§ KERI Suite Glossary
Specification Status: Public Review Draft 01 (PR1)
Latest Draft:
Editors:
Contributors:
Contributors:
Participate:
§ Status
This is the first public review draft of the KERI Main Glossary. It is also the first version published using the Spec-Up-T specification editing utility based on Spec-Up specification editing utility developed by the Decentralized Identity Foundation.
§ Copyright Notice
This specification is subject to the OWF Contributor License Agreement 1.0 - Copyright available at https://www.openwebfoundation.org/the-agreements/the-owf-1-0-agreements-granted-claims/owf-contributor-license-agreement-1-0-copyright.
These terms are inherited from the KERI Suite Working Group at the Trust over IP (ToIP) Foundation. Working Group Charter
§ Terms of Use
These materials are made available under and are subject to the OWF CLA 1.0 - Copyright & Patent license. Any source code is made available under the Apache 2.0 license.
THESE MATERIALS ARE PROVIDED “AS IS.” The Trust Over IP Foundation, established as the Joint Development Foundation Projects, LLC, Trust Over IP Foundation Series (“ToIP”), and its members and contributors (each of ToIP, its members and contributors, a “ToIP Party”) expressly disclaim any warranties (express, implied, or otherwise), including implied warranties of merchantability, non-infringement, fitness for a particular purpose, or title, related to the materials. The entire risk as to implementing or otherwise using the materials is assumed by the implementer and user.
IN NO EVENT WILL ANY ToIP PARTY BE LIABLE TO ANY OTHER PARTY FOR LOST PROFITS OR ANY FORM OF INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES OF ANY CHARACTER FROM ANY CAUSES OF ACTION OF ANY KIND WITH RESPECT TO THESE MATERIALS, ANY DELIVERABLE OR THE ToIP GOVERNING AGREEMENT, WHETHER BASED ON BREACH OF CONTRACT, TORT (INCLUDING NEGLIGENCE), OR OTHERWISE, AND WHETHER OR NOT THE OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
§ Introduction
The KERI Main Glossary is a deliverable of the ToIP KERI Suite Working Group (KSWG). Its purpose is to promote shared understanding of terms and concepts across the many different working groups, communities, enterprises, and ecosystems who are collaborating to develop and deploy decentralized digital trust infrastructure.
Contributions and feedback are encouraged from any stakeholder in this area of terminology.
§ Linking to this Glossary
This glossary is designed to be both human and machine readable. All terms are listed alphabetically; acronyms are listed separately and linked to the fully expanded terms. Document authors can link directly to any term using standard web links and anchors following this syntax:
https://trustoverip.github.io/kerisuite-glossary#term:xxxxx
Where xxxxx is the term as it appears in the glossary, with any spaces are replaced by en-dashes (hyphens). For example, a link to the term self-certifying identifer would be:
https://trustoverip.github.io/kerisuite-glossary#self-certifiying-identifier
A specification document written using the Trustoverip’s open source Spec-Up-T environment documented in the Spec-Up-T manual, originally based on Decentralized Identity Foundation’s open source Spec-Up editor.
The tool may create special external references to terms in this glossary using the Spec-Up xref and the tref tags following this syntax:
[ [xref: glossary, xxxxx] ] and [ [tref: glossary, xxxxx] ]
Note: we’ve put spaces between brackets to be able to present this literally; remove the spaces in use.
Where glossary is the text label the document author assigns to the URL of a Web-accessible glossary, and xxxxx is the term as it appears in that glossary, with any spaces are replaced by en-dashes (hyphens). For example, a Spec-Up external reference to the term self-certifying identifer using the label toip for this glossary would look like this:
[[xref: toip1, self-certifying-identifier]]
An item borrowed from an other glossary might look like this:
[[xref: toip2, hash]]
An alias is used to the generate the preferred spelling on the receiving end:
[ [tref: glossary, xxx-xx, Xxx Xx] ]
leads to ‘Xxx Xx’ as the term in the glossary that’s collected via the key ‘xxx-xx’
§ Referenced Glossaries
These glossaries have been interlinked using tref and xref tags. We show both test and production environments. The specs.json is for proficient users to inspect the production settings.
§ Interlinked glossary summary
| Glossary | TEST repo | Live TEST Glossary | Production repo | Live PRODUCTION Glossary | Specs.json PROD |
|---|---|---|---|---|---|
| KERIsuite | HenkvanCann | TEST | WebofTrust | PRODUCTION | Specs.json |
| vLEI | HenkvanCann | ||||
| ToIP Main | HenkvanCann | TEST | ToIP | PRODUCTION | Specs.json |
| ToIP General IT | HenkvanCann | TEST | ToIP | PRODUCTION | Specs.json |
The following glossaries were used as sources for some of the definitions in the ToIP General Glossary. All source glossaries are cited in the definitions of each term.
| Short Name | Source Glossary | URL |
|---|---|---|
| Wikipedia | Wikipedia | https://www.wikipedia.org/ |
| eSSIF-Lab | eSSIF-Lab Glossary | https://essif-lab.github.io/framework/docs/essifLab-glossary |
| NIST-CSRC | NIST Computer Security Resource Center Glossary | https://csrc.nist.gov/glossary/ |
| W3C DID | W3C Decentralized Identifiers (DIDs) 1.0 | https://www.w3.org/TR/did-core/#terminology |
| W3C VC | W3C VC Data Model 1.1 | https://www.w3.org/TR/vc-data-model/#terminology |
§ Terms and Definitions
- abandoned-identifier
-
An AID is abandoned when either the inception-event or a subsequent rotation-event rotates to an empty next key digest list (which means the next threshold must also be 0).
-
More in extended KERI glossary
- access-controlled-interaction
-
Access controlled actions like submitting a report. If you already have that report then load balancer needs a mechanism to drop repeated requests.
-
Source: Samuel Smith / Daniel Hardman / Lance Byrd - Zoom meeting KERI Suite Jan 16 2024; discussion minute 30-60 min
-
More in extended KERI glossary
- ACDC
-
More in extended KERI glossary
- ADC
-
More in extended KERI glossary
- agency
-
No local definition found.
- agent
-
No local definition found.
- AID
-
ToIP specific : autonomic identifier
-
More in extended KERI glossary
- ambient-verifiability
-
Verifiable by anyone, anywhere, at anytime. Although this seems a general term, it was first used in the context of KERI by Sam Smith.
-
Ambient Duplicity Detection is an example of ambient verifiability that describes the possibility of detecting duplicity by anyone, anywhere, anytime.
-
More in extended KERI glossary
- ample
-
The minimum required number of participants in an event to have a supermajority so that one and only one agreement or consensus on an event may be reached. This is a critical part of the KAACE agreement algorithm (consensus) in KERI for establishing consensus between witnesses on the key state of a KERI identifier.
-
More in extended KERI glossary
- APC
-
More in extended KERI glossary
- Attribute
-
a top-level field map within an ACDC that provides a property of an entity that is inherent or assigned to the entity.
-
Also see: attribute
- attributional-trust
-
No local definition found.
- authentic-chained-data-container
-
a directed acyclic graph with properties to provide a verifiable chain of proof-of-authorship. See the full specification
-
Source: Dr. S.Smith, 2024
-
Explained briefly, an ACDC or authentic-data-container proves digital data consistency and authenticity in one go. An ACDC cryptographically secures commitment to the data contained, and its identifiers are self-addressing, which means they point to themselves and are also contained in the data.
-
More in extended KERI glossary
- authentic-data-container
-
A mechanism for conveying data that allows the authenticity of its content to be proved.
-
Instance
-
A Verifiable Credential is an authentic-chained-data-container.
-
More in extended KERI glossary
- authentic-provenance-chain
-
Interlinked presentation-exchange of evidence that allow data to be tracked back to its origin in an objectively verifiable way.
-
More in extended KERI glossary
-
Established control authority over an identifier, that has received attestations to it, e.g. control over the identifier has been verified to its root-of-trust. So the (control over the) identifier is ‘authoritative’ because it can be considered accurate, renowned, honourable and / or respected.
-
Also used to describe PKI key pairs that have this feature.
-
In TrustoverIP context: authoritative
-
More in extended KERI glossary
-
Also ‘AVR’. This a representative of a Legal Entity that are authorized by the DAR of a Legal Entity to request issuance and revocation of:
-
- vLEI Legal Entity Credentials
-
- Legal Entity Official Organizational Role vLEI Credentials (official-organizational-role vLEI Credentials)
-
- Legal Entity Engagement Context Role vLEI Credentials (engagement-context-role vLEI Credentials).
-
Paraphrased by @henkvancann from source Draft vLEI Ecosystem Governance Framework Glossary.
-
More in extended KERI glossary
- autonomic-identifier
-
a self-managing cryptonymous identifier that must be self-certifying (self-authenticating) and must be encoded in CESR as a qualified Cryptographic primitive.
-
Source: Dr. S.Smith, 2024
-
An identifier that is self-certifying-identifier and self-sovereign-identity (or self-managing).
-
More in extended KERI glossary
- autonomic-trust-basis
-
When we use an AID as the root-of-trust we form a so-called autonomic trust basis. This is diagrammed as follows:
-

-
More in extended KERI glossary
- AVR
-
More in extended KERI glossary
- backer
-
an alternative to a traditional KERI based Witness commonly using Distributed Ledger Technology (DLT) to store the KEL for an identifier.
-
Source: Dr. S.Smith, 2024
-
More in extended KERI glossary
- base-media-type
-
credentialplusldplusjson. -
Other media types of credentials are allowed by must provide either unidirectional or bidirectional transformations. So, for example, we would create credential+acdc+json and provide a unidirectional transformation to credential+ld+json.
-
More in extended KERI glossary
- bespoke-credential
-
It’s an issuance-event of the disclosure or presentation of other ACDCs. Bespoke means Custom or tailor made.
