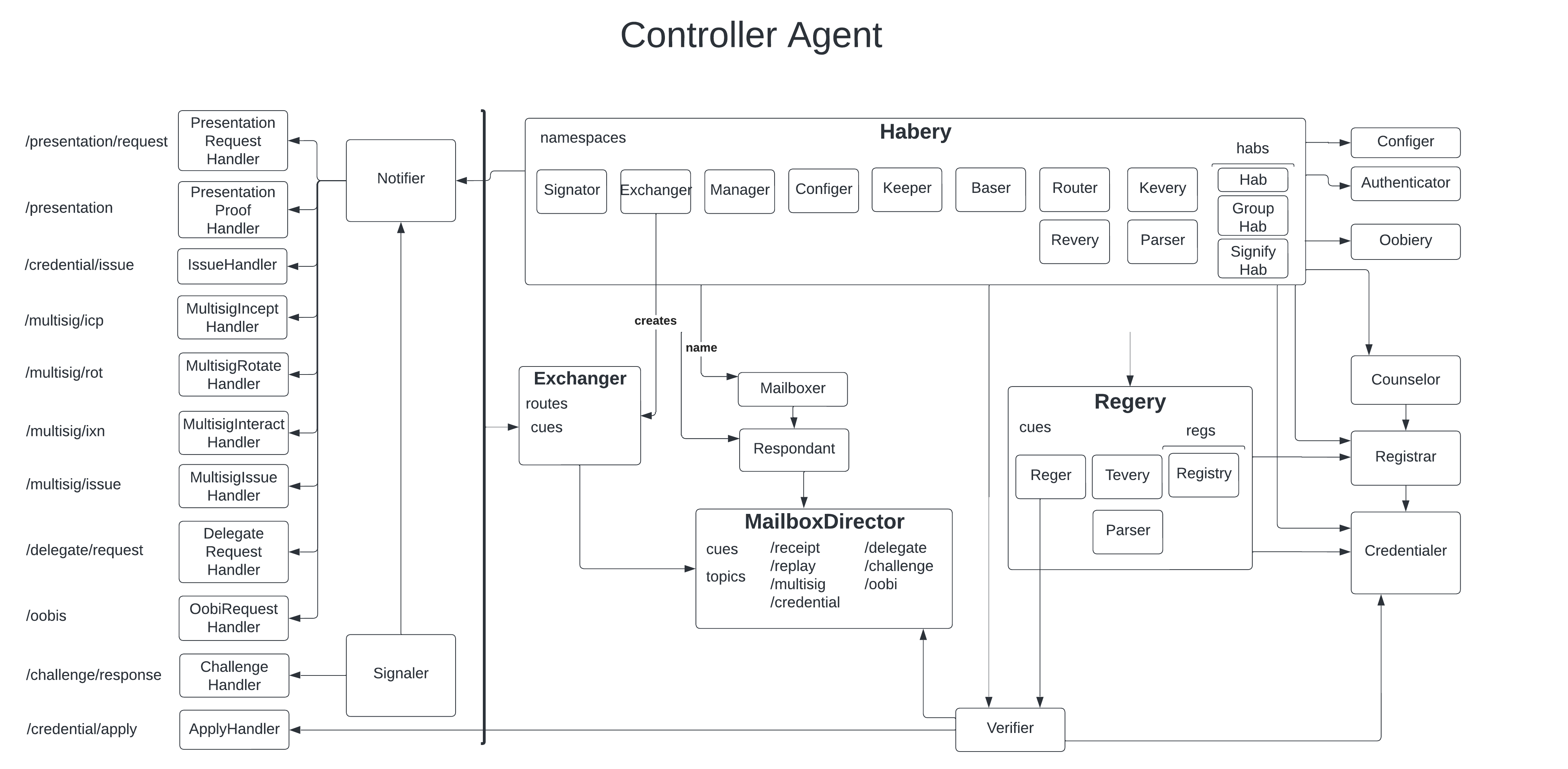
Diagram of the core modules in a Controller node, minus the HTTP API:
Nice, we will incorporate them in KERISSE
Kor and I would like to know whether devs would appreciate the compact version of the Search Engine part of KERISSE here
Hit the Hourglass in the upper right corner
Does the hourglass show up for mobile?
Of course, if not it would be a bug. The filters will be presented first currently, but that’s adjustable, because we now use Bootstrap as the layout framework
The hourglass didn’t show up for me on mobile.
Hi Kent, then that's a bug :slightly_smiling_face:
On my iPhone it takes a second before it is rendered. I will investigate what is going on.