-
A bespoke credential serves as an on-the-fly contract with the issuee; it’s a self-referencing and self-contained contract between the issuer and the verifier. Mind you, here the issuer and issuee are merely the discloser and disclosee of another (set of) ACDC(s).
-
More in extended KERI glossary
- best-available-data-acceptance-mechanism
-
The BADA security model provides a degree of replay-attack protection. The attributate originator (issuer, author, source) is provided by an attached signature couple or quadruple. A single reply could have multiple originators. When used as an authorization the reply attributes may include the identifier of the authorizer and the logic for processing the associated route may require a matching attachment.
-
BADA is part of KERI's Zero Trust Computing Architecture for Data Management: How to support Secure Async Data Flow Routing in KERI enabled Applications.
-
More in extended KERI glossary
- bexter
-
The class variable length text that is used in CESR and preserves the round-trip transposability using Base64 URL safe-only encoding even though the text variable length.
-
More in extended KERI glossary
- bis
-
bis = backed vc issue, registry-backed transaction event log credential issuance
-
More in extended KERI glossary
- bivalent
-
A nested set of layered delegations in a delegation tree, wraps each layer with compromise recovery protection of the next higher layer. This maintains the security of the root layer for compromise recovery all the way out to the leaves in spite of the leaves using less secure key management methods.
-

-
More in extended KERI glossary
- blind-oobi
-
A blind OOBI means that you have some mechanisms in place for verifying the AID instead of via the OOBI itself. A blind OOBI is essentially a URL. It’s called “blind” because the witness is not in the OOBI itself. You haves other ways of verifying the AID supplied.
-
More in extended KERI glossary
- blinded-revocation-registry
-
The current state of a transaction-event-log (TEL) may be hidden or blinded such that the only way for a potential verifier of the state to observe that state is when the controller of a designated AID discloses it at the time of presentation.
-
More in extended KERI glossary
- bran
-
A cryptographic string used as a primary input, a seed, for creating key material for and autonomic-identifier.
-
More in extended KERI glossary
- brv
-
brv = backed vc revoke, registry-backed transaction event log credential revocation
-
More in extended KERI glossary
- CESR
-
More in extended KERI glossary
- cesr-proof-signatures
-
CESR Proof Signatures is an extension to the Composable Event Streaming Representation [CESR] that provides transposable cryptographic signature attachments on self-addressing data SAD. Any SAD, such as an Authentic Chained Data Container (ACDC) Verifiable Credential [ACDC], for example, may be signed with a CESR Proof Signature and streamed along with any other CESR content. In addition, a signed SAD can be embedded inside another SAD, and the CESR proof signature attachment can be transposed across envelope boundaries and streamed without losing any cryptographic integrity.
-
(Philip Feairheller, IETF-cesr-proof)
-
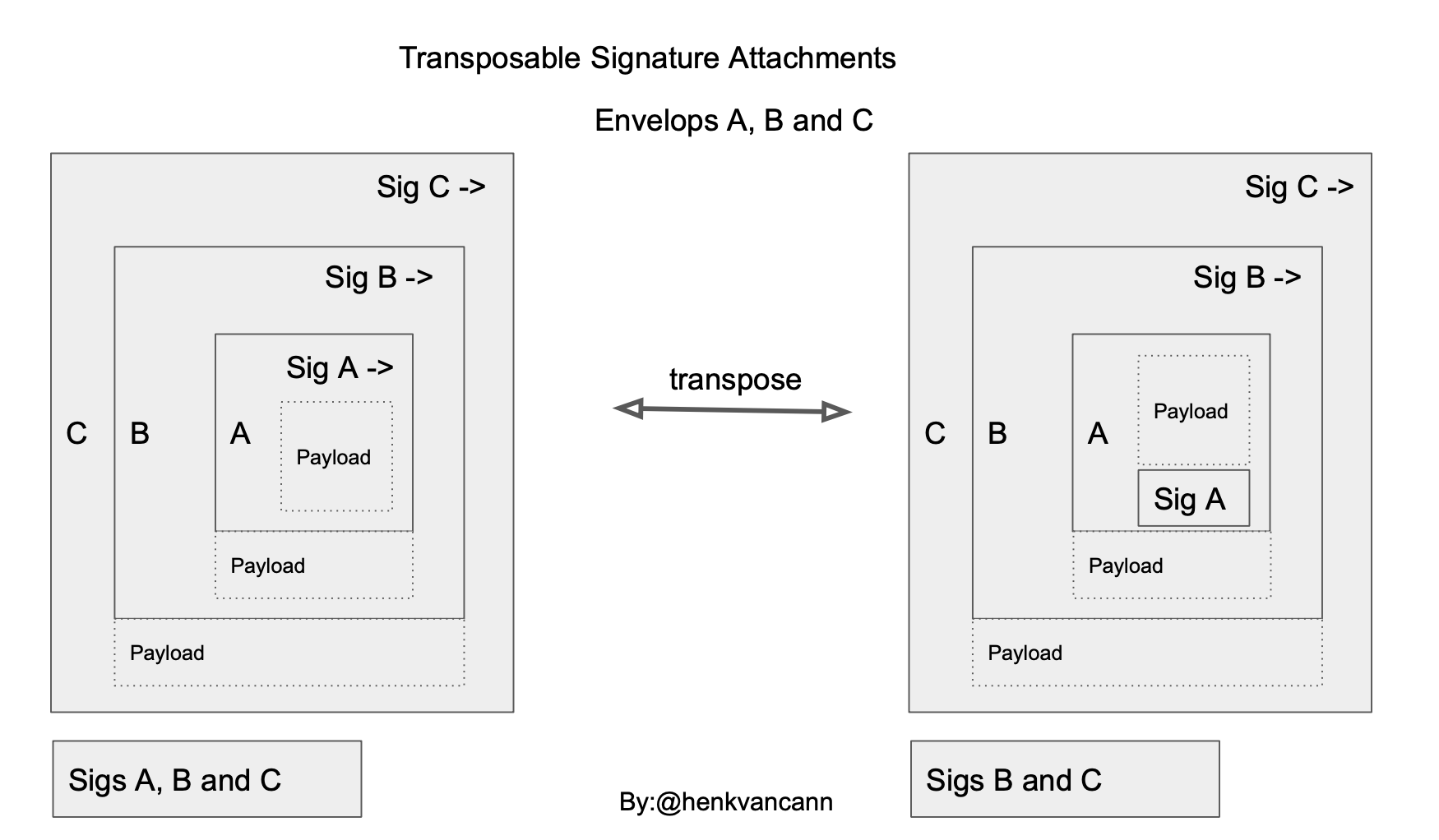
-
More in extended KERI glossary
- CESR-version
-
the CESR Version is provided by a special Count Code that specifies the Version of all the CESR code tables in a given Stream or Stream section.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- cesride
-
is concerned with parsing CESR primitives.
-
Cesride is built from cryptographic primitives that are named clearly and concisely. There are:
-
Each primitive will have methods attached to it that permit one to generate and parse the qualified base2 or base64 representation.
-
More in extended KERI glossary
- chain-link-confidential-disclosure
-
contractual restrictions and liability imposed on a recipient of a disclosed ACDC that contractually link the obligations to protect the disclosure of the information contained within the ACDC to all subsequent recipients as the information moves downstream. The Chain-link Confidential Disclosure provides a mechanism for protecting against un-permissioned exploitation of the data disclosed via an ACDC.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- chain-link-confidentiality
-
Chains together a sequence of disclosee which may also include a set of constraints on data usage by both second and third parties expressed in legal language such that the constraints apply to all recipients of the disclosed data thus the phrase “chain link” confidentiality. Each Disclosee in the sequence in turn is the discloser to the next Disclosee.
-
This is the primary mechanism of granting digital data rights through binding information exchange to confidentiality laws. Confidentiality is dynamically negotiated on a per-event, per-data exchange basis according to the data that is being shared in a given exchange.
-
More in extended KERI glossary
- cigar
-
An unindexed-signature.
-
Source by Jason Colburne
-
More in extended KERI glossary
- CLC
-
More in extended KERI glossary
- code-table-selector
-
the first character in the text code of composable-event-streaming-representation that determines which code-table to use, either a default code table or a code table selector character when not the default code table. Thus the 1 character text code table must do double duty. It must provide selectors for the different text code tables and also provide type codes for the most popular primitives that have a pad size of 1 that appear is the default code table.
-
More in extended KERI glossary
- cold-start-stream-parsing
-
After a reboot (or cold start), a stream processor looks for framing information to know how to parse groups of elements in the stream.
-
If that framing information is ambiguous then the parser may become confused and require yet another cold start. While processing a given stream a parser may become confused especially if a portion of the stream is malformed in some way. This usually requires flushing the stream and forcing a cold start to resynchronize the parser to subsequent stream elements.
-
More in extended KERI glossary
- compact-disclosure
-
a disclosure of an ACDC that discloses only the SAID(s) of some or all of its field maps. Both Partial and Selective Disclosure rely on Compact Disclosure.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- compact-variant
-
Either a most-compact version of an ACDC or the fully-compact version of an ACDC. An issuer commitment via a signature to any variant of ACDC (compact, full, etc) makes a cryptographic commitment to the top-level section fields shared by all variants of that ACDC because the value of a top-level-section is either the SAD or the SAID of the SAD of the associated section.
-
More in extended KERI glossary
- composability
-
short for text-binary concatenation composability. An encoding has Composability when any set of Self-Framing concatenated Primitives expressed in either the Text domain or Binary domain may be converted as a group to the other Domain and back again without loss.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- composable
-
More in extended KERI glossary
- composable-event-streaming-representation
-
Also called ‘CESR’. This compact encoding scheme fully supports both textual and binary streaming applications of attached crypto material of all types. This approach includes composability in both the textual and binary streaming domains. The primitive may be the minimum possible but still composable size.