Here was my experience with the chatbot. It gave good English answers, though it doesn’t know code or JSON yet:
Yes, it often says Hmm, I am not sure
We’ve send the question about feeding “the beast” to their support desk, no answer yet.
“Do you exclusively use the sources we feed you, or do you also use external information out of our reach?”
I can't believe that the chatbot exclusively uses the information found in
The free version only accepted so many URL's so not even the whole content is known by the chatbot. So it must also find it's sources elsewhere. That is not ideal.
I am seeking friendly advice that could also be helpful to KERISSE and <@U02PA6UQ6BV>.
Over the past few months, I have been studying KERI while juggling my day job. I have made progress by reading the white papers, the specifications, and exploring KLI demos in KERIpy. However, I have recently found out the limitations of KLI and now wish to delve deeper into understanding KERI’s inner workings and implementation.
I must confess that I lack formal training as a software engineer, and my coding skills are still at an elementary level. While attempting to read the source code in WebOfTrust (KERIpy, Signifypy, Signify-TS, and KERIA), I found them quite overwhelming. Therefore, I am seeking advice on how to approach these repositories effectively.
My objective is not to become an experienced developer and contribute code to the project. Rather, I aim to gain a solid understanding of KERI’s inner workings so that I can communicate effectively with my developer colleagues and make well-informed business decisions.
Any advice or guidance would be appreciated!
Your request added to
/github subscribe list
/github unsubscribe weboftrust/keridoc deployments
undefined
This channel will receive notifications from for: `issues`, `pulls`, `commits`, `releases`
/github unsubscribe weboftrust/keridoc commits
undefined
This channel will receive notifications from for: `issues`, `pulls`, `releases`
/github subscribe weboftrust/keridoc discussions
undefined
This channel will receive notifications from for: `issues`, `pulls`, `releases`, `discussions`
/github subscribe WebOfTrust/keridoc workflows:{name:“Update Glossary” branch:“gh-pages”}
undefined
This channel will receive notifications from for: `issues`, `pulls`, `releases`, `discussions`, `workflows:{name:"Update Glossary" branch:"gh-pages"}`
<@U04H17ZEX9R> last night I found your articles in . They are excellent, congrats!!!
•
•
•
Thank you so much!
Please let me know if I can improve anything.
Part 2 and 3 now added to KERISSE scraper, should be indexed soon
<@U02PA6UQ6BV> I wonder if there's a way to give stars or "likes" to the search results that we consider the best or more correct, so as the time goes, the engine can improve the way it sort the results presenting at the top the ones we like the most. It's a way to "curate" results.
We are able to instruct Typesense which type of index-results should get precendence over others. For example: kel.md should get a higher relevance than just a hit on KEL in some file.
I will discuss you suggestion with Kor and added it to the discussion:
We’re still collecting data, so if you’re missing something, just let us know
<@U02PA6UQ6BV> , be aware of the following readthedocs links:
Yes, from which perspective do you want me to look at it?
It's for devs, online documentation from the repositories
for implementors of keri/acdc apps
Yes, we plan to scrape/index them, zo KERISSE finds them and users are able to filter the results
It’s part of Michal’s suggestion to organise info in KERISSE:
• At Level beginner: What are the pieces
• At Level advanced: Why is it done this way
• At Level expert: The ‘How’ for the devs and only for them.
Readthedocs -> level 3 / expert
How would we start to rank order the search results of KERISSE? For example, when I search “Diger” it would be useful if the definition from the Python class definition would be the most useful to show first. Yet, a simple search engine doesn’t seem to be able to determine that a definition like that should be ranked first. We would have to have some way to add metadata that would influence sort order in order to sort things to the top of the list.
I would like KERISSE to be able to be my primary documentation look up tool at some point. And I expect we will integrate AI into the search engine at some point, if it isn’t there already. I’d be happy to help do some research here to bring things like this into the mix.
The solution I suspect to the rank order is likely a metadata tagging system where we augment the plain search results with some sort of expert-curated metadata annotations of specific search results.
Hi Kent, thank you, could you please add valuable input to discussions in Github; for example . Brief answer: Typesense can be instructed to rank results.
Added from this morning’s call.
just did
I initially assumed it means “binary random”. It didn’t expect it refers to something edible.
/github unsubscribe weboftrust/keridoc issues
undefined
This channel will receive notifications from for: `pulls`, `releases`, `workflows:{name:"Update Glossary" branch:"gh-pages"}`, `discussions`