-
Making composability a guaranteed property allows future extensible support of new compositions of streaming formats based on pre-existing core primitives and compositions of core primitives. This enables optimized stream processing in both the binary and text domains.
-
More in extended KERI glossary
- configuration-traits
-
a list of specially defined strings representing a configuration of a KEL. See #configuration-traits-field.
-
Source: Dr. S.Smith, 2024
-
More in extended KERI glossary
- contextual-linkability
-
No local definition found.
- contingent-disclosure
-
Contingent disclosure is a privacy-preserving mechanism where only specific information or attributes are disclosed under defined conditions. It enables the selective sharing of data such that only the required information is revealed to a relying party, without exposing other unrelated or sensitive details. chain-link-confidentiality is a form of contingent disclosure.
-
More in extended KERI glossary
- contractually-protected-disclosure
-
a discloser of an ACDC that leverages a Graduated Disclosure so that contractual protections can be put into place to minimize the leakage of information that can be correlated. A Contractually Protected Disclosure partially or selectively reveals the information contained within the ACDC in the initial interaction with the recipient and discloses further information only after the recipient agrees to the terms established by the discloser. More information may be progressively revealed as the recipient agrees to additional terms.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- control-authority
-
No local definition found.
- controller
-
an entity that can cryptographically prove the control authority over an AID and make changes on the associated KEL. A controller of a multi-sig AID may consist of multiple controlling entities.
-
Source: Dr. S.Smith, 2024
-
More in extended KERI glossary
- cooperative-delegation
-
The way KERI addresses the security-cost-performance-architecture-trade-off is via delegation of identifier prefixes. Delegation includes a delegator and a delegate. For this reason we may call this a cooperative delegation. This is a somewhat novel form of delegation.
-
More in extended KERI glossary
- correlation
-
In our scope this is an identifier used to indicate that external parties have observed how wallet contents are related.
-
More in extended KERI glossary
- count-code
-
More in extended KERI glossary
- credential
-
Evidence of authority, status, rights, entitlement to privileges, or the like.
-
(source)
-
A credential has its current state and a history, which is captured in a doc or a graph.
-
More in extended KERI glossary
- current-threshold
-
represents the number or fractional weights of signatures from the given set of current keys required to be attached to a Message for the Message to be considered fully signed.
-
Source: Dr. S.Smith, 2024
-
More in extended KERI glossary
- custodial-agent
-
An agent owned by an individual who has granted signing-authority to a custodian who is usually also the host of the running agent software. Using partial-rotation to facilitate custodial key management the owner of the identifier retains rotation-authority and thus the ability to “fire” the custodian at any time without requiring the cooperation of the custodian.
-
More in extended KERI glossary
- custodial-rotation
-
Rotation is based on control authority that is split between two key sets. The first for signing authority and the second (pre-rotated) for rotation authority, the associated thresholds and key list can be structured so that a designated custodial agent can hold signing authority, while the original controller can hold exclusive rotation authority.
-
partial-rotation supports the vital use case of custodial key rotation to authorize a custodial-agent.
-
Paraphrased by @henkvancann based on the IETF-KERI draft 2022 by Samual Smith.
-
More in extended KERI glossary
- dead-attack
-
an attack on an establishment-event that occurs after the Key-state for that event has become stale because a later establishment event has rotated the sets of signing and pre-rotated keys to new sets.
-
More in extended KERI glossary
- decentralized-identity
-
KERIs definition of decentralization (centralization) is about control not spatial distribution. In our definition decentralized is not necessarily the same as distributed. By distributed we mean that activity happens at more than one site. Thus decentralization is about control and distribution is about place. To elaborate, when we refer to decentralized infrastructure we mean infrastructure under decentralized (centralized) control no matter its spatial distribution. Thus decentralized infrastructure is infrastructure sourced or controlled by more than oneentity. -
TrustoverIP related decentralized identity
-
General IT description decentralized-identity
- DEL
-
More in extended KERI glossary
- delegated-identifier
-
Matches the act of delegation with the appropriate digital twin. Consequently when applied recursively, delegation may be used to compose arbitrarily complex trees of hierarchical (delegative) key management event streams. This is a most powerful capability that may provide an essential building block for a generic universal decentralized key management infrastructure (DKMI) that is also compatible with the demand of generic event streaming applications.
-
More in the whitepaper
-
More in extended KERI glossary
- delegation
-
No local definition found.
- derivation-code
-
To properly extract and use the public-key-infrastructure embedded in a self-certifying-identifier we need to know the cryptographic signing scheme used by the key-pair. KERI includes this very compactly in the identifier, by replacing the pad character (a character used to fill a void to able to always end up with a fixed length public key) with a special character that encodes the derivation process. We call this the derivation code.
-
More in extended KERI glossary
- designated-aliases
-
An AID controller can designate aliases which are AID controlled identifiers such as a did:keri, did:webs, etc. The AID controller issues a designated aliases attestation (no issuee) that lists the identifiers and manages the status through a registry anchored to their KEL. See the designated aliases docs
-
More in extended KERI glossary
-
No local definition found.
-
Also ‘DAR’. These are representatives of a Legal Entity that are authorized by the Legal Entity to act officially on behalf of the Legal Entity. DARs can authorize:
-
- vLEI Issuer Qualification Program Checklists
-
- execute the vLEI Issuer Qualification Agreement
-
- provide designate/replace Authorized vLEI Representatives (authorized-vlei-representatives).
-
Paraphrased by @henkvancann from source Draft vLEI Ecosystem Governance Framework Glossary.
-
More in extended KERI glossary
- diger
-
A primitive that represents a digest. It has the ability to verify that an input hashes to its raw value.
-
Source by Jason Colburne
-
More in extended KERI glossary
- dip
-
dip = delcept, delegated inception
-
More in extended KERI glossary
- direct-mode
-
Two primary trust modalities motivated the KERI design, One of these is the direct (one-to-one) mode, in which the identity controller establishes control via verified signatures of the controlling key-pair. The direct mode doesn’t use witnesses nor key-event-receipt-logs, but has direct (albeit intermittent) network contact with the validator.
-
More in extended KERI glossary
- disclosee
-
a role of an entity that is a recipient to which an ACDC is disclosed. A Disclosee may or may not be the Issuee of the disclosed ACDC.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- discloser
-
a role of an entity that discloses an authentic-chained-data-container. A Discloser may or may not be the Issuer of the disclosed ACDC.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- discovery
-
No local definition found.
- dnd
-
Do Not Delegate is a flag/attribute for an AID, and this is default set to “you can delegate.”
-
More in extended KERI glossary
- domain
-
a representation of a primitive either Text (T), Binary (B) or Raw binary ®.
-
Source: Dr. S. Smith
-
Beware: outside of CESR but within the internet world, the term ‘domain’ mostly refers to the concept of a domain name.
-
More in extended KERI glossary
- drt
-
drt = deltate, delegated rotation
-
More in extended KERI glossary
- dual-indexed-codes
-
a context-specific coding scheme, for the common use case of thresholded multi-signature schemes in CESR.
-
More in extended KERI glossary
- dual-text-binary-encoding-format
-
An encoding format that allows for both text and binary encoding format, which is fully interchangeable. The composability property enables the round trip conversion en-masse of concatenated primitives between the text domain and binary domain while maintaining the separability of individual primitives.
-
Read more in source of Samuel Smith
-
More in extended KERI glossary
- duplicitous-event-log
-
This is a record of inconsistent event messages produced by a given controller or witness with respect to a given key-event-receipt-log. The duplicitous events are indexed to the corresponding event in a KERL.
-
More in extended KERI glossary
- duplicity
-
the existence of more than one version of a Verifiable key-event-log for a given AID.
-
Source: Dr. S.Smith, 2024
-
More in extended KERI glossary
- duplicity-detection
-
A mechanism to detect duplicity in cryptographically secured event logs.
-
More in extended KERI glossary
- ECR
-
More in extended KERI glossary
- edge
-
a top-level field map within an ACDC that provides edges that connect to other ACDCs, forming a labeled property graph (LPG).
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- end-role
-
An end role is an authorization for one AID to serve in a role for another AID.
-
For example, declaring that your agent AID is serving in the role of agent for your business AIDs.
-
Source: Phil Feairheller
-
More in extended KERI glossary
- end-verifiability
-
a data item or statement may be cryptographically securely attributable to its source (party at the source end) by any recipient verifier (party at the destination end) without reliance on any infrastructure not under the verifier’s ultimate control.
-
Source Dr. S.Smith
- engagement-context-role
-
A person that represents the legal-entity in a functional or in another context role and is issued an ECR vlei-credential.
-
More in extended KERI glossary
- escrow-state
-
The current state of all the temporary storage locations (what events are waiting for what other information) that KERI protocol needs to keep track of, due to its fully asynchronous nature.
-
More in extended KERI glossary
- establishment-event
-
a key-event that establishes or changes the key state which includes the current set of authoritative keypairs (key state) for an AID.
-
Source: dr. S.Smith
-
More in extended KERI glossary
- exn
-
exn = exchange
-
More in extended KERI glossary
- exp
-
exp = expose, sealed data exposition
-
More in extended KERI glossary
- field-map
-
A traditional
key:valuepair renamed to avoid confusing with the cryptographic use of the term ‘key’. -
More in extended KERI glossary
- first-seen
-
refers to the first instance of a message received by any witness or watcher. The first-seen event is always seen, and can never be unseen. It forms the basis for duplicity detection in KERI-based systems.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- frame-code
-
More in extended KERI glossary
- framing-code
-
a code that delineates a number of characters or bytes, as appropriate, that can be extracted atomically from a stream.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- full-disclosure
-
a disclosure of an ACDC that discloses the full details of some or all of its field maps. In the context of selective-disclosure, Full Disclosure means detailed disclosure of the selectively disclosed attributes, not the detailed disclosure of all selectively disclosable attributes. In the context of partial-disclosure, Full Disclosure means detailed disclosure of the field map that was so far only partially disclosed.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- fully-compact
-
The most compact form of an ACDC. This is the only signed variant of an ACDC and this signature is anchored in a transaction-event-log (TEL) for the ACDC.
-
This is one valid choice for an ACDC schema.
-
This form is part of the graduated-disclosure mechanism in ACDCs.
-
More in extended KERI glossary
- fully-expanded
-
The most user-friendly version of an ACDC credential. It doesn’t need to be signed and typically is not signed since the most compact version which is signed can be computed from this form and then the signature can be looked up in the TEL of the ACDC in question.
-
Regarding the graduated disclosure objective this form is the one with the highest amount of disclosure for a given node of an ACDC graph.
-
More in extended KERI glossary
- GAR
-
More in extended KERI glossary
- ghost-credential
-
Is a valid credential within in a 90 days grace period (the revocation transaction time frame before it’s booked to revocation registry).
-
More in extended KERI glossary
- GLEIF
-
Global Legal Entity Identifier Foundation, visit https://www.gleif.org/en
-
A representative of GLEIF authorized to perform the identity verifications requirements needed to issue the QVI vLEI Credential.
-
More in extended KERI glossary
- GLEIS
-
Global Legal Entity Identifier System
-
More in extended KERI glossary
- graduated-disclosure
-
a disclosure of an ACDC that does not reveal its entire content in the initial interaction with the recipient and, instead, partially or selectively reveals only the information contained within the ACDC necessary to further a transaction with the recipient. A Graduated disclosure may involve multiple steps where more information is progressively revealed as the recipient satisfies the conditions set by the discloser. compact-disclosure, partial-disclosure, selective-disclosure, and full-disclosure are all Graduated disclosure mechanisms.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- graph-fragment
-
An ACDC is a verifiable data structure and part of a graph, consisting of a node property and one or two edge proporties.
-
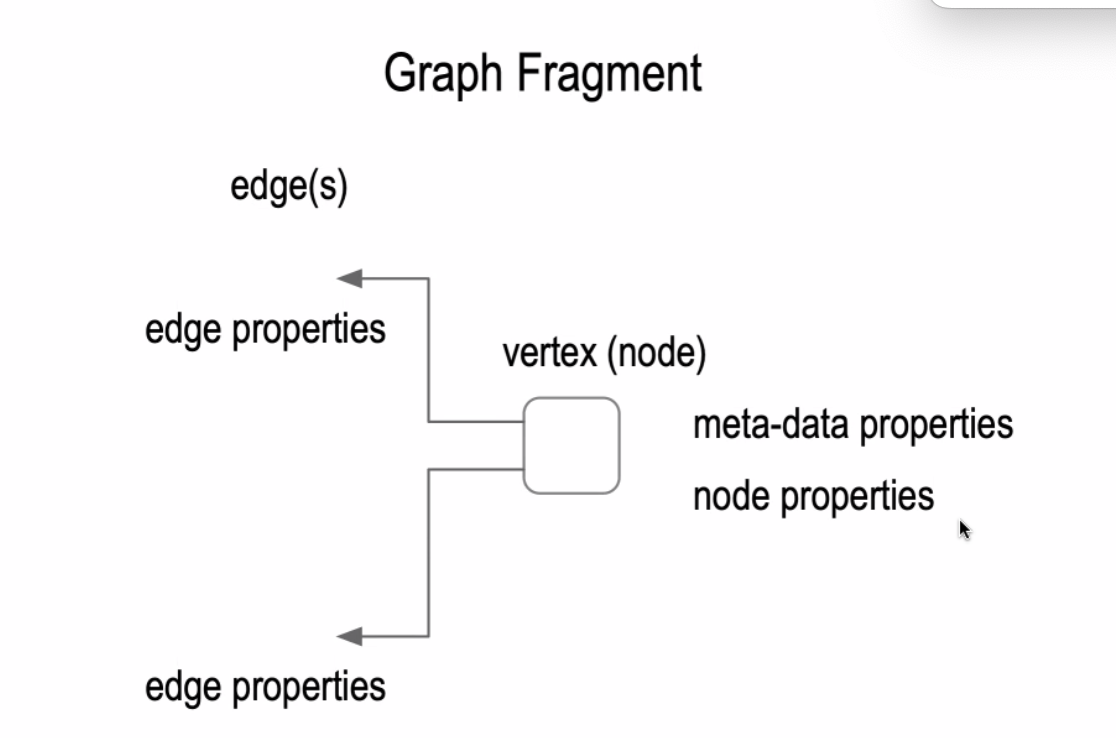
-
More in extended KERI glossary
- group-code
-
More in extended KERI glossary
- group-count-codes
-
special Framing Codes that can be specified to support groups of Primitives which make them pipelinable. Self-framing grouping using Count Codes is one of the primary advantages of composable encoding.
-
Source: Dr. S.Smith
- group-framing-code
-
special Framing Codes that can be specified to support groups of Primitives which make them pipelinable. Self-framing grouping using Count Codes is one of the primary advantages of composable encoding.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- hab
-
A Hab is a keystore for one identifier. The Python implementation in keripy, also used by keria uses LMDB to store key material and all other data.
-
Many Habs are included within and managed by a habery.
-
More in extended KERI glossary
- habery
-
‘Hab’ comes from ‘Habitat’. It’s a place where multi-sigs and AIDs are linked. Habery manages a collection of hab. A Hab is a data structure (a Python object).
-
More in extended KERI glossary
- hierarchical-composition
-
Encoding protocol that is composable in a hierarchy and enables pipelining (multiplexing and de-multiplexing) of complex streams in either text or compact binary. This allows management at scale for high-bandwidth applications.
-
More in extended KERI glossary
- icp
-
icp = incept, inception
-
More in extended KERI glossary
- identity-assurance
-
No local definition found.
- inception
-
The operation of creating an AID by binding it to the initial set of authoritative keypairs and any other associated information. This operation is made verifiable and duplicity evident upon acceptance as the inception event that begins the AID’s KEL.
-
Source Sam Smith
-
More in extended KERI glossary
- inception-event
-
an establishment-event that provides the incepting information needed to derive an AID and establish its initial Key state.
-
Source Sam Smith
-
More in extended KERI glossary
- indexed-signature
-
Also called siger. An indexed signature attachment is used when signing anything with a multi-key autonomic identifier. The index is included as part of the attachment, so a verifier knows which of the multiple public keys was used to generate a specific signature.
-
Source:Philip Feairheller
-
More in extended KERI glossary
- indirect-mode
-
Two primary trust modalities motivated the KERI design, One of these is the indirect (one-to-many) mode, which depends on witnessed key event receipt logs (KERL) as a secondary root-of-trust for validating events. This gives rise to the acronym KERI for key event receipt infrastructure.
-
More in extended KERI glossary
- information-theoretic-security
-
the highest level of cryptographic security with respect to a cryptographic secret (seed, salt, or private key).
-
Source: Dr. S.Smith
- inquisitor
-
In the ACDC context it’s a general term for someone (in a validating role) that launches an inquiry at some KERI witness.
-
More in extended KERI glossary
- integrity
-
~In KERI’s “security first” approach Authenticity includes technical integrity of data involved. This includes:
-
- External consistency or duplicity evident
-
Integrity in ACDCs is “self-verifying”: the self-addressing-identifier) that is contained in the data is also the of hash of the data.
-
The integrity of streaming data in composable-event-streaming-representation and cesr-proof-signatures is established by code tables and verifiable by the mere (killer-)feature: round-robin composability. If you can toggle between the text - and binary representation, then that’s the integrity proof, if not, then it’s provably lacking integrity.
-
A side-benefit of how integrity is implemented in KERI is non-repudiation - done via a crypto-hash verification via the signer’s public key - is not inherent in the meaning of integrity.
-
Furthermore for KERI integrity, as an assessment of the substance or the content itself, does not fall within its narrow definition. Our criterium is cryptographic verifiability. Once you can’t verify, for KERI this type of non-technical integrity is not included in
integrity. For the same reason we wouldn’t use validation* as a mechanism to prove integrity. -
Integrity (of a message or data) means that the information is whole, sound, and unimpaired (not necessarily correct). It means nothing is missing from the information; it is complete and in intended good order.
-
Source: Neil Thomson
-
More in extended KERI glossary
- interaction-event
-
Non-establishment Event that anchors external data to the key-state as established by the most recent prior establishment event.
-
Source Sam Smith
-
More in extended KERI glossary
- interactive-authentication-design
-
A group of approaches having an interactive mechanism that requires a set of requests and responses or challenge responses with challenge response replies for secure authentication.
-
More in source Keri Request Authentication Mechanism (KRAM) by Samuel Smith
-
More in extended KERI glossary
- interceptor
-
a keria class that allows to push events that are happening inside the cloud agent to other backend processes.
-
It is similar to the notifier class but it is used to “notify” other web services.
-
More in extended KERI glossary
- interleaved-serialization
-
Serializations of different types interleaved in an overarching format
-
More in extended KERI glossary
- IPEX
-
More in extended KERI glossary
- iss
-
iss = vc issue, verifiable credential issuance
-
More in extended KERI glossary
- issuance-and-presentation-exchange-protocol
-
provides a uniform mechanism for the issuance and presentation of ACDCs in a securely attributable manner.
-
More in extended KERI glossary
- issuance-event
-
The initial transaction event log event anchored to the issuing AID’s key event log that represents the issuance of an ACDC credential.
-
Source: Philip Feairheller.
-
It’s a sort of “inception-event” of a verifiable credential.
-
More in extended KERI glossary
- issuance-exchange
-
A special case of a presentation-exchange where the discloser is the issuer of the origin (Primary) ACDC of the directed-acyclic-graph formed by the set of chained authentic-chained-data-containers so disclosed.
-
In an issuance exchange, when the origin ACDC has an issuee, the disclosee MAY also be the origin ACDC’s Issuee.
-
More in extended KERI glossary
- issuee
-
a role of an entity to which the claims of an ACDC are asserted.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- issuer
-
a role of an entity that asserts claims and creates an ACDC from these claims.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- ixn
-
JSON field name (attribute) for Interaction Event; its content (value) contains a hash pointer. All transaction-event-log events are anchored in a key-event-log in either ixn (interaction-event) or rot (rotation-events). This is the foundation enabling a verifiable credential protocol to be built on top of KERI.
-
Source Kent Bull 2023
-
More in extended KERI glossary
- judge
-
A judge is an entity or component that examines the entries of one or more key-event-receipt-log and DELs of a given identifier to validate that the event history is from a non-duplicity controller and has been witnessed by a sufficient number of non-duplicitous witness such that it may be trusted or conversely not-trusted by a validator.
-
More in extended KERI glossary
- juror
-
A juror has the basic task of performing duplicity detection on events and event receipts.
-
More in extended KERI glossary
- jury
-
The jury is the set of entities or components acting as juror.
-
More in extended KERI glossary
- KA2CE
-
More in extended KERI glossary
- KAACE
-
More in extended KERI glossary
- KAPI
-
Application programmer interfaces (APIs) for the various components in the KERI ecosystem such as Controllers, Agents, Witnesses, Watchers, Registrars etc need by which they can share information. The unique properties of the KERI protocol require APIs that preserve those properties. We call the set of APIs the KERI API.
-
More in extended KERI glossary
- KAWA
-
More in extended KERI glossary
- keep
-
Is KERI’s and ACDC’s user interface that uses the keripy agent for its backend. It uses the REST API exposed from the keripy agent.
-
Source: Philip Feairheller
-
More in extended KERI glossary
- KEL
-
A Key Event Log.
-
More in extended KERI glossary
- KERI
-
More in extended KERI glossary
- keri-agreement-algorithm-for-control-establishment
-
Agreement on an event in a key event log KEL means each witness has observed the exact version of the event and each witness’ receipt has been received by every other witness.
-
Control establishment means that the set of agreeing witnesses, along with the controller of the identifier and associated keypairs, create a verifiable way to establish control authority for an identifier by reading all of the events in the KEL that have been agreed upon by the witnesses and the controller.
-
More in extended KERI glossary
- keri-command-line-interface
-
Command line tool used to create identifiers, manage keys, query for KELs and participate in delegated identifiers or multi-signature group identifiers. It also includes operations for running witnesses, watchers and cloud agents to establish a cloud presence for any identifier.
-
Most commands require a “name” parameter which references a named Habitat (think wallet) for performing the operation.
-
More in extended KERI glossary
- keri-event-stream
-
A stream of verifiable KERI data, consisting of the key-event-log and other data such as a transaction-event-log. This data is a CESR event stream (TODO: link to IANA application/cesr media type) and may be serialized in a file using composable-event-streaming-representation encoding. We refer to these CESR stream resources as KERI event streams to simplify the vocabulary.
-
Source
did:websToIP specification -
More in extended KERI glossary
- keri-improvement-doc
-
These docs are modular so teams of contributors can independently work and create PRs of individual KIDs; KIDs answer the question “how we do it”. We add commentary to the indivudual KIDs that elaborate on the why. It has been split from the how to not bother implementors with the why.
-
More in extended KERI glossary
- keri-ox
-
The RUST programming-language implementation of the KERI protocol.
-
More in extended KERI glossary
- keri-request-authentication-method
-
All requests from a web client must use KRAM (KERI Request Authentication Method) for replay attack protection. The method is essentially based on each request body needing to include a date time string field in ISO-8601 format that must be within an acceptable time window relative to the server’s date time. See the KRAM Github repo
-
Source SKWA GitHub repo, more info in HackMD.io write-up
-
More in extended KERI glossary
- keri-suite
-
An open-source codebase centered on KERI, with supporting tools like ACDC, CESR, OOBI, KERIA, and Signify — all designed to work together for secure, decentralized key management and identity infrastructure.
-
More in extended KERI glossary
- keri-suite-search-engine
-
KERISSE is the Docusaurus self-education site of Web-of-Trust GitHub repo with Typesense search facilities. Because of its focus on well-versed developers in the field of SSI and the support of their journey to understand the structure of the code and how things work in the keri-suite it’s more a search engine that drills down on documentation.
-
More in extended KERI glossary
- keri’s-algorithm-for-witness-agreement
-
a type of Byzantine Fault Tolerant (byzantine-fault-tolerance) algorithm.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- KERIA
-
KERI Agent in the cloud. The KERIA service will expose 3 separate HTTP endpoints on 3 separate network interfaces.
-
- Boot Interface - Exposes one endpoint for Agent Worker initialization.
-
- Admin Interface - The REST API for command and control operations from the Signify Client.
-
- KERI Protocol Interface - CESR over HTTP endpoint for KERI protocol interactions with the rest of the world.
-
More at Source Github repo
-
More in extended KERI glossary
- KERIA-agent
-
An agent in keria terms, is an instance of a keystore (hab) that runs in a given instance of the KERIA agent server.
-
More in extended KERI glossary
- keride
-
is a Rust programming language library for key-event-receipt-infrastructure. Among its features
-
is CESR, signing, prefixing, pathing, and parsing.
-
More on Github repo
-
More in extended KERI glossary
- keridemlia
-
It is a contraction of key-event-receipt-infrastructure and Kademlia. It’s the distributed database of Witness IP-addresses based on a distributed-hash-table. It also does the CNAME - stuff that domain-name Services (DNS) offers for KERI: the mapping between an identifier and it’s controller AID stored in the KEL to its current wittness AID and the wittness AID to the IP address.
-
(@henkvancann)
-
More in extended KERI glossary
- kerific
-
kerific is a front plugin or extension that currently only works for Chrome and Brave. It matches words in any text on the web that is parseable for kerific and offers buttons to various glossaries and definitions in the self-sovereign-identity field.
-
More in extended KERI glossary
- KERIMask
-
A wallet similar to MetaMask, the manifestation will be a browser extension and it will connect to KERIA servers in order for a person to control AIDs from their browser.
-
More in extended KERI glossary
- keripy
-
The Python programming-language implementation of the KERI protocol.
-
More in extended KERI glossary
- KERISSE
-
More in extended KERI glossary
- KERL
-
More in extended KERI glossary
- kever
-
Kever is a key event verifier.
-
More in extended KERI glossary
- key-event
-
See the more general TrustoverIP concept of key-event: key event
-
Concretely, it is the serialized data structure of an entry in the Key event log (KEL) for an [AID]( autonomic-identifier). Abstractly, the data structure itself. Key events come in different types and are used primarily to establish or change the authoritative set of keypairs and/or anchor other data to the authoritative set of keypairs at the point in the KEL actualized by a particular entry.
-
Source Sam Smith
-
More in extended KERI glossary
- key-event-log
-
a Verifiable data structure that is a backward and forward chained, signed, append-only log of key events for an AID. The first entry in a KEL must be the one and only Inception event of that AID.
-
Source Sam Smith
-
More in extended KERI glossary
- key-event-message
-
Message whose body is a key event and whose attachments may include signatures on its body.
-
Source Sam Smith
-
More in extended KERI glossary
- key-event-receipt
-
message whose body references a Key event and whose attachments must include one or more signatures on that Key event.
-
Source Sam Smith
-
More in extended KERI glossary
- key-event-receipt-infrastructure
-
or the KERI protocol, is an identity system-based secure overlay for the Internet.
-
Source: Dr. S.Smtih
-
More in extended KERI glossary
- key-event-receipt-log
-
a key event receipt log is a kel that also includes all the consistent key event receipt messages created by the associated set of witnesses. See annex key-event-receipt-log.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- Key-state
-
a set of currently authoritative keypairs for an AID and any other information necessary to secure or establish control authority over an AID. This includes current keys, prior next key digests, current thresholds, prior next thresholds, witnesses, witness thresholds, and configurations. A key-state of an AID is first established through an inception event and may be altered by subsequent rotation events.
-
Source: Dr. S.Smith
-
Also see validator
- KID
-
More in extended KERI glossary
- kli
-
More in extended KERI glossary
- KRAM
-
More in extended KERI glossary
- ksn
-
ksn = state, key state notice
-
More in extended KERI glossary
- ledger-backer
-
A witness in KERI that is ledger-registered. It’s a type of backer that proof its authenticity by a signing key anchored to the public key of a data item on a (public) blockchain.
-
More in extended KERI glossary
- legal-entity-engagement-context-role-vlei-credential-governance-framework
-
A document that details the requirements for vlei-role-credential issued to representatives of a Legal Entity in other than official roles but in functional or other context of engagement.
-
Source: Draft vLEI Ecosystem Governance Framework Glossary.
-
More in extended KERI glossary
- legal-entity-official-organizational-role-vlei-credential-governance-framework
-
A document that details the requirements for vlei-role-credential issued to official representatives of a Legal Entity.
-
Source: Draft vLEI Ecosystem Governance Framework Glossary.
-
More in extended KERI glossary
- legal-entity-vlei-credential-governance-framework
-
A document that details the requirements for vLEI Credential issued by a qualified-vlei-issuer to a legal-entity.
-
More in extended KERI glossary
- legitimized-human-meaningful-identifier
-
An AID and its associated self-certifying trust basis gives rise to a trust domain for associated cryptographically verifiable non-repudiable statements. Every other type of identifier including human meaningful identifiers may then be secured in this resultant trust domain via an end-verifiable [[authorization]]. This authorization legitimizes that human meaningful identifier as an LID through its association with an AID. The result is a secured trust domain specific identifier couplet of aid|lid.
-
Source Dr. S.Smith
-
More in extended KERI glossary
- listed-identifier
-
Is a list in an authentic-chained-data-container of authorised did:webs identifier + method; the list appears in the metadata of the did:webs DID-doc.
-
Source: paraphrased Samuel Smith, Zoom meeting KERI dev Thursday Nov 9 2023
-
More in extended KERI glossary
- live-attack
-
an attack that compromises either the current signing keys used to sign non-establishment events or the current pre-rotated keys needed to sign a subsequent establishment event. See (Security Properties of Prerotation)[#live-attacks].
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- locked-state
-
The default status a KERI data store is in once it has been created using a passcode; it is by default encrypted.
-
More in extended KERI glossary
- management-TEL
-
More in extended KERI glossary
- management-transaction-event-log
-
A ‘management transaction-event-log’ will signal the creation of the Virtual Credential Registry VCR and track the list of Registrars that will act as backer for the individual _ transaction event logs (TELs)_ for each virtual-credential (VC).
-
More in extended KERI glossary
- moobi
-
Multi OOBI would allow to share a bunch of different end-points (oobis) all at once. A way for a single store to share multiple endpoints for that store.
-
More in extended KERI glossary
- most-compact
-
An ACDC that, for a given level of disclosure, is as compact as it can be, which means
-
- it has the SAIDs for each section that are not disclosed
-
- it has expanded sections that are disclosed
-
More in extended KERI glossary
- multi-valent
-
A delegator may have multiple delegate, thereby enabling elastic horizontal scalability. Multiple delegates from a single delegator. Furthermore, each delegate may act as a delegator for its own delegates to form a nested delegation tree.
-
More in extended KERI glossary
- naive-conversion
-
Non-CESR Base64 conversion. How people are used to using the Base64 encode and decode. Without pre-padding etc all the stuff CESR does to ensure aligns on 24 bit boundaries so CESR never uses the ‘=’ pad character. But naive base64 will pad if the length is not 24 bit aligned.
-
Source: Samuel Smith in issue 34
-
More in extended KERI glossary
- ndigs
-
Digests of public keys, not keys themselves. The reason to use ndigs is to prove control over public keys or to hide keys. It’s used in Keripy and consists of a list of qualified base64 digests of public rotation key derivations.
-
More in extended KERI glossary
- nested-cooperative-delegated-identifiers
-
In KERI delegations are cooperative, this means that both the delegator and delegate must contribute to a delegation. The delegator creates a cryptographic commitment in either a rotation or interaction event via a seal in a delegated establishment event. The delegate creates a cryptographic commitment in its establishment event via a seal to the delegating event.
-
More in extended KERI glossary
- next-threshold
-
represents the number or fractional weights of signatures from the given set of next keys required to be attached to a Message for the Message to be considered fully signed.
-
More in extended KERI glossary
- non-establishment-event
-
a Key event that does not change the current Key state for an AID. Typically, the purpose of a Non-establishment event is to anchor external data to a given Key state as established by the most recent prior Establishment event for an AID.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- non-interactive-authentication-design
-
A group of approaches having non-interactive mechanisms that pose unique problems because they do not allow a challenge response reply handshake. A request is submitted that is self-authenticating without additional interaction.
-
More in extended KERI glossary
- non-repudiable
-
No local definition found.
- non-transferable-identifier
-
No local definition found.
- official-organizational-role
-
Also ‘OOR’. A person that represents the Legal Entity in an official organizational role and is issued an OOR vLEI Credential.
-
Source Draft vLEI Ecosystem Governance Framework Glossary.
-
More in extended KERI glossary
- OOBI
-
More in extended KERI glossary
- OOR
- opcode
-
Opcodes are meant to provide stream processing instructions that are more general and flexible than simply concatenated primitives or groups of primitives.
-
More in extended KERI glossary
- operator
-
an optional field map in the Edge section that enables expression of the edge logic on edge subgraph as either a unary operator on the edge itself or an m-ary operator on the edge group.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- out-of-band-introduction
-
Out-of-band Introductions (OOBIs) are discovery and validation of IP resources for key-event-receipt-infrastructure autonomic identifiers. Discovery via URI, trust via KERI.
-
The simplest form of a KERI OOBI is a namespaced string, a tuple, a mapping, a structured message, or structured attachment that contains both a KERI AID and a URL. The OOBI associates the URL with the AID.
-
More in extended KERI glossary
- parside
-
is a bunch of generators. Responsible for pulling out a stream of bits from a CESR stream and parse it.
-
Sam Smith suggested for Parside to not iterate stuff, only parse chunks delimited by the count-code. (Source Cesride: meeting Feb 2 2023)
-
More in extended KERI glossary
- partial-disclosure
-
a disclosure of an ACDC that partially discloses its field maps using Compact Disclosure. The Compact Disclosure provides a cryptographically equivalent commitment to the yet-to-be-disclosed content, and the later exchange of the uncompacted content is verifiable to an earlier Partial Disclosure. Unlike Selective disclosure, a partially disclosable field becomes correlatable to its encompassing block after its Full Disclosure.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- partial-pre-rotation
-
More in extended KERI glossary
- partial-rotation
-
The pre-rotation mechanism supports partial pre-rotation or more exactly partial rotation of pre-rotated keypairs. It’s a rotation operation on a set of pre-rotated keys that may keep some keys in reserve (i.e unexposed) while exposing others as needed.
-
More in extended KERI glossary
- pathing
-
It was designed to sign portions of a credential aimed at complex cases like
-
- a credential embedded in another credential
-
- multiple signers, only signing portions of a credential (partial signing)
-
More in extended KERI glossary
- percolated-discovery
-
a discovery mechanism for information associated with an AID or a SAID, which is based on Invasion Percolation Theory. Once an entity has discovered such information, it may in turn share what it discovers with other entities. Since the information so discovered is end-verifiable, the percolation mechanism and percolating intermediaries do not need to be trusted.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- percolated-information-discovery
-
In the OOBI protocol, a discovery mechanism for the KERI and the ACDC protocols is provided by a bootstrap that enables Percolated Information Discovery (PID), which is based on Invasion Percolation Theory.
-
After related information for discovery and verification is bootstrapped from the OOBI, subsequent authorization is non-interactive, thus making it highly scalable. This provides what we call zero-trust percolated discovery or speedy percolated discovery.
-
More in extended KERI glossary
- perfect-security
-
a special case of Information theoretic security ITPS
-
Source: Dr. S.Smith
- persistent-identifier
-
No local definition found.
- PID
-
More in extended KERI glossary
- pre-rotation
-
Cryptographic commitment to next rotated key set in previous rotation or inception-event.
-
More in extended KERI glossary
- prefix
-
A prefix that is composed of a basic Base-64 (URL safe) derivation code pre-pended to Base-64 encoding of a basic public digital signing key.
-
Including the derivation code in the prefix binds the derivation process along with the public key to the resultant identifier.
-
More in extended KERI glossary
- presentation-exchange
-
An exchange that provides disclosure of one or more authentic-chained-data-containers between a Discloser and a Disclosee.
-
A presentation exchange is the process by which authenticity information may be exchanged between two parties, namely, the discloser and disclosee.
-
More in extended KERI glossary
- primary-root-of-trust
-
In KERI a root-of-trust that is cryptographically verifiable all the way to its current controlling key pair in a PKI.
-
The characteristic primary is one-on-one related to the entropy used for the creation of (the seed of) the private keys.
-
More in extended KERI glossary
- proem
-
A “proem” is an introductory statement, preamble, or preface. It sets the stage for the content that follows, often providing context, framing the discussion, or outlining the purpose and scope of the material.
-
More in extended KERI glossary
- promiscuous-mode
-
It is the mode a watcher runs in. A watcher uses the same code as a witness. However a watcher does so “lacking standards of selection; acting without careful judgment; indiscriminate”. Or “Showing little forethought or critical judgment; casual.”
-
More in extended KERI glossary
-
Proof that somebody or something has originally created certain content. It’s about data’s inception. Whereas proof-of-authority is about rights attached to this data.
-
More in extended KERI glossary
- provenanced
-
The act of verifying authenticity or quality of documented history or origin of something.
-
More in extended KERI glossary
- PTEL
-
More in extended KERI glossary
- public-transaction-event-log
-
is a public hash-linked data structure of transactions that can be used to track state anchored to a key-event-log.
-
More in extended KERI glossary
- public-verifiable-credential-registry
-
is a form of a Verifiable Data Registry that tracks the issuance/revocation state of credentials issued by the controller of the key-event-log. Two types of TELs will be used for this purpose: management-transaction-event-log and virtual-credential-transaction-event-log.
-
More in extended KERI glossary
- qry
-
qry = query
-
More in extended KERI glossary
- quadlet
-
a group of 4 characters in the T domain and equivalently in triplets of 3 bytes each in the B domain used to define variable size.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- qualified
-
When qualified, a cryptographic primitive includes a prepended derivation code (as a proem), that indicates the cryptographic algorithm or suite used for that derivation.
-
More in extended KERI glossary
- qualified-vlei-issuer
-
The contracting party to the vLEI Issuer Qualification Agreement that has been qualified by GLEIF as a Qualified vLEI Issuer.
-
Source: Draft vLEI Ecosystem Governance Framework Glossary.
-
More in extended KERI glossary
-
No local definition found.
- qualified-vlei-issuer-vlei-credential-governance-framework
-
A document that details the requirements to enable this Credential to be issued by GLEIF to qualified-vlei-issuer which allows the Qualified vLEI Issuers to issue, verify and revoke legal-entity-vlei-credential-governance-framework, legal-entity-official-organizational-role-vlei-credential-governance-framework, and legal-entity-engagement-context-role-vlei-credential-governance-framework.
-
More in extended KERI glossary
- QVI
-
No local definition found.
-
A designated representative of a QVI authorized, to conduct QVI operations with GLEIF and legal-entity. Also referring to a person in the role of a QAR.
-
Paraphrased by @henkvancann from source Draft vLEI Ecosystem Governance Framework Glossary.
-
More in extended KERI glossary
- rct
-
rct = receipt
-
More in extended KERI glossary
- read-update-nullify
-
Read, update, nullify are a set of actions you (or a server) can take on data. “Read” means to view it, “update” means to change it, and “nullify” means to invalidate it, but not “Delete” it. Mind you, there’s also no “Create”.
-
More in extended KERI glossary
- receipt
-
event message or reference with one or more witness signatures.
-
See Also:
-
More in extended KERI glossary
- receipt-log
-
ordered record of all key event receipts for a given set of witnesses.
-
More in extended KERI glossary
- reconciliation
-
Reconciliation is the process in which you decide to accept a fork of the key-event-log or not.
-
Source: Samuel Smith, Zoom meeting Jan 2 2024.
-
More in extended KERI glossary
- redundant-credential
-
Multiple credentials issued by the same issuer (e.g. a QVI). They do not have anything to do with each other. They are independently valid.
-
More in extended KERI glossary
- registrar
-
identifiers that serve as backers for each transaction-event-log (TEL) under its provenance. This list of Registrars can be rotated with events specific to a certain type of TEL. In this way, a Registrar is analogous to a Backer in KERI KELs and Registrar lists are analogous to Backer lists in KERI KELs.
-
More in extended KERI glossary
- registration-interaction
-
Setup/Registration interaction, new AID and authorization to establish access control. You present a (vLEI) credential. You don’t want that captured and misused. Narrowing the scope to a certain role (e.g. Document Submitter) is a pre-registration via delegation authority.
-
More in extended KERI glossary
- reputation
-
Consistent behaviour over time on the basis of which anyone else makes near-future decisions.
-
Source: Samuel Smith at IIW37.
-
Also see TrustoverIP definition: reputation
-
More in extended KERI glossary
- reputational-trust
-
No local definition found.
- reserve-rotation
-
One important use case for partial-rotation is to enable pre-rotated key pairs designated in one establishment-event to be held in reserve and not exposed at the next (immediately subsequent) establishment event.
-
Source IETF-KERI draft 2022 by Samual Smith.
-
More in extended KERI glossary
- rev
-
rev = vc revoke, verifiable credential revocation
-
More in extended KERI glossary
- revocation-event
-
An event that revokes control-authority over an identifier. From that point in time the authoritative key-pairs at hand are not valid anymore.
-
More in extended KERI glossary
- RID
-
More in extended KERI glossary
- root-autonomic-identifier
-
An entity may provide the root-of-trust for some ecosystem (with delegation )via its root AID. Let’s call this the RID for “root AID”. The RID must be protected using the highest level of security in its key-management.
-
More in extended KERI glossary
- rot
-
JSON field name (attribute) for Rotation Event; its content (value) contains a hash pointer. All transaction-event-log events are anchored in a key-event-log in either ixn (interaction-event) or rot (rotation-events). This is the foundation enabling a verifiable credential protocol to be built on top of KERI.
-
Source Kent Bull 2023
-
More in extended KERI glossary
- rotation
-
The operation of revoking and replacing the set of authoritative key-pair for an AID. This operation is made verifiable and duplicity evident upon acceptance as a rotation event that is appended to the AID’s KEL.
-
Source Sam Smith
-
More in extended KERI glossary
-
The (exclusive) right to rotate the authoritative key pair and establish changed control authority.
-
More in extended KERI glossary
- rotation-event
-
an Establishment Event that provides the information needed to change the Key state, which includes a change to the set of authoritative keypairs for an AID.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- rpy
-
rpy = reply
-
More in extended KERI glossary
- rules
-
a top-level field map within an ACDC that provides a legal language as a Ricardian Contract, which is both human and machine-readable and referenceable by a cryptographic digest.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- RUN
-
The acronym for the new peer-to-peer end-verifiable monotonic update policy is RUN (Read, Update, Nullify).
-
RUN as opposed to CRUD which is the traditional client-server database update policy.
-
More in extended KERI glossary
- run-off-the-crud
-
RUN off the CRUD is an alternative to the traditional CRUD approach to defining basic operations on resources in data management systems (e.g., databases, APIs). RUN stands for Read, Update, Nullify and bears a nuanced approach to deletion.
-
More in extended KERI glossary
- SAD
-
More in extended KERI glossary
- SAID
-
More in extended KERI glossary
- sally
-
is an implementation of a verification service and acting as a reporting server. It is purpose-built software for the vLEI ecosystem to allow participants in the vLEI ecosystem present credentials, so the GLEIF Reporting API can show what vLEI are; issued to legal-entity.
-
More in extended KERI glossary
- salter
-
A primitive that represents a seed. It has the ability to generate new signers.
-
Source by Jason Colburne
-
More in extended KERI glossary
- salty-nonce-blinding-factor
-
For ease of sharing a secret and hiding information with this secret of Blindable State TELs we use a Salty Nonce Blinding Factor. You’d like to hide the state of certain credentials to some verifiers in the future, while keeping the state verifiable for others.
-
More in extended KERI glossary
- schema
-
the said of a JSON schema that is used to issue and verify an ACDC.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- SCID
- secondary-root-of-trust
-
In KERI its a root-of-trust that, for its secure attribution, depends on another verifiable data structure (VDS) which MUST be a primary-root-of-trust.
-
By its nature and cryptographic anchoring via seal to a primary root-of-trust, a secondary root-of-trust still has a high level of trustability and can be automatically verified.
-
More in extended KERI glossary
- secure-asset-transfer-protocol
-
An IETF protocol (and working group) in the making (as of mid 2022) for moving assets between blockchains.
-
More in extended KERI glossary
- secure-attribution
-
No local definition found.
- secure-private-authentic-confidentiality
-
ToIP Trust Spanning Layer Group realized we do have a secure authentication layer (KERI) but we don’t have a secure confidentiality and privacy mechanism. Sam Smith proposes SPAC paper to define this.
-
Related:
-
More in extended KERI glossary
- security
-
‘secure’ is free from or not exposed to danger or harm; safe. For identifiers security typically means secure from exploit or compromise. More specifically an identifier is secure with respect to an entity if there is a mechanism by which that entity may prove it has controller over the identifier.
-
Also see TrustoverIP security policy
-
More in extended KERI glossary
- security-cost-performance-architecture-trade-off
-
The degree of protection offered by a key management infrastructure usually forces a trade-off between security, cost, and performance.
-
Typically, key generation happens relatively infrequently compared to event signing. But highly secure key generation may not support highly performant signing. This creates an architecture trade-off problem.
-
Paraphrased from source Universal Identifier Theory by Samuel Smith
-
More in extended KERI glossary
- selective-disclosure
-
a disclosure of an ACDC that selectively discloses its attributes using Compact Disclosure. The set of selectively disclosable attributes is provided as an array of blinded blocks where each attribute in the set has its own dedicated blinded block. Unlike Partial Disclosure, the selectively disclosed fields are not correlatable to the so far undisclosed but selectively disclosable fields in the same encompassing block.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- self-addressed-data
-
a representation of data content from which a SAID is derived. The SAID is both cryptographically bound to (content-addressable) and encapsulated by (self-referential) its SAD said.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- self-addressing-data
-
an identifier that is content-addressable and self-referential. A SAID is uniquely and cryptographically bound to a serialization of data that includes the SAID as a component in that serialization said.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- self-addressing-identifier
-
any identifier that is deterministically generated out of the content, or a digest of the content.
-
Source: Dr. S. Smtih
-
More in extended KERI glossary
- self-certifying-identifier
-
a type of Cryptonym that is uniquely cryptographically derived from the public key of an asymmetric signing keypair (public, private).
-
Source: Dr. S. Smith
-
Also see the TrustoverIP scope definition: self-certifying identifier
-
More in extended KERI glossary
- self-framing
-
a textual or binary encoding that begins with type, size, and value so that a parser knows how many characters (when textual) or bytes (when binary) to extract from the stream for a given element without parsing the rest of the characters or bytes in the element is Self-Framing.
-
More in extended KERI glossary
- self-sovereign-identity
-
No local definition found.
- SEMVER
-
Semantic Versioning Specification 2.0. See also (https://semver.org)[https://semver.org]
- server-sent-event
-
Mailbox notifications; a streaming service for the agent U/I, to get notifications from the KERI system itself.
-
More in extended KERI glossary
- siger
-
More in extended KERI glossary
- signer
-
A primitive that represents a private key. It has the ability to create Sigers and Cigars (signatures).
-
Source by Jason Colburne
-
More in extended KERI glossary
- signify
-
Signify is a web client key-event signing - and key pair creation app that minimizes the use of KERI on the client.
-
More in extended KERI glossary
- signify-keria-request-authentication-protocol
-
SKRAP is a client to the KERIA server. Mobile clients will be using SKRAP to connect to KERI AIDs via agents in the new, multi-tenant Mark II Agent server, keria.
-
More in extended KERI glossary
-
The authority to sign on behalf of the controller of the authoritative key pair. Often in situation where delegation has taken place, e.g. a custodial agent. These are limited rights because rotation-authority is not included.
-
More in extended KERI glossary
- simple-keri-for-web-auth
-
A KERI implementation that sacrifices performance or other non-security feature for usability. In general a narrow application of KERI may not require all the features of KERI but those features that it does support must still be secure.
-
More on source Github Repo SKWA.
-
More in extended KERI glossary
- SKRAP
-
More in extended KERI glossary
- SKWA
-
More in extended KERI glossary
- sniffable
-
A stream is sniffable as soon as it starts with a group code or field map; in fact this is how our parser (parside) works. and detects if the CESR stream contains a certain datablock.
-
The datablock of CESR binary, CESR Text, JSON, CBOR, MGPK have an Object code or the Group code (binary or text) and it’s always a recognizable and unique three bit combination.
-
More in extended KERI glossary
- sniffer
-
The sniffer is part of parside and detects if the CESR stream contains CESR binary, CESR Text, JSON, CBOR, MGPK.
-
More in extended KERI glossary
- solicited-issuance
-
The issuance of a Legal Entity vLEI Credentials, OOR vLEI Credentials and ECR vLEI Credentials upon receipt by the QAR of a Fully Signed issuance request from the AVR(s) of the legal-entity.
-
Source: Draft vLEI Ecosystem Governance Framework Glossary.
-
More in extended KERI glossary
- SPAC
-
More in extended KERI glossary
- spurn
-
To reject. In KERI, “spurn” refers to a cryptographic or protocol-based act of rejecting an invalid or untrusted event. This rejection is deliberate and purposeful, ensuring the system’s integrity by disregarding information that does not meet the necessary validation criteria. The verb ‘spurn’ is first used in the IPEX specification.
-
More in extended KERI glossary
- SSI
-
No local definition found.
- ssi-system
-
The SSI Infrastructure consists of the technological components that are deployed all over the world for the purpose of providing, requesting and obtaining data for the purpose of negotiating and/or executing electronic transactions.
-
Paraphrased by @henkvancann based on source eSSIF-lab
-
More in extended KERI glossary
- stable
-
Refers to the state of cryptographic verifiability across a network or system. It generally implies that a particular identifier, event, or data set is consistent, fully verified, and cannot be contested within KERI.
-
More in extended KERI glossary
- stale-event
-
A stale key event is an outdated or irrelevant (key) event involving an stale-key that may compromise security.
-
See also: stale-key
- stale-key
-
A stale key is an outdated or expired encryption key that should no longer be used for securing data
-
See also: stale-event
- stream
-
a CESR Stream is any set of concatenated Primitives, concatenated groups of Primitives, or hierarchically composed groups of primitives.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- streamer
-
A convenience class for supporting stream parsing, including nested (tunneled, encrypted) CESR streams. Streams can be a mixture/combination of different primitive, including other streams. A stream is a concatenation of primitives.
-
Source: Kent Bull in chat Zoom meeting KERI Aug 6, 2024.
-
More in extended KERI glossary
- strip-parameter
-
tells us what part of the CESR stream will be parsed by which code.
-
More in extended KERI glossary
- targeted-acdc
-
an ACDC with the presence of the Issuee field in the attribute or attribute aggregate sections.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- TEL
-
More in extended KERI glossary
- text-binary-concatenation-composability
-
An encoding has composability when any set of self-framing concatenated primitives expressed in either the text domain or binary domain may be converted as a group to the other domain and back again without loss.
-
More in extended KERI glossary
- tholder
-
t-holder object that supports fractionally-weighted signing-threshold
-
More in extended KERI glossary
- threshold-of-accountable-duplicity
-
The threshold of accountable duplicity (TOAD) is a threshold number
Mthat the controller declares to accept accountability for an event when any subsetMof theNwitnesses confirm that event. The thresholdMindicates the minimum number of confirming witnesses the controller deems sufficient given some numberFof potentially faulty witnesses, given thatM >= N - F. This enables a controller to provide itself with any degree of protection it deems necessary given this accountability. -
More in extended KERI glossary
- threshold-signature-scheme
-
or TSS; is a type of digital signature protocol used by Mutli-party Computation (MPC) wallets to authorize transactions or key state changes.
-
Source Cryptoapis
-
More in extended KERI glossary
- TOAD
-
More in extended KERI glossary
- top-level-section
-
The fields of an ACDC in compact-variant. The value of a top level section field is either the SAD or the SAID of the SAD of the associated section.
-
An Issuer commitment via a signature to any variant of ACDC (compact, full, etc) makes a cryptographic commitment to the top-level section fields shared by all variants of that ACDC.
-
Paraphrased by @henkvancann based on source.
-
More in extended KERI glossary
- transaction-event-log
-
The set of transactions that determine registry state form a log called a Transaction Event Log (TEL). The TEL provides a cryptographic proof of registry state by reference to the corresponding controlling key-event-log. Any validator may therefore cryptographically verify the authoritative of the registry.
-
More in extended KERI glossary
- transfer-off-ledger
-
The act of transferring control authority over an identifier from a ledger (or blockchain) to the native verifiable KERI data structure Key Event Log.
-
More in extended KERI glossary
- transferable
-
No local definition found.
- transferable-identifier
-
No local definition found.
- trust-domain
-
A trust domain is the ecosystem of interactions that rely on a trust basis. A trust basis binds controllers, identifiers, and key-pairs. For example the Facebook ecosystem of social interactions is a trust domain that relies on Facebook’s identity system of usernames and passwords as its trust basis.
-
See also: trust domain
-
More in extended KERI glossary
- trust-spanning-protocol
-
Protocol using verifiable-identifiers that signs every single message on the internet and makes them verifiable.
-
Also see TrustoverIP ToIP Trust Spanning Protocol
- TSP
- univalent
-
In identifier systems, univalent means having a unique and non-ambiguous identifier for each entity or resource. This means that there is a one-to-one correspondence between the identifiers and the entities, and that no two different entities share the same identifier.
-
Source: Bing chat, Sept 2023
-
More in extended KERI glossary
- unpermissioned-correlation
-
a correlation established between two or more disclosed ACDCs whereby the discloser of the ACDCs does not permit the disclosee to establish such a correlation.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- unsolicited-issuance
-
Issuance of a Legal Entity vLEI Credential upon notice by a QAR to the AVR(s) of the Legal Entity that a Legal Entity vLEI Credential has been solicited on the legal-entity’s behalf.
-
Source: Draft vLEI Ecosystem Governance Framework Glossary.
-
More in extended KERI glossary
- untargeted-acdc
-
an ACDC without the presence of the Issuee field in the attribute or attribute aggregate sections.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- vcp
-
vcp = vdr incept, verifiable data registry inception
-
More in extended KERI glossary
- VCTEL
-
More in extended KERI glossary
- vdr
-
More in extended KERI glossary
- verfer
-
A primitive that represents a public key. It has the ability to verify signatures on data.
-
Source by Jason Colburne
-
More in extended KERI glossary
- verifiable
-
a condition of a KEL: being internally consistent with the integrity of its backward and forward chaining digest and authenticity of its non-repudiable signatures.
-
Source: Dr. S. Smith
-
Explanation
-
Able to cryptographically verify a certain data structure on its inconsistency and its authenticity
-
More in extended KERI glossary
- verifiable identifier
-
No local definition found.
- verifiable-credential
-
Verifiable credentials (VCs) are an open standard for digital credentials. They can represent information found in physical credentials, such as a passport or license, as well as new things that have no physical equivalent, such as ownership of a bank account.
-
See also: verifiable credential
-
More in extended KERI glossary
- verifiable-data-registry
-
A role a system might perform by mediating issuance and verification of ACDCs. See verifiable data registry.
- verifiable-legal-entity-identifier
-
Verifiable credentials are issued by authorized validation agents (QVI) under the governance of GLEIF, who delegate tasks to these agents. They provide cryptographic proof that the information about a legal entity, as linked to its Legal Entity Identifier (LEI), is verifiably authentic, accurate, and up-to-date.
-
More in extended KERI glossary
- verification
-
An action an agent (of a principal) performs to determine the authenticity of a claim or other digital object using a cryptographic key.
-
Source: ToIP glossary, Jan 2024.
-
See also verification
-
More in extended KERI glossary
- verify
-
The act, by or on behalf of a party, of determining whether that data is authenticity (i.e. originates from the party that authored it), timely (i.e. has not expired), and conforms to other specifications that apply to its structure.
-
Source eSSIF-lab in eSSIF-lab glossary
-
See also: verification
-
More in extended KERI glossary
- version
-
an instance of a KEL for an AID in which at least one event is unique between two instances of the kel.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- version-code
-
tells you which set of tables to load, it tells the table state. It’s a unique code. what version of the table is going to load.
-
More in extended KERI glossary
- version-string
-
the first field in any top-level KERI field map in which it appears.
-
More in extended KERI glossary
- virtual-credential-transaction-event-log
-
will track the issued or revoked state of each virtual credential (VC) and will contain a reference to its corresponding management transaction event log (management TEL).
-
More in extended KERI glossary
- vLEI
-
No local definition found.
- vLEI credential
-
No local definition found.
- vlei-ecosystem-governance-framework
-
No local definition found.
- vlei-role-credential
-
No local definition found.
- vrt
-
vrt = vdr rotate, verifiable data registry rotation
-
More in extended KERI glossary
- watcher
-
an entity or component that keeps a copy of a kerl for an identifier but that is not designated by the controller of the identifier as one of its witnesses. See annex watcher.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- weight
-
an optional field map in the Edge section that provides edge weight property that enables directed weighted edges and operators that use weights.
-
Source: Dr. S.Smith
-
More in extended KERI glossary
- weight-of-weights
-
There are 2 levels in the multi-sign weighted thresholds of multisig in KERI because the solution only needs to focus on tightly cooperating teams.
-
- An individual using split keys over devices
-
- A team of teams
-
All other use cases can be solved by other means in KERI (e.g. delegation).
-
More in extended KERI glossary
- well-known-witnesses
-
Witness identifier creation by using salts to initialize their key stores so that you can predict what identifiers will be created. For testing purposes only!
-
More in extended KERI glossary
- witness
-
a witness is an entity or component designated (trusted) by the controller of an identifier. The primary role of a witness is to verify, sign, and keep events associated with an identifier. A witness is the controller of its own self-referential identifier which may or may not be the same as the identifier to which it is a witness. See also keri’s-algorithm-for-witness-agreement.
-
Source: Dr. S. Smith
-
More in extended KERI glossary
- xip
-
A XIP message allows a transaction set to be a mini peer to peer exchange to become a verifiable data structure. It makes the transaction become duplicity evident.
-
Source KERI meeting 2024-03-12
-
More in extended KERI glossary